IP monitoring in blacklists using Zabbix
Some theory
Public spam databases or “black lists” of IP addresses contain information about IP, which for some reason has been declared unfriendly to users. We will not delve into the technological details; It is important that email programs and services use information from these and their own databases in order to protect recipients' email inboxes from unwanted mailings and from spam.
The essence of the problem
If your IP address is blacklisted, the recipients will not receive your emails.
IP penetration into public spam databases threatens the onset of a corporate mail collapse. This is unpleasant, even if the e-mail address on the domain is only 5 and all users can be temporarily “transplanted” to “regular” mail on Yandex or Mail.ru. But, when more than 50 mailboxes integrated with the CRM system are “nailed” to the internal mail server, the problem becomes catastrophic.
')
Decision
“To know, to foresee; foresee to rule. " O. Comte
Calculate the looming threat can and should be before the client feels the punitive measures of mail servers, and the sales department in a panic will make a collective lynch of the local administrator. To do this, we have created an automatic IP monitoring script, notifying the user of possible problems. We chose Powershell as the monitoring platform, and used zabbix 2.4 for the notification.
A little bit about creating a script
The most obvious option seemed to be parsing the web pages of famous IP search engines in the mxtoolbox and 2ip.ru databases. To solve this problem, the .NET and XPATH technologies were used - the most effective tool for parsing XML and WEB, especially for regular expression haters. The first pancake, in some way, turned out to be lumpy, and after a long and exhausting testing, we decided to abandon this decision. The reason was, above all, the dependence on third-party services: if the creators of the site change the structure of the code, then at best, you will need to re-test the software, at worst - rewrite the code.
After a thorough analysis of the existing technologies and developments in this field, we came to a more interesting and practical solution. Development of software based on powershell 3.0, which will independently check for the presence of IP in public spam databases.
How does it work?
Checking the IP address for the presence in the blacklist (DNSBL) is carried out as follows: specify the checked IP in the DNS PTR notation (that is, vice versa “front to back”) and add the DNSBL domain name of the server. If a response from the server is received, then the address being checked is blocked: that is, the IP is seen in one or more blacklists. Regardless of the specifics of the response (it can be any), its very fact indicates that the IP is in the spam database.
Some code
Script code:
<# zabbix . : Key - , zabbix $Zabbix_send = zabbix_sender $zabbix_port = zabbix $zabbix_server = zabbix $zabbix_host = zabbix ( ) #> Function Send_Zabbix { param ( [parameter(mandatory=$true)] $key, [parameter(mandatory=$true)] [int64]$value ) $Zabbix_send = "C:\zabbix_sender.exe" $zabbix_port = "10051" $zabbix_server = "10.0.33.31" $zabbix_host = "Blacklistcheck" echo "$key : $value" $cmd = "$Zabbix_send -z $zabbix_server -p $zabbix_port -s $zabbix_host -k `"$key`" -o $value" echo "$cmd" Invoke-Expression $cmd } # , name,ip $FilePath = "D:\powershell\blacklist.csv" # $iparr = Import-Csv $FilePath foreach ($ipaddr in $iparr) { [string]$IP = $ipaddr.adress [string]$organization = $ipaddr.organization $reversedIP = ($IP -split '\.')[3..0] -join '.' # , $blacklistServers = @( "b.barracudacentral.org"; "bl.deadbeef.com"; "bl.emailbasura.org"; "bl.spamcannibal.org"; "bl.spamcop.net"; "blackholes.five-ten-sg.com"; "blacklist.woody.ch"; "bogons.cymru.com"; "cbl.abuseat.org"; "cdl.anti-spam.org.cn"; "combined.abuse.ch"; "combined.rbl.msrbl.net"; "db.wpbl.info"; "dnsbl-1.uceprotect.net"; "dnsbl-2.uceprotect.net"; "dnsbl-3.uceprotect.net"; "dnsbl.cyberlogic.net"; "dnsbl.inps.de"; "dnsbl.njabl.org"; "dnsbl.sorbs.net"; "drone.abuse.ch"; "drone.abuse.ch"; "duinv.aupads.org"; "dul.dnsbl.sorbs.net"; "dul.ru"; "dyna.spamrats.com"; "dynip.rothen.com"; "http.dnsbl.sorbs.net"; "images.rbl.msrbl.net"; "ips.backscatterer.org"; "ix.dnsbl.manitu.net"; "korea.services.net"; "misc.dnsbl.sorbs.net"; "noptr.spamrats.com"; "ohps.dnsbl.net.au"; "omrs.dnsbl.net.au"; "orvedb.aupads.org"; "osps.dnsbl.net.au"; "osrs.dnsbl.net.au"; "owfs.dnsbl.net.au"; "owps.dnsbl.net.au"; "pbl.spamhaus.org"; "phishing.rbl.msrbl.net"; "probes.dnsbl.net.au"; "proxy.bl.gweep.ca"; "proxy.block.transip.nl"; "psbl.surriel.com"; "rbl.interserver.net"; "rdts.dnsbl.net.au"; "relays.bl.gweep.ca"; "relays.bl.kundenserver.de"; "relays.nether.net"; "residential.block.transip.nl"; "ricn.dnsbl.net.au"; "rmst.dnsbl.net.au"; "sbl.spamhaus.org"; "short.rbl.jp"; "smtp.dnsbl.sorbs.net"; "socks.dnsbl.sorbs.net"; "spam.abuse.ch"; "spam.dnsbl.sorbs.net"; "spam.rbl.msrbl.net"; "spam.spamrats.com"; "spamlist.or.kr"; "spamrbl.imp.ch"; "t3direct.dnsbl.net.au"; "tor.dnsbl.sectoor.de"; "torserver.tor.dnsbl.sectoor.de"; "ubl.lashback.com"; "ubl.unsubscore.com"; "virbl.bit.nl"; "virus.rbl.jp"; "virus.rbl.msrbl.net"; "web.dnsbl.sorbs.net"; "wormrbl.imp.ch"; "xbl.spamhaus.org"; "zen.spamhaus.org"; "zombie.dnsbl.sorbs.net" ) $blacklistedOn = @() foreach ($server in $blacklistServers) { $fqdn = "$reversedIP.$server" try { $null = [System.Net.Dns]::GetHostEntry($fqdn) $blacklistedOn += $server } catch { } } if ($blacklistedOn.Count -gt 0) { Write-Host "$organization is blacklisted on the following servers: $($blacklistedOn -join ', ')" send_zabbix -key $organization -value 1 } else { Write-Host "$organization is not currently blacklisted on any server." send_zabbix -key $organization -value 0 } } In zabbix, data is transmitted via trapper. To use the trapper item, we must:
- have a configured trapper data item in Zabbix
- send data to Zabbix.
Create a blacklistcheck host:
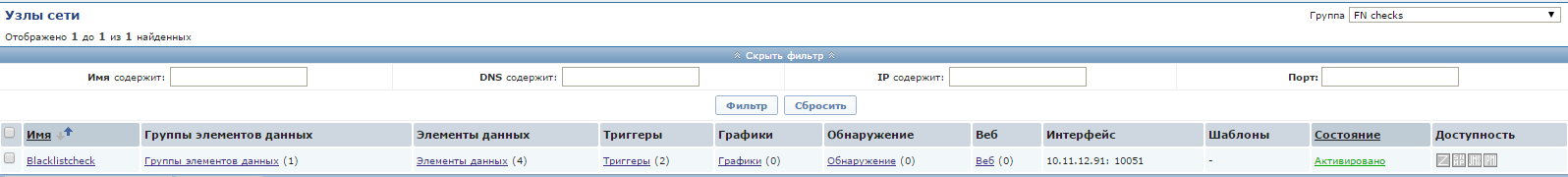
Now you need to configure the trapper:
Create a data item.
Name - can be any
The key is the main element when creating a trapper, this element is case sensitive. The key KEY and key are two different keys.
Type of information : there are 3 options that are suitable for our task: a number, symbol or text. But since we excluded regular expressions, we preferred integer value to text arrays.
The data type is logical; 2 IP values are important for us: it is present (1), or it is not present in the spam lists (0).
The display of values can be left as is, but you can create your own conversion, something like this: 1 = ip is listing, 0 = ip isn`t listing - these values do not affect the script operation, but the visualization of information in zabbix turns out to be interesting.
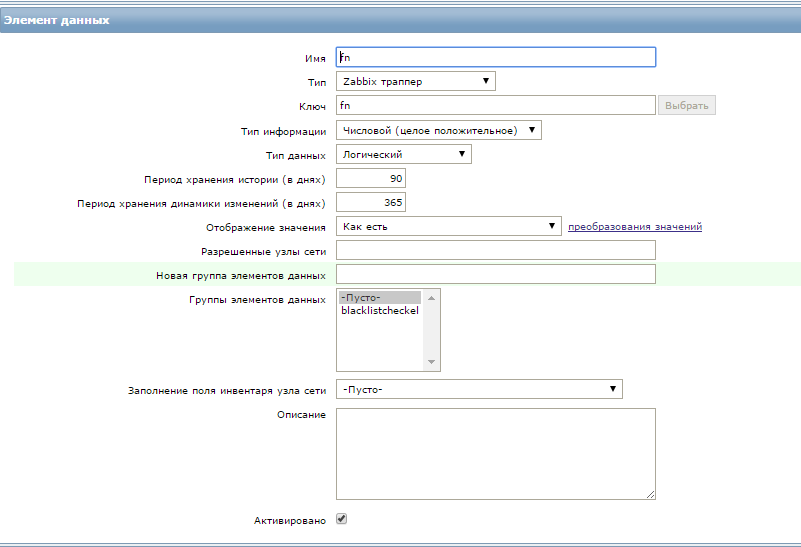
After that, the data element is ready to accept values. You can perform the check through the program zabbix_sender.
In the case of correct operation, a similar result will be obtained:
Result zabbix sender
C: \> zabbix_sender.exe -z 10.0.33.31 -p 10051 -s Blacklistcheck -k fn -o 1 -vv
zabbix_sender.exe [14276]: DEBUG: answer [{"response": "success", "info": "processe
d: 1; failed: 0; total: 1; seconds spent: 0.000066 »}]
info from server: “processed: 1; failed: 0; total: 1; seconds spent: 0.000066 »
sent: 1; skipped: 0; total: 1
zabbix_sender.exe [14276]: DEBUG: answer [{"response": "success", "info": "processe
d: 1; failed: 0; total: 1; seconds spent: 0.000066 »}]
info from server: “processed: 1; failed: 0; total: 1; seconds spent: 0.000066 »
sent: 1; skipped: 0; total: 1
To view the diagnostic data, use the –vv parameter.
The speed of checking one IP is no more than 3 minutes.
Next, you need to configure the trigger for the alert.
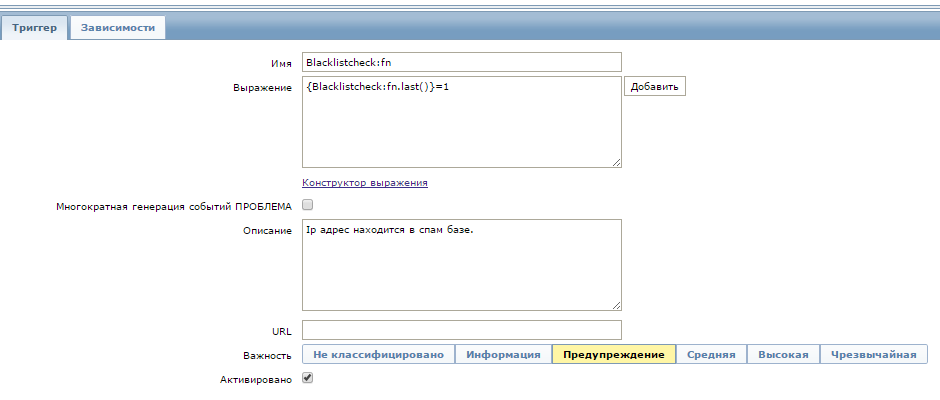
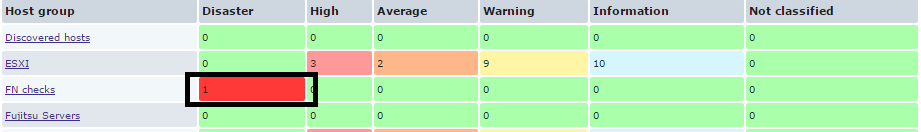
You can specify any name. The expression corresponds to a change in the state of the data item from 0 to 1. In the event of a trigger triggering, a notification will appear in the main zabbix panel.
Practice use
We have created a compact, well-functioning script that automatically notifies the client about possible problems in the operation of the mail system. Agree that the prevention of this issue is much nicer and calmer compared to the need to solve the problem of "fallen off" mail in time trouble.
We have implemented this solution with our customers, and it shows itself well - especially in companies where the sales department works through commercial mailings. This script allows you to quickly localize the problem that caused the IP to enter the spam database and continue to work without damage.
We wish the number of e-mail takeoffs coincided with the number of touchdowns!
Source: https://habr.com/ru/post/267189/
All Articles