Outbound mail routing using Cisco ESA

In some cases, it is necessary to make mail routing based on the sender. The English term for this task is Sender Based Routing. This task can be solved in different ways: various external relays for the mail server, special agents in case of using MS Exchange (for example, Sender Based Routing Agent for Exchange Server), etc. In this article, I wanted to share a solution to the problem using Cisco Email Security Appliance tools (hereinafter ESA) - the former IronPort ESA.
The task of Sender Based Routing is relevant when you need to use multiple sender / recipient domains on the same mail server. And it is relevant for the following reason. The vast majority of anti-spam systems check for the presence of a PTR record for the sender's IP address. For one IP-address it is extremely not recommended to have several PTR-records. Therefore, emails from each domain of the mail server must be sent from its own IP address, for which there is a single PTR record. Otherwise, it is likely that the anti-spam system on the recipient side will drop the message. This is where the question arises: how can you scatter letters from one mail server to different IP addresses (in particular, send via different Internet providers) based on the sender's domain?
In my specific example, the task was set as follows: you need to send letters of a specific MS Exchange domain from the IP address of a third-party provider. In other words, on the MS Exchange server it was supposed to use a new additional domain of senders / recipients, letters from which should be sent from the IP address of a remote office located in another country.
')
In the central office where the MS Exchange server is located, ITU uses the Cisco ASA to access the Internet. At a remote office, there is also a Cisco ASA. Between offices, VPN Site-to-Site is configured using IPsec technology.
The approximate scheme of sending letters is presented below:

Emails from the @ abc.ru domain should be sent via the local ISP Main ISP from address 1.1.1.1, emails from the @ xyz.ru domain should go through the VPN to the remote office and access the Internet via the local ISP Remote ISP there with the address 9.9.9.9. In this article, the construction of a VPN Site-to-Site on the Cisco ASA and the organization of access to the Internet through a remote provider will not be considered, as this topic is described in detail both in the official documentation on cisco.com and in numerous forums.
Initially, in this customer's network, Cisco ESA was used exclusively as an anti-spam solution. Through Cisco ESA passed only incoming correspondence. Mail is sent to bypass the Cisco ESA: the MS Exchange server sent letters directly to where the default gateway points, i.e. on Cisco ASA in our case.
Just want to note, in the organization of incoming mail for the domains @ abc and @ xyz there is no trick. It is enough to publish the MX record for @ abc under the address of the main provider (Main ISP), the MX record for @ xyz under the address of the remote provider (Remote ISP) and correctly configure the routing and publishing of the Cisco ESA.
In the example being described, a Cisco ESA has already been deployed in the customer's infrastructure, which can be used as an external relay for outgoing mail. Therefore, first of all, I wondered if it would help solve the problem of Sender Based Routing? As it turned out - yes. This task can be solved using outgoing mail filters on the ESA - Outgoing Content Filters:
Cisco ESA allows you to configure the filter so that certain emails are sent from a different IP address. The screenshots below show the Outgoing Content Filters setting:
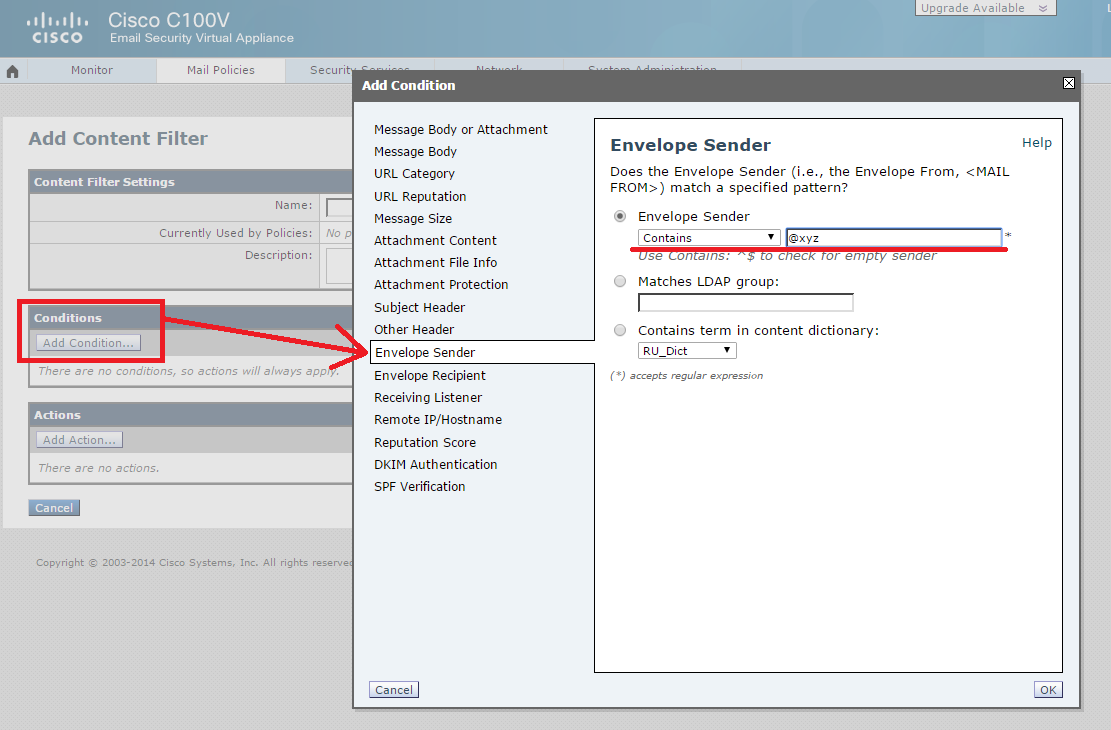
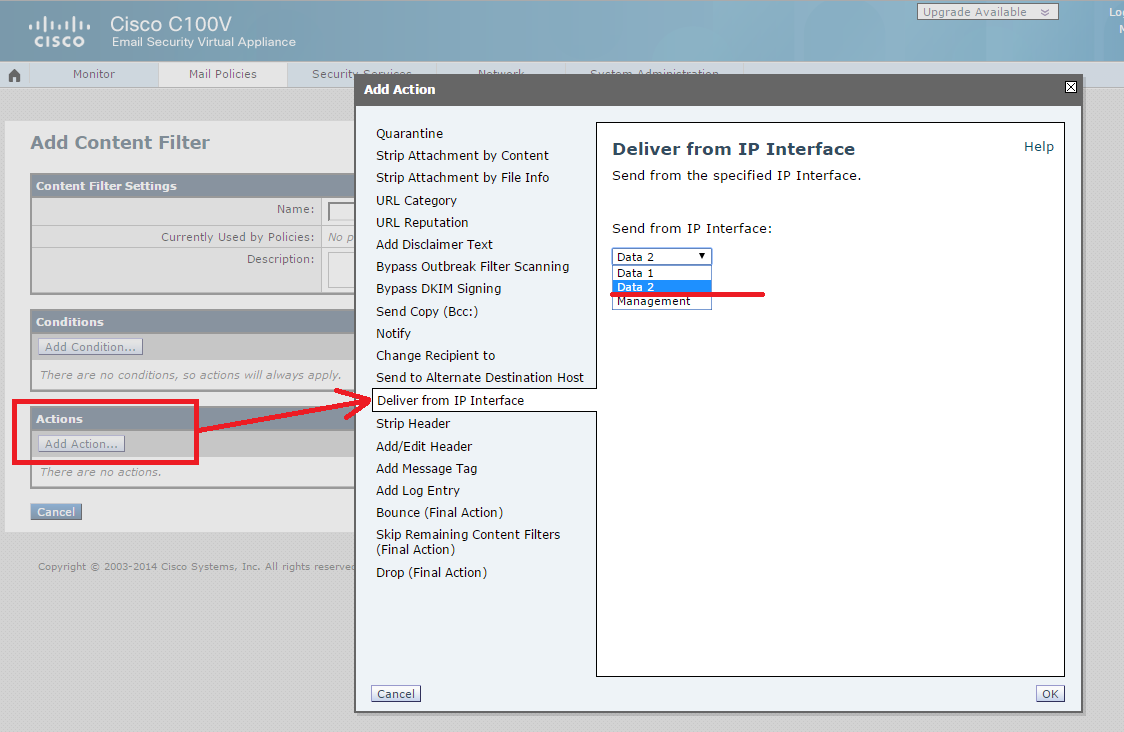
As you can see from the first “Add Condition” screenshot, the Cisco ESA provides a wide choice of letters for applying the required action to them (from the “Add Action”). Moreover, you can create sets of conditions and apply AND or OR logic to them. To solve my problem, it was enough to specify in the condition that the field MAIL FROM letters contained the phrase @ xyz. You must specify Deliver from IP Interface as the “Add Action”, and select the second (not yet used) Cisco ESA interface with a different IP address. This interface is called Data 2. It remains only to save the created filter under the name, for example, Redirect-Filter, and apply the created filter to the default policy for outgoing emails in the Outgoing Mail Policies section:
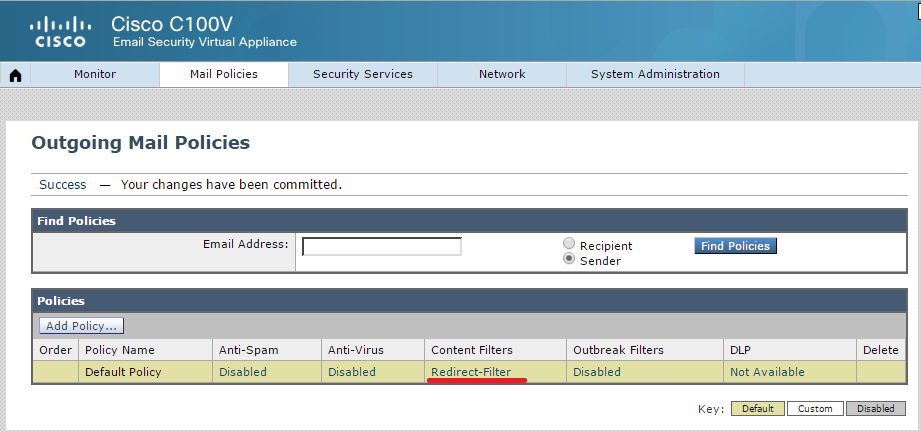
Thus, we managed to configure Cisco ESA so that letters from the @ xyz domain are sent from the IP address of the Data 2 interface, while letters from the @ abc domain will be sent to the IP addresses of the first interface - Data 1. To it was sent letters through Cisco ESA, you need to remember to specify the MS Exchange IP addresses in the RELAYLIST of the HAT (Host Access Table) table:
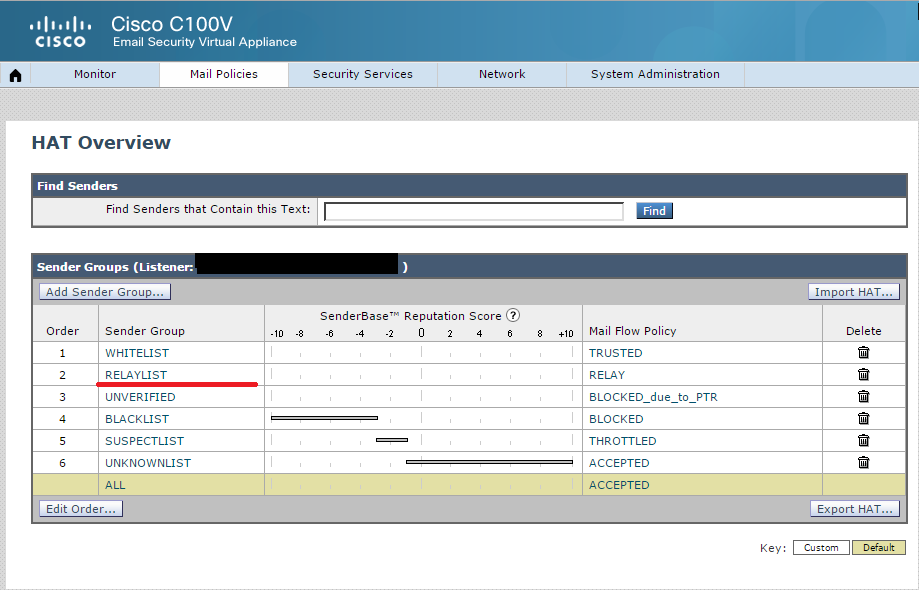
It remains to configure MS Exchange to send all emails via Cisco ESA (specify Cisco ESA as Smart Host) and configure VPN between offices to encrypt traffic between the Cisco ESA Data 2 IP address (from which @ xyz domain letters are sent) and the Internet. In fact, in the Cisco ASA settings, you need to add the IP address of the Data 2 interface to the appropriate crypto access-list and, if necessary, correct the NAT rules.
Thus, in this article we looked at a specific example of how Cisco ESA can be used to solve the Sender Based Routing task. The main idea of the proposed solution is to send letters of the first domain from the IP address of the Data 1 interface of Cisco ESA, letters of the second domain - from the IP address of the interface of Data 2. After assigning the letters of different IP addresses, it is possible to route such letters on the network equipment to any convenient and accessible in a way. In the case described, the traffic was routed to Cisco ASA using crypto access-lists, and the packets were wrapped in a VPN tunnel. On routers for this purpose, you can use Policy Based Routing or VRF.
In conclusion, I would like to note that the implementation of the described functionality on the Cisco ESA does not require the acquisition of any additional license. All you need is the usual Cisco Email Security Inbound license, which is required to provide anti-spam features.
The Cisco ESA licensing scheme is described in more detail here:
The Cisco ESA licensing scheme offers three types of licenses: Inbound, Outbound and Premium (Inbound + Outbound), as well as an A-la-Carte license set for opening additional features (Image Analyzer, McAfee additional antivirus, SoureFIRE additional file antivirus - AMP, and etc.). An Inbound license is required to provide anti-spam features. To be more precise, this license opens anti-spam functionality, antivirus (Sophos) and zero-day threat filters (Outbreak Filters). Judging by the name of the license, you might think that an Outbound license is required to send letters through the Cisco ESA. But it is not. To send letters through the Cisco ESA and use Outbound Content Filters, it is enough to have an Inbound license. The Outbound license is only needed to open the email encryption functionality and protect against information leakage (Encryption and Data Loss Prevention). Moreover, the Outbound license, and, therefore, the Premium license, falls into category C3, since these licenses include strong encryption. The importation of such products into the territory of the Russian Federation requires obtaining permission from the FSB, therefore, as a rule, the delivery time of such licenses increases.
Source: https://habr.com/ru/post/266981/
All Articles