Secure WiFi in Yandex Browser. About protection for those who have not had time to HTTPS
Today I want to tell you about the new technology Yandex. The browser, which protects traffic when using public WiFi. And soon in the framework of the competition at the ZeroNights conference, anyone can try to find a vulnerability in it. But first things first.
Insecure wifi
')
About the risks that are open or poorly protected WiFi, you can not tell on Habré. Suffice it to recall the largest in the history of bank data loss, when the loss of millions of credit card numbers became possible largely due to the use of unreliable WEP protocol in WiFi networks. Ten years have passed since then, but the situation has not become better, because now we are everywhere surrounded by dots without any encryption at all. They can be found in cafes, airports and even at bus stops. In this case, the interception of such WiFi can master any student with a sniffer. And the simplest devices for hacking are generally sold on the Internet for a few dollars.
Although why hack something, if a scammer needs to create his own open WiFi-point in a public place with the name of the form "Free WiFi". Moreover, if its name coincides with the name of another widespread one, then the smartphone can automatically connect to such a point as soon as it is within the radius of action. As a result, fraudsters intercept all unencrypted data. Or replace the DNS with all its consequences. And after all, they can, on the contrary, embed shock advertising or fake authorization forms into this stream.
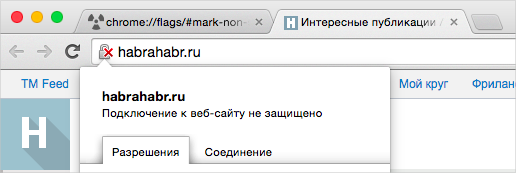
The risk of data interception is well known. That is why the use of HTTPS is an unspoken rule for any site that works with confidential data. In the browser industry, even the idea of switching from HTTPS marking to scary warnings about the insecurity of sites with HTTP is discussed. But change does not happen so quickly. For example, according to our data, 68% of all downloaded pages in the browser still use HTTP. And users, we admit to ourselves, for the most part do not pay attention to the locks in the address bar.
Chromium experiment
At some point, when sorting out requests for support, we thought, and if we do not turn on traffic encryption on the browser side? Moreover, we already have a proxy server, and Turbo technology, which is responsible for optimizing pages and videos, runs on it. But Turbo mode, contrary to popular belief, did not know how to encrypt traffic. A few words about how the old version of Turbo technology worked now in our browser.
Turbo 1.0
Turbo server component was once written by Opera in such widely known in very narrow circles language as Pike . Therefore, we tried not to touch the server again, remembering you know what commandment.
Data exchange with the client was carried out through an already outdated version of SPDY without any TLS. The client code in the browser, initially focused on the simplest mode of operation with compression (ON / OFF), over time has acquired new chips. We taught him to turn on automatically depending on the speed. Moreover, even the statistics of other users from the nearest IP addresses were taken into account in order to turn on the acceleration before the person feels the brakes. And then integrated such a cool chip, as the compression of streaming video. The code from all this for some reason did not get any easier, but really wanted to.
In other words, for the beginning it was necessary to update all the technology of proxying. Fortunately, we had slippers.
Project Slippers
Slippers (TAPOC is Advanced Page Optimizer and Compressor) is a project within the Yandex.Browser development team that initially arose on the personal initiative of several people. The purpose of Sneaker was to update the Turbo code and bring it to modern requirements. At a minimum, it was necessary to rewrite the server part using common technologies. This would allow more actively develop it. Plus, it was necessary to bring order to the client, which was becoming harder to test. And one more trifle: it was important not to break anything.
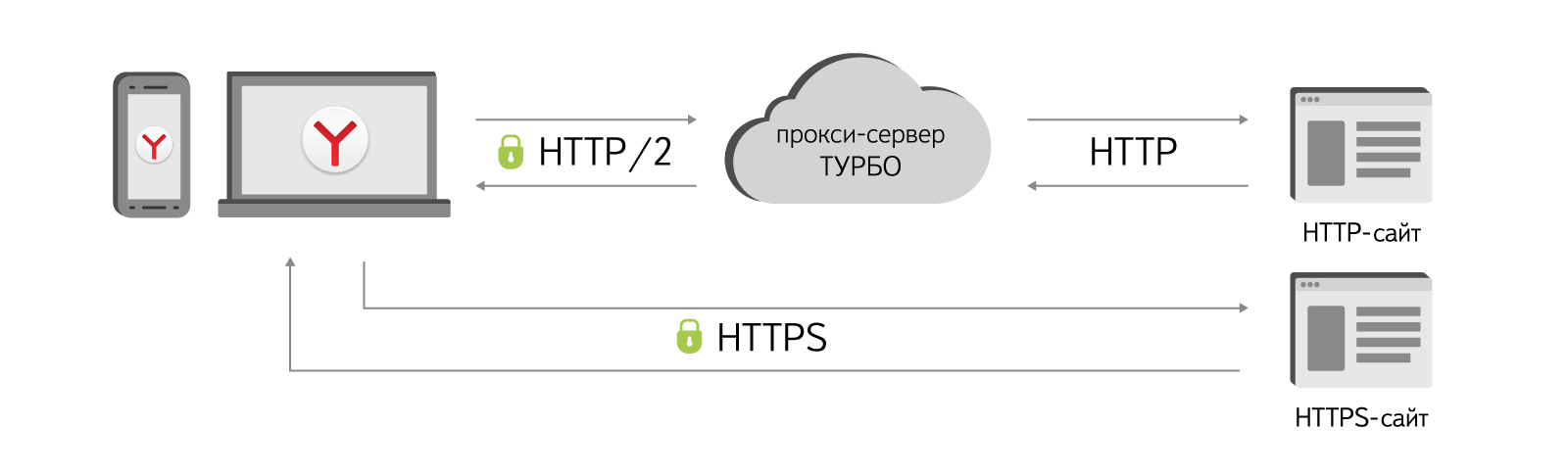
Fortunately, Slippers flew (in a good way), and the plan was even exceeded. The server part was rewritten in slightly more common C ++ using nginx as the kernel. And to compress the pages, instead of the old code, we decided to use the open source library PageSpeed Optimization . Thanks to this, our Turbo mode has learned to minify CSS / JS / HTML, and not just compress. Although something added from myself. For example, converting heavy animated gifs to WebP. They didn’t start producing bicycles on the client and, to the maximum, used the code already existing in Chromium, which is responsible for communication with Data Reduction Proxy (this is a Google server, where content compression also takes place). It was only necessary to make friends this code with video compression and other functions of Yandex. Browser.
But the most pleasant thing is that the connection between the browser and the server now works over HTTP / 2. This includes traffic encryption, stream prioritization, and server push support for critical resources (by the way, they helped the Chromium project with them in due time).
Secure wifi
The issue of encryption was resolved (and at the same time we updated the entire content compression technology). This protected our users' HTTP traffic from interception and DNS spoofing (HTTPS is protected by a certificate without us). But we did not stop there, because we had a more specific goal. Remember the wifi protection?
From the very beginning of this story, we wanted to protect user data, but not to interfere with it, i.e. work without any optimization or compression. Therefore, at the stage of restructuring Turbo, we added a special mode “without compression” “under the hood”. If it is activated, all HTTP traffic will go encrypted through our proxy server, but the content itself will not be changed. But this is not enough.
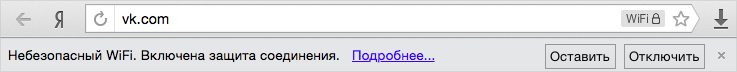
We taught the browser to analyze the connection and enable secure WiFi only when it is really needed. Modern encryption using the WPA and WPA2 protocols is quite reliable. What can not be said about WEP or those points that do not require a password at all. For them, the secure WiFi mode will be turned on automatically. Connection verification will be performed again each time one of the following changes: IP, router's Mac address, ESSID. By the way, the check includes intranet detection as well, in order not to try to send traffic through a proxy without going online.
Protecting WiFi from interception is now available in Yandex Browser for Windows, OS X and Android . Our team continues to refine it now, so your feedback would be very helpful.
Yandex. Browser on ZeroNights
We understand that it is impossible to work on security in an isolated environment. Therefore, soon Yandex. Browser will be available to search for errors and vulnerabilities in a special contest. It will be held in conjunction with the organizers of the conference ZeroNights, which traditionally attracts experts in the field of security. Winners will receive cash prizes. Follow the news!

Insecure wifi
')
About the risks that are open or poorly protected WiFi, you can not tell on Habré. Suffice it to recall the largest in the history of bank data loss, when the loss of millions of credit card numbers became possible largely due to the use of unreliable WEP protocol in WiFi networks. Ten years have passed since then, but the situation has not become better, because now we are everywhere surrounded by dots without any encryption at all. They can be found in cafes, airports and even at bus stops. In this case, the interception of such WiFi can master any student with a sniffer. And the simplest devices for hacking are generally sold on the Internet for a few dollars.
Although why hack something, if a scammer needs to create his own open WiFi-point in a public place with the name of the form "Free WiFi". Moreover, if its name coincides with the name of another widespread one, then the smartphone can automatically connect to such a point as soon as it is within the radius of action. As a result, fraudsters intercept all unencrypted data. Or replace the DNS with all its consequences. And after all, they can, on the contrary, embed shock advertising or fake authorization forms into this stream.
The risk of data interception is well known. That is why the use of HTTPS is an unspoken rule for any site that works with confidential data. In the browser industry, even the idea of switching from HTTPS marking to scary warnings about the insecurity of sites with HTTP is discussed. But change does not happen so quickly. For example, according to our data, 68% of all downloaded pages in the browser still use HTTP. And users, we admit to ourselves, for the most part do not pay attention to the locks in the address bar.

Chromium experiment
At some point, when sorting out requests for support, we thought, and if we do not turn on traffic encryption on the browser side? Moreover, we already have a proxy server, and Turbo technology, which is responsible for optimizing pages and videos, runs on it. But Turbo mode, contrary to popular belief, did not know how to encrypt traffic. A few words about how the old version of Turbo technology worked now in our browser.
Turbo 1.0
Turbo server component was once written by Opera in such widely known in very narrow circles language as Pike . Therefore, we tried not to touch the server again, remembering you know what commandment.
Data exchange with the client was carried out through an already outdated version of SPDY without any TLS. The client code in the browser, initially focused on the simplest mode of operation with compression (ON / OFF), over time has acquired new chips. We taught him to turn on automatically depending on the speed. Moreover, even the statistics of other users from the nearest IP addresses were taken into account in order to turn on the acceleration before the person feels the brakes. And then integrated such a cool chip, as the compression of streaming video. The code from all this for some reason did not get any easier, but really wanted to.
In other words, for the beginning it was necessary to update all the technology of proxying. Fortunately, we had slippers.
Project Slippers
Slippers (TAPOC is Advanced Page Optimizer and Compressor) is a project within the Yandex.Browser development team that initially arose on the personal initiative of several people. The purpose of Sneaker was to update the Turbo code and bring it to modern requirements. At a minimum, it was necessary to rewrite the server part using common technologies. This would allow more actively develop it. Plus, it was necessary to bring order to the client, which was becoming harder to test. And one more trifle: it was important not to break anything.

Fortunately, Slippers flew (in a good way), and the plan was even exceeded. The server part was rewritten in slightly more common C ++ using nginx as the kernel. And to compress the pages, instead of the old code, we decided to use the open source library PageSpeed Optimization . Thanks to this, our Turbo mode has learned to minify CSS / JS / HTML, and not just compress. Although something added from myself. For example, converting heavy animated gifs to WebP. They didn’t start producing bicycles on the client and, to the maximum, used the code already existing in Chromium, which is responsible for communication with Data Reduction Proxy (this is a Google server, where content compression also takes place). It was only necessary to make friends this code with video compression and other functions of Yandex. Browser.
But the most pleasant thing is that the connection between the browser and the server now works over HTTP / 2. This includes traffic encryption, stream prioritization, and server push support for critical resources (by the way, they helped the Chromium project with them in due time).
Secure wifi
The issue of encryption was resolved (and at the same time we updated the entire content compression technology). This protected our users' HTTP traffic from interception and DNS spoofing (HTTPS is protected by a certificate without us). But we did not stop there, because we had a more specific goal. Remember the wifi protection?
From the very beginning of this story, we wanted to protect user data, but not to interfere with it, i.e. work without any optimization or compression. Therefore, at the stage of restructuring Turbo, we added a special mode “without compression” “under the hood”. If it is activated, all HTTP traffic will go encrypted through our proxy server, but the content itself will not be changed. But this is not enough.
We taught the browser to analyze the connection and enable secure WiFi only when it is really needed. Modern encryption using the WPA and WPA2 protocols is quite reliable. What can not be said about WEP or those points that do not require a password at all. For them, the secure WiFi mode will be turned on automatically. Connection verification will be performed again each time one of the following changes: IP, router's Mac address, ESSID. By the way, the check includes intranet detection as well, in order not to try to send traffic through a proxy without going online.

Protecting WiFi from interception is now available in Yandex Browser for Windows, OS X and Android . Our team continues to refine it now, so your feedback would be very helpful.
Yandex. Browser on ZeroNights
We understand that it is impossible to work on security in an isolated environment. Therefore, soon Yandex. Browser will be available to search for errors and vulnerabilities in a special contest. It will be held in conjunction with the organizers of the conference ZeroNights, which traditionally attracts experts in the field of security. Winners will receive cash prizes. Follow the news!
Source: https://habr.com/ru/post/267013/
All Articles