Dangerous world of malicious extensions and protection from them. Experience Yandex Browser
Browser extensions lately, unfortunately, are increasingly being used not as a tool to benefit, but as a tool for scammers. Today we want to share with you our experience in dealing with malware, to talk about measures and technologies that protect users of Yandex. Browser.
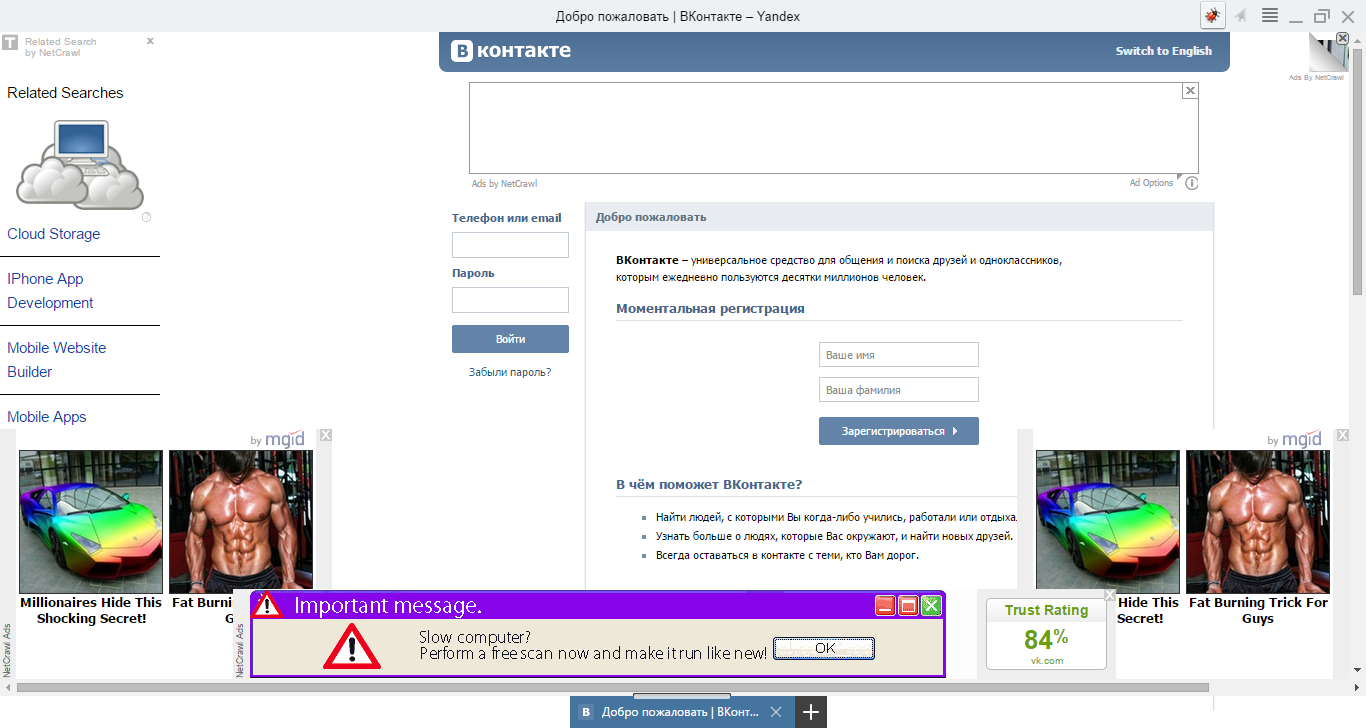
In the spring of 2014, the support of Yandex. Browser drew attention to the rapidly growing number of hits from users, which referred to "virus infection of the browser" and aggressive advertising that pops up on the websites visited. The most common symptom was the substitution or addition of new ad units on sites popular in RuNet (VKontakte, Yandex, ...). At the same time, the developers of malicious extensions did not bother to care about users and did not disdain frankly fraudulent or shock advertising. There were other manifestations. For example, the automatic opening of a tab with a specific site, the substitution of the default search or even data theft.
')
At a certain point, the number of such requests reached 30% of all messages in support. Observations of support were also confirmed by statistics on the main reasons for deleting our browser (users are asked to describe the reason when deleting). Many people sincerely believed that it was our team who decided to monetize the browser in such a way. In a short period of time, the number of Yandex. Browser deletions related to the activities of third-party malicious software has doubled. It was necessary to urgently intervene and start working on this problem.
First hit
The simplest and fastest thing we could do in this situation is to introduce a blacklist of extensions. Here we were helped by colleagues responsible for security in Yandex.Search and having solid experience in the fight against malicious sites. It is their data that underlies the Safe Browsing technology used in Yandex Browser. As a result of the joint work, Yandex. Browser 14.5 learned how to block the work of extensions whose ID is included in the list of malicious add-ons. The list itself was regularly replenished, after which the new version was distributed to users through the Safe Browsing API in a matter of hours.

This was our first serious blow to fraudulent extensions that had not previously encountered any particular resistance from the browser. This step led to the fact that within a few weeks the number of complaints decreased 10 times. Unfortunately, the effect did not last long. The joy of a quick victory was replaced by the understanding that this is only the beginning of a real struggle for the safety of users.
Security or freedom?
Last spring, we learned how to quickly identify and block widespread malicious extensions through the blacklist. Here are just the creators of such developments are not lost, and moved to a new tactic. We learned about it from all the same complaints. Users periodically send us bad extensions for analysis. Thanks to such help we add to our black list. But at some point we began to receive very strange samples. For example, they sent us an extension called NxAxR, whose ID was equal to "pioclpoplcdbaefihamjohnefbikjilc". If you now look for this ID in the search, you will find out that it belongs to the completely secure extension of Evernote Web Clipper, which is published in the Chrome Web Store and certainly could not create any nasty things (but, by the way, we still checked). And over time, the audience of such fakes has become even more than the original extensions. But we could not ban the same NxAxR by ID, because after such a step Evernote would be banned too.

Almost immediately, the idea of hacking into accounts of the Chrome Web Store was dropped, which theoretically could explain the update of the storage extension for notes to a malicious adware. Nobody hacked into the account, and the correct extension version was still distributed in the directory. Fortunately, it was not long to think, because our developers themselves guessed about the mechanism used by fraudsters.
The malicious program running on the user's computer installed its extension into the browser not through standard tools for this, but by direct editing the profile. At the same time, the fake was disguised at the ID level under the well-known extension that was published in the Web Store. Even “update_url” (server address where the browser should check for new versions) was specified correctly. And so that the malicious functions of the extension did not disappear after the first update of the original, the attackers deliberately exhibited a large version. The browser compared versions in the manifest of the extension and on the server. If the computer is newer, the update did not occur.

By the way, over time, the creators of dangerous extensions realized that the names of the form “NxAxR” attracted unnecessary attention of the user, so they began to be called, for example, “Translator for Chrome”. This is terrible to remove: suddenly the translator really stops working.
Our team had a big and interesting task. It was necessary to develop a technology that could detect fakes and protect people from them. I would like to tell you in this place about the fantastic ideas that we went over, but everything was much simpler (and faster, which is especially important). To recognize a fake, we needed to compare it with a standard, i.e. with a knowingly original copy that the user installs from the official catalog. The problem was that many extensions were distributed in alternative ways and were not related to the directory in any way. In this case, there is simply no reference. And malware especially abused similar. In this situation, we could only provide protection against falsifications by restricting the installation of extensions to trusted sources.
As you may have guessed (or even remember the August of last year), we have introduced restrictions on installing extensions from third-party sources. Nevertheless, our team sought not only to protect users from malicious extensions, but also to preserve the right to choose. Users should be able to select both extensions and the directory from which they can be installed. That is why at one time we added the Add-on section to the browser. And it is for this very reason that we not only introduced restrictions, but also supported the Opera Addons catalog, which can be installed as easily as from the Chrome Web Store. In addition, those developments that were installed from third-party sources were not completely blocked. We just turned them off by default. After restarting the browser, people have retained the ability to activate them manually and continue working.

No matter how hard it was to combine security and freedom of choice, it seems that we managed to find a balance between them.
Authentication
After the introduction of the ban on installation from third-party sources, the browser was able to detect fakes, comparing them with the standards. But how exactly should you compare? If you compare only the contents of the manifest, then this is not enough, because fraudsters can be embedded in existing js-files. Compare the contents of all js and html files? This is a long time and can affect performance. Many of you could already guess that ultimately the choice fell on hashes comparison. If the extension was installed from Opera Addons, Web Store or Add-ons, then Yandex.Browser has a hash of a safe copy. It is enough to compare it with the hash of the current extension to quickly identify those that have been changed.

It sounds simple, but it took a lot of time to debug this technology. We had to look for a middle ground between the effectiveness of protection, the number of false positives and the impact on performance. We apologize for not disclosing all the details here. We hope that you understand the reason. Many users paid for the security inconvenience associated with installing extensions, but ultimately this measure allowed us to repeat the success of the blacklist and significantly reduce the number of "infected" browsers.
Group politicians and other loopholes
Safe Browsing blacklists, limiting sources, and authentication significantly complicated the work of fraudsters. They retreated, recounted their losses, but, like last time, they found an alternative option. And this time the main blow took over the Chrome Web Store.
The Web Store catalog is open for free adding extensions and does not require pre-moderation. The attackers took advantage of this. In the catalog we have previously found some, say, not very useful samples. But in 2015, such activity clearly increased. The fraudsters tried to circumvent the protective measures with a simple amount: one popular extension would quickly fall into the blacklist, but if you download multiple copies, some may well have a chance to survive and recoup the investment.
Despite the fact that such extensions had names and functions that were clearly targeted at attracting users (“Download music / video from VKontakte” and the like), the main channel for distribution was still software on the user's computer. The browser while no one "hacked." It was enough to use the method documented in the Chromium project. The installer created in the registry a key of the form HKEY_LOCAL_MACHINE \ Software \ Yandex \ Extensions \ extension_ID, in which the address of the Web Store directory was registered. After restarting, the browser itself downloaded the CRX file from the specified address and installed it. A similar method was invented at the time for native programs that carried their own extension (for example, Skype or Kaspersky Anti-Virus). But due to the relative ease of use, this tool was quickly mastered by the developers of malicious add-ons.
In the Chromium project, it is also possible to install both the browser itself and extensions for it by means of group policies . They were created initially for the corporate segment. But as in the case of the first method, the main application was found in a completely different area. Extensions are installed without any notice. But the most unpleasant thing here is that in group policies you can prescribe a ban on disabling or deleting such extensions. And without the ability to work with the system registry, the user cannot get rid of them.

Methods for installing extensions through the registry or group policies, despite their initial purpose, were mainly used by fraudsters. The problems of many thousands of our users mean more than convenience for several third-party programs. Therefore, in the spring of this year we turned off these loopholes.
What's next?
We would not like to spoil and deprive the pleasure of those who are on the other side of the barricades, so we will not talk about our plans and upcoming technologies. With all the others, we can share some of our own observations.
First, the proliferation of advertisements and other dangerous extensions is a whole industry that has the money, the time, and the best minds to find all the new ways to bypass protection. In order to successfully counter this threat, we have identified a whole line of responsibility for the safety of users in the team.
Secondly, the measures taken in the Yandex Browser, as well as in other browsers and directories, gradually create unfavorable conditions for fraudsters. They have to look for alternative channels to replace advertising or stealing data on the user's computer. And here it is important not to lose sight of them. In future posts we will try to tell about it in more detail.

In the spring of 2014, the support of Yandex. Browser drew attention to the rapidly growing number of hits from users, which referred to "virus infection of the browser" and aggressive advertising that pops up on the websites visited. The most common symptom was the substitution or addition of new ad units on sites popular in RuNet (VKontakte, Yandex, ...). At the same time, the developers of malicious extensions did not bother to care about users and did not disdain frankly fraudulent or shock advertising. There were other manifestations. For example, the automatic opening of a tab with a specific site, the substitution of the default search or even data theft.
')
At a certain point, the number of such requests reached 30% of all messages in support. Observations of support were also confirmed by statistics on the main reasons for deleting our browser (users are asked to describe the reason when deleting). Many people sincerely believed that it was our team who decided to monetize the browser in such a way. In a short period of time, the number of Yandex. Browser deletions related to the activities of third-party malicious software has doubled. It was necessary to urgently intervene and start working on this problem.
First hit
The simplest and fastest thing we could do in this situation is to introduce a blacklist of extensions. Here we were helped by colleagues responsible for security in Yandex.Search and having solid experience in the fight against malicious sites. It is their data that underlies the Safe Browsing technology used in Yandex Browser. As a result of the joint work, Yandex. Browser 14.5 learned how to block the work of extensions whose ID is included in the list of malicious add-ons. The list itself was regularly replenished, after which the new version was distributed to users through the Safe Browsing API in a matter of hours.

This was our first serious blow to fraudulent extensions that had not previously encountered any particular resistance from the browser. This step led to the fact that within a few weeks the number of complaints decreased 10 times. Unfortunately, the effect did not last long. The joy of a quick victory was replaced by the understanding that this is only the beginning of a real struggle for the safety of users.
Security or freedom?
Last spring, we learned how to quickly identify and block widespread malicious extensions through the blacklist. Here are just the creators of such developments are not lost, and moved to a new tactic. We learned about it from all the same complaints. Users periodically send us bad extensions for analysis. Thanks to such help we add to our black list. But at some point we began to receive very strange samples. For example, they sent us an extension called NxAxR, whose ID was equal to "pioclpoplcdbaefihamjohnefbikjilc". If you now look for this ID in the search, you will find out that it belongs to the completely secure extension of Evernote Web Clipper, which is published in the Chrome Web Store and certainly could not create any nasty things (but, by the way, we still checked). And over time, the audience of such fakes has become even more than the original extensions. But we could not ban the same NxAxR by ID, because after such a step Evernote would be banned too.

Almost immediately, the idea of hacking into accounts of the Chrome Web Store was dropped, which theoretically could explain the update of the storage extension for notes to a malicious adware. Nobody hacked into the account, and the correct extension version was still distributed in the directory. Fortunately, it was not long to think, because our developers themselves guessed about the mechanism used by fraudsters.
The malicious program running on the user's computer installed its extension into the browser not through standard tools for this, but by direct editing the profile. At the same time, the fake was disguised at the ID level under the well-known extension that was published in the Web Store. Even “update_url” (server address where the browser should check for new versions) was specified correctly. And so that the malicious functions of the extension did not disappear after the first update of the original, the attackers deliberately exhibited a large version. The browser compared versions in the manifest of the extension and on the server. If the computer is newer, the update did not occur.

By the way, over time, the creators of dangerous extensions realized that the names of the form “NxAxR” attracted unnecessary attention of the user, so they began to be called, for example, “Translator for Chrome”. This is terrible to remove: suddenly the translator really stops working.
Our team had a big and interesting task. It was necessary to develop a technology that could detect fakes and protect people from them. I would like to tell you in this place about the fantastic ideas that we went over, but everything was much simpler (and faster, which is especially important). To recognize a fake, we needed to compare it with a standard, i.e. with a knowingly original copy that the user installs from the official catalog. The problem was that many extensions were distributed in alternative ways and were not related to the directory in any way. In this case, there is simply no reference. And malware especially abused similar. In this situation, we could only provide protection against falsifications by restricting the installation of extensions to trusted sources.
As you may have guessed (or even remember the August of last year), we have introduced restrictions on installing extensions from third-party sources. Nevertheless, our team sought not only to protect users from malicious extensions, but also to preserve the right to choose. Users should be able to select both extensions and the directory from which they can be installed. That is why at one time we added the Add-on section to the browser. And it is for this very reason that we not only introduced restrictions, but also supported the Opera Addons catalog, which can be installed as easily as from the Chrome Web Store. In addition, those developments that were installed from third-party sources were not completely blocked. We just turned them off by default. After restarting the browser, people have retained the ability to activate them manually and continue working.

No matter how hard it was to combine security and freedom of choice, it seems that we managed to find a balance between them.
Authentication
After the introduction of the ban on installation from third-party sources, the browser was able to detect fakes, comparing them with the standards. But how exactly should you compare? If you compare only the contents of the manifest, then this is not enough, because fraudsters can be embedded in existing js-files. Compare the contents of all js and html files? This is a long time and can affect performance. Many of you could already guess that ultimately the choice fell on hashes comparison. If the extension was installed from Opera Addons, Web Store or Add-ons, then Yandex.Browser has a hash of a safe copy. It is enough to compare it with the hash of the current extension to quickly identify those that have been changed.

It sounds simple, but it took a lot of time to debug this technology. We had to look for a middle ground between the effectiveness of protection, the number of false positives and the impact on performance. We apologize for not disclosing all the details here. We hope that you understand the reason. Many users paid for the security inconvenience associated with installing extensions, but ultimately this measure allowed us to repeat the success of the blacklist and significantly reduce the number of "infected" browsers.
Group politicians and other loopholes
Safe Browsing blacklists, limiting sources, and authentication significantly complicated the work of fraudsters. They retreated, recounted their losses, but, like last time, they found an alternative option. And this time the main blow took over the Chrome Web Store.
The Web Store catalog is open for free adding extensions and does not require pre-moderation. The attackers took advantage of this. In the catalog we have previously found some, say, not very useful samples. But in 2015, such activity clearly increased. The fraudsters tried to circumvent the protective measures with a simple amount: one popular extension would quickly fall into the blacklist, but if you download multiple copies, some may well have a chance to survive and recoup the investment.
Despite the fact that such extensions had names and functions that were clearly targeted at attracting users (“Download music / video from VKontakte” and the like), the main channel for distribution was still software on the user's computer. The browser while no one "hacked." It was enough to use the method documented in the Chromium project. The installer created in the registry a key of the form HKEY_LOCAL_MACHINE \ Software \ Yandex \ Extensions \ extension_ID, in which the address of the Web Store directory was registered. After restarting, the browser itself downloaded the CRX file from the specified address and installed it. A similar method was invented at the time for native programs that carried their own extension (for example, Skype or Kaspersky Anti-Virus). But due to the relative ease of use, this tool was quickly mastered by the developers of malicious add-ons.
In the Chromium project, it is also possible to install both the browser itself and extensions for it by means of group policies . They were created initially for the corporate segment. But as in the case of the first method, the main application was found in a completely different area. Extensions are installed without any notice. But the most unpleasant thing here is that in group policies you can prescribe a ban on disabling or deleting such extensions. And without the ability to work with the system registry, the user cannot get rid of them.

Methods for installing extensions through the registry or group policies, despite their initial purpose, were mainly used by fraudsters. The problems of many thousands of our users mean more than convenience for several third-party programs. Therefore, in the spring of this year we turned off these loopholes.
What's next?
We would not like to spoil and deprive the pleasure of those who are on the other side of the barricades, so we will not talk about our plans and upcoming technologies. With all the others, we can share some of our own observations.
First, the proliferation of advertisements and other dangerous extensions is a whole industry that has the money, the time, and the best minds to find all the new ways to bypass protection. In order to successfully counter this threat, we have identified a whole line of responsibility for the safety of users in the team.
Secondly, the measures taken in the Yandex Browser, as well as in other browsers and directories, gradually create unfavorable conditions for fraudsters. They have to look for alternative channels to replace advertising or stealing data on the user's computer. And here it is important not to lose sight of them. In future posts we will try to tell about it in more detail.
Source: https://habr.com/ru/post/266061/
All Articles