Peering network base.network

“ Freedom is an opportunity to say that twice two is four. If this is allowed, everything else follows from here. "
George Orwell - "1984"
Various distributed technologies are actively developing in the modern world. Such projects as the peer-to-peer payment system Bitcoin, distributed microblogs (Twister), distributed messengers (for example, Tox) have been successfully operating for years. It came to complete distributed sites.
Partially functional distributed sites have already been implemented in projects such as Freenet and I2P. However, such projects have several disadvantages. For example, at present, Freenet cannot be used to create or distribute dynamic content, such as using databases or scripts. To access such networks, it is often necessary to install special software or download huge databases. Many peer-to-peer networks have a great response time. Between the publication of information and when it sees the rest of the users a lot of time passes.
')
The proposed base.network system is designed to eliminate such disadvantages of peer-to-peer networks and combine all the technical advantages of centralized systems with the freedom to exchange information in distributed networks.
This is a kind of attempt to create a secure decentralized network with low response time and autonomy, resiliency and scalability properties. The key goal of the project is the ability to function even under pressure from organizations that control, suppress publication, and also limit access to information on the Internet. All aspects of the project are available as open source and free. This allows you to make sure that the software does exactly what is stated, and allows all developers to improve the protection of the network from attempts to limit the free flow of information.
base.network - What is it?
This is a peer-to-peer network designed for decentralized distributed data storage without the possibility of censoring it. The system has no central servers and is not under the control of any individuals or organizations. Created to provide users with freedom of speech in the online space. The system works on the basis of combining server nodes provided by network members free of charge into a common cluster. All data is evenly distributed between the server nodes and do not require central storage. Participants provide the bandwidth and disk space of their servers for publishing or receiving various kinds of information on the Web. For example, files, data structures, and ordered lists.
As a result, such a data storage scheme allows for the implementation of dynamic applications, such as blogs, news channels, comments, closed group correspondence, media lists, search indexes and directories. A feature of these applications is the resistance to interruptions due to the decentralized system architecture. Another important feature is the impossibility of censoring by third parties, including application developers.
All data uploaded to the system must be signed by the author using public-key cryptosystems. It is always possible to check the authorship of certain data by knowing the author's public key. As a cryptographic algorithm for creating digital signatures and data encryption, the system uses an asymmetric public key encryption algorithm based on ECDSA (Elliptic Curve Digital Signature Algorithm) with a key length of 256 bits (in particular, the secp256k1 curve) and the SHA-256 hash function.
How is the network
In the system, unlike other peering networks, the concept of server and client is divided. Client software is a regular browser, which makes the network more accessible to use for the average user compared to many other peer-to-peer networks.
All network data is stored on servers provided by the participants at no charge. Ideally, dedicated server nodes have access to a good Internet channel, which allows users to get quick access to network resources.
So, system participants provide their server resources to maintain the network. To do this, they install a special server software, which essentially is a small web server and database in one person - the so-called server node . For the node to work, you must allocate an external IP address (v4) and a free port.
Data storage
To begin with, in order to understand the organization of data storage, let us imagine that the entire network space is limited to a strictly defined amount, say, 32 GB. Thus, the network turns into a huge hash table, where each document at its hash address will strictly have its place in the virtual network space. In order not to store all the network data on one physical machine (as it was done, for example, in the Bitcoin system), we will divide our entire virtual space into a number of segments. To begin with, let's divide it into, say, 8 segments. Each segment is 4GB. Now, dedicated physical machines can individually serve individual segments, without the need to store a complete copy of the database, but only a piece of it. Each such server node can support several network segments. The same segment will be served by several independent nodes. Knowing the physical addresses of machines, and having information about which segments are serviced by which machines, we can always access a separate document at its address. Access to the nodes is via the standard http protocol.
After users add data to one of the nodes, the information is immediately synchronized between all the nodes serving the same segment, using the same http protocol.
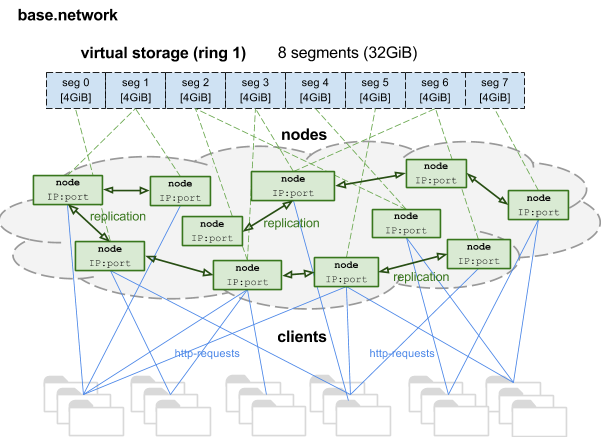
Rings
It was stated above that the network space is limited to a certain amount (32 GB) and the network thus works like a huge hash table. All this is true for the virtual space limited within the framework of one so-called Ring.
The ring system was designed to freely scale the virtual storage of the network and not strictly limit its space. As the data of the current rings is filled, the network will use the following virtual rings. The number of segments for each next ring increases by 8 times, the size of the segments in turn also increases several times. More precisely, in the number of times multiple of two, for different types of storage, this number will be different (see below Types of storage). Thus, the total volume of each next ring is an order of magnitude greater than the size of the previous one and allows you to place more and more data. The potential growth in popularity of the network and, as a result, the increase in the number of machines makes it possible to service the following rings, allowing the network to achieve essentially unlimited growth.
For example, to store files, the number of segments in the first ring is 8. In the second 64., etc. The size of the segments increased by 2 times. The volume of each following ring, thus, increases by 16 times. And, for example, for the third ring it will be 16 TB. And for the 5th already 4 PB!
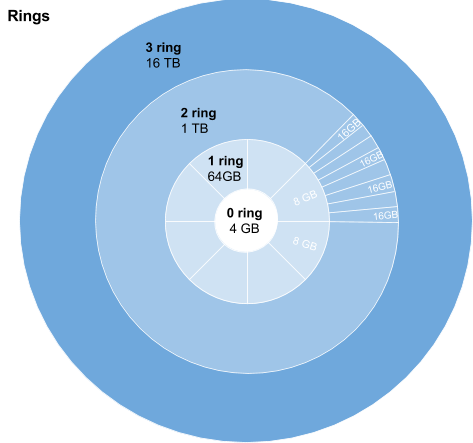
In the zero ring is always located one segment. It usually contains key information for the network.
Nodes
As mentioned above, the nodes are a small web server with a dedicated IP address and port. Each node of the network has information about the rest of its members. You can get a map of the entire network by making a special http request to any node.
curl http://5.9.123.140:8080/-/nodes {"nid":"5.9.123.140/8080","ver":1,"seg":"D,N,F,P,D0,D1,D2,D3,D4,D5,D6,D7,F0,F1,F2,F3,F4,F5,F6,F7,P0,P1,P2,P3,P4,P5,P6,P7,D06,D64,F50,P00,P55,P77"} {"nid":"46.4.76.98/8081","ver":1,"seg":"D,N,F,P,D0,D1,D2,D3,D4,D5,D6,D7,F0,F1,F2,F3,F4,F5,F6,F7,P0,P1,P2,P3,P4,P5,P6,P7,D57,D66,F41,F54,P04"} When you first connect to the system, the node tries to get a network map by contacting at least one of the nodes specified in its original list.
The server version of a particular node, which segments it maintains, and how full they are, can also be obtained by making the following http request:
curl http://5.9.123.140:8080/-/about {"ver":1,"nid":"5.9.123.140/8080","segments":{"D":{"usage":0},"N":{"usage":0},"F":{"usage":0},"P":{"usage":0},"D0":{"usage":0},"D1":{"usage":0},"D2":{"usage":0},"D3":{"usage":0}," ... , "updated":1441639911027} After synchronization of information, the node informs other participants about itself. They in turn, making sure that the new node is correct, update their network map.
Addressing documents
To receive (or save) any document on the network, we need to know its address. The address can be any string identifier. From this string address, a hash is calculated (using the SHA-256 algorithm) - the so-called uid (unique document identifier). For files with a similar identifier, a hash from the contents of the file appears. The first digits of the received hash will tell us about the number of the segment in which the document is located. For example,
document URI:
D2/my-domain.base/path/document.txt path:
my-domain.base/path/document uid - sha256 (path) (hex):
49ea72cbd1de7f2d...3cf23d49778 uid (oct):
2236516262750736...44365113570 document`s coordinates:
storage: D ring: 2 uid: 49ea72cbd1de7f...f23d49778 segment: D22 Now, knowing the segment number and the list of nodes servicing this segment, as well as their external IP addresses and ports, we can contact any physical machine and request the document using the usual http request. To form such requests, the user does not need to install special software. As a client software can be a regular browser.
All data networks have an author. At the time of publication, each document must necessarily have its digital signature, which is generated by the private key of its author. Subsequently, the authorship of each document can be verified using its public key.
All documents in the system are characterized by the following parameters:
- storage - The type of storage. It is specified as a single character. For example F, N, D, P
- ring - the number of the ring in the repository (integer)
- uid - unique resource identifier (hex64)
In general, a link to a single document or data list will look like this:
<storage:char><ring:int>/<uid:hex64> For some types of storage, such as file storage, the list of parameters will be slightly wider. For example:
- extention - file extension. Speaks about the type of content.
- aid is a unique identifier of the author (a hash of his public certificate with a length of 20 characters), is required when we request information only of a specific author for the specified address.
Link example:
F1/ef43c9adc8aeec6910b4373ba0d9fbf28048ed53ec631ab9fd6fa8ad00a8a3a0.txt D4/930bbc0fa952dcc8eb7e8a711ac953c61f76f86fecd1ba7b0b5c4e74834e12bf?aid=Ipf8SOrpxbgYnNMXszFk Storage Types
Currently, the system implements 4 types of data warehouses, each of which allows you to store different information structures.
- F - file storage
- N - domain name storage, certificates
- D - data lists of one author
- P - public data lists
Let's tell a little more about each of them.
File Storage (Storage Type F)
Files, unlike string data, have some specificity in addressing. The file address (its uid) is the sha-256 hash from its contents. Thus, the same file, flooded into the network by different users, will have the same address. You can make sure that the correct content is returned to the specified address by checking its hash. The type of content (Content-Type) of the file is indicated directly in the link as an extension (extention).
For example, the following link
F1/ef43c9adc8aeec6910b4373ba0d9fbf28048ed53ec631ab9fd6fa8ad00a8a3a0.txt will match the document with the parameters:- storage = F - type of storage “Files”,
- ring = 1 - the first ring
- uid = ef43 ... a3a0 - unique file identifier,
- extention = txt - file extension to which the content type (“text / plain”) corresponds
For a given uid, transferring it to the octal system, using the first digit, we get the segment number. It corresponds to "7". Now, knowing all the nodes that serve the segment with the name “F7”, as well as the physical addresses of the nodes, we can get the document itself:
curl -i http://5.9.123.140:8080/-/F7/data/ef43c9adc8aeec6910b4373ba0d9fbf28048ed53ec631ab9fd6fa8ad00a8a3a0.txt HTTP/1.1 200 OK Content-Type: text/plain; charset=utf-8 Cache-Control: max-age=315360000, public Expires: Sun, 17 Aug 2025 15:18:30 GMT Access-Control-Expose-Headers: x-base-author x-base-author: AA3Evvx1AR...i8UONOm92Q== Connection: keep-alive Transfer-Encoding: chunked TEST FILE Now let's check the hash from the contents of the received document:
curl http://5.9.123.140:8080/-/F7/data/ef43c9adc8aeec6910b4373ba0d9fbf28048ed53ec631ab9fd6fa8ad00a8a3a0.txt|shasum -a 256 ef43c9adc8aeec6910b4373ba0d9fbf28048ed53ec631ab9fd6fa8ad00a8a3a0 - Everything is in order: it corresponds to our requested uid.
Below is a table of correspondences of the number of segments and the size of the ring, depending on its number for the file storage type.
Params of F-storage
| ring | Size of segment GB | Count of segments | TOTAL SIZE OF RING | Max Size of Data Pack, KB | Min count of records |
| 0 | 2 | one | 2 GB | 2 | 1.05E + 06 |
| one | four | eight | 32 GB | sixteen | 2.10E + 06 |
| 2 | eight | 64 | 512 GB | 128 | 4.19E + 06 |
| 3 | sixteen | 512 | 8 TB | 1,024 | 8.39E + 06 |
| four | 32 | 4,096 | 128 TB | 8 192 | 1.68E + 07 |
| five | 64 | 32,768 | 2 PB | 65,536 | 3.36E + 07 |
| 6 | 128 | 262 144 | 32 PB | 524 288 | 6.71E + 07 |
| 7 | 256 | 2,097,152 | 512 PB | 4 194 304 | 1.34E + 08 |
It is worth paying attention to the fact that the permissible size of one file in each ring is limited to a certain size. This is done to ensure that the network is not “killed” by uploading huge files by unscrupulous users. As can be seen from the table, restrictions on file sizes decrease as the network grows and subsequent rings are captured by new nodes.
It should also be taken into account that this type of storage is available for recording only to registered users (with a certificate signed by a registrar) and does not allow users to add files with an anonymous certificate. This restriction is introduced in order to protect against potential flooding and not to clog the store with any unnecessary information.
Domain names (storage type N)
This type of storage is required to store information about domain names, domain owners and public certificates of registered users. This type of storage is available for recording only to domain zone registrars. At the moment it is the only one - it is a registrar of the virtual domain zone .base. The public key of the registrar is known to all network participants and is hard-wired directly in the client and server software.
The size of the zero storage ring segment is 8 GB. This size should theoretically be long enough to store all data on domains and certificates exclusively in one segment of the zero ring. Thus, obtaining information on the domain name will occur without searching in different rings.
So the N-type repository is a kind of huge hash table. By the domain name, you can request information about the owner of the domain and its public key.
For example, for the test.base.network domain, the following data will be returned to us:
curl 'http://5.9.123.140:8080/-/N/data/test.base' {"ver":0,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWw=","hash":"yU6mMInrZqN43/ggsj+0J/g1rpsMs+lFiO7LuoXGwRo=","sign":"vB00Eewv7hzVrvtGUhUtjOHvU8u7uM0KujyId+py6GvJdwBNkInw8FeUX1+DYYFtygFX5QyB70BShhDv9Gd9ZA==","data":"eyJvd25lciI6IkFBM0V2dngxQVJEVlZ5aVBXWjExOTdsM01BT1BlMlUxRlI3aGp4UXBMNlRRbXFmOGR4RUVvQi9BVjE5VW00OXU5VTdMYjhMeDl1algyTXVyVGQ2cW5XeHVFeHhhdExQb1BadWtPdS9iTktkZEVqbm9VeDljZ0UzMzlnWkdzQUJWRGMvWDFGS1dPMjJGOElJejVxamF5b2R2ZklZZHZ0WmRjUEdXVm1rWUxYdngifQ=="} This information is signed by the registrar's root certificate and the client can always verify its validity. Having decoded the data from base64, we will receive the following information about the domain in the form of JSON. The owner is the public certificate of the domain owner.
{"owner":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx"} Now, knowing the certificate of the owner of the domain, we can request the manifest of the site - data on the settings, structure, engine and name of the site.
Data lists (storage type D)
In addition to single documents, there is an opportunity to work with lists of data in the network, to form so-called tapes. Lists, like single documents, are arranged by a specific unique identifier uid. The list widget is the sha256 hash from its string address. However, for this type of storage, in contrast to the first two, it is possible to request lists of documents of a given author with a given sorting order and offsets. In fact, this storage implements a simple index that allows you to return ordered data.
For example, the address of the test.base.network/blog list will match the following uid
sha256(“test.base/blog/”) -> e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438 Now we can request a list of documents that are authored in this case by the owner of the site test.base.network (with aid = Ipf8SOrpxbgYnNMXszFk). By default, the records are sorted in the reverse order of addition time.
curl -i 'http://5.9.123.140:8080/-/D7/data/e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438?aid=Ipf8SOrpxbgYnNMXszFk' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:38:44 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA3MTkwOTI1NDU5ODg=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"MWEyLxrkDosW2FU3+GTYXk045PN8TBhsiloovkxuTvA=","sign":"rgtR7qJXc5GMbm7TxZijbQiKOtH9gpWhUUt7z6L2yetEcRR7bUdVxmW9UvUPVaMfq1LpVEcZ4IF2CuQf4NVvHw==","data":"eyJ0aXRsZSI6...sbCJ9"} {"pos":"MjAxNTA3MTkwOTEzNTY0NzE=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"7r+ZfOVi+2/ZkRFeHwNytk20j6xTZKvJ73m1GCuXsFY=","sign":"ZpZBWLrUT1RZ/s+5ea8o6ckG2dfqqzUkKkQMUjAnVoC3pRzaGW4Q3lV8/rUjDpCdCWPum9juA2tDNBLG+qqL1g==","data":"eyJkZXNjcm...iYWxsIn0="} ... ", "ver": curl -i 'http://5.9.123.140:8080/-/D7/data/e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438?aid=Ipf8SOrpxbgYnNMXszFk' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:38:44 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA3MTkwOTI1NDU5ODg=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"MWEyLxrkDosW2FU3+GTYXk045PN8TBhsiloovkxuTvA=","sign":"rgtR7qJXc5GMbm7TxZijbQiKOtH9gpWhUUt7z6L2yetEcRR7bUdVxmW9UvUPVaMfq1LpVEcZ4IF2CuQf4NVvHw==","data":"eyJ0aXRsZSI6...sbCJ9"} {"pos":"MjAxNTA3MTkwOTEzNTY0NzE=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"7r+ZfOVi+2/ZkRFeHwNytk20j6xTZKvJ73m1GCuXsFY=","sign":"ZpZBWLrUT1RZ/s+5ea8o6ckG2dfqqzUkKkQMUjAnVoC3pRzaGW4Q3lV8/rUjDpCdCWPum9juA2tDNBLG+qqL1g==","data":"eyJkZXNjcm...iYWxsIn0="} ... AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu / bNKddEjnoUx9cgE339gZGsABVDc / X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx", "hash": "MWEyLxrkDosW2FU3 + GTYXk045PN8TBhsiloovkxuTvA =", "sign": "rgtR7qJXc5GMbm7TxZijbQiKOtH9gpWhUUt7z6L2yetEcRR7bUdVxmW9UvUPVaMfq1LpVEcZ4IF2CuQf4NVvHw ==" curl -i 'http://5.9.123.140:8080/-/D7/data/e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438?aid=Ipf8SOrpxbgYnNMXszFk' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:38:44 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA3MTkwOTI1NDU5ODg=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"MWEyLxrkDosW2FU3+GTYXk045PN8TBhsiloovkxuTvA=","sign":"rgtR7qJXc5GMbm7TxZijbQiKOtH9gpWhUUt7z6L2yetEcRR7bUdVxmW9UvUPVaMfq1LpVEcZ4IF2CuQf4NVvHw==","data":"eyJ0aXRsZSI6...sbCJ9"} {"pos":"MjAxNTA3MTkwOTEzNTY0NzE=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"7r+ZfOVi+2/ZkRFeHwNytk20j6xTZKvJ73m1GCuXsFY=","sign":"ZpZBWLrUT1RZ/s+5ea8o6ckG2dfqqzUkKkQMUjAnVoC3pRzaGW4Q3lV8/rUjDpCdCWPum9juA2tDNBLG+qqL1g==","data":"eyJkZXNjcm...iYWxsIn0="} ... ", "ver": curl -i 'http://5.9.123.140:8080/-/D7/data/e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438?aid=Ipf8SOrpxbgYnNMXszFk' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:38:44 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA3MTkwOTI1NDU5ODg=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"MWEyLxrkDosW2FU3+GTYXk045PN8TBhsiloovkxuTvA=","sign":"rgtR7qJXc5GMbm7TxZijbQiKOtH9gpWhUUt7z6L2yetEcRR7bUdVxmW9UvUPVaMfq1LpVEcZ4IF2CuQf4NVvHw==","data":"eyJ0aXRsZSI6...sbCJ9"} {"pos":"MjAxNTA3MTkwOTEzNTY0NzE=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"7r+ZfOVi+2/ZkRFeHwNytk20j6xTZKvJ73m1GCuXsFY=","sign":"ZpZBWLrUT1RZ/s+5ea8o6ckG2dfqqzUkKkQMUjAnVoC3pRzaGW4Q3lV8/rUjDpCdCWPum9juA2tDNBLG+qqL1g==","data":"eyJkZXNjcm...iYWxsIn0="} ... AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu / bNKddEjnoUx9cgE339gZGsABVDc / X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx", "hash": "7r + ZfOVi + curl -i 'http://5.9.123.140:8080/-/D7/data/e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438?aid=Ipf8SOrpxbgYnNMXszFk' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:38:44 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA3MTkwOTI1NDU5ODg=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"MWEyLxrkDosW2FU3+GTYXk045PN8TBhsiloovkxuTvA=","sign":"rgtR7qJXc5GMbm7TxZijbQiKOtH9gpWhUUt7z6L2yetEcRR7bUdVxmW9UvUPVaMfq1LpVEcZ4IF2CuQf4NVvHw==","data":"eyJ0aXRsZSI6...sbCJ9"} {"pos":"MjAxNTA3MTkwOTEzNTY0NzE=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"7r+ZfOVi+2/ZkRFeHwNytk20j6xTZKvJ73m1GCuXsFY=","sign":"ZpZBWLrUT1RZ/s+5ea8o6ckG2dfqqzUkKkQMUjAnVoC3pRzaGW4Q3lV8/rUjDpCdCWPum9juA2tDNBLG+qqL1g==","data":"eyJkZXNjcm...iYWxsIn0="} ... : " curl -i 'http://5.9.123.140:8080/-/D7/data/e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438?aid=Ipf8SOrpxbgYnNMXszFk' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:38:44 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA3MTkwOTI1NDU5ODg=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"MWEyLxrkDosW2FU3+GTYXk045PN8TBhsiloovkxuTvA=","sign":"rgtR7qJXc5GMbm7TxZijbQiKOtH9gpWhUUt7z6L2yetEcRR7bUdVxmW9UvUPVaMfq1LpVEcZ4IF2CuQf4NVvHw==","data":"eyJ0aXRsZSI6...sbCJ9"} {"pos":"MjAxNTA3MTkwOTEzNTY0NzE=","ver":3,"author":"AA3Evvx1ARDVVyiPWZ1197l3MAOPe2U1FR7hjxQpL6TQmqf8dxEEoB/AV19Um49u9U7Lb8Lx9ujX2MurTd6qnWxuExxatLPoPZukOu/bNKddEjnoUx9cgE339gZGsABVDc/X1FKWO22F8IIz5qjayodvfIYdvtZdcPGWVmkYLXvx","hash":"7r+ZfOVi+2/ZkRFeHwNytk20j6xTZKvJ73m1GCuXsFY=","sign":"ZpZBWLrUT1RZ/s+5ea8o6ckG2dfqqzUkKkQMUjAnVoC3pRzaGW4Q3lV8/rUjDpCdCWPum9juA2tDNBLG+qqL1g==","data":"eyJkZXNjcm...iYWxsIn0="} ... The validity and authorship of each such record can be checked by its hash (hash) and signature (sign), formed by the author when adding the document.
In addition, D and P storages provide customers with the ability to subscribe to adding recordings to tape using SSE (Server-Sent Events) technology. For example, the following query can subscribe to add data to our feed. The client will open the connection and wait for a server event to occur.
http://5.9.123.140:8080/-/D7/listen/e1d8f9c396164dbbb8debf9c0ce08805bcf4bd8d98c2cc462c8bc21c21f27438?aid=Ipf8SOrpxbgYnNMXszFk As for files, anonymous users do not have the opportunity to form their own tapes, and only registered users can add new items to the list (with a certificate with a registrar signature).
In conclusion, the characteristics of its rings are given for this type of storage. Like files, initially the size of a single record is strongly limited. In the first ring, they are only 16 KB. However, this should be quite enough for the development of dynamic services such as posts, blogs, catalogs, playlists, various lists, etc.
Public data lists (storage type P)
This type of storage is very similar to the previous one, except that various users, including anonymous, can add items to the same list. Such storage allows you to organize a system of comments, reviews, groups, closed correspondence of two or more users.
For example, the http address of the list is http://test.base.network/chat/ will correspond to the following uid (= SHA256 (“test.base / chat /”))
be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4
curl -i 'http://5.9.123.140:8080/-/P5/data/be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:29:47 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA4MTQwODQ5MzYyOTA=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW/ODlXARG8Pk=","sign":"+LG5/taPav00KoRqScABctzjxTlvZIV7nykpqKtxn7AVx6fY4itn7Mtrbisiw5yhf0pC8DLd4akTHYO5C8iWtA==","data":"eyJ0ZXh0IjoidGVzdCAzMzMifQ=="} {"pos":"MjAxNTA4MTQwODQ5MDI0MjQ=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"llOP+Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4=","sign":"EsUH37lW4qF+N/4r0DcgSJKVf4j3UN0uWGHuh6asBbOER539K98o2/DBSCL10YKrA3KCOEHsTE2tsAGf9B/zSQ==","data":"eyJ0ZXh0IjoidGVzdDIyMiJ9"} {"pos":"MjAxNTA4MTQwODA3Mzg1NTI=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir+6q+gs=","sign":"aYF7kB0OVc8gvg5U7TrsBB25+tF/HwpCePHkyyWPVvuS5ylgbxJV5Tb06eb/VIaeEK2Y2gMY23hHcRw4SDT1jQ==","data":"eyJ0ZXh0IjoidGVzdCJ9"} ... ", "ver": curl -i 'http://5.9.123.140:8080/-/P5/data/be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:29:47 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA4MTQwODQ5MzYyOTA=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW/ODlXARG8Pk=","sign":"+LG5/taPav00KoRqScABctzjxTlvZIV7nykpqKtxn7AVx6fY4itn7Mtrbisiw5yhf0pC8DLd4akTHYO5C8iWtA==","data":"eyJ0ZXh0IjoidGVzdCAzMzMifQ=="} {"pos":"MjAxNTA4MTQwODQ5MDI0MjQ=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"llOP+Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4=","sign":"EsUH37lW4qF+N/4r0DcgSJKVf4j3UN0uWGHuh6asBbOER539K98o2/DBSCL10YKrA3KCOEHsTE2tsAGf9B/zSQ==","data":"eyJ0ZXh0IjoidGVzdDIyMiJ9"} {"pos":"MjAxNTA4MTQwODA3Mzg1NTI=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir+6q+gs=","sign":"aYF7kB0OVc8gvg5U7TrsBB25+tF/HwpCePHkyyWPVvuS5ylgbxJV5Tb06eb/VIaeEK2Y2gMY23hHcRw4SDT1jQ==","data":"eyJ0ZXh0IjoidGVzdCJ9"} ... Bl / naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp + fQty6fHcjU =", "hash": "JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW / ODlXARG8Pk =", "sign": "+ LG5 / curl -i 'http://5.9.123.140:8080/-/P5/data/be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:29:47 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA4MTQwODQ5MzYyOTA=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW/ODlXARG8Pk=","sign":"+LG5/taPav00KoRqScABctzjxTlvZIV7nykpqKtxn7AVx6fY4itn7Mtrbisiw5yhf0pC8DLd4akTHYO5C8iWtA==","data":"eyJ0ZXh0IjoidGVzdCAzMzMifQ=="} {"pos":"MjAxNTA4MTQwODQ5MDI0MjQ=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"llOP+Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4=","sign":"EsUH37lW4qF+N/4r0DcgSJKVf4j3UN0uWGHuh6asBbOER539K98o2/DBSCL10YKrA3KCOEHsTE2tsAGf9B/zSQ==","data":"eyJ0ZXh0IjoidGVzdDIyMiJ9"} {"pos":"MjAxNTA4MTQwODA3Mzg1NTI=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir+6q+gs=","sign":"aYF7kB0OVc8gvg5U7TrsBB25+tF/HwpCePHkyyWPVvuS5ylgbxJV5Tb06eb/VIaeEK2Y2gMY23hHcRw4SDT1jQ==","data":"eyJ0ZXh0IjoidGVzdCJ9"} ... ", "ver": curl -i 'http://5.9.123.140:8080/-/P5/data/be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:29:47 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA4MTQwODQ5MzYyOTA=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW/ODlXARG8Pk=","sign":"+LG5/taPav00KoRqScABctzjxTlvZIV7nykpqKtxn7AVx6fY4itn7Mtrbisiw5yhf0pC8DLd4akTHYO5C8iWtA==","data":"eyJ0ZXh0IjoidGVzdCAzMzMifQ=="} {"pos":"MjAxNTA4MTQwODQ5MDI0MjQ=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"llOP+Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4=","sign":"EsUH37lW4qF+N/4r0DcgSJKVf4j3UN0uWGHuh6asBbOER539K98o2/DBSCL10YKrA3KCOEHsTE2tsAGf9B/zSQ==","data":"eyJ0ZXh0IjoidGVzdDIyMiJ9"} {"pos":"MjAxNTA4MTQwODA3Mzg1NTI=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir+6q+gs=","sign":"aYF7kB0OVc8gvg5U7TrsBB25+tF/HwpCePHkyyWPVvuS5ylgbxJV5Tb06eb/VIaeEK2Y2gMY23hHcRw4SDT1jQ==","data":"eyJ0ZXh0IjoidGVzdCJ9"} ... Bl / naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp + fQty6fHcjU =", "hash": "llOP + Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4 =", "sign": "EsUH37lW4qF + N curl -i 'http://5.9.123.140:8080/-/P5/data/be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:29:47 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA4MTQwODQ5MzYyOTA=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW/ODlXARG8Pk=","sign":"+LG5/taPav00KoRqScABctzjxTlvZIV7nykpqKtxn7AVx6fY4itn7Mtrbisiw5yhf0pC8DLd4akTHYO5C8iWtA==","data":"eyJ0ZXh0IjoidGVzdCAzMzMifQ=="} {"pos":"MjAxNTA4MTQwODQ5MDI0MjQ=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"llOP+Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4=","sign":"EsUH37lW4qF+N/4r0DcgSJKVf4j3UN0uWGHuh6asBbOER539K98o2/DBSCL10YKrA3KCOEHsTE2tsAGf9B/zSQ==","data":"eyJ0ZXh0IjoidGVzdDIyMiJ9"} {"pos":"MjAxNTA4MTQwODA3Mzg1NTI=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir+6q+gs=","sign":"aYF7kB0OVc8gvg5U7TrsBB25+tF/HwpCePHkyyWPVvuS5ylgbxJV5Tb06eb/VIaeEK2Y2gMY23hHcRw4SDT1jQ==","data":"eyJ0ZXh0IjoidGVzdCJ9"} ... ", "ver": curl -i 'http://5.9.123.140:8080/-/P5/data/be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:29:47 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA4MTQwODQ5MzYyOTA=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW/ODlXARG8Pk=","sign":"+LG5/taPav00KoRqScABctzjxTlvZIV7nykpqKtxn7AVx6fY4itn7Mtrbisiw5yhf0pC8DLd4akTHYO5C8iWtA==","data":"eyJ0ZXh0IjoidGVzdCAzMzMifQ=="} {"pos":"MjAxNTA4MTQwODQ5MDI0MjQ=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"llOP+Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4=","sign":"EsUH37lW4qF+N/4r0DcgSJKVf4j3UN0uWGHuh6asBbOER539K98o2/DBSCL10YKrA3KCOEHsTE2tsAGf9B/zSQ==","data":"eyJ0ZXh0IjoidGVzdDIyMiJ9"} {"pos":"MjAxNTA4MTQwODA3Mzg1NTI=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir+6q+gs=","sign":"aYF7kB0OVc8gvg5U7TrsBB25+tF/HwpCePHkyyWPVvuS5ylgbxJV5Tb06eb/VIaeEK2Y2gMY23hHcRw4SDT1jQ==","data":"eyJ0ZXh0IjoidGVzdCJ9"} ... Bl / naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp + fQty6fHcjU =", "hash": "XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir + 6q + gs =", "sign": "aYF7kB0OVc8gvg5U7TrsBB25 curl -i 'http://5.9.123.140:8080/-/P5/data/be977147bd78d5a4db7d09aa3a48b3f24c8578c3ea06806d8ff4210f08a2c5a4' HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Access-Control-Allow-Origin: http://core.base.network Date: Tue, 25 Aug 2015 11:29:47 GMT Connection: keep-alive Transfer-Encoding: chunked {"pos":"MjAxNTA4MTQwODQ5MzYyOTA=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"JgRFIFD3AyzsATMNCeAnyxvGgjU7TMmW/ODlXARG8Pk=","sign":"+LG5/taPav00KoRqScABctzjxTlvZIV7nykpqKtxn7AVx6fY4itn7Mtrbisiw5yhf0pC8DLd4akTHYO5C8iWtA==","data":"eyJ0ZXh0IjoidGVzdCAzMzMifQ=="} {"pos":"MjAxNTA4MTQwODQ5MDI0MjQ=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"llOP+Sq5BfIJMZKGfqdCJ5ERq8gPITanj9yDH75PAR4=","sign":"EsUH37lW4qF+N/4r0DcgSJKVf4j3UN0uWGHuh6asBbOER539K98o2/DBSCL10YKrA3KCOEHsTE2tsAGf9B/zSQ==","data":"eyJ0ZXh0IjoidGVzdDIyMiJ9"} {"pos":"MjAxNTA4MTQwODA3Mzg1NTI=","ver":1,"author":"AMywBHKulTlmRXYZ2P+Bl/naYVh9Gx6MACcKYXWd1ypuPrWnJrd0mu7xgAUxrfeArq43zaM9BeQp+fQty6fHcjU=","hash":"XrRlv2sF9ae2GOWehfem6ovLJomZIXtLk27ir+6q+gs=","sign":"aYF7kB0OVc8gvg5U7TrsBB25+tF/HwpCePHkyyWPVvuS5ylgbxJV5Tb06eb/VIaeEK2Y2gMY23hHcRw4SDT1jQ==","data":"eyJ0ZXh0IjoidGVzdCJ9"} ... The characteristics of rings for public lists are very similar to the characteristics of a repository of type D:
P-storage
| ring | Size of segment GB | Count of segments | TOTAL SIZE OF RING | Max Size of Data Pack, KB | Min count of records |
| 0 | 2 | one | 2 GB | 2 | 1.05E + 06 |
| one | four | eight | 32 GB | sixteen | 2.10E + 06 |
| 2 | eight | 64 | 512 GB | 128 | 4.19E + 06 |
| 3 | sixteen | 512 | 8 TB | 1,024 | 8.39E + 06 |
| four | 32 | 4,096 | 128 TB | 8 192 | 1.68E + 07 |
| five | 64 | 32,768 | 2 PB | 65,536 | 3.36E + 07 |
| 6 | 128 | 262 144 | 32 PB | 524 288 | 6.71E + 07 |
| 7 | 256 | 2,097,152 | 512 PB | 4 194 304 | 1.34E + 08 |
The repository also allows clients to subscribe to the event of adding entries to a specific tape through Server-Sent Events.
In conclusion, we can say that potentially the system is not limited to only 4 types of storage. Third-party developers may be offered other types of repositories with more features. For example, such as full-text indexes, servers with the distribution of media streams in real time, storage of aggregated data, statistics, systems for transmitting instant messages between users without storing them on disk, IP telephony, Internet radio, IP television, video conferencing and other streaming protocols and services.
How the network works for the user
For the average user, working with the system begins without installing any special software. To do this, just use a regular browser. For ALL * .base.network / * addresses, a static html page is returned, which includes the code of the client kernel written in JavaScript.
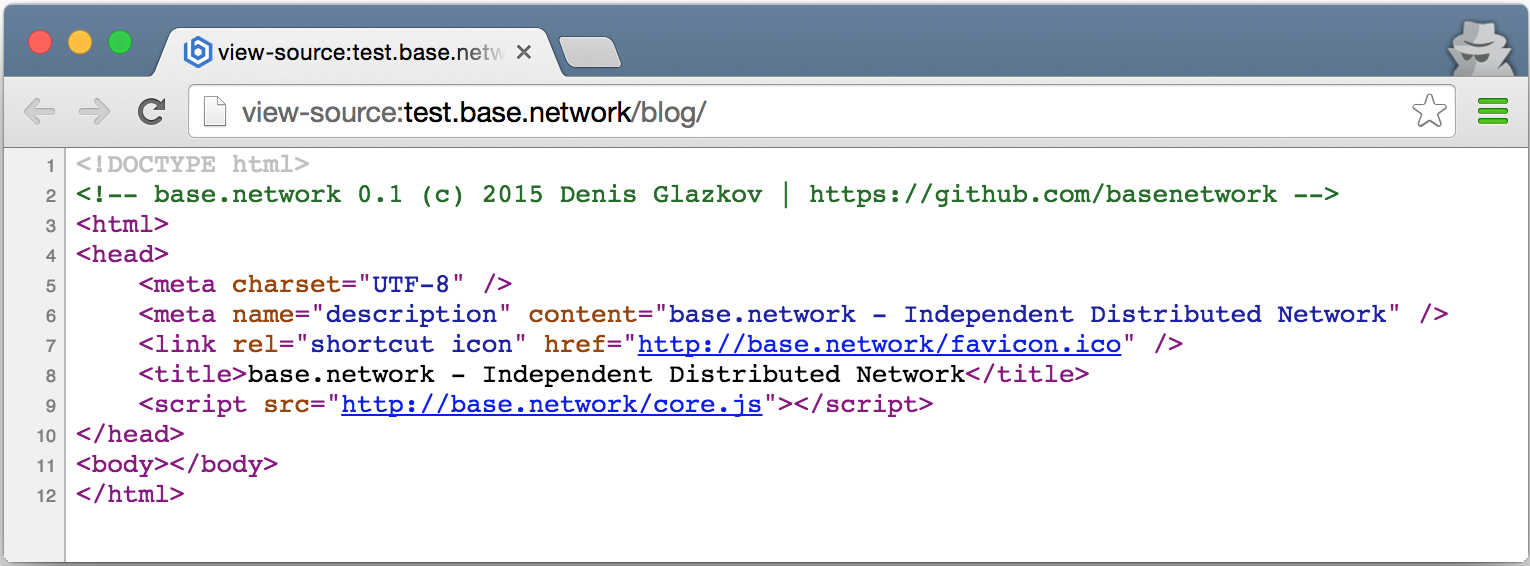
Such a scheme now certainly has a central entry point in the form of the site and the domain base.network, for which you must use the existing domain name system. However, such an assumption can later be easily eliminated by installing a custom browser plug-in. Such a plugin for all * .base.network addresses will return a static page with the base code of the system kernel, without using the current domain name system and without making additional requests to external central resources.
The client core contains the initial list of nodes (their IP addresses and ports). When the engine is first loaded, the script tries to connect to any node from this list and get a fresh network map from it, which it will later store in the browser's LocalStorage. The script will periodically poll nodes from its list and update information about the network. The network map contains a list of all the nodes, their addresses and ports, the version of the server software, as well as a list of the segments serviced by each node. Now on the client enough information to get any document from the network. For any address of the document, we know in which segment it is located and by which nodes this segment is serviced. For faster data download from the network, the client selects the node closest to it. The client can verify the authenticity of the downloaded data by hash and verifying the author's signature using his public key.
When you first log into the network, an anonymous certificate is generated for the user, containing the private and public key. This certificate is stored in the browser LocalStorage in the domain name domain core.base.network. Scripts from other domains do not have direct access to this space and cannot obtain information about the private key.
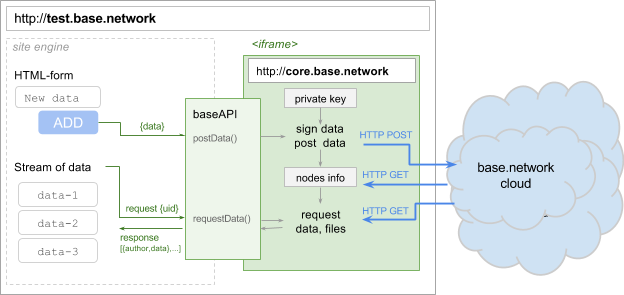
All external http requests are made exclusively from the client core frame - core.base.network. The site engine can work with the system only through this frame, using a special API for this. The API provides the site engine with the ability to upload files to the network, post data, receive data feeds, subscribe to the data add event to the feed.
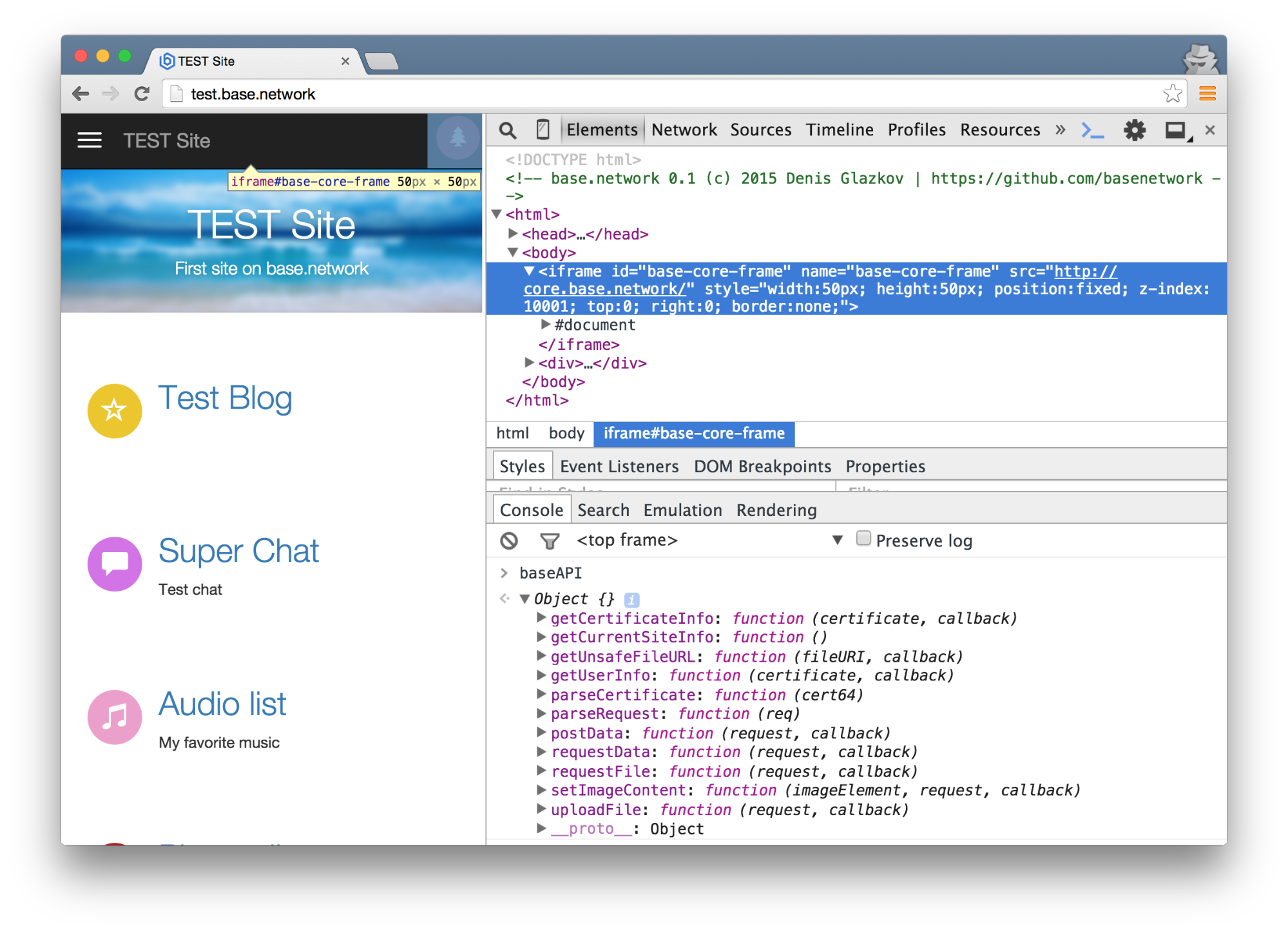
At the time of publication, the kernel signs the data sent by the site engine, using the private key for this, and having a network card in hand, it directly performs a POST request for the necessary nodes.
check in
When the user first visits any site on the network, the kernel automatically generates an anonymous certificate for it. Anonymous certificate has a number of limitations in working with the network. Anonymous users cannot upload files to the network, register their personal domain, website, and also cannot leave comments on certain topics that have corresponding restrictions in access rights.
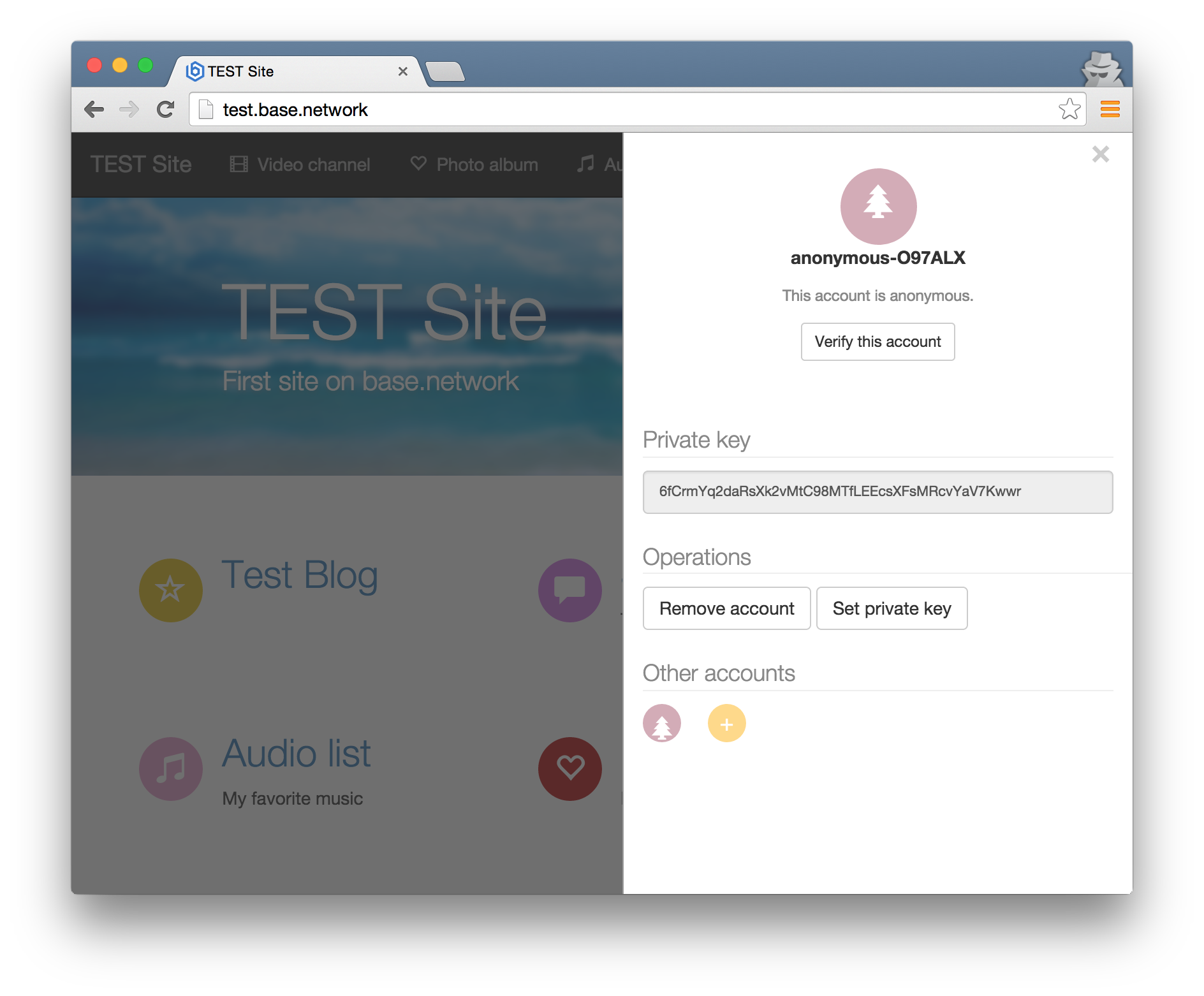
The registration of the certificate takes place simultaneously with the registration of the personal domain assigned by this certificate. Now the concepts of domain and public certificate are inextricably linked. During registration, the user in an encrypted form sends to the registrar his public key and the name of the domain to which the registered certificate will be bound. The registrar adds his signature to the user's public key and places the data on the generated certificate and the domain owner in the storage N domain (storage N), where it will be available to other users.
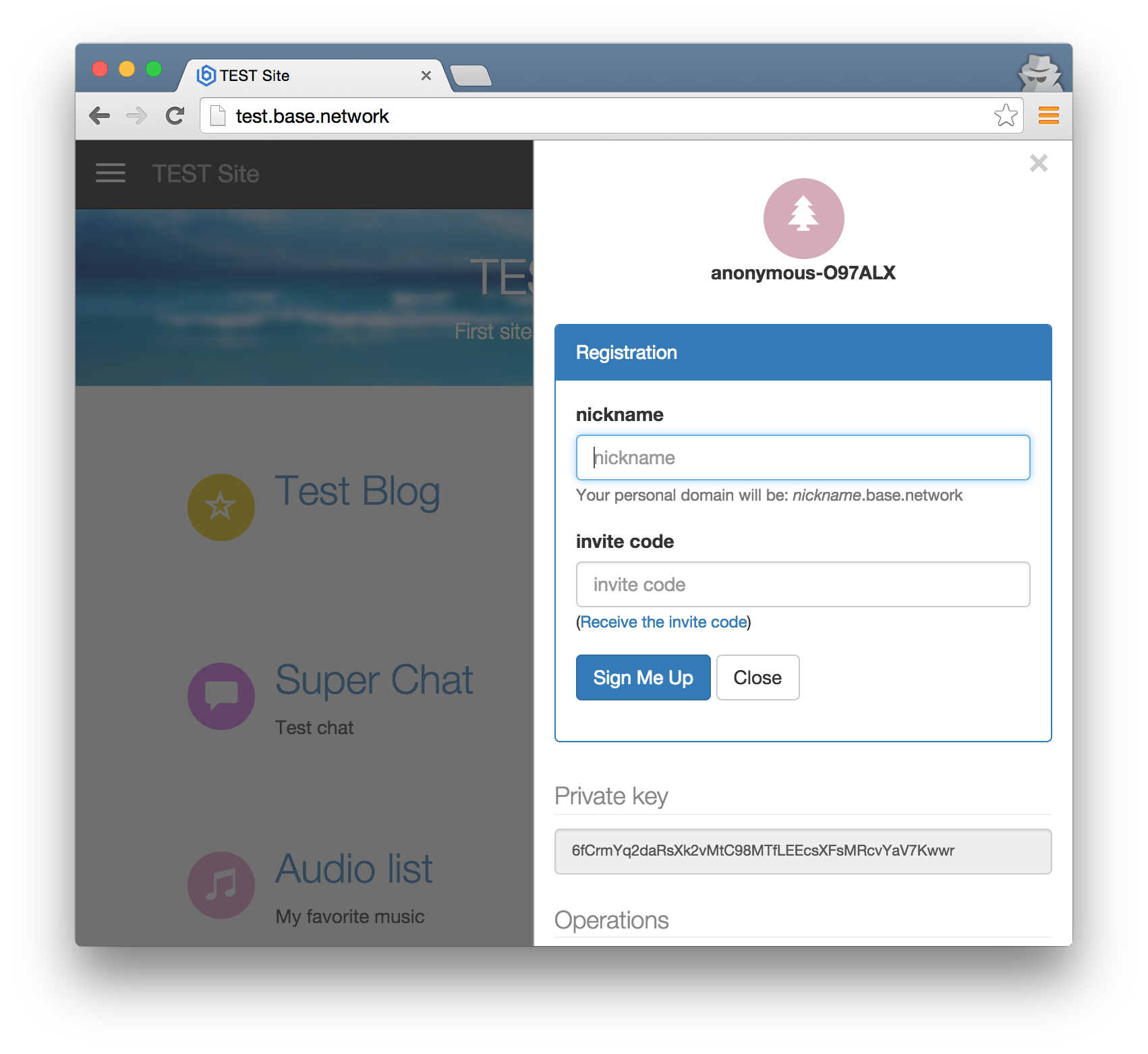
It is worth saying a little about who the Registrar is. A registrar is a root certificate that everyone trusts. The public key of the registrar is sewn directly into the client and server software. Certificates of all registered users include his signature. The registrar signs information about domains and their owners. It is a kind of limiter against random registrations of domains. It is only a domain registrar and does not have the technical ability to change or somehow control the information of sites. He knows nothing about the physical owner of the certificate, its IP-address.
Now the registrar is a certain central figure in the organization of the network, which somewhat contradicts the spirit of the decentralized system design. Subsequently, in the plans to make the registration and transfer of domains completely decentralized. The existing domain registration scheme is chosen solely because of the speed of the network. The user does not need to download a heavy base of all domain names (as it is done, for example, in neimcoin), but it is enough to verify the registrar signature by one entry. In addition, the current registration scheme does not severely limit the number of registrations, which ensures quick entry of participants and further spread of the popularity of the system.
So, a certificate is registered if it has a registrar signature. The domain owner is the person who has the private key of the public certificate. By the existing certificate you can always get information about its owner, including the name of his personal domain. And vice versa. By the domain name you can always get a public certificate of its owner. Information about the domain and certificate is signed by the registrar and it can always be obtained from the N-repository and checked for authenticity.
At the moment registration is happening on invite. The invite code can be obtained by any person with a gmail account. For one gmail-account you can get one invite. A similar system of invitations is introduced solely in order to at least somehow restrict uncontrolled domain registrations at the initial stage of the system operation. gmail- -. - , , .
Acquaintance.
. , , . , .
, , , , , , , . , : http://test.base.network/ .
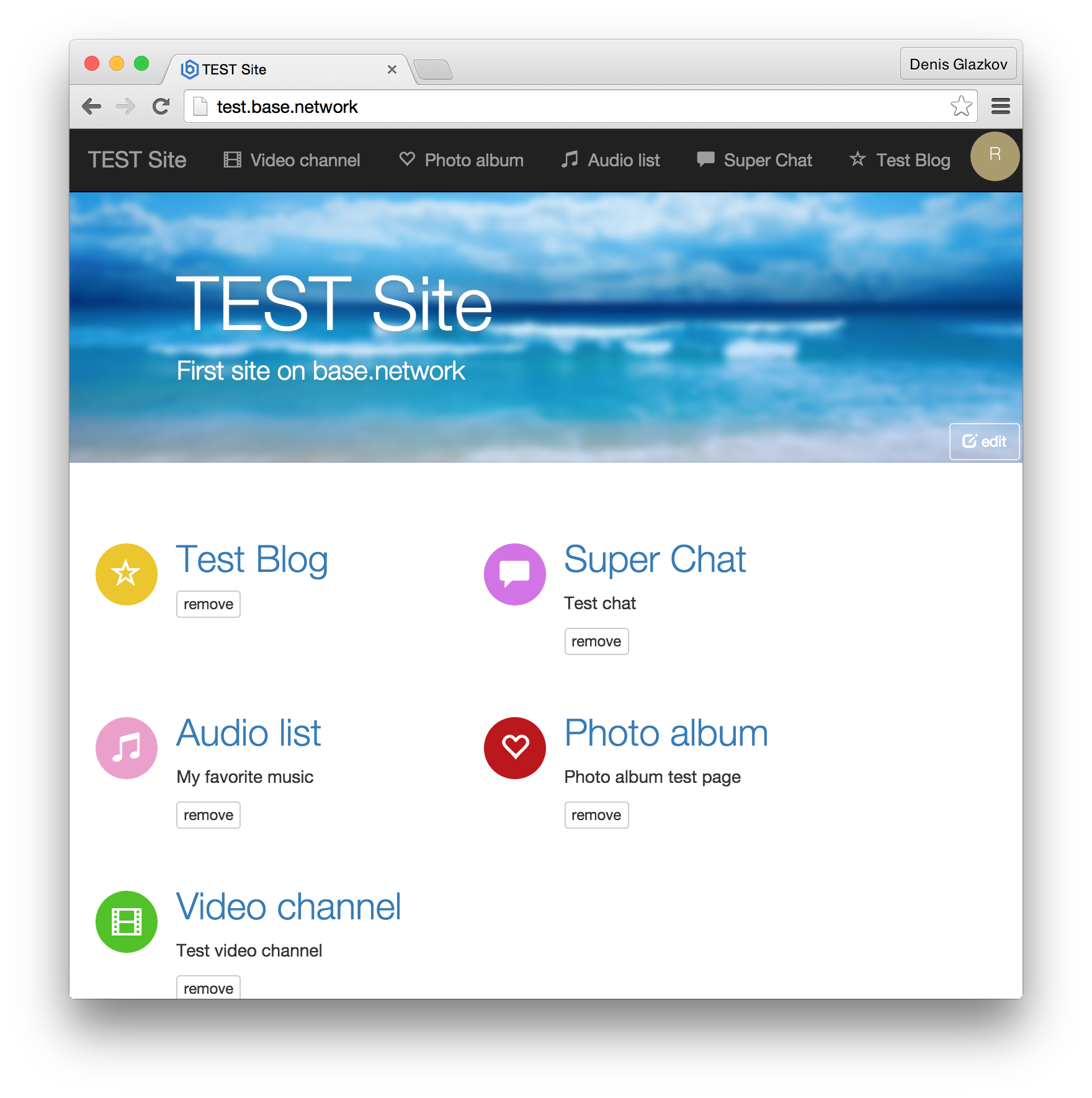
:
, , , . .
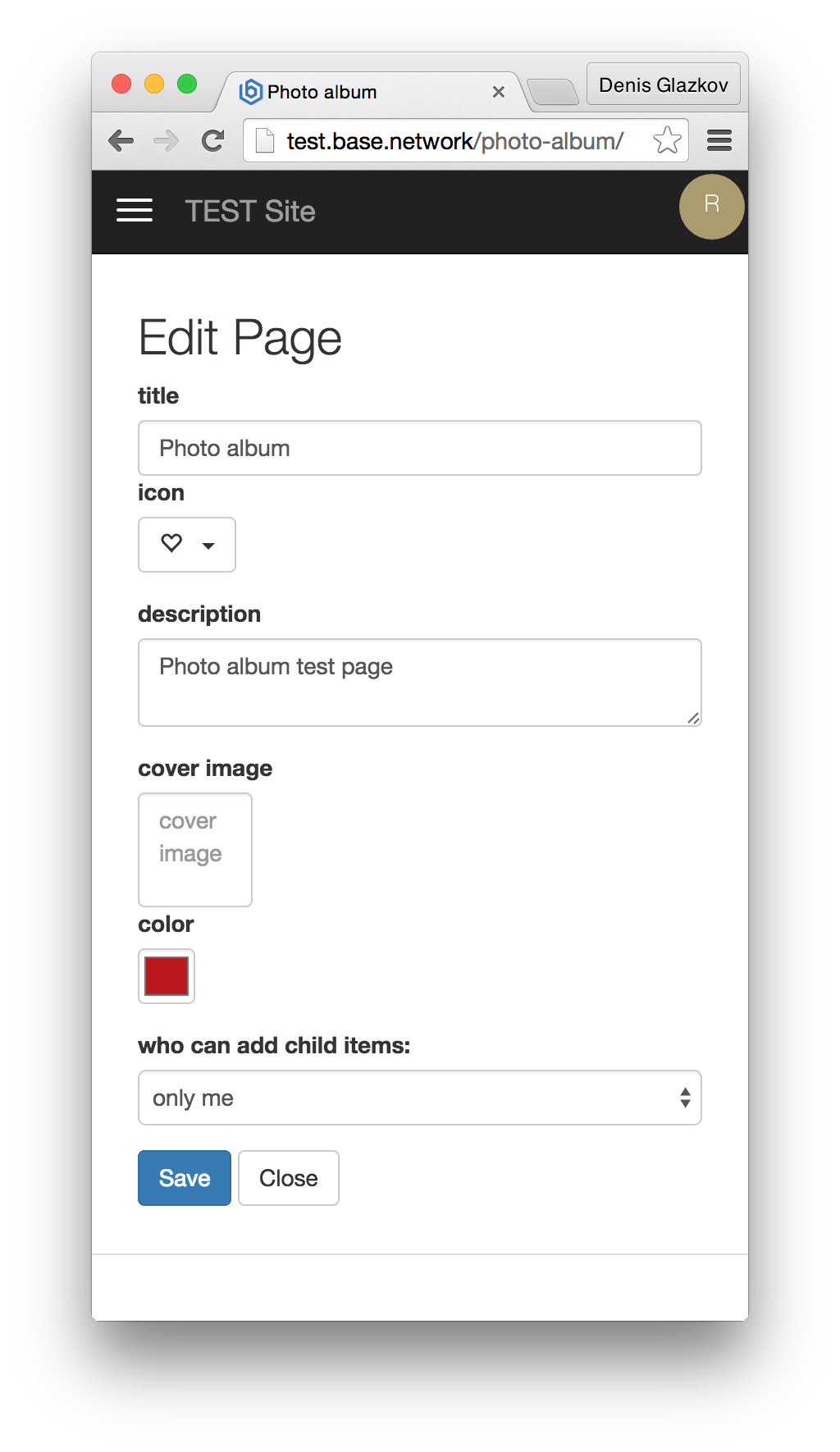
.
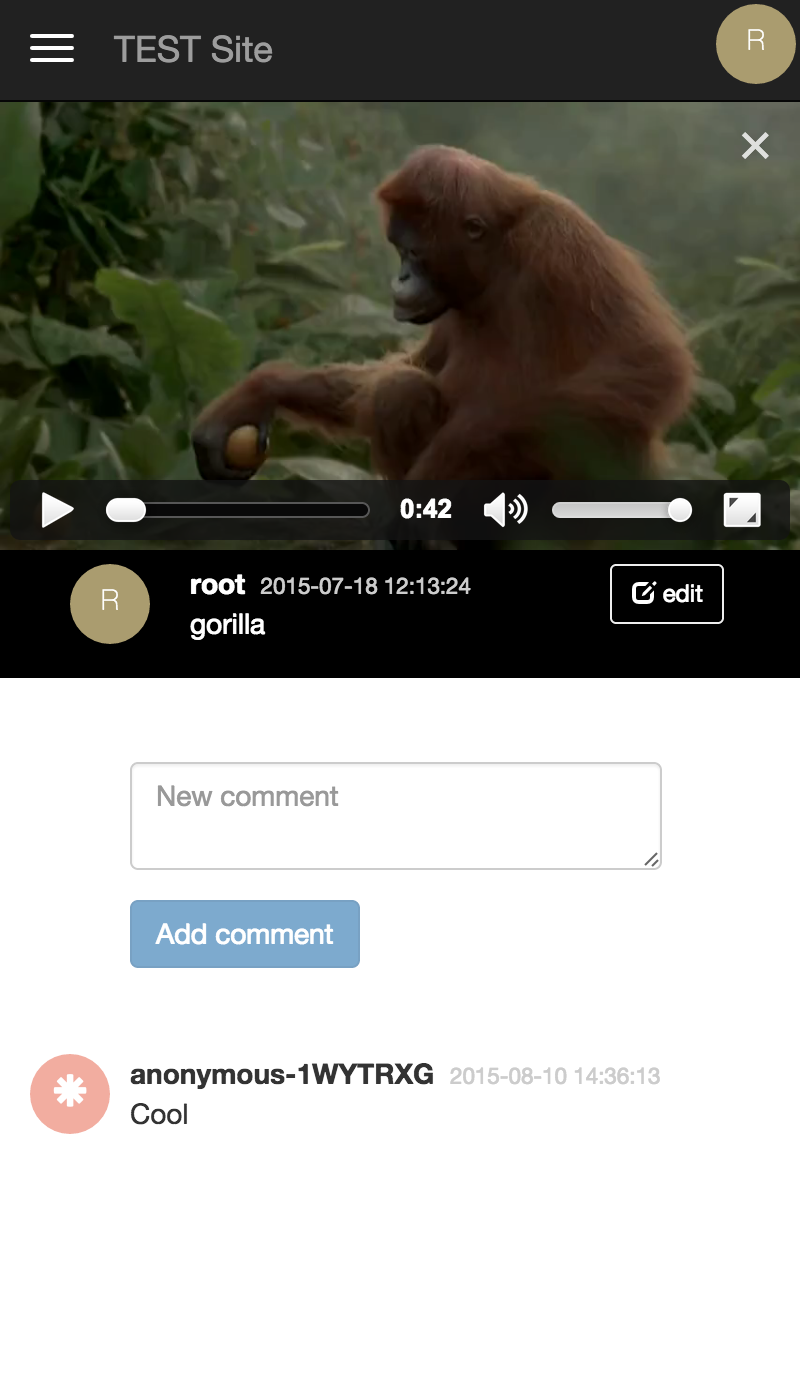
, , , , , . .
, — , , . Wellcome! .
. .
- , Node.js
- github
git clone https://github.com/basenetwork/base.server-node - sqlite3 Node.js
cd base.server-node && npm install sqlite3 --build-from-source && cd .. nohup base.server-node/base.node.js --size=32 >/var/log/base.node.log &
As the size parameter, you must specify the free space on the disk (in GB), which you are ready to allocate under the node.
For the node to work, you must allocate an external IP address and a free port. By default, the system will automatically attempt to use one of the external IP addresses in the list of network interfaces of the operating system. It is possible to manually specify the IP address and port using the startup parameters --host and --port:
nohup base.server-node/base.node.js --size=32 --host=41.34.55.66 --port=2222 >/var/log/base.node.log & You can check the node performance by making an http request to the web server:
curl http://41.34.55.66:2222/-/about Source
All project sources can be viewed on GitHub - github.com/basenetwork . Account contains several repositories:
- base.server-node
Actually, the server node itself. The repository is written on Node.js. Instructions for installing a base node on your server have been presented above. - client-js
. JavaScript. . , — http://base.network/core.js API — baseAPI - site-engine-js
. JavaScript React.js. Bootstrap v3. , , . . , , . , API. - static-builder
. Node.js. javascript-. . : , , , , , . , .
css- base64 . css-, js jsx js-.
, . . ( ). , .
- . . , .
- - .
- . , . . .
- GO, Node.js .
- .
- , API -.
- Store , , -.
Project support
, . , . , .
, , , . github . .
-, Node.js, .
-, HTML-, , JavaScript, . .
, : ! .
Thanks for the support!
Conclusion
. — . , , — , . , . . , , , . , : ? - ? ?
, — base.network — , — .
Source: https://habr.com/ru/post/266315/
All Articles