Published exploit code for critical Android vulnerabilities Stagefright
In the spring of 2015, researchers discovered a number of critical vulnerabilities in the core component of the Android mobile OS called Stagefright (a library for working with multimedia files, such as PDF). Security errors allowed attackers to remotely access the smartphone, for example, by sending a malicious MMS message - to conduct such an attack, you only need to know the victim's phone number.
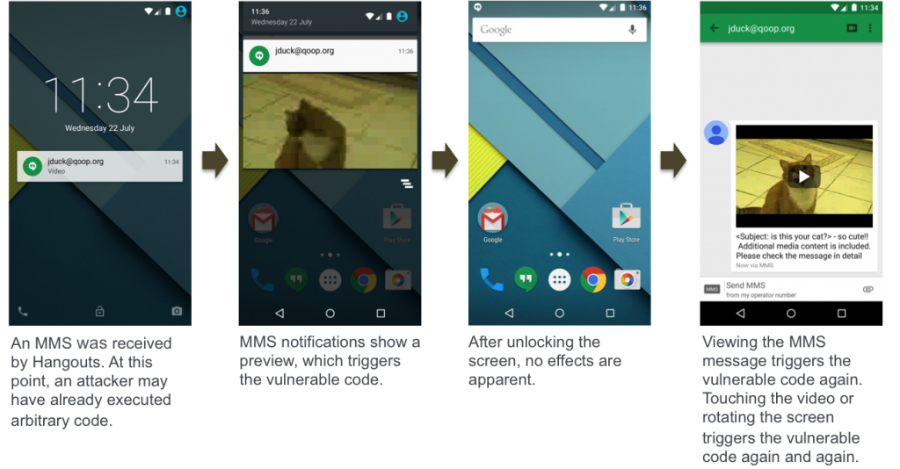
An exploit code has been published this week using security bugs in the Stagefright component. These vulnerabilities were discovered by researchers at Zimperium, who described the attack on her blog using a specially crafted exploit.
')
The researchers passed on vulnerability information to OS developers in April and May 2015. Since then, Google experts have worked on security fixes, which are then transmitted to partners (including manufacturers of smartphones), but have not yet been able to solve the problem until the end.
For example, released patches for Hangouts and Messenger block only the attack described in the Zimperium blog using a malicious MMS message, leaving room for other smartphone hacking scenarios - for example, using a link leading to the site containing the exploit. In addition, some patches were so poor-quality that attackers could still exploit the vulnerabilities even after they were installed (for example, CVE-2015-3864 ). According to security researchers, even a Nexus 5 device with all the patches currently available is still vulnerable to attacks.
The difficulty with fixing security bugs prompted Google to ask researchers from Zimperium to postpone the publication of a proof-of-concet-exploit code, but on September 9, the company posted it on its blog.
The Python script generates an MP4 format media file that exploits the CVE-2015-1538 vulnerability and provides the attacker with access to the device. Then the attacker can remotely take photos or listen to the audio through the microphone of the smartphone. Due to the introduction of new protection mechanisms, the exploit does not work for the new version of Android 5.0.
Zimperium researchers were not the only ones who discovered vulnerabilities in the Stagefright component. A 36-year-old Moscow researcher Yevgeny Legerov also discovered two zero-day vulnerabilities in this component. Google has released a series of patches for partners ( one , two , three ) that fixes vulnerabilities found by Legerov.
At conferences on information security, Positive Technologies researchers also demonstrated the results of a study on the security of 4G communications and SIM cards (they can also be hacked ).
During the Positive Hack Days forum held in May in Moscow, a competition was also held on hacking MiTM Mobile mobile communications - we published an analysis of its tasks in Habré (some event attendees received reports about hacking their devices). The link presents a webinar entry on this topic.

An exploit code has been published this week using security bugs in the Stagefright component. These vulnerabilities were discovered by researchers at Zimperium, who described the attack on her blog using a specially crafted exploit.
')
The researchers passed on vulnerability information to OS developers in April and May 2015. Since then, Google experts have worked on security fixes, which are then transmitted to partners (including manufacturers of smartphones), but have not yet been able to solve the problem until the end.
For example, released patches for Hangouts and Messenger block only the attack described in the Zimperium blog using a malicious MMS message, leaving room for other smartphone hacking scenarios - for example, using a link leading to the site containing the exploit. In addition, some patches were so poor-quality that attackers could still exploit the vulnerabilities even after they were installed (for example, CVE-2015-3864 ). According to security researchers, even a Nexus 5 device with all the patches currently available is still vulnerable to attacks.
The difficulty with fixing security bugs prompted Google to ask researchers from Zimperium to postpone the publication of a proof-of-concet-exploit code, but on September 9, the company posted it on its blog.
The Python script generates an MP4 format media file that exploits the CVE-2015-1538 vulnerability and provides the attacker with access to the device. Then the attacker can remotely take photos or listen to the audio through the microphone of the smartphone. Due to the introduction of new protection mechanisms, the exploit does not work for the new version of Android 5.0.
Zimperium researchers were not the only ones who discovered vulnerabilities in the Stagefright component. A 36-year-old Moscow researcher Yevgeny Legerov also discovered two zero-day vulnerabilities in this component. Google has released a series of patches for partners ( one , two , three ) that fixes vulnerabilities found by Legerov.
At conferences on information security, Positive Technologies researchers also demonstrated the results of a study on the security of 4G communications and SIM cards (they can also be hacked ).
During the Positive Hack Days forum held in May in Moscow, a competition was also held on hacking MiTM Mobile mobile communications - we published an analysis of its tasks in Habré (some event attendees received reports about hacking their devices). The link presents a webinar entry on this topic.
Source: https://habr.com/ru/post/266581/
All Articles