A variety of network security tests: a review of IXIA solutions

Constantly developing and new attacks are aimed at finding yet to be found holes in the network security system. Traditional penetration tests or synthetic attacks are outdated and impractical. We need a flexible architecture that can cope with the onslaught of dynamic attacks, and be able to quickly recover the attacked network, and it is best to find gaps in IT before the attacks. Evaluate the protection of various components of the network infrastructure allows the concept proposed by IXIA .
Review of her approach to such load tests, as well as the case of application under the cut.
')
The main idea of the IXIA approach is a comprehensive assessment of the capabilities of security systems. The only tool for this is testing and analyzing the response of the system in real conditions of the IT system.
This requires solving the following tasks:
• evaluation of the effectiveness of the declared protection functions of the implemented security devices (UTMFirewall, IDS / IPS, DPI, WebApplicationFirewall, LoadBalancer, LawfulInterceptionSystem, DDoSProtector, SSLAccelerator);
• configuration optimization - whether devices are properly configured on the network;
• performance comparison on benchmark tests and in real conditions.
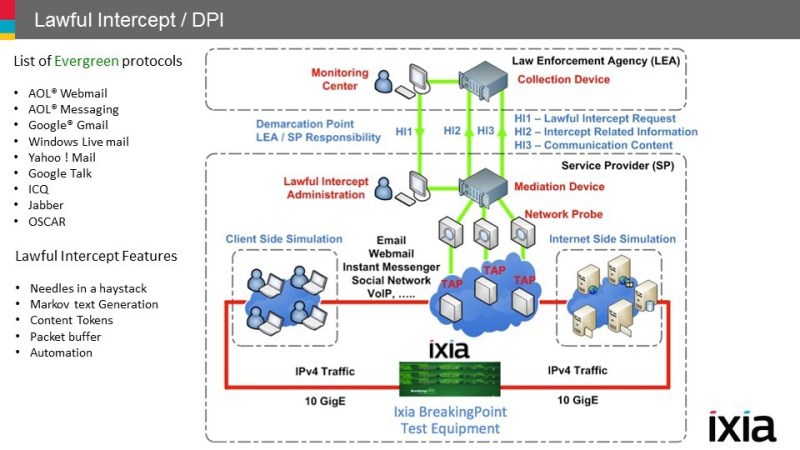
Evaluation of equipment
The first thing to do before purchasing safety devices is to make sure that their specifications comply with the supplier’s specifications. The IXIA BreakingPoint solution can analyze the hardware protection functionality. When using this solution, independent of the manufacturers, you can experimentally verify this.

The only objective way to evaluate the device is to test it in a real customer network. After all, often the stated numbers are characteristics in “ideal” conditions, which has nothing to do with a similar situation under real load.
If the equipment offered by the supplier does not meet the required characteristics, you can use the information obtained to purchase solutions that meet the security requirements of your network.
Device Configuration Optimization
Many organizations invest huge amounts of money in high-tech IT systems for business: using cloud technologies, increasing application performance, implementing mobile solutions. At the same time, there are practically no guarantees of network performance or flexibility. The complexity of the interaction of various systems makes it even more difficult to optimize security measures and also reduce the network's flexibility. The introduction of a new solution requires mandatory testing and determining the most appropriate configuration. In this case, the optimal settings, as a rule, will require a series of cyclical tests.
IXIA BreakingPoint allows you to create real user traffic at any speed to accurately determine how the equipment behaves after installation in the system.

This system allows you to work simultaneously as a client and a server, generating clean traffic along with threats and performing critical measurements of signal transit time in both directions, delays and throughput.
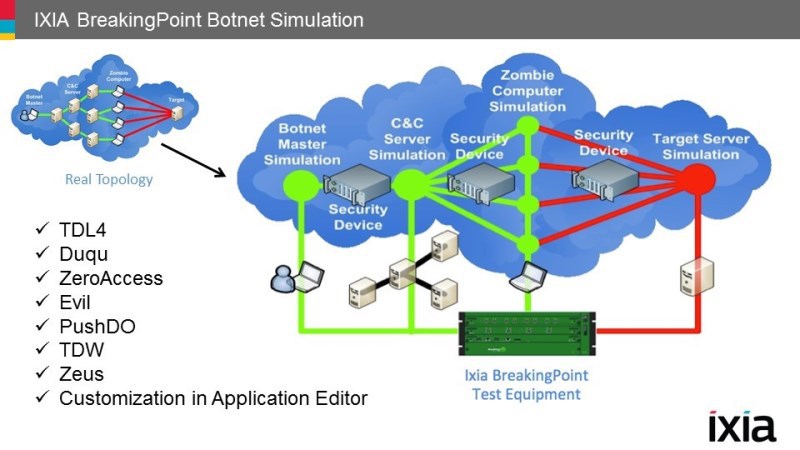
You can also run tests on individual devices or on the entire network, optimize the configuration, and then rerun the same test to make sure the network is secure.

IXIA BreakingPoint will help security professionals fine-tune protection: from hardware selection and network design to upgrading and modeling potential threats to determine readiness. Evaluating the response to DDoS attacks and readiness for attacks, networks as security tools develop reduces the risks for companies.
The priority task of testing is to optimize the components of the entire network. BreakingPoint uses a variety of tests for:
• Interaction - will help close the gaps and ensure the interaction of components of a network of different vendors
• Intentional change - performing targeted data changes to detect protocol implementation errors, as well as assessing how these vulnerabilities can be exploited by hackers
• Detection of known vulnerabilities - an extensive set of tests to verify the readiness of security devices
• Performance — Determining the maximum performance of devices, applications, and the entire network under actual conditions and overload conditions (for example, denying access to new users, periods of slowing down, failures, etc.).
Performance issue
No less important is the third task. It is necessary to carry out reference tests of the selected device, technology and configuration after installation on the network and before launch. If you do not conduct such a test, there will be a false sense of security, the result of which can be serious consequences.

Pre-deployment testing prevents the launch of network components with vulnerabilities that have been missed. Also, you can determine how the information security solution works already being part of the network. Such tests help to compare the declared performance indicators with those after the launch. When upgrading the network or changing the configuration, you can determine how much the performance differs before and after. Even a software update can fix one problem while creating another.
Frames decide everything
Many organizations and government institutions in response to the challenges of growing cyber threats install firewalls, intrusion prevention systems and other means of protection.

Effective infrastructure protection is the result of the interaction of automated systems and qualified specialists. Therefore, another vector of the IXIA approach to security is the implementation of solutions to improve the competence of information security professionals.
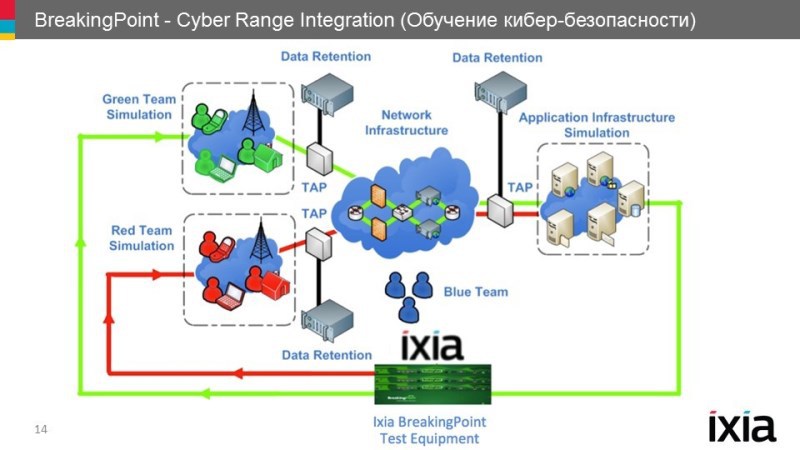
The human factor is the most important element in countering cyber threats, so you need to invest wisely in your employees. It is necessary to combine small cyber-training grounds and standardized training in order to provide the real experience necessary for real skills of information security specialists.
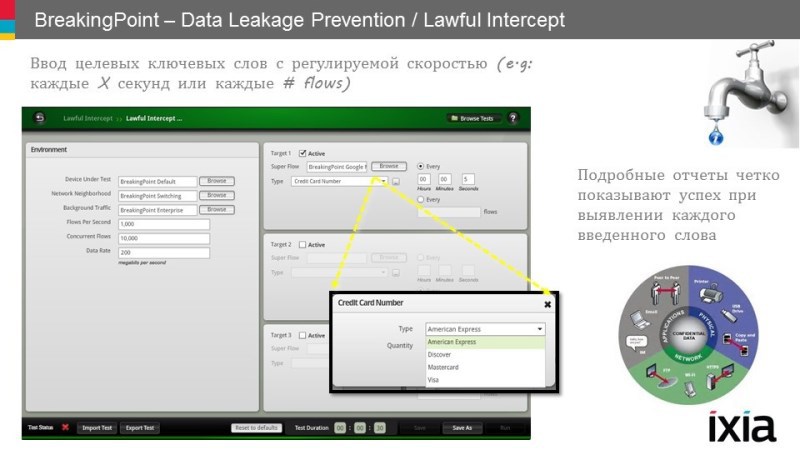
Traditional cyberpolygons require serious investments in equipment and personnel, but even this does not guarantee results. IXIA BreakingPoint can help you test and train without a fast-aging test bench. IXIA offers training based on the capabilities of staff and training for company personnel in solving real-world information security tasks.
ATI service
Ready-made test suites of typical scenarios are available, including a test of information interception systems, which significantly reduce the testing time.
Users can quickly run complex targeted tests for 30 seconds using more than 3,000 ready-made ATI super-flows — real traffic flows that simulate application behavior. An example of such a stream is a Gmail session in which a client goes through all the necessary DNS query sequences, runs a TLS authentication session on the Gmail server, retrieves mail, and closes the session.
In addition to this, an ATI subscription provides testing using real software traffic and support for application protocols. At the same time, each protocol is configured and dynamic content of the applications is repeated, the network conditions under which the data flows change as well as real ones.

Advantages of IXIA Solutions
IXIA offers customers the technology, experience and learning opportunities needed to enhance protection and ensure information security systems. Products of the company allow:
• Perform load tests of the network, applications, equipment on information security not in ideal conditions, but within the working network
• Identify the weaknesses of the security solutions used and eliminate them;
• Improve the skills of employees in repelling attacks and eliminating their consequences;
• Improve readiness to repel attacks;
• Evaluate whether the equipment is in compliance with the stated specifications before purchasing it
• Reduce the cost of information security and improve infrastructure performance
IXIA testing capabilities table for various IT environments
| Applications | Storage | Network | Security |
| · Application Load · Application security · Server power · Contact center · VoIP · DC Migration Plans · Video services | · NAS, SAN and cloud storage capacity · Cash stress test · Deduplication · Compression · Backup and restore | · Application delivery · LTE EPC testing · Mobile transport network · Wireless LAN controller · Firewall · Session Border Controller · IPv6 Ready | · NGFW · DDoS protection · Data interception systems, DLP, IPS · VPN · Antivirus and antispam · Countering cyber threats |
Line of devices
| PerfectStorm ONE device 1 / 10GE |  | The 8-port 1GE / 10GE SFP + model with application bandwidth from 4 to 80 Gb / s, bandwidth and hardware are flexibly licensed. |
| PerfectStorm ONE device 10 / 40GE |  | Model with 2 40GE QSFP + ports and support for 8 10GE SFP + ports in branching mode, 80 Gb / s application bandwidth per device. |
| XGS12 12-slot chassis (11 RU) |  | Ixia's latest chassis technology, offering a test system with the industry's highest density of Ethernet ports. The device provides the power required for high-performance testing applications 4-7 levels. The XGS12-HS chassis supports IxLoad and BreakingPoint applications on PerfectStormFusion modules. |
| 8 - port 10GbE module PerfectStorm |  | Generates up to 80 Gbit / s application traffic (960 bps on XGS12 chassis) for wired and wireless 10 Gbps networks. Provides 8 10GE SFP + ports. |
| 2 - port 40GbE modulePerfectStorm |  | Generates up to 80 Gbit / s application traffic (960 bps on the XGS12 chassis) for wired and wireless 40 Gigabit networks. Provides 2 40GE QSFP + ports. |
| 1-port 100GbE modulePerfectStorm |  | Generates up to 80 Gbit / s application traffic (960 bit / s on XGS12 chassis) for wired and wireless 100 Gigabit networks. Provides one 100GbE CXP + port. |
| BreakingPoint Virtual Edition software package |  | Scalable solution for generating real-world applications and attacks for deployment in a virtualized environment. |
Case of application of load tests IXIA on the stock exchange (USA)
Case Description
The client (the stock exchange in the USA) was concerned about the increasing frequency of DDoS attacks, and wanted to understand how effective the DDoS protection was for their provider (the client spent almost 225 thousand per month).
It was a successful project, which improved the overall level of client cybersecurity and network readiness for attacks and prevented the main exchange services from failing, as well as increased the speed of DDoS protection of the network.
Technical details
IXIA conducted tests on Sunday morning, warning about the FBI tests - they very much wanted to know the test results, since the transactions on this exchange are key for the American and world economy.
The client called the ports through which they communicate with the outside world; tons of traffic were sent to their main transactions, which the provider monitored.
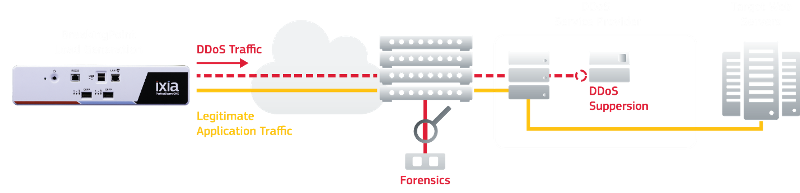
Introductory for stress tests were given by the client. Engineers made 3 main types of test attacks that the client complained the most about.
The attacks were of three types:
- Syn Flood
- Slowloris attack
- Excessive Get
Such IP addresses were involved. The first address pool included attack targets — you can access them from anywhere. In the second pool of addresses, applications were allowed to run.
The following addresses were tested:
205.209.196.38
205.209.196.39
205.209.196.60
205.209.196.20
205.209.196.9
205.209.196.10
205.209.196.51
Attack address
208.97.218.15
Address to run applications
208.97.218.100-254
Default route
208.97.218.1
Client: - we increased the number of SYN requests to 14,000 per second, then attacked the IP addresses at a constant speed of 7,450 SYN per second, and then returned to the original value of 14,000 - that was enough for DDoS protection to detect the SYN - flood attack.
As a benchmark, the load balancer has set the SYN request level to 150,000, which means that the total number of SYNs per second provided for all virtual servers must reach 150,000 requests before they enable their protection mechanisms. The vendor of the presented balancer recommended setting a certain level of operation for each virtual server, as in this case they will be more efficient. Depending on the environment, they could set a response threshold of 3,000 to ensure that single servers do not receive a DDoS attack when the limit for the entire platform is 30,000 (if we have, for example, 10 virtual servers).
As soon as the client provider reached a threshold below 14,000 synes per second - which is an indication of the attack, the engineers would be able to exceed the threshold to see if protection would work or not.
Test results
- The protection response rate was reduced from 50 minutes at the beginning of the tests to 5 minutes.
- Prevention of interruptions in work, which could lead to enormous financial losses, and even greater image losses.
- The overall level of preparedness for future attacks and the security of the IT infrastructure of the financial exchange improved.
- It took about 15 seconds in the test to find out that there was a huge attack on 2 external routers that were ready to “fall” as a result of the attack. The tests did not use as much bandwidth as possible, but were based on data about real attacks on the client. Because of the tests, there were certain irregular configurations of routers that no one would ever know until it was too late. And they would really be attacked if the IXIA hadn't tested.
- Another important test result was that the exchange could check, among other things, the smooth functioning of the reaction processes of the responsible employees to the threat.
- The first time the engineers launched the test, the customers did not tell their protection vendor, and only a few Exchange employees knew about the attack tests. Despite the fact that employees had clear instructions in case of an attack, the response time took about 50 minutes before the “alarm was raised”: considering all internal approvals of all responsible persons, as well as the IT security provider. All these people had to decide that it was necessary to “sound the alarm” with the provider so that it would cut off all incoming traffic.
- For the second test, the client reduced the response time to 15 minutes, and in the third test - 5 minutes. It was a good fire brigade training!
With the entire line of equipment NTS IXIA can be found here.
BreakingPoint virtual performance here
For questions about IXIA decisions contact: dcs@muk.ua.
Distribution of IXIA solutions in Ukraine , Belarus , CIS countries .
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/266533/
All Articles