Technical support of computer forensics - continued
Start habrahabr.ru/users/uc_itsecurity/topics
It is obvious that all expert systems in their capabilities are not too different from each other. Each has a certain "competitive advantage". For example, EnCase works best with all other systems with RAID arrays, Paraben Commander "understands" the largest number of email programs, and Forensic Toolkit allows a highly qualified specialist to perform some poorly formalized delicate manual operations. Therefore, each user can purchase the system that best suits his needs.
Pure hardware for the production of examinations are not designed to work with the Cyrillic alphabet and therefore are not in high demand on the Russian market. But often used hardware copying discs and blocking records on the hard disk. At the moment, Tableau is the absolute leader in the market for blockers of recording (in Russia, Tableau products are sold strictly through Guidance Software). This company produces blockers for every taste - from luxury models like TD2u (the figures below show this embodied expert dream immediately after unpacking and during use - simultaneously copying a flash drive to a similar drive and hard drive) to “consumer goods” such as the T35 family.
In general, such hardware blockers connect to the computer of an expert via USB 3.0, FireWire or eSATA ports and allow you to securely copy data from hard drives (IDE, eSATA, SATA and notebook), flash drives and memory cards.
In order to ensure compliance with procedural requirements, computer technical expertise should be conducted in five stages:
• Examination of the computer is turned off. At this stage, the integrity of the seals or seals is checked, these seals are photographed, after which the computer case is opened, the computer’s internal device is inspected and photographed. At this stage, the presence of hardware “bookmarks” on the examined computer is also detected, intended to destroy information on the hard disk in the event of unauthorized turning on of the computer.
• Download a trusted operating system on a computer under test or dismount a hard disk and connect it to an expert computer through a write lock. Creating an image of the investigated hard disk on the computer expert.
• Booting the BIOS subsystem on the computer being examined. At this stage, the hardware configuration of the computer under investigation and the set system time are monitored.
• Examination of the disk image using the appropriate tools.
• Interpretation of results and preparation of conclusions.
When the investigated hard disk is connected to the expert’s computer, an image of this hard disk is created on the expert’s computer. This operation is also desirable with the help of appropriate tools. In the case of using system-wide software, such as Symantec Ghost, an expert faces the problem of proving the immutability of the disk image during the production of expertise. To do this, you will have to either use expensive means of protection against unauthorized access, significantly reducing the performance and usability of the system. Specialized software automatically divides the disk image into portions and each of them signs with a digital signature. After that, if the digital signature of one or several fragments turns out to be incorrect during the examination, these fragments are simply excluded from the studied materials or the image is re-created from the source disk.
As a tool for creating a disk image, you can use, for example, the Paraben Forensic Replicator program. First, the investigated hard disk is connected via the write lock to the computer of the expert, then the program is started, and the appropriate item is selected in the menu:

Then the expert selects the physical disk from which to remove the image:

')
Now it remains only to choose a place for the image file and the save option:
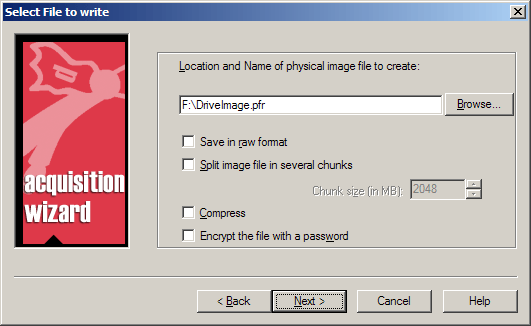
After entering the service report headers, the image itself is created. At the end of the program, the image is ready for study:

It is obvious that all expert systems in their capabilities are not too different from each other. Each has a certain "competitive advantage". For example, EnCase works best with all other systems with RAID arrays, Paraben Commander "understands" the largest number of email programs, and Forensic Toolkit allows a highly qualified specialist to perform some poorly formalized delicate manual operations. Therefore, each user can purchase the system that best suits his needs.
Pure hardware for the production of examinations are not designed to work with the Cyrillic alphabet and therefore are not in high demand on the Russian market. But often used hardware copying discs and blocking records on the hard disk. At the moment, Tableau is the absolute leader in the market for blockers of recording (in Russia, Tableau products are sold strictly through Guidance Software). This company produces blockers for every taste - from luxury models like TD2u (the figures below show this embodied expert dream immediately after unpacking and during use - simultaneously copying a flash drive to a similar drive and hard drive) to “consumer goods” such as the T35 family.
In general, such hardware blockers connect to the computer of an expert via USB 3.0, FireWire or eSATA ports and allow you to securely copy data from hard drives (IDE, eSATA, SATA and notebook), flash drives and memory cards.
In order to ensure compliance with procedural requirements, computer technical expertise should be conducted in five stages:
• Examination of the computer is turned off. At this stage, the integrity of the seals or seals is checked, these seals are photographed, after which the computer case is opened, the computer’s internal device is inspected and photographed. At this stage, the presence of hardware “bookmarks” on the examined computer is also detected, intended to destroy information on the hard disk in the event of unauthorized turning on of the computer.
• Download a trusted operating system on a computer under test or dismount a hard disk and connect it to an expert computer through a write lock. Creating an image of the investigated hard disk on the computer expert.
• Booting the BIOS subsystem on the computer being examined. At this stage, the hardware configuration of the computer under investigation and the set system time are monitored.
• Examination of the disk image using the appropriate tools.
• Interpretation of results and preparation of conclusions.
When the investigated hard disk is connected to the expert’s computer, an image of this hard disk is created on the expert’s computer. This operation is also desirable with the help of appropriate tools. In the case of using system-wide software, such as Symantec Ghost, an expert faces the problem of proving the immutability of the disk image during the production of expertise. To do this, you will have to either use expensive means of protection against unauthorized access, significantly reducing the performance and usability of the system. Specialized software automatically divides the disk image into portions and each of them signs with a digital signature. After that, if the digital signature of one or several fragments turns out to be incorrect during the examination, these fragments are simply excluded from the studied materials or the image is re-created from the source disk.
As a tool for creating a disk image, you can use, for example, the Paraben Forensic Replicator program. First, the investigated hard disk is connected via the write lock to the computer of the expert, then the program is started, and the appropriate item is selected in the menu:

Then the expert selects the physical disk from which to remove the image:

')
Now it remains only to choose a place for the image file and the save option:

After entering the service report headers, the image itself is created. At the end of the program, the image is ready for study:

Source: https://habr.com/ru/post/266663/
All Articles