Minimalism in cryptography, or the Even – Mansour scheme
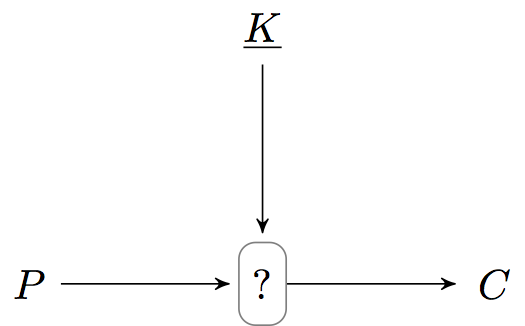
Back in 1997, Israeli scientists Shimon Even and Ishay Mansour (Yishay Mansour) asked themselves the question: how minimal can a strong block cipher have ? By minimality they meant the number of structural elements in the cipher scheme, and by persistence - any (formally correct) lower estimate of the complexity of the attacks on this cipher. As they say, under the cut - a description of the minimum (to this day) block cipher with provable strength.
Lyrical digression
And all because we still do not know how to get lower ratings. Friends, in mathematics (and especially in cryptography) there are not so many beautiful ideas and elegant solutions, and there are even less proven estimates from below. The cipher considered here, in my opinion, falls into the intersection: it is as simple as possible, and at the same time formally resistant.
')
I warn you at once that this publication is not a work of art for unprepared readers, although it does not contain anything more complicated than the Bayes conditional probability formula and elementary arithmetic of fractions. The inexperienced reader will remain satisfied with the description of the design of the cipher , and a strict proof of its endurance is given here for professionals and true connoisseurs of mathematics.
Israeli scientists Shiman Even (Shimon Even) and Ishei Mansour (Yishay Mansour) in [EM97] proposed a way to build a block cipher with demonstrable persistence, based on the only randomly selected permutation from
Before I introduce you directly to this block cipher, let me indicate a list of the introduced symbols and basic definitions. However, you can always return to it, therefore, in the event that I managed to awaken in you a serious interest to see everything “here and now”, go directly to the description of the cipher.
Definitions and conventions
Cryptosystem is called an ordered set of five
is called an ordered set of five  where
where


Sets, sets
- unordered set of elements
- ordered set of elements
Inscriptions
- spaces used by cryptosystems
- algorithms, computing models
- oracles
- sets developed by algorithms
- substitutions
- tasks
Legend
- a lot of open texts (messages)
- open texts
- many ciphertexts (cryptograms)
- ciphertexts
- many keys
- keys
- true key
- encryption function
- decryption function
- oracles that implement substitutions
- oracles realizing functions
on the key
- probability of success of the algorithm
- algorithm execution time
Definitions
Cryptosystem
- a lot of open texts ( plaintexts ),
- many ciphertexts ( ciphertexts ),
- set of keys ( keys ),
- (injective) encryption function ( encipher ):
- decipher function:
Classical Even – Mansour scheme
Israeli scientists Shimon Even and Yishay Mansour in their work proposed a block cipher with provable cryptographic strength, for which only one substitution is required
It is assumed that the selected substitution is not part of the key, and is available to any attacker in the form of a “black box”.
It is argued that, from the point of view of the attacker, the proposed cipher is almost indistinguishable from the ideal random cipher, and the probability of a successful opening of the system
It is also argued that the use of a pseudo-random substitution instead of a truly random substitution does not change the shown cipher strength.
Description
Let be
It is assumed that for any elements
Open spaces and ciphertexts are binary spaces.
The secret key
It is also assumed that the selected secret key

Plain text encryption
and decryption ciphertext
Really simple? They took the message, poked it with the first half of the key, replaced the plate that was open and accessible to everyone, poked it with the second half of the key, and the cryptogram was obtained. Great, right? Why does nobody use this scheme in practice? After all, it is much easier AES, and DES. The easiest block cipher. Where is the catch?
Trick
The thing is, the substitution is set to binary  –Bit vectors, and storing the replacement table for a randomly selected substitution is completely unacceptable;
–Bit vectors, and storing the replacement table for a randomly selected substitution is completely unacceptable; ) of memory. The only possible solution to this problem is to build good pseudo-random substitutions (polynomially indistinguishable from random ones), whose values could be relatively easily calculated at any point; and this we do not know how.
of memory. The only possible solution to this problem is to build good pseudo-random substitutions (polynomially indistinguishable from random ones), whose values could be relatively easily calculated at any point; and this we do not know how.
About minimal scheme
It should be noted that the classical scheme is minimal in the sense that the removal of any of the elements of this scheme leads to a significant weakening of its durability. It is easy to show that removing any of the additions with subkeys, or substitutions
- There is no addition with the first subkey.
The encryption function is:
The attacker can easily calculate the secret keyknowing the substitution
:
- There is no addition with the second subkey.
The encryption function is:
The attacker can easily calculate the secret keyknowing the substitution
:
- Missing
–Block (substitution
)
The encryption function is:
The attacker can easily calculate the secret key:
About circuit durability
Assumptions of persistence, determination
The persistence of the proposed scheme is due to the following assumptions:
- the attacker does not know the true key
;
- the attacker has the ability to encrypt plaintext (messages) and decrypt ciphertexts (cryptograms) on the secret key
;
- the attacker has the ability to calculate the permutation values
and reverse permutations to it
.
Any algorithm that uncovers a system can refer to the following four oracles.
- oracle
calculates the permutation value
on
–Dimensional binary input set
:
- oracle
calculates the permutation value
on
–Dimensional binary input set
:
- oracle
encrypts
–Dimensional binary set (clear text)
on
–Dimensional key
:
- oracle
decodes
–Dimensional binary set (ciphertext)
on
–Dimensional key
:
Further, if the substitution, the value of which calculates the oracle
Addressing the oracles
Thus, the communication of any algorithm with oracles
Let's call such pairs
Addressing the oracles
So, communication of any algorithm with oracles
Let's call such pairs
Definition
A similar definition can be formulated for
Definition
Statement 1 (Overlapping pairs are identical)
Due to the fact that all oracles
- intersecting
–Pairs are the same;
- intersecting
–Pairs are the same.
Modulo statement 1, we can assume that all pairs of sets
Probability of success
Under runtime
Definition
Function
Definition
Task
Description of the formal model
In the model proposed in [EM97], the attacker fully has knowledge of the cipher device and the selected substitution
Decryption Task (  )
)
Under the task of decryption (
- (limited to
oracle
decrypts everyone
–Dimensional binary set (ciphertext)
, Besides
on the key
:
Algorithm
The task of building a new pair of plaintext / ciphertext (  )
)
Under the task of building a new pair of texts (
The success of the algorithm
Reduction of the task of constructing a text / ciphertext pair to the task of opening (  )
)
Theorem 1 (EFP to CP reduction)
Let be
Evidence
Fix the plaintext  key
key  and ciphertext
and ciphertext ) , and consider the progress of the algorithm
, and consider the progress of the algorithm ![\ operatorname {A} \ left [C_0 \ right]}](http://tex.s2cms.ru/svg/%5Coperatorname%7BA%7D%5Cleft%5BC_0%5Cright%5D%7D) .
.
Without loss of generality, we can assume that if the algorithm successfully decrypts
successfully decrypts  then at some critical point in time
then at some critical point in time ) the execution of this algorithm, the attacker checks the plaintext found, candidate
the execution of this algorithm, the attacker checks the plaintext found, candidate  by sending (for the first time) a request to encrypt it to an oracle
by sending (for the first time) a request to encrypt it to an oracle  and comparing the decrypted ciphertext
and comparing the decrypted ciphertext  with oracle answer:
with oracle answer:
![\ operatorname {E_K} \ left [P_0 \ right]} \ stackrel {?} {=} C_0.](http://tex.s2cms.ru/svg/%0A%5Coperatorname%7BE_K%7D%5Cleft%5BP_0%5Cright%5D%7D%20%5Cstackrel%7B%3F%7D%7B%3D%7D%20C_0.%0A)
Based on the algorithm let's build an algorithm
let's build an algorithm  solving the problem
solving the problem  :
:
It is easy to see that the algorithm carries no more
carries no more ) requests to oracles
requests to oracles  while the desired pair
while the desired pair  will be built only if the decryption algorithm
will be built only if the decryption algorithm  successfully decrypts text
successfully decrypts text  (with probability
(with probability ) ) and
) and  will be stopped at a critical time
will be stopped at a critical time  (with probability
(with probability ) ):
):
%7D%20%3D%20%5Cfrac%7B%5Cxi(n)%7D%7BT(n)%7D%2C%0A)
Q.E.D.
Without loss of generality, we can assume that if the algorithm
Based on the algorithm
- Fix ciphertext
;
- Let's start the execution of the algorithm
;
- Choose random
evenly distributed on the segment
;
- Stop the execution of the algorithm
after
requests to oracles;
- If in request
algorithm
requests encryption
, the execution of the algorithm is terminated, and the initial pair is
.
It is easy to see that the algorithm
Q.E.D.
Corollary 1.1
Let the task
It should be noted that the converse statement (reducibility
Durability of the system when using random substitution 
The main ideas of proof of persistence are as follows:
- show that at any stage of a polynomially limited attack, the set of “good” keys (keys whose truth the attacker neither confirm nor deny on the basis of his data) is exponentially large ( Lemma 1 );
- show that the attacker can “guess” the true key
only with a polynomially small probability ( Theorem 2 );
- show that the attacker collect enough data to identify the true key
for the polynomial number of requests to oracles ( Theorem 2 ).
Definition
The first subkey of a
In other words, a subkey
Obviously, such a key
With the help of other collected
A similar definition can be formulated for the second subkeys.
The definition of the
second
Definition
Key
Statement 2 (True subkeys share goodness)
With a private key
Lemma 1 (The fraction of bad keys)
Let the algorithm
Evidence
,  ,
,  –
–  and
and  –
– %5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BP%7D) , ,
, ,

, , ,
, ,  and
and  ,
, 
 .
.
,
 .
.
 , :
, :

 :
:

.
,
,
.
Definition
Let be
We say that the pair
- The substitution is
indistinguishable from the true substitution
on the resulting set –
pairs:
- The substitution is
indistinguishable from the true substitution
on the resulting set –
pairs:
The following lemma shows that all good keys are, in a sense, equal candidates for the role of a true encryption key.
Lemma 2 (Distribution of true key candidates)
Let be
Evidence
, :
![\forall K_{i} \in \mathcal{K} \>\Longrightarrow\> \Pr{\left[K_{i} = \underline{K}\right]} = \frac{1}{2^{2n}},](http://tex.s2cms.ru/svg/%0A%5Cforall%20K_%7Bi%7D%20%5Cin%20%5Cmathcal%7BK%7D%20%5C%3E%5CLongrightarrow%5C%3E%20%5CPr%7B%5Cleft%5BK_%7Bi%7D%20%3D%20%5Cunderline%7BK%7D%5Cright%5D%7D%20%3D%20%5Cfrac%7B1%7D%7B2%5E%7B2n%7D%7D%2C%0A)
 :
:
![\forall \sigma_{i} \in S_{\left\vert\,\mathcal{P}\,\right\vert} \>\Longrightarrow\> \Pr{\left[\sigma_{i} = \pi\right]} = \frac{1}{2^n !},](http://tex.s2cms.ru/svg/%0A%5Cforall%20%5Csigma_%7Bi%7D%20%5Cin%20S_%7B%5Cleft%5Cvert%5C%2C%5Cmathcal%7BP%7D%5C%2C%5Cright%5Cvert%7D%20%5C%3E%5CLongrightarrow%5C%3E%20%5CPr%7B%5Cleft%5B%5Csigma_%7Bi%7D%20%3D%20%5Cpi%5Cright%5D%7D%20%3D%20%5Cfrac%7B1%7D%7B2%5En%20!%7D%2C%0A)
,
![\alpha = \Pr{\left[K_{i} = \underline{K} \mid \left\langle \pi, K_{i} \right\rangle \text{ satisfies } \mathsf{E}, \mathsf{P}\right]}.](http://tex.s2cms.ru/svg/%0A%5Calpha%20%3D%20%5CPr%7B%5Cleft%5BK_%7Bi%7D%20%3D%20%5Cunderline%7BK%7D%20%5Cmid%20%5Cleft%5Clangle%20%5Cpi%2C%20K_%7Bi%7D%20%5Cright%5Crangle%20%5Ctext%7B%20satisfies%20%7D%20%5Cmathsf%7BE%7D%2C%20%5Cmathsf%7BP%7D%5Cright%5D%7D.%0A)
:
![\Pr{\left[K_{i} = \underline{K} \mid \left\langle \pi, K_{i \right\rangle} \text{ satisfies } \mathsf{E}, \mathsf{P}\right]} =
\frac
{
\overbrace{
\Pr{\left[K_{i} = \underline{K}\right]}
}^{\operatorname{const}} \cdot \overbrace{
\Pr{\left[\left\langle \pi, K_{i \right\rangle} \text{ satisfies } \mathsf{E}, \mathsf{P} \mid K_{i} = \underline{K}\right]}
}^{\beta}
}
{
\underbrace{
\Pr{\left[\left\langle \pi, K_{i} \right\rangle \text{ satisfies } \mathsf{E}, \mathsf{P} \right]}
}_{\operatorname{const}}
}.](http://tex.s2cms.ru/svg/%0A%5CPr%7B%5Cleft%5BK_%7Bi%7D%20%3D%20%5Cunderline%7BK%7D%20%5Cmid%20%5Cleft%5Clangle%20%5Cpi%2C%20K_%7Bi%20%5Cright%5Crangle%7D%20%5Ctext%7B%20satisfies%20%7D%20%5Cmathsf%7BE%7D%2C%20%5Cmathsf%7BP%7D%5Cright%5D%7D%20%3D%20%0A%5Cfrac%0A%7B%0A%5Coverbrace%7B%0A%5CPr%7B%5Cleft%5BK_%7Bi%7D%20%3D%20%5Cunderline%7BK%7D%5Cright%5D%7D%0A%7D%5E%7B%5Coperatorname%7Bconst%7D%7D%20%5Ccdot%20%5Coverbrace%7B%0A%5CPr%7B%5Cleft%5B%5Cleft%5Clangle%20%5Cpi%2C%20K_%7Bi%20%5Cright%5Crangle%7D%20%5Ctext%7B%20satisfies%20%7D%20%5Cmathsf%7BE%7D%2C%20%5Cmathsf%7BP%7D%20%5Cmid%20K_%7Bi%7D%20%3D%20%5Cunderline%7BK%7D%5Cright%5D%7D%0A%7D%5E%7B%5Cbeta%7D%0A%7D%0A%7B%0A%5Cunderbrace%7B%0A%5CPr%7B%5Cleft%5B%5Cleft%5Clangle%20%5Cpi%2C%20K_%7Bi%7D%20%5Cright%5Crangle%20%5Ctext%7B%20satisfies%20%7D%20%5Cmathsf%7BE%7D%2C%20%5Cmathsf%7BP%7D%20%5Cright%5D%7D%0A%7D_%7B%5Coperatorname%7Bconst%7D%7D%0A%7D.%0A)
, .
.
,
 –
– 
 –
–  ,
,  , :
, :

, , ,
, 
 –
–  ,
,  –
–  . ,
. ,  ,
,  .
.
, :
:
![\beta \equiv \Pr{ \left[
\left\langle \pi, K_{i} \right\rangle \text{ satisfies } \mathsf{E}, \mathsf{P} \mid K_{i} = \underline{K} \right]
} =
\Pr{ \left[
\left\langle \pi, K_{i} \right\rangle \text{ satisfies } \emptyset, \mathsf{P} \cup \mathsf{P}' \mid K_{i} = \underline{K} \right]
}](http://tex.s2cms.ru/svg/%0A%5Cbeta%20%5Cequiv%20%5CPr%7B%20%5Cleft%5B%0A%5Cleft%5Clangle%20%5Cpi%2C%20K_%7Bi%7D%20%5Cright%5Crangle%20%5Ctext%7B%20satisfies%20%7D%20%5Cmathsf%7BE%7D%2C%20%5Cmathsf%7BP%7D%20%5Cmid%20K_%7Bi%7D%20%3D%20%5Cunderline%7BK%7D%20%5Cright%5D%0A%7D%20%3D%0A%5CPr%7B%20%5Cleft%5B%0A%5Cleft%5Clangle%20%5Cpi%2C%20K_%7Bi%7D%20%5Cright%5Crangle%20%5Ctext%7B%20satisfies%20%7D%20%5Cemptyset%2C%20%5Cmathsf%7BP%7D%20%5Ccup%20%5Cmathsf%7BP%7D'%20%5Cmid%20K_%7Bi%7D%20%3D%20%5Cunderline%7BK%7D%20%5Cright%5D%0A%7D%0A)
 ,
,  –
–  and
and  :
:

 , ( )
, ( ) 
 .
. 
![\beta = \Pr{\left[
\pi(M) =
M' \mid \left\langle M, M' \right\rangle \in \mathsf{P} \cup \mathsf{P}'
\right]} =
\frac{\left( 2^n - (l + m) \right) !}{2^n !} =
\prod_{j = 0}^{l + m - 1} \frac{1}{2^n - i}.](http://tex.s2cms.ru/svg/%0A%5Cbeta%20%3D%20%5CPr%7B%5Cleft%5B%0A%5Cpi(M)%20%3D%0AM'%20%5Cmid%20%5Cleft%5Clangle%20M%2C%20M'%20%5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BP%7D%20%5Ccup%20%5Cmathsf%7BP%7D'%0A%5Cright%5D%7D%20%3D%0A%5Cfrac%7B%5Cleft(%202%5En%20-%20(l%20%2B%20m)%20%5Cright)%20!%7D%7B2%5En%20!%7D%20%3D%0A%5Cprod_%7Bj%20%3D%200%7D%5E%7Bl%20%2B%20m%20-%201%7D%20%5Cfrac%7B1%7D%7B2%5En%20-%20i%7D.%0A)
, , .
, .
,
:
,
,
, ,
,
,
Theorem 2 (Boundary Probability for by success of the any
Where
Evidence
,  ,
, 
 and
and 
 –
–  – . :
– . :  ,
, 
 «»
«»  ,
, %7D) .
.
%7D) and
and %7D) sets
sets  –
–  –,
–, 
 :
:
%7D%20%5Csubseteq%20%5Cmathsf%7BE%7D%2C%5C%20%5Cbig%5Clvert%20%5Cmathsf%7BE%7D%5E%7B(r)%7D%20%5Cbig%5Crvert%20%3D%20l%5E%7B(r)%7D%20%5Cleq%20l%20%3D%20%5Cleft%5Cvert%5C%2C%7B%5Cmathsf%7BE%7D%5C%2C%5Cright%5Cvert%2C%5Cquad%0A%5Cmathsf%7BP%7D%5E%7B(r)%7D%20%5Csubseteq%20%5Cmathsf%7BP%7D%2C%5C%20%5Cbig%5Clvert%20%5Cmathsf%7BP%7D%5E%7B(r)%7D%20%5Cbig%5Crvert%20%3D%20m%5E%7B(r)%7D%20%5Cleq%20m%20%3D%20%5Cleft%5Cvert%5C%2C%7B%5Cmathsf%7BP%7D%5C%2C%5Cright%5Cvert.%0A)
%7D) ,
, %7D) and
and %7D) . , , :
. , , :
%7D%20%5Cbig%5Crvert%20%5Cgeq%202%5E%7B2n%7D%20-%202%20l%5E%7B(r)%7D%20m%5E%7B(r)%7D%202%5En%20%5Cgeq%202%5E%7B2n%7D%20-%202lm%202%5En.%0A)
, ( ). ,
( ). ,  , ,
, ,  –
–  . , , , .
. , , , .
, ,
,  – , , , ,
– , , , ,  (
(  ):
):
Let be —
—  –. :
–. :
%7D%20%3D%20%5Cmathsf%7BE%7D%5E%7B(r)%7D%20%5Ccup%20%5Cleft%5Clangle%20P%2C%20C%20%5Cright%5Crangle%3B%20%5Cquad%20%5Cmathsf%7BP%7D%5E%7B(r%20%2B%201)%7D%20%3D%20%5Cmathsf%7BP%7D%5E%7B(r)%7D.%0A)
 ,
,  . Key
. Key  ,
,  :
:
%7D%20%5Csetminus%20%5Cmathcal%7BK%7D%5E%7B(r%20%2B%201)%7D%20%5Cbig%5Crvert%20%5Cleq%0A%5C%23%7BK_1%20%7D%0A)
Number%7D)
 (
(  )
)  ,
, 
 –
– %7D) ,
,  —
—  –
– %7D) :
:
%7D%0A%3D%20%5C%23%5Cleft%5Clbrace%20K_1%20%5Ctext%7B%20is%20a%20bad%20key%7D%20%5Cright%5Crbrace%0A%3D%20%5C%23%5Cleft%5Clbrace%20%0AP_i%20%5Coplus%20M_j%20%5Cmid%20%5Cleft%5Clangle%20P_i%2C%20C_i%20%5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BE%7D%5E%7B(r%20%2B%201)%7D%2C%20%5Cleft%5Clangle%20M_j%2C%20M_j'%20%5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BP%7D%5E%7B(r%20%2B%201)%7D%20%20%5Cright%5Crbrace%7D.%0A)
%7D) and
and %7D) , :
, :
%7D%0A%3D%20Q_%7BK_1%7D%5E%7B(r)%7D%20%2B%20%5C%23%5Cleft%5Clbrace%20P%20%5Coplus%20M_j%20%5Cprovided%20%5Cleft%5Clangle%20M_j%2C%20M_j'%20%5Cright%5Crbrace%20%5Cin%20%5Cmathsf%7BP%7D%5E%7B(r)%20%5Cright%5Crangle%7D%0A%5Cleq%20Q_%7BK_1%7D%5E%7B(r)%7D%20%2B%20m.%0A)
,
%7D%20%2B%20m) :
:
%7D%0A%3D%20Q_%7BK_2%7D%5E%7B(r)%7D%20%2B%20%5C%23%5Cleft%5Clbrace%20C%20%5Coplus%20M_j'%20%5Cprovided%20%5Cleft%5Clangle%20M_j%2C%20M_j'%20%5Cright%5Crbrace%20%5Cin%20%5Cmathsf%7BP%7D%5E%7B(r)%20%5Cright%5Crangle%7D%0A%5Cleq%20Q_%7BK_2%7D%5E%7B(r)%7D%20%2B%20m.%0A)
%7D)

 :
:
%7D%20%5Cleq%20Q_%7BK_1%7D%5E%7B(r%20%2B%201)%7D%20%5Ccdot%202%5En%20%2B%202%5En%20%5Ccdot%20Q_%7BK_2%7D%5E%7B(r%20%2B%201)%7D%20%3D%20Q_K%5E%7B(r)%7D%20%2B%202%20m%202%5En%2C%0A)
:
%7D%20-%20Q_K%5E%7B(r)%7D%20%5Cleq%202%20m%202%5En.%0A)
, ( )
 , (
, (  ),
),
![\Pr{\left[
\underline{K} \in \mathcal{K}^{(r)} \setminus \mathcal{K}^{(r + 1)} \mid
\left\langle P, C \right\rangle
\right]} =
\frac{
\Delta_{r, r+1} Q_{\mathrm{E}, K}
}{
Q_K^{(r)}
} \leq \frac{2m}{2^n - 2lm} .](http://tex.s2cms.ru/svg/%0A%5CPr%7B%5Cleft%5B%0A%5Cunderline%7BK%7D%20%5Cin%20%5Cmathcal%7BK%7D%5E%7B(r)%7D%20%5Csetminus%20%5Cmathcal%7BK%7D%5E%7B(r%20%2B%201)%7D%20%5Cmid%20%0A%5Cleft%5Clangle%20P%2C%20C%20%5Cright%5Crangle%20%0A%5Cright%5D%7D%20%3D%20%0A%5Cfrac%7B%0A%5CDelta_%7Br%2C%20r%2B1%7D%20Q_%7B%5Cmathrm%7BE%7D%2C%20K%7D%0A%7D%7B%0AQ_K%5E%7B(r)%7D%0A%7D%20%5Cleq%20%5Cfrac%7B2m%7D%7B2%5En%20-%202lm%7D%20.%0A)
 , ,
, ,  (
(  ),
),
![\Pr{\left[
\underline{K} \in \mathcal{K}^{(r)} \setminus \mathcal{K}^{(r + 1)} \mid
\left\langle P, C \right\rangle
\right]} =
\frac{
\Delta_{r, r+1} Q_{\mathrm{D}, K}
}{
Q_K^{(r)}
} \leq \frac{2m}{2^n - 2lm} .](http://tex.s2cms.ru/svg/%0A%5CPr%7B%5Cleft%5B%0A%5Cunderline%7BK%7D%20%5Cin%20%5Cmathcal%7BK%7D%5E%7B(r)%7D%20%5Csetminus%20%5Cmathcal%7BK%7D%5E%7B(r%20%2B%201)%7D%20%5Cmid%20%0A%5Cleft%5Clangle%20P%2C%20C%20%5Cright%5Crangle%20%0A%5Cright%5D%7D%20%3D%20%0A%5Cfrac%7B%0A%5CDelta_%7Br%2C%20r%2B1%7D%20Q_%7B%5Cmathrm%7BD%7D%2C%20K%7D%0A%7D%7B%0AQ_K%5E%7B(r)%7D%0A%7D%20%5Cleq%20%5Cfrac%7B2m%7D%7B2%5En%20-%202lm%7D%20.%0A)
Let be —
—  –. :
–. :
%7D%20%3D%20%5Cmathsf%7BE%7D%5E%7B(r)%7D%3B%20%5Cquad%20%5Cmathsf%7BP%7D%5E%7B(r%20%2B%201)%7D%20%3D%20%5Cmathsf%7BP%7D%5E%7B(r)%7D%20%5Ccup%20%5Cleft%5Clangle%20M%2C%20M'%20%5Cright%5Crangle.%0A)
 ,
,  .
.
Number%7D)
 (
(  )
)  ,
, 
 –
– %7D) ,
,  —
—  –
– %7D) :
:
%7D%0A%3D%20%5C%23%5Cleft%5Clbrace%20K_1%20%5Ctext%7B%20is%20a%20bad%20key%7D%20%5Cright%5Crbrace%0A%3D%20%5C%23%5Cleft%5Clbrace%20P_i%20%5Coplus%20M_j%20%5Cmid%20%5Cleft%5Clangle%20P_i%2C%20C_i%20%5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BE%7D%5E%7B(r%20%2B%201)%7D%2C%20%5Cleft%5Clangle%20M_j%2C%20M_j'%20%5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BP%7D%5E%7B(r%20%2B%201)%7D%20%5Cright%5Crbrace.%0A)
%7D) and
and %7D) , :
, :
%7D%0A%3D%20Q_%7BK_1%7D%5E%7B(r)%7D%20%2B%20%5C%23%5Cleft%5Clbrace%20P_i%20%5Coplus%20M%20%5Cmid%20%5Cleft%5Clangle%20P_i%2C%20C_i%20%5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BE%7D%5E%7B(r)%7D%20%5Cright%5Crbrace%0A%5Cleq%20Q_%7BK_1%7D%5E%7B(r)%7D%20%2B%20l.%0A)
,
%7D%20%2B%20l) :
:
%7D%0A%3D%20Q_%7BK_2%7D%5E%7B(r)%7D%20%2B%20%5C%23%5Cleft%5Clbrace%20C%20%5Coplus%20M_j'%20%5Cmid%20%5Cleft%5Clangle%20M_j%2C%20M_j'%20%5Cright%5Crangle%20%5Cin%20%5Cmathsf%7BP%7D%5E%7B(r)%7D%20%5Cright%5Crbrace%0A%5Cleq%20Q_%7BK_2%7D%5E%7B(r)%7D%20%2B%20m.%0A)
%7D)

 :
:
%7D%20%5Cleq%20Q_%7BK_1%7D%5E%7B(r%20%2B%201)%7D%20%5Ccdot%202%5En%20%2B%202%5En%20%5Ccdot%20Q_%7BK_2%7D%5E%7B(r%20%2B%201)%7D%20%3D%20Q_K%5E%7B(r)%7D%20%2B%202%20l%202%5En%2C%0A)
:
%7D%20-%20Q_K%5E%7B(r)%7D%20%5Cleq%202%20l%202%5En.%0A)
, ( )
 , (
, (  ),
),
![\Pr{\left[
\underline{K} \in \mathcal{K}^{(r)} \setminus \mathcal{K}^{(r + 1)} \mid
\left\langle M, M' \right\rangle
\right]} = \frac{\Delta_{r, r+1} Q_{\mathrm{P}, K}}{Q_K^{(r)}} \leq \frac{2l}{2^n - 2lm}.](http://tex.s2cms.ru/svg/%0A%5CPr%7B%5Cleft%5B%0A%5Cunderline%7BK%7D%20%5Cin%20%5Cmathcal%7BK%7D%5E%7B(r)%7D%20%5Csetminus%20%5Cmathcal%7BK%7D%5E%7B(r%20%2B%201)%7D%20%5Cmid%0A%20%5Cleft%5Clangle%20M%2C%20M'%20%5Cright%5Crangle%0A%5Cright%5D%7D%20%3D%20%5Cfrac%7B%5CDelta_%7Br%2C%20r%2B1%7D%20Q_%7B%5Cmathrm%7BP%7D%2C%20K%7D%7D%7BQ_K%5E%7B(r)%7D%7D%20%5Cleq%20%5Cfrac%7B2l%7D%7B2%5En%20-%202lm%7D.%0A)
 , ,
, ,  (
(  ),
),
%7D%20%5Csetminus%20%5Cmathcal%7BK%7D%5E%7B(r%20%2B%201)%7D%20%5Cprovided%20%5Cleft%5Clangle%20M%2C%20M'%20%5Cright%5Crangle%7D%20%3D%20%5Cfrac%7B%5CDelta_%7Br%2C%20r%2B1%7D%20Q_%7B%5Cmathrm%7BP%7D%5E%7B-1%7D%2C%20K%7D%7D%7BQ_K%5E%7B(r)%7D%7D%20%5Cleq%20%5Cfrac%7B2l%7D%7B2%5En%20-%202lm%7D.%0A)
:
 –
–  ,
,  , ,
, ,  , ,
, , ) ,
, 
 (
(  ),
), ) .
.
,


 ,
, ) . ,
. , 
 :
:
%7D%7D%20%5Cleq%20%5Cfrac%7B4lm%7D%7B2%5En%20-%202lm%7D.%0A)
 «»
«»  –
–  :
:
%20%5Coplus%20%5Cunderline%7BK%7D_2%20%3D%20C%0A)
 ,
,  —
—  and
and  . ,
. ,  –
– 
 ,
,  or
or  .
.
,

 –
–  ,
, 
 – , «»
– , «»  — . ,
— . , )
) «»,
«»,
![\Pr{\left[
\pi(P \oplus \underline{K}_1) = C \oplus \underline{K}_2
\right]} = \frac{1}{2^n - (m + l)} = \mathcal{O}\!\left(\frac{lm}{2^n}\right).](http://tex.s2cms.ru/svg/%0A%5CPr%7B%5Cleft%5B%0A%5Cpi(P%20%5Coplus%20%5Cunderline%7BK%7D_1)%20%3D%20C%20%5Coplus%20%5Cunderline%7BK%7D_2%0A%5Cright%5D%7D%20%3D%20%5Cfrac%7B1%7D%7B2%5En%20-%20(m%20%2B%20l)%7D%20%3D%20%5Cmathcal%7BO%7D%5C!%5Cleft(%5Cfrac%7Blm%7D%7B2%5En%7D%5Cright).%0A)

 :
:
%7D%20%3D%20%5Cbigo%7B%5Cfrac%7Blm%7D%7B2%5En%7D%7D%2C%0A)
.
,
,
:
Let be
, ,
;
, :
Number
,
:
, ( )
Let be
, ,
;
, :
Number
,
:
, ( )
.
:
,
,
.
Corollary 2.1.
Let the permutation be
Durability of the system using pseudo-random substitution 
The cipher proposed in [EM97] retains the shown crypto resistance property even if the substitution is
To prove this statement, it suffices to clarify the concept of a pseudo-random permutation.
Definition
Let be
In other words, in the presented computation model with oracles, the pseudo-random substitution is indistinguishable from the random one. Therefore, the following theorem holds.
Theorem 3
Let the permutation be
In continuation
Yes, there is gunpowder in the old dog yet. If there are people interested in Habré, then in the next part I can consider modifications of this classical scheme, and various cryptographic attacks on it (which, by the way, show that the obtained estimate from the bottom is accurate and cannot be improved).
Bibliography
For those who are very interested in:
- Eli Biham, Yaniv Carmeli, Itai Dinur, Orr Dunkelman, Nathan Keller, and Adi Shamir. Cryptanalysis of iterated Even-Mansour schemes with two keys. IACR Cryptology ePrint Archive, 2013:674, 2013.
- Andrey Bogdanov, Lars R Knudsen, Gregor Leander, Francois-Xavier Standaert, John Steinberger, and Elmar Tischhauser. Key-alternating ciphers in a provable setting: Encryption using a small number of public permutations. In Advances in Cryptology–EUROCRYPT 2012, pages 45–62. Springer, 2012.
- Alex Biryukov and David Wagner. Advanced slide attacks. In Advances in Cryptology—EUROCRYPT 2000, pages 589–606. Springer, 2000.
- Shan Chen, Rodolphe Lampe, Jooyoung Lee, Yannick Seurin, and John Steinberger. Minimizing the two-round Even-Mansour cipher. In Advances in Cryptology–CRYPTO 2014, pages 39–56. Springer, 2014.
- Joan Daemen. Limitations of the Even-Mansour construction. In Advances in Cryptology—ASIACRYPT'91, pages 495–498. Springer, 1993.
- Itai Dinur, Orr Dunkelman, Nathan Keller, and Adi Shamir. Key recovery attacks on 3-round Even-Mansour, 8-step LED-128, and full AES2. In Advances in Cryptology-ASIACRYPT 2013, pages 337–356. Springer, 2013.
- Orr Dunkelman, Nathan Keller, and Adi Shamir. Minimalism in cryptography: The Even-Mansour scheme revisited. In Advances in Cryptology–EUROCRYPT 2012, pages 336–354. Springer, 2012.
- [EM97] Shimon Even and Yishay Mansour. A construction of a cipher from a single pseudorandom permutation. Journal of Cryptology, 10(3):151– 161, 1997.
- Shoni Gilboa and Shay Gueron. Balanced permutations even-mansour ciphers. arXiv preprint arXiv:1409.0421, 2014.
- Philip Hawkes and Luke O'Connor. Xor and non-xor differential probabilities. In Advances in Cryptology—EUROCRYPT'99, pages 272–285. Springer, 1999.
- Nicky Mouha and Atul Luykx. Multi-key security: The Even-Mansour construction revisited. Technical report, Cryptology ePrint Archive, Report 2015/101, 2015.
- Ivica Nikolic, Lei Wang, and Shuang Wu. Cryptanalysis of round-reduced LED. In Shiho Moriai, editor, Fast Software Encryption, volume 8424 of Lecture Notes in Computer Science, pages 112–129. Springer Berlin Heidelberg, 2014.
PS A part of this publication was written in TeX, while the layout on Habré could appear jambs, mainly in formulas. If you notice - please, fix it.
EDIT 1. Corrected the names of scientists, thanks alexyr .
Source: https://habr.com/ru/post/265607/
All Articles