A new way of MITM-attack on the TLS protocol makes the attacker invisible
Austrian security researchers have discovered a TLS (Transport Layer Security) protocol vulnerability that allows attackers to carry out Man in the middle (MITM) attacks.
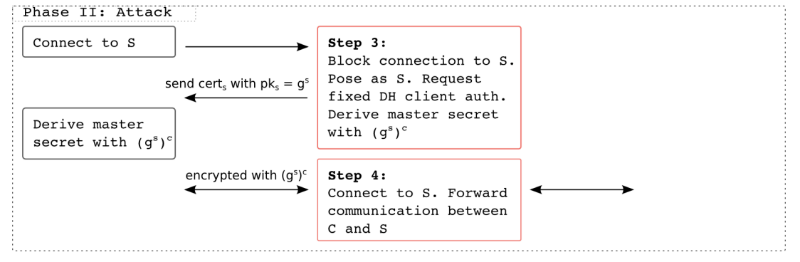
The new technique allows an attacker to get full control over applications in the client browser, listen to communications, replace content on websites and perform actions on them on behalf of the victim. This does not substitute server certificates, thus avoiding the detection of an attack.
')
TLS is used to securely transfer data, but it’s not the first time that serious vulnerabilities have been discovered - two previous security errors called Logjam and Bar Mitzvah .
To launch an attack, the attacker must in some way convince the victim to install a specially crafted client-side SSL certificate, the key of which is known to the attacker. In the future, this allows you to "convince" the client software that it interacts with a trusted server, while in fact communication is carried out with the attacker.
To successfully launch an attack, several factors must also coincide:
1) The server for the connection must support encryption (EC) DH, have an ECDSA certificate without “X509 Key Usage” or “X509 Key Usage” with a KeyAgreement set (according to researchers, such servers make up at least 9.25% of all available HTTPS- servers from the list of the million most popular sites Alexa.com).
2) The client must support the following types of client certificates:
3) The client must support Non-ephemeral (EC) DH and client certificates from the following list:
The authors of the study highlight several options for installing malicious certificates on attacked client applications.
Attackers can create a special version of the software product, in which the certificate for the attack is installed by default. It can also be installed by a cybercriminal working in a company that develops software. In this case, the product will not contain any obvious vulnerabilities, fully complying with the TLS specification, thus nothing will indicate the presence of a backdoor.
In addition, despite the fact that the mechanism for generating and installing client certificates used in modern browsers does not imply the transfer of a secret key from a client computer, it is common practice among various companies and organizations to distribute pre-generated key pairs to clients. Some operating systems (for example, Apple's iOS) even provide functionality to facilitate the installation of key pairs sent by email. Accordingly, attackers can convince the victim to install a malicious certificate using social engineering methods.
Also, a specially developed Android application can install a malicious key into the trusted list, which leads to the possibility of an attack on the TLS connections of other applications. A similar attack method was implemented on Android 4.4.
The video below shows a proof-of-concept demonstration of an attack developed by Austrian researchers:
The researchers found that the implementation of TLS in the BouncyCastle library is subject to a new attack. This means that any client software that uses the TLS BouncyCastle implementation may be vulnerable to attack.
In addition, the Mac OS X (Secure Transport) TLS library is also vulnerable. In the course of the experiment, it was possible to successfully carry out an attack that was not detected on the Safari browser in OS X versions up to 10.5.3. In later versions of the operating system, the client must confirm the choice of the client certificate — however, if the victim installs a malicious certificate, the subsequent connection will also not detect the attack. The attack failed to reproduce on Mac OS X versions 10.8, 10.9 and 10.10.
The most common versions of the OpenSSL library (0.9.8, 1.0.0, 1.0.1) do not support the TLS options required for an attack (which makes systems such as Google Android not susceptible to it). However, in the source code of the library, researchers found evidence of plans to implement support for these options - and one of the developers of a newer version of OpenSSL 1.0.2 confirmed the partial addition of such features. This suggests that client applications using this version of the OpenSSL library may also be vulnerable to the described attack.
The information presented in the study was transmitted to Google, Microsoft and Apple prior to its public disclosure, therefore, the developers of popular browsers had the opportunity to issue corresponding fixes that prevented an attack.
To reduce the likelihood of an attack, the authors of the study recommend service providers who use TLS technology to perform two steps:
In addition, the researchers recommend that developers of client software make corrections to the code of software products:
Developers of TLS library implementations are advised to immediately check them for support for the X509 Key Usage extensions, and mark in the documentation functions that use encryption (EC) DH as outdated and dangerous.
Obviously, the release of patches from manufacturers will take some time, and then you will need to update all the software described, which can hardly be done "right tomorrow." All this time, attackers can use vulnerabilities to attack. Therefore, experts from Positive Technologies recommend using specialized protection tools that allow you to protect yourself right now.
So, the MaxPatrol security monitoring system allows detecting web, mail and other servers that are subject to the described attack, as well as a number of other SSL / TLS vulnerabilities.
In turn, using the PT Application Firewall firewall, you can identify vulnerable client applications and find suspicious connections that could potentially be used by attackers to launch an attack.

The new technique allows an attacker to get full control over applications in the client browser, listen to communications, replace content on websites and perform actions on them on behalf of the victim. This does not substitute server certificates, thus avoiding the detection of an attack.
')
TLS is used to securely transfer data, but it’s not the first time that serious vulnerabilities have been discovered - two previous security errors called Logjam and Bar Mitzvah .
Attack details
To launch an attack, the attacker must in some way convince the victim to install a specially crafted client-side SSL certificate, the key of which is known to the attacker. In the future, this allows you to "convince" the client software that it interacts with a trusted server, while in fact communication is carried out with the attacker.
To successfully launch an attack, several factors must also coincide:
1) The server for the connection must support encryption (EC) DH, have an ECDSA certificate without “X509 Key Usage” or “X509 Key Usage” with a KeyAgreement set (according to researchers, such servers make up at least 9.25% of all available HTTPS- servers from the list of the million most popular sites Alexa.com).
2) The client must support the following types of client certificates:
- rsa_fixed_dh
- dss_fixed_dh
- rsa_fixed_ecdh
- ecdsa_fixed_ecdh
3) The client must support Non-ephemeral (EC) DH and client certificates from the following list:
- TLS_DH_DSS_WITH_3DES_EDE_CBC_SHA
- TLS_DH_RSA_WITH_3DES_EDE_CBC_SHA
- TLS_DH_DSS_WITH_AES_128_CBC_SHA
- TLS_DH_RSA_WITH_AES_128_CBC_SHA
- TLS_DH_DSS_WITH_AES_256_CBC_SHA
- TLS_DH_RSA_WITH_AES_256_CBC_SHA
- TLS_DH_DSS_WITH_AES_128_CBC_SHA256
- TLS_DH_RSA_WITH_AES_128_CBC_SHA256
- TLS_DH_DSS_WITH_AES_256_CBC_SHA256
- TLS_DH_RSA_WITH_AES_256_CBC_SHA256
- TLS_DH_DSS_WITH_CAMELLIA_128_CBC_SHA
- TLS_DH_RSA_WITH_CAMELLIA_128_CBC_SHA
- TLS_DH_DSS_WITH_CAMELLIA_256_CBC_SHA
- TLS_DH_RSA_WITH_CAMELLIA_256_CBC_SHA
- TLS_DH_DSS_WITH_SEED_CBC_SHA
- TLS_DH_RSA_WITH_SEED_CBC_SHA
- TLS_DH_RSA_WITH_AES_128_GCM_SHA256
- TLS_DH_RSA_WITH_AES_256_GCM_SHA384
- TLS_DH_DSS_WITH_AES_128_GCM_SHA256
- TLS_DH_DSS_WITH_AES_256_GCM_SHA384
- TLS_ECDH_ECDSA_WITH_NULL_SHA
- TLS_ECDH_ECDSA_WITH_RC4_128_SHA
- TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_RSA_WITH_NULL_SHA
- TLS_ECDH_RSA_WITH_RC4_128_SHA
- TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384
How attackers install a certificate to attack
The authors of the study highlight several options for installing malicious certificates on attacked client applications.
Attackers can create a special version of the software product, in which the certificate for the attack is installed by default. It can also be installed by a cybercriminal working in a company that develops software. In this case, the product will not contain any obvious vulnerabilities, fully complying with the TLS specification, thus nothing will indicate the presence of a backdoor.
In addition, despite the fact that the mechanism for generating and installing client certificates used in modern browsers does not imply the transfer of a secret key from a client computer, it is common practice among various companies and organizations to distribute pre-generated key pairs to clients. Some operating systems (for example, Apple's iOS) even provide functionality to facilitate the installation of key pairs sent by email. Accordingly, attackers can convince the victim to install a malicious certificate using social engineering methods.
Also, a specially developed Android application can install a malicious key into the trusted list, which leads to the possibility of an attack on the TLS connections of other applications. A similar attack method was implemented on Android 4.4.
The video below shows a proof-of-concept demonstration of an attack developed by Austrian researchers:
Vulnerable Clients
The researchers found that the implementation of TLS in the BouncyCastle library is subject to a new attack. This means that any client software that uses the TLS BouncyCastle implementation may be vulnerable to attack.
In addition, the Mac OS X (Secure Transport) TLS library is also vulnerable. In the course of the experiment, it was possible to successfully carry out an attack that was not detected on the Safari browser in OS X versions up to 10.5.3. In later versions of the operating system, the client must confirm the choice of the client certificate — however, if the victim installs a malicious certificate, the subsequent connection will also not detect the attack. The attack failed to reproduce on Mac OS X versions 10.8, 10.9 and 10.10.
The most common versions of the OpenSSL library (0.9.8, 1.0.0, 1.0.1) do not support the TLS options required for an attack (which makes systems such as Google Android not susceptible to it). However, in the source code of the library, researchers found evidence of plans to implement support for these options - and one of the developers of a newer version of OpenSSL 1.0.2 confirmed the partial addition of such features. This suggests that client applications using this version of the OpenSSL library may also be vulnerable to the described attack.
The information presented in the study was transmitted to Google, Microsoft and Apple prior to its public disclosure, therefore, the developers of popular browsers had the opportunity to issue corresponding fixes that prevented an attack.
How to protect yourself right now
To reduce the likelihood of an attack, the authors of the study recommend service providers who use TLS technology to perform two steps:
- Disable non-ephemeral (EC) DH handshakes support;
- Install the X509 Key Usage extension for ECDSA and DSS certificates, and disable the KeyAgreement flag.
In addition, the researchers recommend that developers of client software make corrections to the code of software products:
- Disable non-ephemeral (EC) DH handshake options;
- Or, at a minimum, disable authentication support using encryption (EC) DH.
Developers of TLS library implementations are advised to immediately check them for support for the X509 Key Usage extensions, and mark in the documentation functions that use encryption (EC) DH as outdated and dangerous.
Obviously, the release of patches from manufacturers will take some time, and then you will need to update all the software described, which can hardly be done "right tomorrow." All this time, attackers can use vulnerabilities to attack. Therefore, experts from Positive Technologies recommend using specialized protection tools that allow you to protect yourself right now.
So, the MaxPatrol security monitoring system allows detecting web, mail and other servers that are subject to the described attack, as well as a number of other SSL / TLS vulnerabilities.
In turn, using the PT Application Firewall firewall, you can identify vulnerable client applications and find suspicious connections that could potentially be used by attackers to launch an attack.
Source: https://habr.com/ru/post/267069/
All Articles