Security on trust
There are a number of technologies on the market, the thoughtless use of which can lead to problems. Nobody says that there are no positive moments in them, but ...
This article was conceived for a long time, but a simple experiment served as a direct reason for it, which allowed to check for a long time suspicions.
First of all, three flash drives from the party intended for gifts to everyone and everything were written out and received at the warehouse. We especially note that the warehouse worker was not aware of our experiment and took randomly sticking flash drives out of the box.
Attention! This article is not intended to tarnish a particular product. All the places on the screenshots that allow you to point to a specific product, carefully smeared. Information about technologies obtained from conversations at conferences or (unfortunately, it turned out very rarely) from documentation.
')
Everyone knows that the uncontrolled use of removable media does not lead to anything good. Infections, file leaks, and even burned ports. Naturally, administrators seek to streamline the use of removable media by defining a white list. But how does this solve the problem?
So, we set one of the solutions, which includes the white list creation functionality (we do not describe the procedure for adding to the white list and skip it, since it differs slightly from each product).
We print and insert the first flash drive from the received in stock. Add it to the white list.

Insert the second flash drive:

The system does not see the difference! Here you have a trusted list.
Let's try to connect the first flash drive (the one we inserted earlier). We had it resolved, but now in the port where we previously inserted it - a second flash drive is inserted.
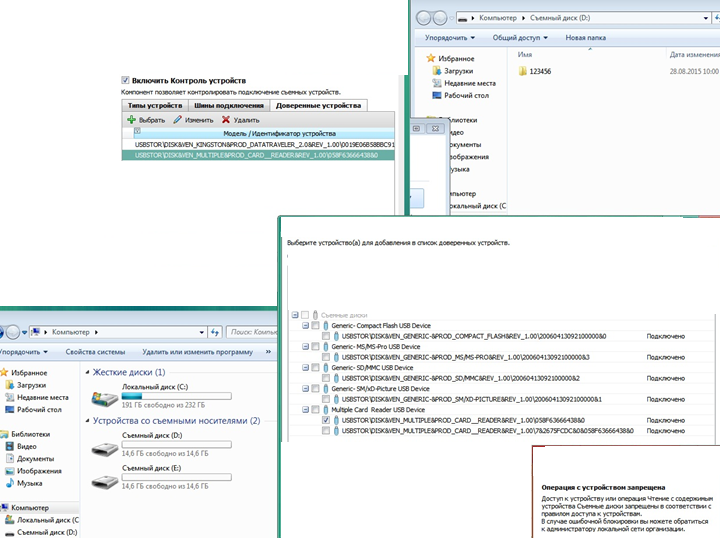
There is a lock! Only the truth of the flash drive that we have on the white list ...
For interest in, two Kingston's were found and tested (administrators usually buy already liked models, but according to orders - at different times).
Insert the first, add it to the white list
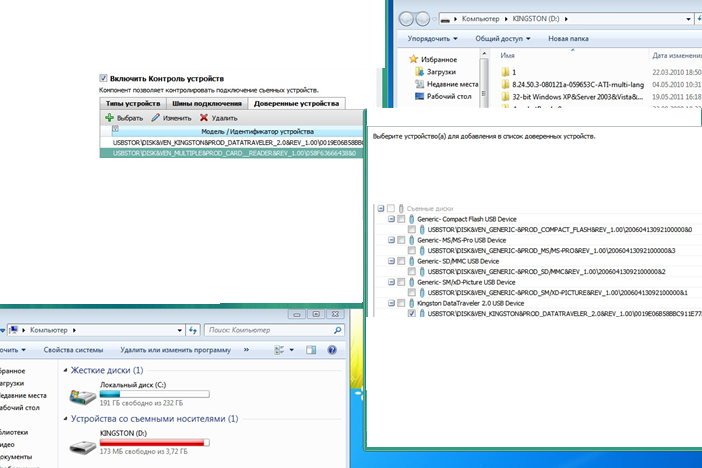
We insert the second Kingston.

There is a lock!
Total:
In the information security industry, a situation has arisen where specialists demand the openness of encryption systems - but we are calm about the fact that all other technologies are closed. Being closed can be understood - knowing the insides an attacker can exploit flaws and architectures and vulnerabilities. But one thing that cannot be justified is the absence of manuals for information security specialists, who clearly describe the limitations of this or that technology. Practically at every meeting it is necessary to prove on the fingers of its participants that their security system is full of holes! And the saddest thing is that occasionally there are waves of laughter about the fact that one or another product does not use fashionable or “all the necessary” technology.
Let's go over the list (these technologies are used in antiviruses, but for some reason it seems that for other types of products you can also make a similar list)?
DNSBL database spam filtering . One quote :
Such databases are not controlled by either the vendor, the supplier of the anti-spam solution, or the client, the solution using. The real situation is when someone forges a sender and sends it to base traps (for example, organizing a stream of spam from a botnet). The last time I was told about a similar case in Samara. As a result of the next update of the DNSBL database, the letters to the domains / addresses in the database will cease to pass. I will not say for all owners of the DNSBL bases, but they also talked about situations when deletion from the bases happens for money.
Filtering spam based on greylisting technology . Here opinions differ. Who says that it is effective, who says that at the moment spammers stupidly ignore the delay in receiving letters. Quite possibly this is due to spamming technologies. When sending it through a botnet, the delay can be ignored; when using a special server, they can be critical.
Vulnerability analysis systems . The thing is necessary, but you cannot trust it blindly. As practice shows, they know only known vulnerabilities - you should not rely that all vulnerabilities will be found by them. Accordingly, unknown malware will penetrate. Again, there are very serious doubts that the vulnerability scan engines used in personal antivirus systems correspond to the level of special products. I did not see any descriptions of the technology, its limitations.
Virtual keyboards . They are promoted as one of their pillars for the protection of personal information, passwords for remote banking services and so on.
How many have heard of such restrictions?
Very interesting combination of two paragraphs. Thus, a malicious program that can take screenshots of information will completely remove keystrokes on the virtual keyboard.
And now a quote from a marketing document:
Password Managers The idea of storing passwords on a computer is not bad in itself, but such programs also have vulnerabilities and can be cracked .
Cloud Antivirus . The network is present in a huge number of panegyrics cloud technologies. As far as you can understand, cloud systems are based on two whales - a file (link) gets a positive reputation if it didn’t cause problems for a large number of users and the reputation from the cloud is higher than the opinion of the local system . Theoretically, a situation is possible when an unknown (not detectable) virus spreads across users (say on a botnet), gets a high reputation and only then introduces the desired victim - and the opinion of the local antivirus will be ignored. If at the time of implementation, the system administrator tries to change the file's reputation, it is not a fact that it will succeed. Opinion million lemming. Until the file gets to the laboratory for analysis, it will be distributed freely
Is there a plus for technology? Yes.
Systems based on change control, including cloud . Based on the calculation of checksums. The technology at the time of occurrence is breakthrough, allowing you to reduce the scan time, but now there are updates every hour and even more. Since at the time of the arrival of a new update in the system there may be a previously unknown malicious file, the checksums of the files need to be recalculated after each update, that is, approximately once an hour, which increases the braking of the system. Plus, again, not all control systems are the same. Just control over the files costs - just by changing the path that the program runs.
The biggest disadvantage of products based on state control is the inability to protect against an unknown threat. They are not able to remove already running malware.
Proactive systems based on knowledge of program behavior profiles . They require that all profiles of all existing programs in the world be available in the database (taking into account their updates - after all, old versions can work for users), which is unrealistic - including the fact that programs are constantly updated. This leads to the fact that the user is sometimes requested permission for a particular action. The user is not able to distinguish a request for a virus from a request for an ordinary program.
Integration of antivirus with corporate management systems and updates . Using systems such as Microsoft Update, MMC, and so on. Integration with corporate management systems allows, in particular, without switching between management system interfaces, to monitor the status of the entire network. A huge plus. But it is possible that a hacker, having gained access to a corporate management system, will demolish the same antivirus and leave the network unprotected. All of these systems are not under the control of the self-defense system and can be intercepted by an intruder.
Wheels of course now rubber:
But how safe is the situation when the control system is built on an external library, which can be modified at any time by a hacker?
Barring incoming channels during RBS operation . It does not make sense if the BOB is intercepted by malware.
Confirmation of payments by SMS . SMS can be modified by malware introduced by phishing such as
Protection of billing data during transmission - data encryption. Great thing, but it is often forgotten that the data can be modified before it enters the protected channel - a virus can be between the client program and the trusted channel.
Protected runtime environments . Malicious programs can recognize being in a protected environment and at this time do nothing wrong. Well, the protected environment itself can be hacked.
Again, not a panacea.
Antivirus for virtualization systems .
Quote from the article: Eugene Kaspersky Ambitions, laziness and greed in IT business
The most interesting thing is that for systems based on the API, VmWare is not at all clear - can these systems deal with previously known malware? Can they remove already running malware, etc.?
Protection against viruses by formatting the system . The virus can not only be in the form of a file.
Naturally, this is not all that is used to ensure security, but the above list is enough to conclude. There is no panacea. Blindly believing journalists and marketers is impossible. You should always check any statements. Especially when another wave of fashion rises.
This article was conceived for a long time, but a simple experiment served as a direct reason for it, which allowed to check for a long time suspicions.
First of all, three flash drives from the party intended for gifts to everyone and everything were written out and received at the warehouse. We especially note that the warehouse worker was not aware of our experiment and took randomly sticking flash drives out of the box.
Attention! This article is not intended to tarnish a particular product. All the places on the screenshots that allow you to point to a specific product, carefully smeared. Information about technologies obtained from conversations at conferences or (unfortunately, it turned out very rarely) from documentation.
')
Everyone knows that the uncontrolled use of removable media does not lead to anything good. Infections, file leaks, and even burned ports. Naturally, administrators seek to streamline the use of removable media by defining a white list. But how does this solve the problem?
So, we set one of the solutions, which includes the white list creation functionality (we do not describe the procedure for adding to the white list and skip it, since it differs slightly from each product).
We print and insert the first flash drive from the received in stock. Add it to the white list.

Insert the second flash drive:

The system does not see the difference! Here you have a trusted list.
Let's try to connect the first flash drive (the one we inserted earlier). We had it resolved, but now in the port where we previously inserted it - a second flash drive is inserted.

There is a lock! Only the truth of the flash drive that we have on the white list ...
For interest in, two Kingston's were found and tested (administrators usually buy already liked models, but according to orders - at different times).
Insert the first, add it to the white list

We insert the second Kingston.

There is a lock!
Total:
- The technology works, but since the devices of one (and who knows the Chinese, maybe not one) of the party are determined equally, then before creating a white list, you must select a batch of flash drives, each of which is unique. Otherwise, under certain conditions, the USB device can be replaced without even resorting to technical tricks with the carrier itself.
- Unfortunately to keep the parameters of flash drives secret is unrealistic. Therefore, administrators should not blindly believe that the authorized flash drive is inserted, and not the malicious USB flash drive. It is also necessary to differentiate access rights (Captain Obvious. Yes).
In the information security industry, a situation has arisen where specialists demand the openness of encryption systems - but we are calm about the fact that all other technologies are closed. Being closed can be understood - knowing the insides an attacker can exploit flaws and architectures and vulnerabilities. But one thing that cannot be justified is the absence of manuals for information security specialists, who clearly describe the limitations of this or that technology. Practically at every meeting it is necessary to prove on the fingers of its participants that their security system is full of holes! And the saddest thing is that occasionally there are waves of laughter about the fact that one or another product does not use fashionable or “all the necessary” technology.
Let's go over the list (these technologies are used in antiviruses, but for some reason it seems that for other types of products you can also make a similar list)?
DNSBL database spam filtering . One quote :
Some mail administrators rely on so-called DNSBL (RBL) for filtering spam - blacklists of sites seen in spamming. So, never add any DNSBL checks to your mail servers. ... In these lists, the nodes are logged completely randomly and there are no guarantees that a normal host will not get there (on which, maybe, at some point the spamming virus has settled , but now the virus has already been cured, or easier and much more real - one external IP for a large network, in which a spammer has started).
Such databases are not controlled by either the vendor, the supplier of the anti-spam solution, or the client, the solution using. The real situation is when someone forges a sender and sends it to base traps (for example, organizing a stream of spam from a botnet). The last time I was told about a similar case in Samara. As a result of the next update of the DNSBL database, the letters to the domains / addresses in the database will cease to pass. I will not say for all owners of the DNSBL bases, but they also talked about situations when deletion from the bases happens for money.
Filtering spam based on greylisting technology . Here opinions differ. Who says that it is effective, who says that at the moment spammers stupidly ignore the delay in receiving letters. Quite possibly this is due to spamming technologies. When sending it through a botnet, the delay can be ignored; when using a special server, they can be critical.
Vulnerability analysis systems . The thing is necessary, but you cannot trust it blindly. As practice shows, they know only known vulnerabilities - you should not rely that all vulnerabilities will be found by them. Accordingly, unknown malware will penetrate. Again, there are very serious doubts that the vulnerability scan engines used in personal antivirus systems correspond to the level of special products. I did not see any descriptions of the technology, its limitations.
Virtual keyboards . They are promoted as one of their pillars for the protection of personal information, passwords for remote banking services and so on.
The virtual keyboard protects against interception of personal information only when working with Microsoft Internet Explorer, Mozilla Firefox and Google Chrome browsers. When working with other browsers, the Virtual Keyboard does not protect the entered personal data from interception.
The virtual keyboard is not available in Microsoft Internet Explorer 10 from the Windows Store, as well as in the Miscrosoft Internet Explorer 10 browser, if the Enable enhanced Protected Mode check box is selected in the browser settings. In this case, it is recommended to invoke the virtual keyboard from the Kaspersky Internet Security interface.
The virtual keyboard cannot protect your personal data in case of hacking a web site that requires the input of such data, since in this case the information will fall directly into the hands of intruders.
How many have heard of such restrictions?
Many spyware programs have the functions of taking screenshots, which are automatically transferred to the attacker for further analysis and extraction of personal user data. The virtual keyboard protects the entered personal data from interception by taking screenshots.
The virtual keyboard does not prevent taking screenshots by pressing the Print Screen key and other key combinations specified in the operating system settings, as well as taking screenshots using DirectX technology.
Very interesting combination of two paragraphs. Thus, a malicious program that can take screenshots of information will completely remove keystrokes on the virtual keyboard.
And now a quote from a marketing document:
Also, to ensure secure data entry, a virtual keyboard and a special driver are used to protect data entry on a hardware keyboard. As a result, protection is provided against programs that register keystrokes (keylogger) and screenshots (screenshot).
Password Managers The idea of storing passwords on a computer is not bad in itself, but such programs also have vulnerabilities and can be cracked .
Cloud Antivirus . The network is present in a huge number of panegyrics cloud technologies. As far as you can understand, cloud systems are based on two whales - a file (link) gets a positive reputation if it didn’t cause problems for a large number of users and the reputation from the cloud is higher than the opinion of the local system . Theoretically, a situation is possible when an unknown (not detectable) virus spreads across users (say on a botnet), gets a high reputation and only then introduces the desired victim - and the opinion of the local antivirus will be ignored. If at the time of implementation, the system administrator tries to change the file's reputation, it is not a fact that it will succeed. Opinion million lemming. Until the file gets to the laboratory for analysis, it will be distributed freely
Is there a plus for technology? Yes.
- The ability to assess the reputation of a file between updates of anti-virus databases;
- When organizing a local cloud, this technology allows you to exclude cross-checking of identical files on different machines connected to the cloud. In essence, checksums are cached.
Systems based on change control, including cloud . Based on the calculation of checksums. The technology at the time of occurrence is breakthrough, allowing you to reduce the scan time, but now there are updates every hour and even more. Since at the time of the arrival of a new update in the system there may be a previously unknown malicious file, the checksums of the files need to be recalculated after each update, that is, approximately once an hour, which increases the braking of the system. Plus, again, not all control systems are the same. Just control over the files costs - just by changing the path that the program runs.
The biggest disadvantage of products based on state control is the inability to protect against an unknown threat. They are not able to remove already running malware.
Proactive systems based on knowledge of program behavior profiles . They require that all profiles of all existing programs in the world be available in the database (taking into account their updates - after all, old versions can work for users), which is unrealistic - including the fact that programs are constantly updated. This leads to the fact that the user is sometimes requested permission for a particular action. The user is not able to distinguish a request for a virus from a request for an ordinary program.
Integration of antivirus with corporate management systems and updates . Using systems such as Microsoft Update, MMC, and so on. Integration with corporate management systems allows, in particular, without switching between management system interfaces, to monitor the status of the entire network. A huge plus. But it is possible that a hacker, having gained access to a corporate management system, will demolish the same antivirus and leave the network unprotected. All of these systems are not under the control of the self-defense system and can be intercepted by an intruder.
Wheels of course now rubber:
to work with ... you must have the Microsoft .NET Framework 4 package. If it is not available, it launches its installation, which requires at least another 800 MB of disk space.
But how safe is the situation when the control system is built on an external library, which can be modified at any time by a hacker?
Barring incoming channels during RBS operation . It does not make sense if the BOB is intercepted by malware.
Confirmation of payments by SMS . SMS can be modified by malware introduced by phishing such as
Protection of billing data during transmission - data encryption. Great thing, but it is often forgotten that the data can be modified before it enters the protected channel - a virus can be between the client program and the trusted channel.
Protected runtime environments . Malicious programs can recognize being in a protected environment and at this time do nothing wrong. Well, the protected environment itself can be hacked.
Again, not a panacea.
Antivirus for virtualization systems .
First of all, anti-virus protection is supported only for Windows. To implement the agentless scenario for Linux virtualization / Unix / ... you will have to wait for VMware. Secondly, ... the quarantine function for files and infected virtual machines does not work. Those. caught malware can only kill, cure or blow the signal to the sysadmin. Thirdly ... Alas - all these are also the features of the API from VMware.
Quote from the article: Eugene Kaspersky Ambitions, laziness and greed in IT business
The most interesting thing is that for systems based on the API, VmWare is not at all clear - can these systems deal with previously known malware? Can they remove already running malware, etc.?
Protection against viruses by formatting the system . The virus can not only be in the form of a file.
Naturally, this is not all that is used to ensure security, but the above list is enough to conclude. There is no panacea. Blindly believing journalists and marketers is impossible. You should always check any statements. Especially when another wave of fashion rises.
Source: https://habr.com/ru/post/266323/
All Articles