SYNful Knock backdoor to attack routers: what's the problem and how to defend

Representatives of the company Mandiant (owned by FireEye) this week published the results of a study on the security of Cisco routers. They were able to detect a backdoor, with the help of which attackers could carry out previously unknown attacks and collect large amounts of confidential data without attracting attention to themselves.
What is the problem
The backdoor was named SYNful Knock (the news about it was already on Habré) and was found on several dozens of routers around the world, including in Russia and Ukraine. Most infected routers were found in the USA (25 devices), Lebanon (12) comes second, followed by Russia with 8 infected routers.
')
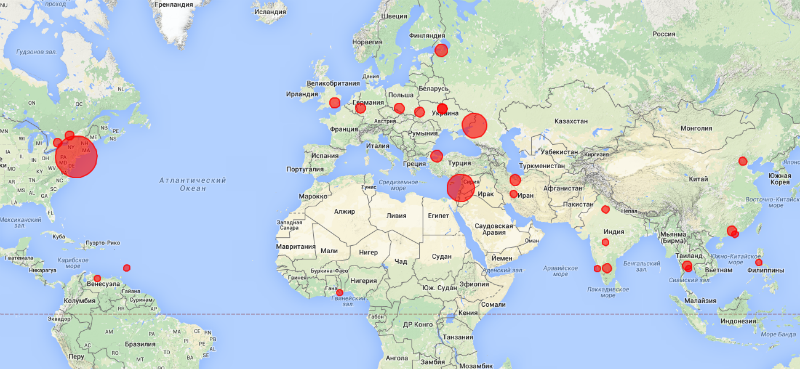
Zmap data
During the attack, attackers do not exploit any serious software vulnerabilities. Instead, an implant is used — a modified Cisco IOS operating system image that allows you to download functional modules from the Internet. The modules are initialized using HTTP (not HTTPS) and special TCP packets sent to the router interface.
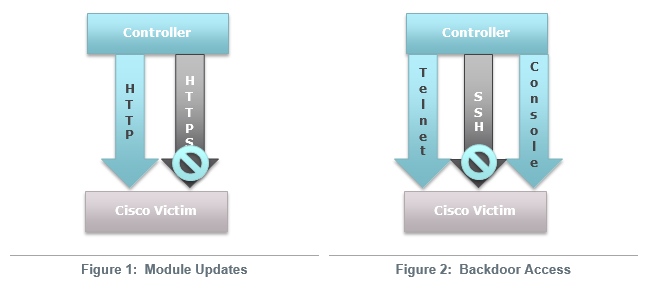
In addition, with the help of a password “wired” into a malicious OS image, attackers can gain remote access to the router via the console or telnet. Bookmarks are activated every time after restarting the device. For OS substitution, stolen credentials and standard administrator passwords are used (users often forget to change the default password).
According to the researchers, Cisco 1841, 2811, and 3825 routers are susceptible to attack. In their blog, the company confirmed the problem.
Mandiant specialists point out that detecting a backdoor indicates that other systems are likely to compromise, not just routers — such devices usually work outside the perimeter of firewall protection and other means of protection, which makes backdoors especially dangerous for them.
The researchers suggest that infected routers could be used to launch attacks against a number of industrial and government organizations.
The described attack is similar to the method that Cisco employees themselves presented in August of this year. Then the company warned customers that attackers could replace ROMMON firmware (ROM Monitor) with a malicious copy. It also did not exploit any vulnerabilities, and hackers accessed the device using real credentials, which may indicate that employees of the organization that owns the router or people who had physical access to the device took part in the attack.
Not only Cisco
The attack described is not specific to Cisco routers only: similarly, you can attack network devices from different hardware manufacturers. In particular, various researchers have published information about the hacking firmware Juniper equipment.
In addition, US intelligence officials said that the Chinese network equipment manufacturer Huawei helps industrial espionage in favor of the Chinese government with backdoors built into the firmware.
Also in September 2015, independent information security researchers published information on a variety of zero-day vulnerabilities in FireEye products.
How to protect
Despite the difficulty of detecting the SYNful Knock backdoor, you can protect yourself with the help of standard security tools — for example, the MaxPatrol security analysis system. To do this, the administrator needs to start Cisco IOS and calculate the checksum of the OS image:
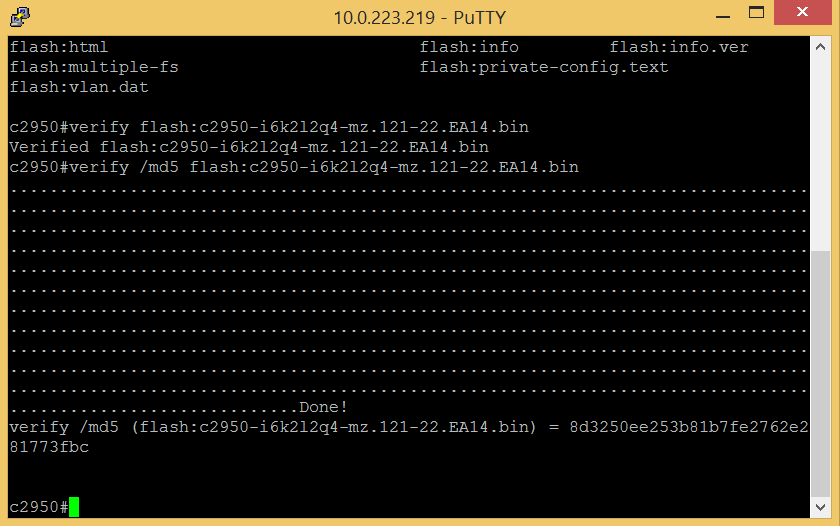
Next, this checksum must be entered into MaxPatrol, after which the system will check for its compliance with the real value:
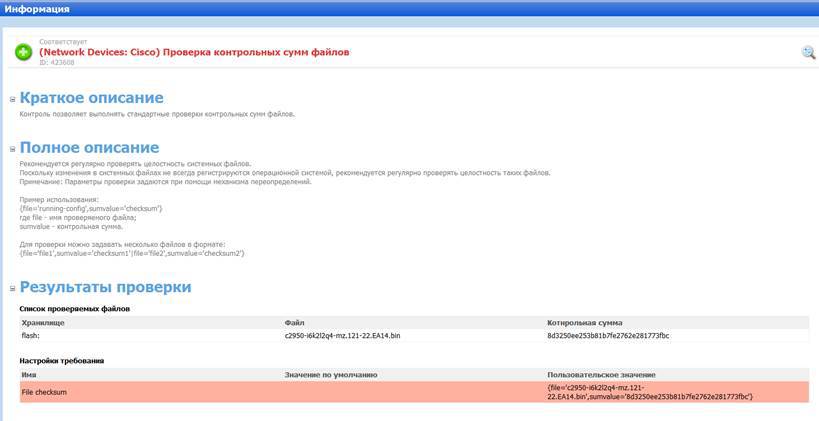
At first glance, the method seems complicated, since in large organizations the number of network devices can reach several thousand. However, even in this case, unique images of the operating system, as a rule, are no more than a few dozen, and you can quickly check them all.
There is another option for detecting SYNful Knock. To do this, the administrator must activate the checksum calculation of the OS image in MaxPatrol 8 using the requirement used above. After a Cisco IOS scan using MaxPatrol, you need to configure the dif-reports and monitor changes to the checksums of the image.
The first method, which involves a comparison with values from a Cisco checksum set , is more efficient. However, given the fact that software changes do not occur so often, the use of dif-reports also allows you to seriously minimize the risk of attack. In this case, however, the script is missing, in which the image can already be modified by hackers, so experts from Positive Technologies recommend using both methods.
We also asked Cisco representatives to comment on the discovery of the SYNful knock backdoor and provide recommendations on how to minimize the associated risks.
Alexey Lukatsky, Cisco Information Security Business Consultant:
- The first generation of Cisco routers has been sold in quantities of about 10 million copies. How serious can be considered the problem encountered by 79 routers? This is not even a ten thousandth percent. And not to mention the fact that the affected generation is removed from sales in 2010.
Fearing [this problem] is worth those who are not having a service contract to support the purchased equipment and wanting to save money, decided to download a new version of IOS not from the Cisco site. Fortunately, the number 79 shows that there are not so many such companies. Of course, one cannot disregard the fact of malicious installation of such a modified network OS. But without an understanding of the affected organizations to draw any conclusions about the focus of such a threat is premature.
To counteract this threat, I would consider three possible scenarios. The first is to upgrade the infrastructure equipment to the third generation of routers (ISR 4K) or at least the second (ISR G2), which are equipped with appropriate protection mechanisms against IOS image substitution and a number of other threats. The second scenario is to build a protective chain of network security tools - IPS, ITU, means of monitoring anomalous activity around obsolete models of network equipment, as well as control physical and network access to equipment. And finally, the third scenario is to implement the recommendations described in our IOS security guides and integrity monitoring. The best strategy is the combination of all three scenarios.
Source: https://habr.com/ru/post/267141/
All Articles