Cyberband Carbanak returns with a new arsenal of malware
Last year, the banking malware Carbanak made a lot of noise in the media, its analysis was published by Group-IB and Fox-IT, as well as Kaspersky here and here . Both reports covered a malware that a cyberband had stolen several hundred million dollars from various financial institutions. Shortly before the release of our report, security company CSIS published details of the analysis of new Carbanak samples that they were able to detect.

Cyberband activity is interesting not only from the point of view of the stolen amount, but also from the technical point of view. Its distinguishing feature is the fact that the gang is already acting as a mature APT group, purposefully infecting a large number of computers and deriving actual benefits from it. She specializes in compromising large financial institutions, as well as other institutions. Our analyst Anton Cherepanov ( @ cherepanov74 ) analyzed the activities of Carbanak.
')
Casino Compromise in the USA
In late August, we discovered an attempt to compromise the internal casino network, which is located in a hotel in the USA. The infection vector could be a phishing message with a malicious attachment in the form of an RTF exploit or a .SCR file. The main task of the attackers was to compromise the PoS servers that were used to process financial payments.
The attackers have adapted a small open source backdoor called Tiny Meterpreter for their own purposes. Some changes have been made to introduce malicious code into the svchost.exe system process.
The backdoor dumps executable files of two different malware onto the disk.
As was pointed out in a study of our colleagues from antivirus company TrendMicro, the Carbanak malware is focused on compromising Epicor / NSB PoS systems, while the Win32 / Wemosis backdoor is PoS RAM Scraper. PoS RAM Scraper is a module that specializes in copying a portion of the virtual memory of a legitimate process in order to search for numbers and other credit card information. The Wemosis backdoor is written in Delphi and allows an attacker to remotely control an infected system.
Both malware dropped by the Tiny Meterpreter backdoor is signed with the same digital certificate.
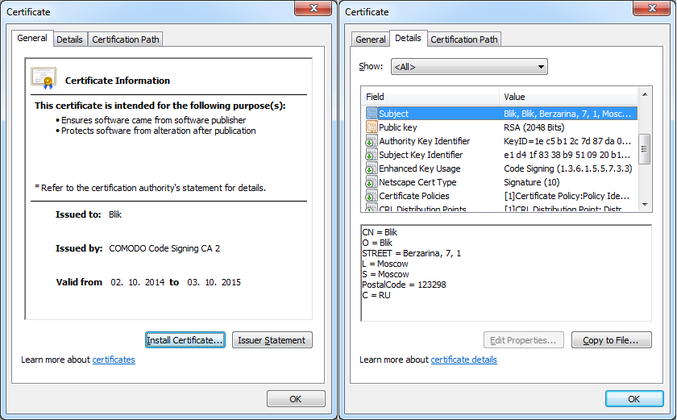
Fig. Information about the digital certificate that was used to sign the modules of the cyberband of Carbanak.
Certificate Information:
Company name: Blik
Validity: from 02 October 2014 to 03 October 2015
Thumbprint: 0d0971b6735265b28f39c1f015518768e375e2a3
Serial number: 00d95d2caa093bf43a029f7e2916eae7fb
Subject: CN = Blik
O = blik
STREET = Berzarina, 7, 1
L = Moscow
S = Moscow
PostalCode = 123298
C = RU
This certificate was also used to sign the executable file of another Win32 / Spy.Agent.ORM malware family that was used by the Carbanak cyber gang.
Win32 / Spy.Agent.ORM malware review
The Win32 / Spy.Agent.ORM malware (aka Win32 / Toshliph) is a Trojan that was used by the cyberband as a first-level payload. The threat executable was signed by the above digital certificate. In addition, the trojan has common code characteristics with the malware of the cyberband, which they used in their malicious campaigns regularly.
In fact, the Win32 / Spy.Agent.ORM malware family is already known to the public. In July 2015, security company Cyphort reported on the compromise of the news portal rbc.ua and the banking website unicredit.ua. As a result of the investigation, it was found that the compromised websites distributed using the Win32 / Spy.Agent.ORM exploit kit. Another company, Blue Coat, also reported on a phishing e-mail that was sent to employees of the Central Bank of Armenia. The mailing list was used to distribute Win32 / Spy.Agent.ORM.
We recorded an increased activity of this modification of the malware family at the beginning of the summer of 2015, after which we began to monitor its activity. We also observed cyber attacks on users using this malware in Russia and Ukraine. Phishing emails were sent to users with malicious attachments of .SCR files or .RTF exploits. Below is an example of a phishing message that was sent to an employee of one of the largest companies engaged in trading on the Forex market.
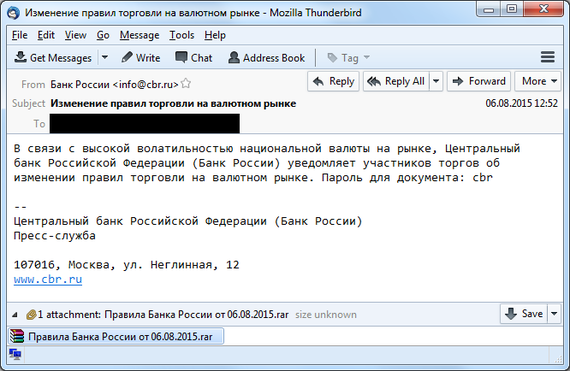
Fig. An example of a phishing email message with a malicious program.
Below are the names of the files from the various phishing messages of this malicious campaign.
“ALFA-BANK” JSC CONTRACT.scr ”
"The list of materials for blocking from 04.08.2015g.scr"
“Postanovlene_ob_ustranenii_18.08.2015.pdf% mnogo.pfrelov% ..scr”
"The rules of the Bank of Russia from 06.08.2015.pdf% mnogoproslov% .scr"
All attachments to these letters contain an archive with a .SCR file that is password protected. Files contain icons of applications such as Adobe Acrobat Reader and MS Word.
In other cases, attackers used RTF files with various exploits, including an exploit for one of the latest MS Office vulnerabilities. This is a vulnerability CVE-2015-1770, which was fixed by Microsoft in June 2015 by updating MS15-059. Below are the names of the RTF files that we observed in this malicious campaign.
"Prikaz-451.doc"
"REMITTANCE ADVICE ON REJECTION.doc"
"PROOF OF REMITTANCE ADVICE .doc"
"HDHS739_230715_010711_A17C7148_INTERNAL.doc"
"Անկերի և բանկային գործունեության մասին ՀՀ օրենք 07.27.2015.doc" (Armenian: Law on Banks and Banking Activity 07.27.2015)
"PAYMENT DETAILS.doc"
"ALFA-BANK" JSC AGREEMENT.doc "
"AML REPORTS_20082015_APPLICATION FORM-USD-MR VYDIAR.doc"
Anti-Money Laudering & Suspicious cases.doc
"ApplicationXformXUSDXduplicateXpayment.doc"
"AML USD & Suspicious cases.doc"
“Amendment inquiry (reference TF1518869100.doc”
"Information 2.doc"
Below is an example of a phishing message that was sent to a bank employee in the UAE.
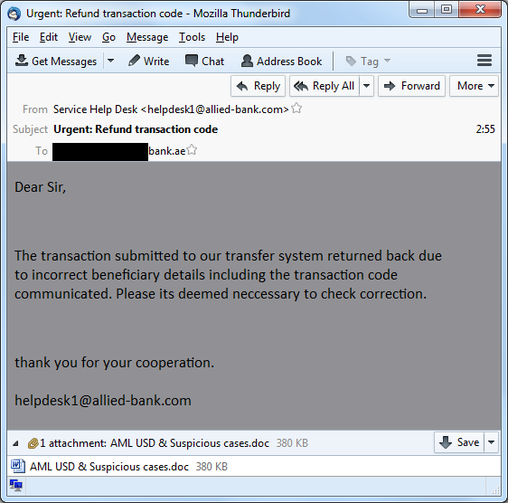
Fig. An example of a phishing message with an RTF file in the attachment.
Below is an example of a phishing message that was sent to a German bank.
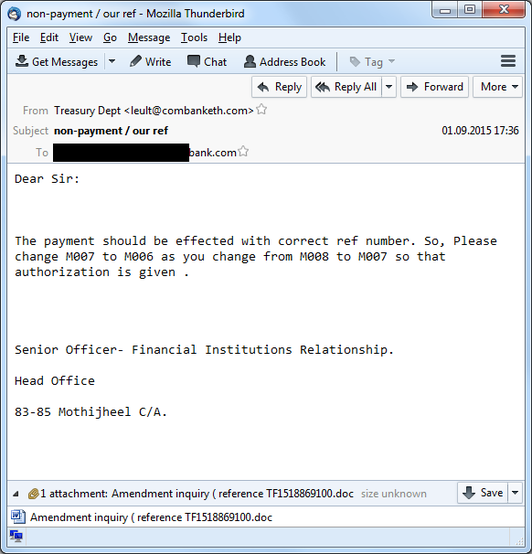
Fig. An example of a phishing message with an RTF file in the attachment.
Win32 / Spy.Agent.ORM Technical Analysis
As we have already indicated, this malware is a simple and small backdoor, which allows attackers to remotely access the victim’s computer. After its launch, the Trojan connects to the C & C server and receives various commands: take a screenshot of the screen, get a list of running processes, get information about the system, get the campaign ID. Based on this information, operators can determine the degree of usefulness of the infected computer, i.e., is this computer one that was of interest to intruders or is it a randomly infected system.
Below is a list of commands that a bot can receive from a C & C server.
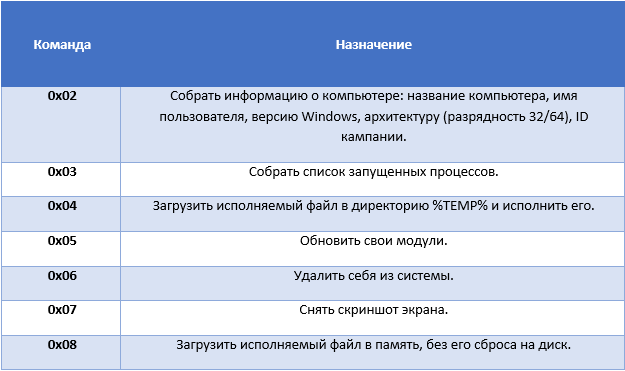
One of the latest samples of this malware family, which was discovered by our anti-virus laboratory, was signed with another digital certificate.
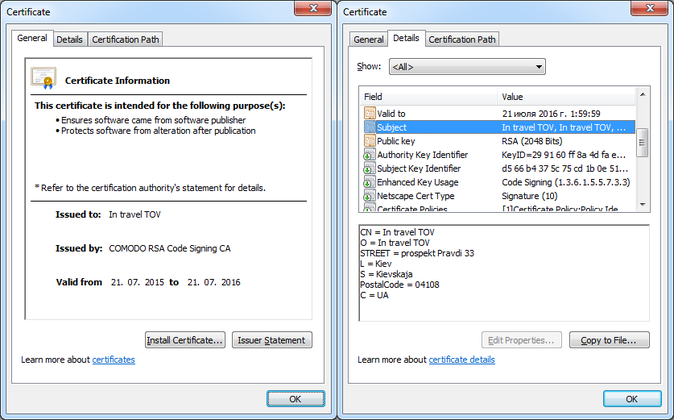
Fig. Information about the digital certificate that signed the malware file.
Certificate data.
Company name: In travel TOV
Validity: from 21 July 2015 to 21 July 2016
Thumbprint: 7809fbd8d24949124283b9ff14d12da497d9c724
Serial number: 00dfd915e32c5f3181a0cdf0aff50f8052
Subject: CN = In travel TOV
O = In travel TOV
STREET = prospekt Pravdi 33
L = Kiev
S = Kievskaja
PostalCode = 04108
C = UA
This latter sample also contains an LPE exploit to gain system privileges in the system and to set itself up as a system service. The exploit relates to the CVE-2015-2426 ( Hacking Team ) vulnerability in the Windows system component Adobe Type Manager Library (ATMFD.dll), which we wrote about here . It has been fixed by updating MS15-078 .
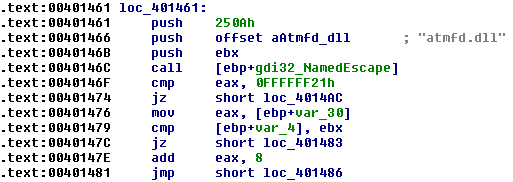
Fig. Part of the exploit code CVE-2015-2426.
The digital certificate for the Blik organization is one of the common features that links Win32 / Spy.Agent.ORM and Win32 / Spy.Sekur (Carbanak). Another common feature is in the malware code, below is an example of such a common function. The function specializes in generating a BOTID value that is unique and is generated based on the hardware parameters of the infected computer.
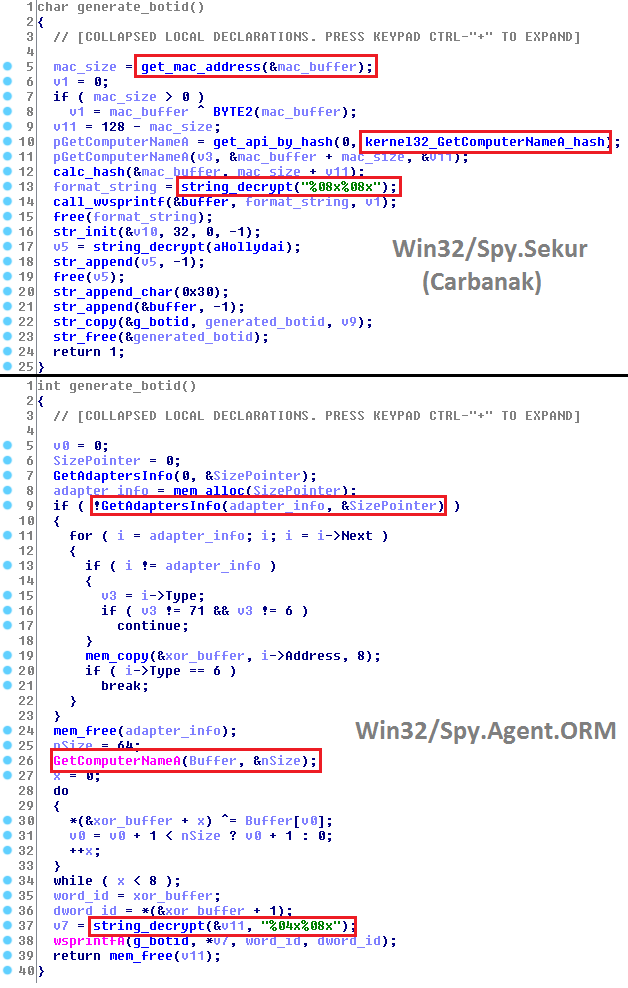
Fig. Similarities in malware code.
The BOTID value is used by attackers to identify the infected computer. In both cases, the value is generated based on the MAC address and computer name, then this value is converted to a string using the well-known wsprintf function.
Sinkhole stats
Using the sinkhole mechanism, we were able to obtain the following statistics on the distribution of this malicious program.
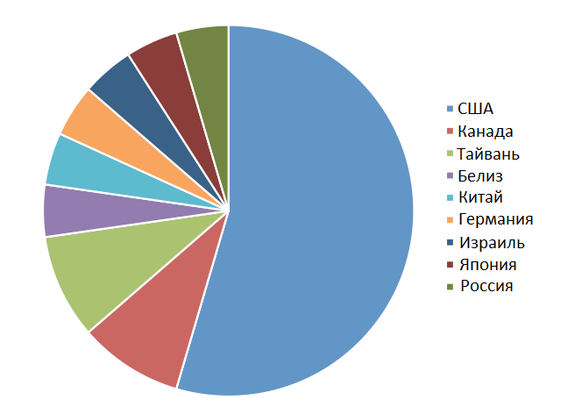
Since the cyber attacks conducted by the gang were highly targeted, the total number of victims was not so great in absolute terms. Victims of malware in the United States are in several states, including Nevada (Las Vegas), California and New York. Compromise exposed various casinos and hotels.
Conclusion
Even after the previous series of successful cyber attacks and theft of hundreds of millions of dollars, the gang or the Carbanak APT group did not want to remain in the shadows and rest on their laurels. On the contrary, it continues its activity and specializes in cyber attacks of its chosen targets, which relate to the banking sector, companies trading in the Forex market, as well as American casinos. We recently discovered Carbanak victims also in the following countries.
As shown above, cyberbanda uses for its purposes not only one family of malicious programs, but also several others. It can be seen that all these malicious programs - Carbanak (Win32 / Spy.Sekur), Win32 / Spy.Agent.ORM, Win32 / Wemosis - are based on different code bases, however, contain some common features, such as digital signatures based on a single certificate.
Cyberband has updated its arsenal with the latest exploits for vulnerabilities such as MS Office RCE CVE-2015-1770 and CVE-2015-2426, which was located in the leaked data from the Hacking Team cybergroup.
We continue to monitor the activities of Carbanak threats. For additional materials on this topic or for sending new malware samples, please contact threatintel@eset.com.
Compromise Indicators (IoC)
Sample IDs of SHA-1 Trojan.Win32 / Spy.Sekur (Carbanak malware)
A048C093C5DA06AF148CA75299960F618F878B3A
3552338D471B7A406D8F7E264E93B848075235C0
3A9A23C01393A4046A5F38FDBAC371D5D4A282F1
8D5F2BF805A9047D58309788A3C9E8DE395469A8
BCF9E4DCE910E94739728158C98578A8D145BE56
8330BC5A3DCC52A22E50187080A60D6DBF23E7E6
E838004A216E58C44553A168760100B497E514E8
CF1F97879A6EB26FEDC7207D6679DFA221DD2D45
7267791340204020727923CC7C8D65AFC18F6F5B
F8CBF647A64028CAE835A750EF3F8D1AA216E46C
33870482BA7DE041587D4B809574B458C0673E94
3927835C620058EFCADF76642489FC13AACE305B
D678BD90257CF859C055A82B4A082F9182EB3437
0B8605D0293D04BBF610103039768CBE62E2FAAE
7A9BE31078BC9B5FECE94BC1A9F45B7DBF0FCE12
SHA-1 RTF exploits
D71E310ADF183F02E36B06D166F8E3AD54FDBCC9
5B6ABA51215A9662987F59AEF6CAE0A9E3A720B8
1AD84A244B7D4FBB4D89D023B21715B346027E49
E8514BF4C4E1F35FB1737C2F28A4A4CED07AA649
68EA12CDCCEE01D50C23EBC29CAA96BF40925DC6
AC95F01487B4F179A1F10684B1E0A5656940A005
B4A94A214FC664B8D184154431E1C5A73CA0AE63
Addresses of C & C servers Trojan.Win32 / Spy.Sekur
weekend-service.com:80
seven-sky.org:80
comixed.org:80
91.207.60.68:80
89.144.14.65:80
87.98.217.9:443
82.163.78.188:443
50.62.171.62:700
31.3.155.123:443
216.170.116.120:80
216.170.116.120:700
216.170.116.120:443
194.146.180.58:80
193.203.48.41:700
185.29.9.28:443
178.209.50.245:443
162.221.183.11:80
162.221.183.11:443
162.221.183.109:443
141.255.167.28:443
104.232.32.62:443
104.232.32.61:443
SHA-1 for Trojan.Win32 / Spy.Agent.ORM
2DD485729E0402FD652CF613E172EA834B5C9077
5E8B566095FD6A98949EF5C479CE290F520DD9E2
8C2C08111F76C84C7573CF07C3D319A43180E734
36093A6004A9502079B054041BADC43C69A0BDEB
6F452C76F7AC00FE1463314F5AA0A80EC4F7360C
850E9A10E6D20D33C8D2C765E22771E8919FC3EE
A09F520DDED0D5292A5FA48E80DE02F9AF718D06
3707029DC5CBBE17FD4DE34134847F92E7324C45
905D0842CC246A772C595B8CF4A4E9E517683EB7
237784574AFB8868213C900C18A114D3FA528B95
6090853934833D0814F9239E6746161491CCCB44
3672C9F4E7F647F2AF9AE6D5EA8D9C7FF16FAF40
EC5DADAACAE763D0E55CE6A78C9A5F57B01A5135
4E8EE08FF4F8DC06AFF8DE2E476AFAFBA58BDC11
A734193F550DDA5C1FFD9FEC3A0186A0A793449C
EFC0555418A6ED641047D29178D0DA3AEFA7ADEB
B79E6A21D8C2813EC2279727746BDB685180751A
4DB58E7D0FCA8D6748E17087EB34E562B78E1FDE
567749B4F2330F02DD181C6C0840191CEE2186D9
3ACEA9477B219FC6B8C0A734E67339AE2EB2AA5B
2896814E5F8860E620AC633AF53A55D9AA21F8C0
84CC02B3C10306BFCECE8BF274B57475B056C6D6
207FF65543DAC6D1D9F86DFFD891C507AD24018B
D627DD4E3850CBD571AFC4799A331054C7080B0D
DCC932B878B374D47540D43A2DEE97F37D68267F
983D33F547588A59B53D7F794768B264454446D5
19E7C7A78C5D58945B615D98FF0990389485933F
DED83A1E3B6630D69077976CC01321FBC946DCE2
170142C042BF32FF86AF680EAD86CD1AF075B0CB
A77336620DF96642691C1E5B6C91511BFA76A5BE
3CEF1CA36A78CBA308FB29A46B20E5CA22D03289
DD01331ABFF03525506CDCBAC4D76CB4EFD602A4
SHA-1 RTF exploits
1F9462AA39645376C74566D55866F7921BD848F7
81E43D653ACD2B55C8D3107E5B50007870D84D76
AC68AD2E5F5802A6AB9E7E1C1EC7FAB3C6BDBAA4
F869C7EA683337A2249908C21B9D3283CC2DD780
7162BB61CD36ED8B7EE98CBD0BFFEC33D34DD3E7
5943ABCF662DC9634B714B1358164B65E5651D15
A40BDF005B4B469D2C7BED1766C9DA9823E1CFB7
833A8D88BE11807BAE966D56B28AF7B3CC34DBCD
AF7564EE7959142C3B0D9EB8129605C2AE582CB7
DCC932B878B374D47540D43A2DEE97F37D68267F
6FF3AE5BA4E9A312602CBD44A398A02AB0437378
32AA4911BC6AB8098E496CD88790FF7147EC6AC3
Addresses of C & C servers Trojan.Win32 / Spy.Agent.ORM
192.52.166.66
84.200.4.226
78.128.92.117
176.31.157.62
clients4-google.com (192.169.82.86)
adobe-dns-3-adobe.com (78.128.92.112)
img.in-travelusa.com (192.169.82.86)
SHA-1 backdoor Tiny Meterpreter
28D514FE46D8B5720FE27C40C3889F3B45967CC7
0B0884992F28A3C1439DBA60007076B22831CE51
SHA-1 Win32 / Wemosis (PoS RAM Scraper)
5E31DB305A97736C0F419A3F2F8F093FF6A1F56F
Win32 / Wemosis C & C Server Address
198.100.119.14

Cyberband activity is interesting not only from the point of view of the stolen amount, but also from the technical point of view. Its distinguishing feature is the fact that the gang is already acting as a mature APT group, purposefully infecting a large number of computers and deriving actual benefits from it. She specializes in compromising large financial institutions, as well as other institutions. Our analyst Anton Cherepanov ( @ cherepanov74 ) analyzed the activities of Carbanak.
')
Casino Compromise in the USA
In late August, we discovered an attempt to compromise the internal casino network, which is located in a hotel in the USA. The infection vector could be a phishing message with a malicious attachment in the form of an RTF exploit or a .SCR file. The main task of the attackers was to compromise the PoS servers that were used to process financial payments.
The attackers have adapted a small open source backdoor called Tiny Meterpreter for their own purposes. Some changes have been made to introduce malicious code into the svchost.exe system process.
The backdoor dumps executable files of two different malware onto the disk.
- Win32 / Spy.Sekur is a well-known malware that has already been used by Carbanak cyberband.
- Win32 / Wemosis - backdoor to steal confidential card data from PoS terminals (PoS RAM Scraper backdoor).
As was pointed out in a study of our colleagues from antivirus company TrendMicro, the Carbanak malware is focused on compromising Epicor / NSB PoS systems, while the Win32 / Wemosis backdoor is PoS RAM Scraper. PoS RAM Scraper is a module that specializes in copying a portion of the virtual memory of a legitimate process in order to search for numbers and other credit card information. The Wemosis backdoor is written in Delphi and allows an attacker to remotely control an infected system.
Both malware dropped by the Tiny Meterpreter backdoor is signed with the same digital certificate.

Fig. Information about the digital certificate that was used to sign the modules of the cyberband of Carbanak.
Certificate Information:
Company name: Blik
Validity: from 02 October 2014 to 03 October 2015
Thumbprint: 0d0971b6735265b28f39c1f015518768e375e2a3
Serial number: 00d95d2caa093bf43a029f7e2916eae7fb
Subject: CN = Blik
O = blik
STREET = Berzarina, 7, 1
L = Moscow
S = Moscow
PostalCode = 123298
C = RU
This certificate was also used to sign the executable file of another Win32 / Spy.Agent.ORM malware family that was used by the Carbanak cyber gang.
Win32 / Spy.Agent.ORM malware review
The Win32 / Spy.Agent.ORM malware (aka Win32 / Toshliph) is a Trojan that was used by the cyberband as a first-level payload. The threat executable was signed by the above digital certificate. In addition, the trojan has common code characteristics with the malware of the cyberband, which they used in their malicious campaigns regularly.
In fact, the Win32 / Spy.Agent.ORM malware family is already known to the public. In July 2015, security company Cyphort reported on the compromise of the news portal rbc.ua and the banking website unicredit.ua. As a result of the investigation, it was found that the compromised websites distributed using the Win32 / Spy.Agent.ORM exploit kit. Another company, Blue Coat, also reported on a phishing e-mail that was sent to employees of the Central Bank of Armenia. The mailing list was used to distribute Win32 / Spy.Agent.ORM.
We recorded an increased activity of this modification of the malware family at the beginning of the summer of 2015, after which we began to monitor its activity. We also observed cyber attacks on users using this malware in Russia and Ukraine. Phishing emails were sent to users with malicious attachments of .SCR files or .RTF exploits. Below is an example of a phishing message that was sent to an employee of one of the largest companies engaged in trading on the Forex market.

Fig. An example of a phishing email message with a malicious program.
Below is a text from another phishing email. A message with this text was sent to an employee of one of the largest electronic payment processing companies in Russia.
Resolution of Roskomnadzor from 04.08.2015. You need to block the materials falling under the Federal Law of 27.07.2006 N 152-FZ (as amended on 07.21.2014) “On Personal Data”. List of materials in the document.
Password roscomnadzor
Below are the names of the files from the various phishing messages of this malicious campaign.
“ALFA-BANK” JSC CONTRACT.scr ”
"The list of materials for blocking from 04.08.2015g.scr"
“Postanovlene_ob_ustranenii_18.08.2015.pdf% mnogo.pfrelov% ..scr”
"The rules of the Bank of Russia from 06.08.2015.pdf% mnogoproslov% .scr"
All attachments to these letters contain an archive with a .SCR file that is password protected. Files contain icons of applications such as Adobe Acrobat Reader and MS Word.
In other cases, attackers used RTF files with various exploits, including an exploit for one of the latest MS Office vulnerabilities. This is a vulnerability CVE-2015-1770, which was fixed by Microsoft in June 2015 by updating MS15-059. Below are the names of the RTF files that we observed in this malicious campaign.
"Prikaz-451.doc"
"REMITTANCE ADVICE ON REJECTION.doc"
"PROOF OF REMITTANCE ADVICE .doc"
"HDHS739_230715_010711_A17C7148_INTERNAL.doc"
"Անկերի և բանկային գործունեության մասին ՀՀ օրենք 07.27.2015.doc" (Armenian: Law on Banks and Banking Activity 07.27.2015)
"PAYMENT DETAILS.doc"
"ALFA-BANK" JSC AGREEMENT.doc "
"AML REPORTS_20082015_APPLICATION FORM-USD-MR VYDIAR.doc"
Anti-Money Laudering & Suspicious cases.doc
"ApplicationXformXUSDXduplicateXpayment.doc"
"AML USD & Suspicious cases.doc"
“Amendment inquiry (reference TF1518869100.doc”
"Information 2.doc"
Below is an example of a phishing message that was sent to a bank employee in the UAE.

Fig. An example of a phishing message with an RTF file in the attachment.
Below is an example of a phishing message that was sent to a German bank.

Fig. An example of a phishing message with an RTF file in the attachment.
Win32 / Spy.Agent.ORM Technical Analysis
As we have already indicated, this malware is a simple and small backdoor, which allows attackers to remotely access the victim’s computer. After its launch, the Trojan connects to the C & C server and receives various commands: take a screenshot of the screen, get a list of running processes, get information about the system, get the campaign ID. Based on this information, operators can determine the degree of usefulness of the infected computer, i.e., is this computer one that was of interest to intruders or is it a randomly infected system.
Below is a list of commands that a bot can receive from a C & C server.

One of the latest samples of this malware family, which was discovered by our anti-virus laboratory, was signed with another digital certificate.

Fig. Information about the digital certificate that signed the malware file.
Certificate data.
Company name: In travel TOV
Validity: from 21 July 2015 to 21 July 2016
Thumbprint: 7809fbd8d24949124283b9ff14d12da497d9c724
Serial number: 00dfd915e32c5f3181a0cdf0aff50f8052
Subject: CN = In travel TOV
O = In travel TOV
STREET = prospekt Pravdi 33
L = Kiev
S = Kievskaja
PostalCode = 04108
C = UA
This latter sample also contains an LPE exploit to gain system privileges in the system and to set itself up as a system service. The exploit relates to the CVE-2015-2426 ( Hacking Team ) vulnerability in the Windows system component Adobe Type Manager Library (ATMFD.dll), which we wrote about here . It has been fixed by updating MS15-078 .

Fig. Part of the exploit code CVE-2015-2426.
The digital certificate for the Blik organization is one of the common features that links Win32 / Spy.Agent.ORM and Win32 / Spy.Sekur (Carbanak). Another common feature is in the malware code, below is an example of such a common function. The function specializes in generating a BOTID value that is unique and is generated based on the hardware parameters of the infected computer.

Fig. Similarities in malware code.
The BOTID value is used by attackers to identify the infected computer. In both cases, the value is generated based on the MAC address and computer name, then this value is converted to a string using the well-known wsprintf function.
Sinkhole stats
Using the sinkhole mechanism, we were able to obtain the following statistics on the distribution of this malicious program.

Since the cyber attacks conducted by the gang were highly targeted, the total number of victims was not so great in absolute terms. Victims of malware in the United States are in several states, including Nevada (Las Vegas), California and New York. Compromise exposed various casinos and hotels.
Conclusion
Even after the previous series of successful cyber attacks and theft of hundreds of millions of dollars, the gang or the Carbanak APT group did not want to remain in the shadows and rest on their laurels. On the contrary, it continues its activity and specializes in cyber attacks of its chosen targets, which relate to the banking sector, companies trading in the Forex market, as well as American casinos. We recently discovered Carbanak victims also in the following countries.
- USA
- Germany
- UAE
As shown above, cyberbanda uses for its purposes not only one family of malicious programs, but also several others. It can be seen that all these malicious programs - Carbanak (Win32 / Spy.Sekur), Win32 / Spy.Agent.ORM, Win32 / Wemosis - are based on different code bases, however, contain some common features, such as digital signatures based on a single certificate.
Cyberband has updated its arsenal with the latest exploits for vulnerabilities such as MS Office RCE CVE-2015-1770 and CVE-2015-2426, which was located in the leaked data from the Hacking Team cybergroup.
We continue to monitor the activities of Carbanak threats. For additional materials on this topic or for sending new malware samples, please contact threatintel@eset.com.
Compromise Indicators (IoC)
Sample IDs of SHA-1 Trojan.Win32 / Spy.Sekur (Carbanak malware)
A048C093C5DA06AF148CA75299960F618F878B3A
3552338D471B7A406D8F7E264E93B848075235C0
3A9A23C01393A4046A5F38FDBAC371D5D4A282F1
8D5F2BF805A9047D58309788A3C9E8DE395469A8
BCF9E4DCE910E94739728158C98578A8D145BE56
8330BC5A3DCC52A22E50187080A60D6DBF23E7E6
E838004A216E58C44553A168760100B497E514E8
CF1F97879A6EB26FEDC7207D6679DFA221DD2D45
7267791340204020727923CC7C8D65AFC18F6F5B
F8CBF647A64028CAE835A750EF3F8D1AA216E46C
33870482BA7DE041587D4B809574B458C0673E94
3927835C620058EFCADF76642489FC13AACE305B
D678BD90257CF859C055A82B4A082F9182EB3437
0B8605D0293D04BBF610103039768CBE62E2FAAE
7A9BE31078BC9B5FECE94BC1A9F45B7DBF0FCE12
SHA-1 RTF exploits
D71E310ADF183F02E36B06D166F8E3AD54FDBCC9
5B6ABA51215A9662987F59AEF6CAE0A9E3A720B8
1AD84A244B7D4FBB4D89D023B21715B346027E49
E8514BF4C4E1F35FB1737C2F28A4A4CED07AA649
68EA12CDCCEE01D50C23EBC29CAA96BF40925DC6
AC95F01487B4F179A1F10684B1E0A5656940A005
B4A94A214FC664B8D184154431E1C5A73CA0AE63
Addresses of C & C servers Trojan.Win32 / Spy.Sekur
weekend-service.com:80
seven-sky.org:80
comixed.org:80
91.207.60.68:80
89.144.14.65:80
87.98.217.9:443
82.163.78.188:443
50.62.171.62:700
31.3.155.123:443
216.170.116.120:80
216.170.116.120:700
216.170.116.120:443
194.146.180.58:80
193.203.48.41:700
185.29.9.28:443
178.209.50.245:443
162.221.183.11:80
162.221.183.11:443
162.221.183.109:443
141.255.167.28:443
104.232.32.62:443
104.232.32.61:443
SHA-1 for Trojan.Win32 / Spy.Agent.ORM
2DD485729E0402FD652CF613E172EA834B5C9077
5E8B566095FD6A98949EF5C479CE290F520DD9E2
8C2C08111F76C84C7573CF07C3D319A43180E734
36093A6004A9502079B054041BADC43C69A0BDEB
6F452C76F7AC00FE1463314F5AA0A80EC4F7360C
850E9A10E6D20D33C8D2C765E22771E8919FC3EE
A09F520DDED0D5292A5FA48E80DE02F9AF718D06
3707029DC5CBBE17FD4DE34134847F92E7324C45
905D0842CC246A772C595B8CF4A4E9E517683EB7
237784574AFB8868213C900C18A114D3FA528B95
6090853934833D0814F9239E6746161491CCCB44
3672C9F4E7F647F2AF9AE6D5EA8D9C7FF16FAF40
EC5DADAACAE763D0E55CE6A78C9A5F57B01A5135
4E8EE08FF4F8DC06AFF8DE2E476AFAFBA58BDC11
A734193F550DDA5C1FFD9FEC3A0186A0A793449C
EFC0555418A6ED641047D29178D0DA3AEFA7ADEB
B79E6A21D8C2813EC2279727746BDB685180751A
4DB58E7D0FCA8D6748E17087EB34E562B78E1FDE
567749B4F2330F02DD181C6C0840191CEE2186D9
3ACEA9477B219FC6B8C0A734E67339AE2EB2AA5B
2896814E5F8860E620AC633AF53A55D9AA21F8C0
84CC02B3C10306BFCECE8BF274B57475B056C6D6
207FF65543DAC6D1D9F86DFFD891C507AD24018B
D627DD4E3850CBD571AFC4799A331054C7080B0D
DCC932B878B374D47540D43A2DEE97F37D68267F
983D33F547588A59B53D7F794768B264454446D5
19E7C7A78C5D58945B615D98FF0990389485933F
DED83A1E3B6630D69077976CC01321FBC946DCE2
170142C042BF32FF86AF680EAD86CD1AF075B0CB
A77336620DF96642691C1E5B6C91511BFA76A5BE
3CEF1CA36A78CBA308FB29A46B20E5CA22D03289
DD01331ABFF03525506CDCBAC4D76CB4EFD602A4
SHA-1 RTF exploits
1F9462AA39645376C74566D55866F7921BD848F7
81E43D653ACD2B55C8D3107E5B50007870D84D76
AC68AD2E5F5802A6AB9E7E1C1EC7FAB3C6BDBAA4
F869C7EA683337A2249908C21B9D3283CC2DD780
7162BB61CD36ED8B7EE98CBD0BFFEC33D34DD3E7
5943ABCF662DC9634B714B1358164B65E5651D15
A40BDF005B4B469D2C7BED1766C9DA9823E1CFB7
833A8D88BE11807BAE966D56B28AF7B3CC34DBCD
AF7564EE7959142C3B0D9EB8129605C2AE582CB7
DCC932B878B374D47540D43A2DEE97F37D68267F
6FF3AE5BA4E9A312602CBD44A398A02AB0437378
32AA4911BC6AB8098E496CD88790FF7147EC6AC3
Addresses of C & C servers Trojan.Win32 / Spy.Agent.ORM
192.52.166.66
84.200.4.226
78.128.92.117
176.31.157.62
clients4-google.com (192.169.82.86)
adobe-dns-3-adobe.com (78.128.92.112)
img.in-travelusa.com (192.169.82.86)
SHA-1 backdoor Tiny Meterpreter
28D514FE46D8B5720FE27C40C3889F3B45967CC7
0B0884992F28A3C1439DBA60007076B22831CE51
SHA-1 Win32 / Wemosis (PoS RAM Scraper)
5E31DB305A97736C0F419A3F2F8F093FF6A1F56F
Win32 / Wemosis C & C Server Address
198.100.119.14
Source: https://habr.com/ru/post/266489/
All Articles