Extortionist Android / Lockerpin.A attacks US users
Recently, our analysts have recorded another surge in the activity of attackers, who distributed one of the modifications of the extortionist for Android. Earlier, we already observed families of ransomware who also combined the functions of a fake antivirus (Fake AV) and could block the screen of a user's device (for example, Android Defender). Last year, we also wrote about the extortionist Simplocker, which is the first malicious program, the extortioner for Android, which contained the ability to encrypt files.

In previous versions of the ransomware for Android, such as LockScreen, the screen lock mechanism was usually implemented by constantly drawing the ransomware window in the foreground, and such an operation was performed in an infinite loop so that no one could interrupt it. On the other hand, overcoming such a mechanism of self-defense was not difficult for an experienced user, he could use the Android Debug Bridge (ADB) mechanism to unlock or disable Administrator rights, and also remove malware in Safe Mode.
')
In the new version of the ransomware family for Android, which is detected by ESET antivirus products like Android / Lockerpin.A , users are deprived of any way to restore lost control over their device without having root rights or without an installed security product on the device. This eliminates the obvious way hard reset, which helps to return the device to the factory settings and remove all data from it.
In addition, the extortioner also uses a special method to obtain and maintain Administrator rights (Device Administrator) on the device to prevent its deletion. This is the first case of this behavior of Android malware from those we have observed earlier.
Analysis
After successful installation on the device, Android / Lockerpin.A tries to get device administrator privileges on the system. This method is used by the authors of malware for Android more and more often and significantly complicates their removal from the system. Earlier versions of the Android / Locker family also relied on it.
In recent versions, however, the extortioner gets administrative rights more secretively than in previous ones. A special activation window with the special name “Update patch installation” covers the main window of the ransomware lockout. When a user clicks on the control of this window to “install an update”, he activates device administrator privileges, giving them to the malicious program.
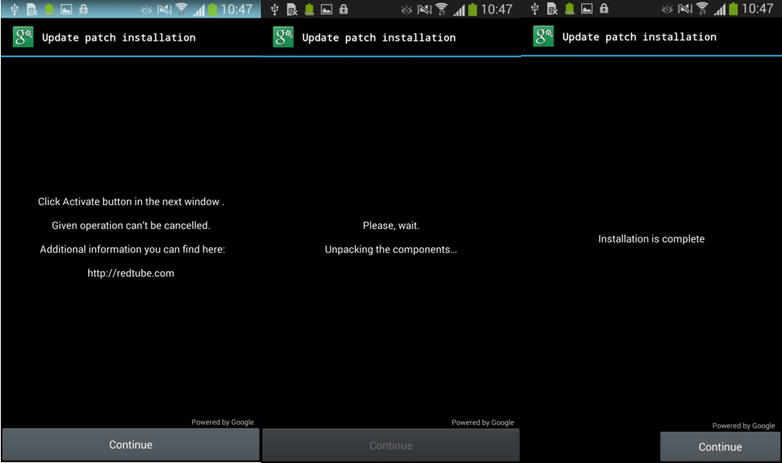
Fig. Window for secret activation of the device administrator mode.
After clicking on the button, the user's device will be at the complete disposal of the extortioner: the malicious code receives administrator rights and can block the device, as well as set a new PIN code to unlock it. After this operation, the user will be asked to pay a ransom of $ 500 for viewing and storing prohibited pornographic materials.

Fig. Redemption window.
After displaying this warning, the screen of the device is blocked in the style typical for this kind of ransomware. In the simplest case, you can close the ransom window and remove the malware from the system by downloading in safe mode or using the Android Debug Bridge (ADB) mode. However, after displaying a warning message, Android / Lockerpin.A blocks the device with a new PIN code, and the new PIN code is unknown to both the owner and the attackers themselves. The only way to unlock the device is to reset it to the factory settings or to get root privileges in the system.

Fig. Extortion device unlock screen.
Extortionist self-defense mechanisms
The extortioner Android / Lockerpin.A not only obtains the rights of the device administrator, it also uses a kind of aggressive self-defense mechanisms to support them. In the event that a user wants to deactivate the device administrator mode for a malicious program, he will not be able to perform such an operation, since the malicious program registers a callback function to reactivate elevated privileges in case of an attempt to remove them. When a user tries to disable this elevated mode, it displays a fake window, which is shown in Fig. 4. Pressing the “Continue” button re-activates the administrator mode.

Fig. A warning message about disabling the device administrator mode.
Lockerpin self-defense includes mechanisms for forcing the anti-virus product processes on a system when a user tries to disable administrator privileges. The list of anti-virus products includes ESET Mobile Security, Avast and Dr.Web.

Fig. The function of forcing the completion of running processes.
Tracking the actions of the com.android.settings process is an attempt to prevent malware from being removed from the system through the application manager built into Android. The self-defense mechanisms of our anti-virus product, ESET Mobile Security, do not allow us to forcibly terminate its processes.
Ways to spread
The attackers chose social engineering methods to lure the user to install a malicious program. For this, it is offered as an adult video, as well as an application for viewing this kind of content. In all such cases, the application was called “Porn Droid”.
Statistics obtained using our cloud technology ESET LiveGrid shows that the largest number of infected devices is in the US (more than 75% of the total number of infections). Such a geography of distribution is not customary for us, since those extortioners that we recorded earlier were mainly used to compromise users in Russia and Ukraine. Obviously, in the US, attackers can benefit more from user compromise than in the above-mentioned countries.

Fig. The geography of the spread of Android / Lockerpin.A.
Unlock device
As we mentioned earlier, the only solution that can be used to remove the screen with the PIN code request, without returning the device to factory settings, is to obtain root rights or use the functions of an already installed security software. In the case of obtaining root rights, the user can use the ADB tool to connect the device to the PC and delete the file with the PIN code of the malicious program. To perform such an operation, the device must have the debugging feature enabled (Settings -> Developer options -> USB Debugging). The user can use the following set of commands to unlock the device.
> adb shell
> su
> rm /data/system/password.key
After executing the above commands, the PIN request screen will be deleted, and the user will gain access to the device. In some cases, after the operations, the device needs to be rebooted.
Conclusion
Fortunately, the user cannot download the malicious Android / Lockerpin.A application from the Google Play Store. The malicious program can get on the user's device through third-party application stores, pirated software websites or torrents. The most effective way to avoid infection and blocking the device is to use proactive means of protection. We strongly recommend timely update antivirus. Antivirus product ESET Mobile Security detects this threat as Android / Lockerpin.A .

In previous versions of the ransomware for Android, such as LockScreen, the screen lock mechanism was usually implemented by constantly drawing the ransomware window in the foreground, and such an operation was performed in an infinite loop so that no one could interrupt it. On the other hand, overcoming such a mechanism of self-defense was not difficult for an experienced user, he could use the Android Debug Bridge (ADB) mechanism to unlock or disable Administrator rights, and also remove malware in Safe Mode.
')
In the new version of the ransomware family for Android, which is detected by ESET antivirus products like Android / Lockerpin.A , users are deprived of any way to restore lost control over their device without having root rights or without an installed security product on the device. This eliminates the obvious way hard reset, which helps to return the device to the factory settings and remove all data from it.
In addition, the extortioner also uses a special method to obtain and maintain Administrator rights (Device Administrator) on the device to prevent its deletion. This is the first case of this behavior of Android malware from those we have observed earlier.
Analysis
After successful installation on the device, Android / Lockerpin.A tries to get device administrator privileges on the system. This method is used by the authors of malware for Android more and more often and significantly complicates their removal from the system. Earlier versions of the Android / Locker family also relied on it.
In recent versions, however, the extortioner gets administrative rights more secretively than in previous ones. A special activation window with the special name “Update patch installation” covers the main window of the ransomware lockout. When a user clicks on the control of this window to “install an update”, he activates device administrator privileges, giving them to the malicious program.

Fig. Window for secret activation of the device administrator mode.
After clicking on the button, the user's device will be at the complete disposal of the extortioner: the malicious code receives administrator rights and can block the device, as well as set a new PIN code to unlock it. After this operation, the user will be asked to pay a ransom of $ 500 for viewing and storing prohibited pornographic materials.

Fig. Redemption window.
After displaying this warning, the screen of the device is blocked in the style typical for this kind of ransomware. In the simplest case, you can close the ransom window and remove the malware from the system by downloading in safe mode or using the Android Debug Bridge (ADB) mode. However, after displaying a warning message, Android / Lockerpin.A blocks the device with a new PIN code, and the new PIN code is unknown to both the owner and the attackers themselves. The only way to unlock the device is to reset it to the factory settings or to get root privileges in the system.

Fig. Extortion device unlock screen.
Extortionist self-defense mechanisms
The extortioner Android / Lockerpin.A not only obtains the rights of the device administrator, it also uses a kind of aggressive self-defense mechanisms to support them. In the event that a user wants to deactivate the device administrator mode for a malicious program, he will not be able to perform such an operation, since the malicious program registers a callback function to reactivate elevated privileges in case of an attempt to remove them. When a user tries to disable this elevated mode, it displays a fake window, which is shown in Fig. 4. Pressing the “Continue” button re-activates the administrator mode.

Fig. A warning message about disabling the device administrator mode.
Lockerpin self-defense includes mechanisms for forcing the anti-virus product processes on a system when a user tries to disable administrator privileges. The list of anti-virus products includes ESET Mobile Security, Avast and Dr.Web.

Fig. The function of forcing the completion of running processes.
Tracking the actions of the com.android.settings process is an attempt to prevent malware from being removed from the system through the application manager built into Android. The self-defense mechanisms of our anti-virus product, ESET Mobile Security, do not allow us to forcibly terminate its processes.
Ways to spread
The attackers chose social engineering methods to lure the user to install a malicious program. For this, it is offered as an adult video, as well as an application for viewing this kind of content. In all such cases, the application was called “Porn Droid”.
Statistics obtained using our cloud technology ESET LiveGrid shows that the largest number of infected devices is in the US (more than 75% of the total number of infections). Such a geography of distribution is not customary for us, since those extortioners that we recorded earlier were mainly used to compromise users in Russia and Ukraine. Obviously, in the US, attackers can benefit more from user compromise than in the above-mentioned countries.

Fig. The geography of the spread of Android / Lockerpin.A.
Unlock device
As we mentioned earlier, the only solution that can be used to remove the screen with the PIN code request, without returning the device to factory settings, is to obtain root rights or use the functions of an already installed security software. In the case of obtaining root rights, the user can use the ADB tool to connect the device to the PC and delete the file with the PIN code of the malicious program. To perform such an operation, the device must have the debugging feature enabled (Settings -> Developer options -> USB Debugging). The user can use the following set of commands to unlock the device.
> adb shell
> su
> rm /data/system/password.key
After executing the above commands, the PIN request screen will be deleted, and the user will gain access to the device. In some cases, after the operations, the device needs to be rebooted.
Conclusion
Fortunately, the user cannot download the malicious Android / Lockerpin.A application from the Google Play Store. The malicious program can get on the user's device through third-party application stores, pirated software websites or torrents. The most effective way to avoid infection and blocking the device is to use proactive means of protection. We strongly recommend timely update antivirus. Antivirus product ESET Mobile Security detects this threat as Android / Lockerpin.A .
Source: https://habr.com/ru/post/266431/
All Articles