The company D-Link mistakenly published the secret keys for signing firmware
Manufacturer of routers and other equipment D-Link accidentally published secret certificate encryption keys for signing software, including device firmware.
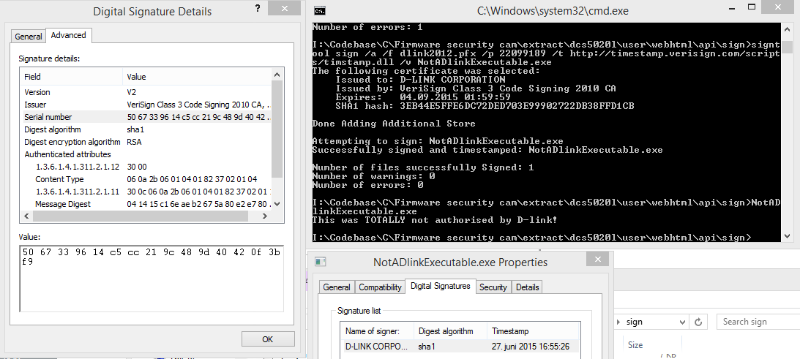
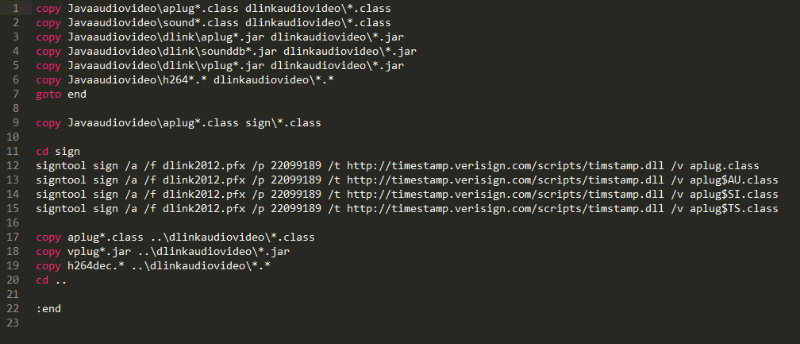
The user under the name bartvbl purchased a D-Link DCS-5020L video surveillance camera and downloaded the firmware update. This software is released under the free license GPL, which gives the opportunity to study the source code. The user studied the firmware code for his device and found in it four “wired” encryption keys to create a signature. Some firmware files contained the keys themselves for signing the code, and some even had scripts with the necessary commands and passwords.
')
In addition, the researcher was able to generate a digital signature for a file that was not related to D-Link products.
According to Threatpost, the problem was confirmed by the researcher Yonathan Klijnsma from the Dutch company Fox-IT.
I think this happened as a result of the error of someone who was packing the source code for publication. The keys for signing certificates were contained in only one source package for a specific firmware version. The version above and below the specific package does not contain the folder in which the keys should be located. Simple folder exception error.
The keys expired in September, however, according to the researcher, any software that was signed with their help will previously be perceived by various systems as a legitimate release of D-Link. In particular, the software signed with the help of such keys is accepted by Microsoft Windows and OS X, says Kleinsma. He also sent the keys to Symantec, which validated D-Link keys, but it is unknown how soon the keys will be revoked.
D-Link has released a new version of the firmware, from which the key information for creating digital signatures has been removed.
As of September 22, the D-Link key for creating a signature has not been revoked. A user of Stack Exchange conducted an experiment and created a file using a key that was published in the screenshot in an article on Tweakers.net
$ openssl x509 -in 0.dlink.cer -text Certificate: Data: Version: 3 (0x2) Serial Number: 50:67:33:96:14:c5:cc:21:9c:48:9d:40:42:0f:3b:f9 Signature Algorithm: sha1WithRSAEncryption Issuer: C=US, O=VeriSign, Inc., OU=VeriSign Trust Network, OU=Terms of use at https://www.verisign.com/rpa (c)10, CN=VeriSign Class 3 Code Signing 2010 CA Validity Not Before: Jul 5 00:00:00 2012 GMT Not After : Sep 3 23:59:59 2015 GMT Subject: C=TW, ST=Taipei, L=TAIPEI CITY, O=D-LINK CORPORATION, OU=Digital ID Class 3 - Microsoft Software Validation v2, CN=D-LINK CORPORATION Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:e2:d5:cc:02:33:47:16:ea:79:bc:51:39:ae:c3: f6:96:f6:43:73:68:6c:35:83:58:63:f6:46:d8:56: 48:df:48:fd:bd:b0:a6:0c:59:10:20:89:c0:cc:73: 59:2f:8c:1a:5a:fc:15:b7:b8:de:cc:4e:1b:3f:50: 4c:98:bb:53:33:fc:7b:13:15:b1:b5:c0:5d:97:95: 81:ab:9c:2d:0a:3c:e5:14:0d:03:3d:cd:6e:43:9c: 0a:75:04:00:b8:50:32:12:ba:9e:6f:ac:fe:93:c7: 93:53:c9:98:29:71:dc:85:fc:23:ef:8c:4a:6a:e7: b9:c7:47:af:58:73:cb:29:e1:3b:ac:c9:55:71:89: 4c:d6:0a:7c:70:dc:bc:cb:f0:b4:dd:25:ec:72:96: 86:36:86:09:1c:c7:ba:5f:a4:37:2d:42:f0:ae:00: fb:5d:97:52:ed:c6:e0:d5:bd:2f:71:fe:98:f6:b4: 40:d1:67:61:0a:41:ce:a2:32:6d:ce:90:d9:5f:09: df:b3:c8:f9:8c:da:33:89:42:8d:72:1e:a2:39:c7: 2a:2d:b0:a3:91:aa:8a:e9:a9:e6:ab:24:7b:62:d2: 9b:35:22:0f:46:1c:87:8b:af:e1:19:98:b4:bd:cf: 6d:4c:c4:04:7f:cf:a1:dd:47:71:d8:fb:eb:33:3e: 09:d9 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:FALSE X509v3 Key Usage: critical Digital Signature X509v3 CRL Distribution Points: Full Name: URI:http://csc3-2010-crl.verisign.com/CSC3-2010.crl X509v3 Certificate Policies: Policy: 2.16.840.1.113733.1.7.23.3 CPS: https://www.verisign.com/rpa X509v3 Extended Key Usage: Code Signing Authority Information Access: OCSP - URI:http://ocsp.verisign.com CA Issuers - URI:http://csc3-2010-aia.verisign.com/CSC3-2010.cer X509v3 Authority Key Identifier: keyid:CF:99:A9:EA:7B:26:F4:4B:C9:8E:8F:D7:F0:05:26:EF:E3:D2:A7:9D Netscape Cert Type: Object Signing 1.3.6.1.4.1.311.2.1.27: 0....... Signature Algorithm: sha1WithRSAEncryption eb:4e:60:57:88:d5:ce:77:a1:94:32:9b:68:fd:3c:23:c4:06: fc:43:2e:d6:66:8c:9d:6d:7a:03:07:fb:7b:66:24:3b:30:99: 9b:d1:3d:66:a9:ca:95:f0:e3:1c:e0:6b:45:03:51:f4:64:15: e8:8e:7a:98:17:8c:c0:95:56:58:55:54:ae:54:5d:8f:e2:65: 0e:cd:79:17:87:0e:8a:2e:40:de:2e:1c:35:5b:6e:ea:23:5a: 4d:70:8e:1d:05:c0:04:d6:2d:c1:26:80:cf:0f:f8:b6:84:4c: eb:82:44:c4:03:f0:65:9e:33:43:f0:e7:39:73:30:be:51:11: e8:70:b3:c3:48:77:fd:d2:e0:8f:fe:dd:89:27:b5:b0:31:ac: 57:63:9d:29:68:9d:2a:8e:e4:d0:dd:5e:d0:6d:f3:bf:63:4d: fa:76:ff:f8:ad:a8:29:c9:90:32:f4:31:22:32:b8:67:92:00: 15:3f:ae:cd:27:71:c2:01:80:24:52:09:6c:14:63:0b:c0:b6: 69:16:5c:d4:34:a4:40:b0:c6:b6:c3:90:ef:64:fc:a8:b2:eb: d8:57:68:43:47:21:55:88:2b:f3:f8:e7:84:52:75:17:73:0c: 8f:86:f7:b1:ea:66:4e:c5:47:7c:27:13:d0:f4:c7:c6:8a:8a: f0:df:d9:a5 Then this file was uploaded to VirusTotal and successfully passed the test.
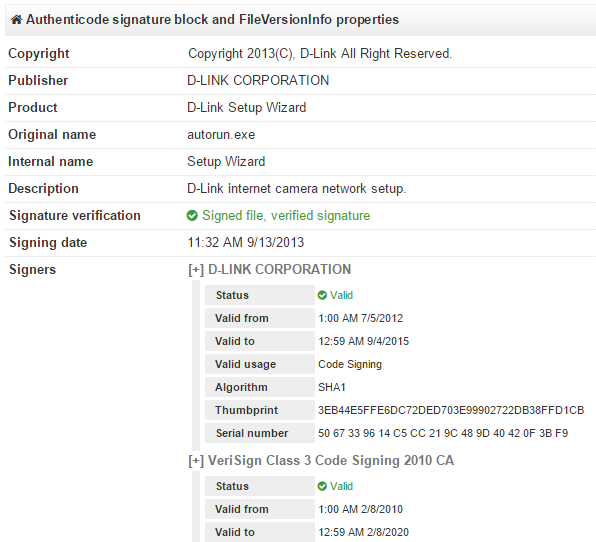
Despite the fact that only one of the found keys turned out to be valid, attackers could still be able to forge certificates and the firmware itself, which could then be installed by unsuspecting users.
Large-scale attacks with malicious software signed with stolen certificates are not so rare. For example, to attack Sony Pictures Entertainment, the malware Destover wiper was used , which was signed with a certificate stolen from Sony.
Similar tactics were used by the hackers behind the Duqu 2.0 APT attack — they used to sign their software certificate stolen from the Chinese technology company Foxconn, which makes Apple, Blackberry, Dell and other well-known vendors.
Source: https://habr.com/ru/post/267547/
All Articles