Protection of negotiations. Anti-bugs and field indicators
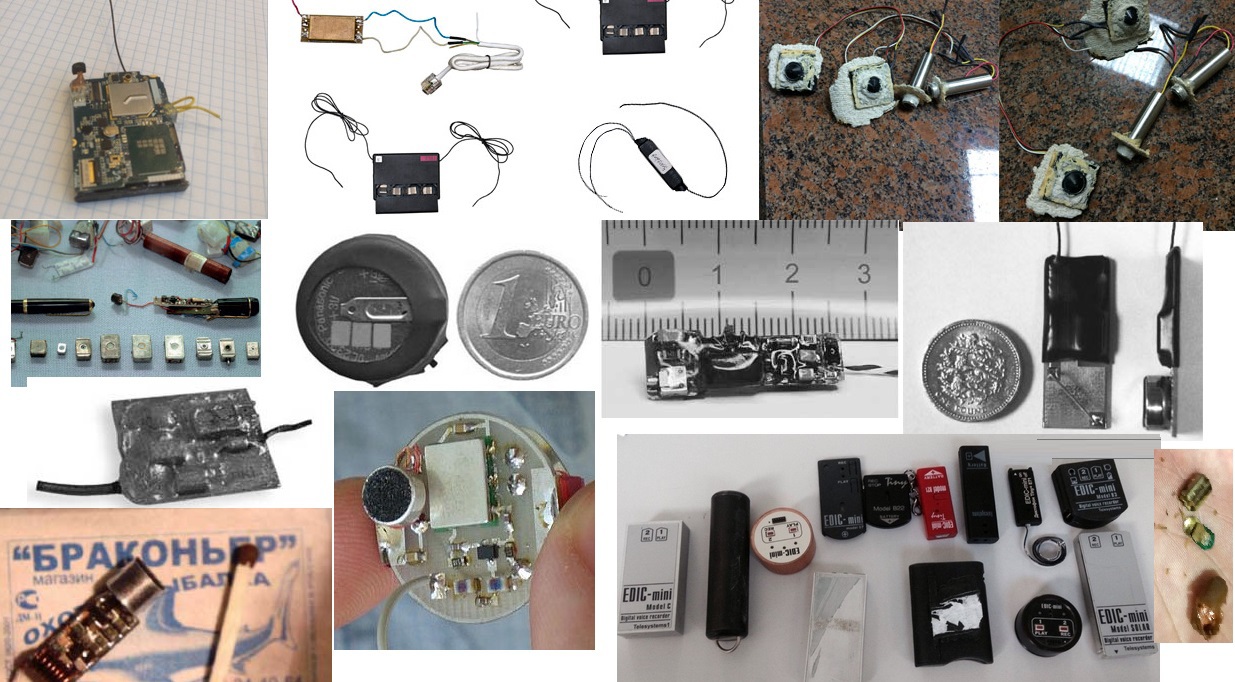
Examples of bugs found (photo source: Internet)
It was still in Vladivostok.
Familiar, the owners of travel agencies, said that one day the cleaning lady asked them: "And why in the evening, when everyone leaves, do you have something blinking on top of the closet?". Climbed on the cabinet, and there - almost a car battery and a walkie-talkie, bolted with blue electrical tape. This was the harshness of the Far Eastern wiretapping.
I found out that detsys.ru is hosting free training on the use of field indicators and asked them for a week three copies of anti-bugs and a couple more signal simulators to test the performance of the search engine in order to tinker with them in Hackspace.
')
Under the cut there are some historical examples of wiretapping and available ways to self-check their premises.
(If your distant acquaintances are confronted with the detection and, God forbid, with the installation of bugs, share in the comments)
Part 3 of Art. 138 of the Criminal Code of the Russian Federation provides for criminal liability for the illegal production, sale or purchase of special technical equipment intended for secretly obtaining information.
Such special technical means include, for example, devices for secretly obtaining acoustic information, visual observation, and listening to telephone conversations. The free circulation of such special devices is prohibited by federal law; only law enforcement officers and special services are allowed to use them during operational investigative activities. Development, production, sale and purchase of special technical equipment can be carried out exclusively on the basis of a license issued by the Federal Security Service of Russia.
How to listen
Legend
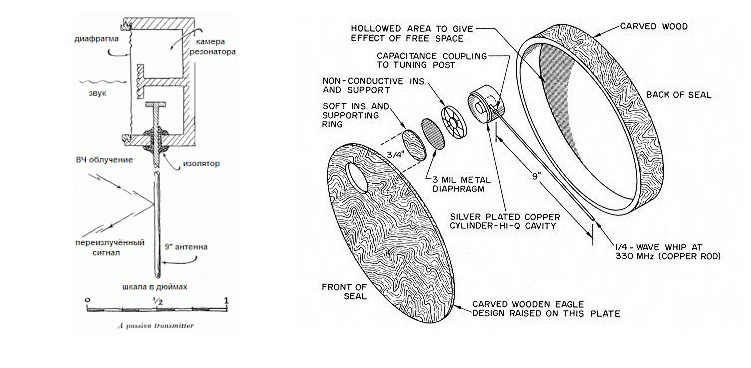
This legendary story began at the end of 1943, when Stalin was informed about the creation in the USSR of a unique listening device - a microwave resonator designed by Lev Theremen.
The Perpetual Mover did not need batteries and operated in a completely passive mode — neither magnetic fields, nor its own power sources — anything that could unmask the device. Placed inside an object, the “tadpole” was driven by microwave radiation from a remote source - the microwave wave generator itself could be located anywhere within a radius of hundreds of meters. Under the influence of the human voice, the nature of the oscillations of the resonating antenna was changed - it remained only to receive the signal reflected by the “bug”, record it on a magnetic tape and decipher it, restoring the original speech.
The spy system, code-named "Chrysostom," consisted of three elements: a pulse generator, a resonator ("bug") and a receiver of reflected signals, placed in the form of an isosceles triangle. The generator and receiver could be located outside the object being listened to, but the main problem was the installation of a “bug” in the office of the American ambassador.
Focus with fire failed. As practice has shown, the security of the Americans was all good. Access to the secret premises of the Embassy was strictly limited. None of the Soviet citizens and members of official delegations were allowed close to the upper floors of the building.
It was then that the idea of the "Trojan horse" was born.
The solemn ruler in the Artek camp, tied red ties and a line of young voiced voices singing the English anthem of the United States - the American ambassador broke through a tear. Touched by the warm welcome, Harriman handed the pioneer organization a check for 10 thousand dollars. Present on the lineup, the British ambassador also gave the pioneers a check for 5,000 pounds sterling. At the same moment, to the solemn sounds of music, the four pioneers introduced a varnished wooden shield with the USA coat of arms carved on it.
On the upper floors of the houses on the opposite side of the street, in front of the American Embassy, two safe houses of the NKVD appeared - they installed a generator and a receiver of reflected signals. The espionage system worked like a clock: the Yankees spoke, the Soviet intelligence officers recorded. In the mornings, wet linen was hung on the balconies of the apartments, the “housewives” from the NKVD diligently shook out the rugs, literally blowing dust into the eyes of the American counterintelligence.
For seven years, the Russian bug "undermined" worked in the interests of Russian intelligence. During this time, Zlatoust experienced four ambassadors - every time the new inhabitants of the office sought to change all the furniture and interiors, only the wonderful coat of arms remained invariably in the same place.
The existence of the "bug" in the Embassy of the Yankees learned only in 1952 - according to the official version, radio engineers accidentally discovered on the air the frequency on which Zlatoust worked. An urgent inspection of the Embassy’s premises was carried out, the entire office of the head of the embassy “was shaken upside down” - and found.

The British scientist Peter Wright helped Americans understand Zlatoust's work principles - familiarity with the microwave resonator Theremin was shocked by the Western intelligence services, experts themselves admitted that if not for the case, the “eternal bug” could still “undermine” the symbol of American statehood at the Embassy USA Moscow.
[ source ]
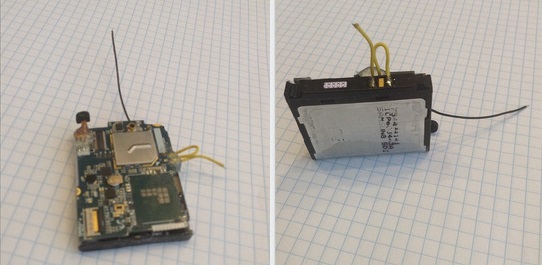
Battery cell phone (fake, but still interesting)

An unexpected find in the mobile phone that can expect each of us.
In general, - Samsung c4. Acc died, bought a new one. BUT, the old ack was swollen and the silhouette of the loop antenna showed up very nicely - like on tags of goods - in stores, so that they wouldn’t carry it out, I decided to find out what this thing was, I still wanted to throw it out.
A surprise was waiting for me.
read further about the sudden find
seemingly ordinary battery. neatly so we tear off the tape - and bang the antenna! really antenna!
and it is arranged in such a way that as you do not get out of it - it comes off when you try to open it. what actually happened.

climb further. looks torn like this:
1. - this is where the trail that comes off.
2. - the remains of the antenna.
Yes, here it is, SS45AE chip, in theory everything is a power controller, i.e. The whole system is a wireless charging system.
BUT! look further!

It would seem that the usual scheme for remote charging is wireless, but I was intrigued by the stray - highlighted in red. It goes from board to battery. Saw it.
The trick is that, as I understand it, a certain piezoelectric element. When connected to the tester, it does not show anything, but we include it in the supply chain - and we trim it to the insole display from the tape recorder - at the sounds - THE ARROW KITCHES!
Those. this element MAY work, (and apparently it works) AS A MICROPHONE!
In other words - such a chip many ask themselves: “Why even pulling out the battery is not enough - so they won't watch you?”
So the answer - in fact, the bug is built into the battery! That's all I wanted to say.
[ source ]

seemingly ordinary battery. neatly so we tear off the tape - and bang the antenna! really antenna!
and it is arranged in such a way that as you do not get out of it - it comes off when you try to open it. what actually happened.

climb further. looks torn like this:
1. - this is where the trail that comes off.
2. - the remains of the antenna.
Yes, here it is, SS45AE chip, in theory everything is a power controller, i.e. The whole system is a wireless charging system.
BUT! look further!

It would seem that the usual scheme for remote charging is wireless, but I was intrigued by the stray - highlighted in red. It goes from board to battery. Saw it.
The trick is that, as I understand it, a certain piezoelectric element. When connected to the tester, it does not show anything, but we include it in the supply chain - and we trim it to the insole display from the tape recorder - at the sounds - THE ARROW KITCHES!
Those. this element MAY work, (and apparently it works) AS A MICROPHONE!
In other words - such a chip many ask themselves: “Why even pulling out the battery is not enough - so they won't watch you?”
So the answer - in fact, the bug is built into the battery! That's all I wanted to say.
[ source ]
NSA

[ source ]
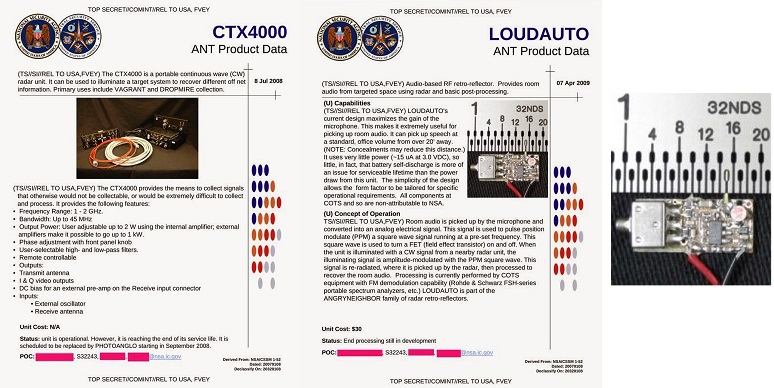
Portable radar CTX4000 is used as a base for all radio bookmarks.
The radar operates in the 1-2GHz range. The power of the internal amplifier is 2 W, the external one is up to 1 kW (for comparison, the power of a standard Wi-Fi card is 0.2 W). In 2008, the CTX4000 was supposed to be replaced by a more advanced version of PHOTOANGLO with the range expanded to 4 GHz and the size of a “small portfolio”.
When turned on, the radar creates around itself (or in front of itself, depending on the type of the radiator antenna) a high-power electromagnetic field at the selected frequency. The informative signal from the radio bookmark modulates this field, and the receiving antenna of the radio complex reads the modulated signal and uses the filter to extract the informative signal from it (HF imposition). The radar in this scheme as it organizes the communication channel between the bookmark and the receiving antenna. Similarly, for example, passive Recco avalanche sensors, or RFID cards, work.
The use of a powerful external carrier signal has several advantages:
antenna size and power of the bookmark emitter can be minimized;
a passive tab will consume significantly less energy (hence the size of the battery pack can also be reduced);
Passive bookmark is activated only when it is irradiated with a signal of a certain frequency, therefore, it is much more difficult to identify it than a conventional radio bookmark.
LOUDAUTO bug

Size: about 1.5 centimeters long without batteries
Price: $ 30
Sensitive microphone allows you to eavesdrop on the "office" conversation from a distance of more than 6 meters. The bug works on a 3 volt battery and consumes so little that the battery self-discharging currents can be higher than the current consumption of the bug. It is assembled from widely available components, therefore it will not be possible to connect it with the NSA (hence the “handicraft” look).
You can buy for 700 rubles on Aliexpress
Radio Tag TAWDRYYARD

Size: 6mm
Price: $ 30
Radio tag, which is often used to determine the location of the VGA cable with the RAGEMASTER tab, or any other purpose. Easily determined by radar from a distance of 15 meters. Able to work on one standard hour battery for months or years. Made from publicly available radio components. It is planned to integrate into it a GPS, a hardware identifier and a radio scanner-detector of other tabs TAWDRYYARD.
SURLYSPAWN Transmitter
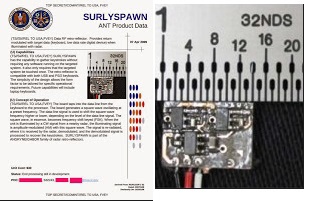
Size: 9mm
Price: $ 30
When irradiated with radar, it transmits to the radio in real time the keystrokes on the keyboard of a PC or laptop.
Bookmark for VGA cables RAGEMASTER
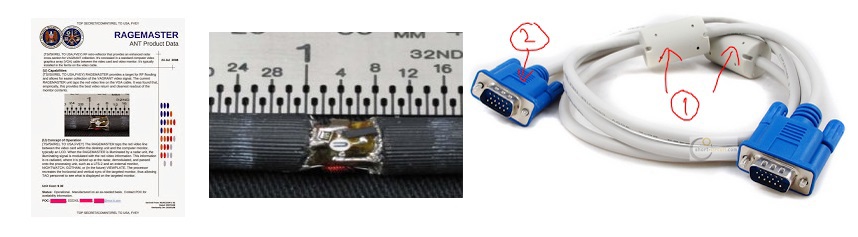
Size: 6mm
Price: $ 30
The bookmark is installed in the gap of the red core of the VGA cable.
When irradiated with a radar, the bookmark begins to emit a broadcast signal containing the current image on the monitor (only the red channel to simplify the whole scheme).
With the help of the NIGHTWATCH device, the attacker gets an exact copy of the image on his monitor.
[ source ]
Bulk Navalny

“Very poor equipment,” begin experts in the field of devices for secretly obtaining information. - Once upon a time such people in Russia were mass-produced and were massively used by law enforcement officers. But it was many, many years ago. So this is a mastodon of some kind. The microphone is very large, thick wires stick out in all directions ... It’s even a shame to show such a professional, and it’s just not decent to use. Now listen to committed in other ways.
[ source ]
Venediktov's bug
[ source ]
Bug in the prosecutor's office

One of the "bugs" was found in the telephone, the second was attached to the wire of the TV and turned on when the plug was plugged into the outlet. According to Anatoly Boyarkin, his office approximately twice a year is checked by officers of the FSB department in the Voronezh region for listening devices. The last one was held about six months ago, and the secret services did not find anything, and Boyarkin was assured that his office was out of control. “But I suspected that my office would be bugged,” said the prosecutor, “therefore I decided to turn to independent specialists.”
[ source ]
Under chevrons

“About the bugs ... Similarly, they were found in late July under the chevrons of the Slavs from the Druzhka battalion after shelling of its base in Petrovka. Unfortunately, I do not remember all the details. The Ukrainian attack aircraft worked out clearly in the mine department, under the chevrons of a wounded soldier, a bug was accidentally discovered during the dressing. A friend reported to me, the operatives found another 5 or 6 bugs exclusively in the form given in Slavyansk as early as the end of April ”
[ source ]
The future is here
When you do not need any special devices, but the sound can be restored by the picture.
Article on Habré - Researchers have restored the sound from the vibrations of objects in the video
TED Talk
How to find a wiretap
There are active and passive methods.
The nonlinear locator belongs to the active, it is something like a microwave impaled on a mine detector. When the teacher at the university turned it on, he warned that cell phones might smoke, and my head began to feel a little dizzy.
Passive detectors or field indicators. They respond to wireless transmission. Now there are three categories of devices on the market - “toys” (up to 10,000 rubles), “business” (10-50 thousand rubles) and professional (from 100 thousand rubles)
There are bugs, which, like the Chukchi, that they hear, they transmit. In this case, they can be detected by the “search” mode (this is like in the movie / cartoon “Ghostbusters” looking for anomalies). But there are “smart” bugs that accumulate information, and at certain times it is sent. In this case, only the “monitoring” mode with the recording of events and subsequent analysis will help.
a little theory about field indicators
The simplest UE (field indicator) consists of an antenna, a broadband amplifier, a threshold device, and a display device for a detected signal. The operating frequency range of such an indicator is determined by the bandwidth of the wideband amplifier, and the IP bandwidth is usually several gigahertz. Since in most PIs there are no input signal selection circuits, they are not capable of scanning the frequency range and react to the appearance of electromagnetic signals above the threshold value almost instantly,
regardless of the transmission frequency.
Recently, selective IPs have appeared on the market, operating on the principle of a scanning receiver, but with a wider bandwidth.
review. Due to the wide bandwidth, the sensitivity of the power source does not exceed 10 mV, and therefore the detection range of electromagnetic radiation exceeding the threshold value is low and in practice amounts to several meters (“near zone”), and also strongly depends on the operating frequency and power of the radiation source . Thus, the PI registers electromagnetic emissions exceeding the threshold values at the monitoring site and, in accordance with the criteria laid down in the control circuit of the device, displays the data about the detected signals to the display device.
Electromagnetic environment of almost any room is characterized by many components. It includes, above all,
radiation of legal sources, which include VHF radio stations, cellular and trunking communication systems, television, radio telephones, working household electronics, etc. The combination of these radiations constitutes the electromagnetic background of a room, which determines the threshold value for most field indicators . The background values of electromagnetic radiation will be approximately the same for the rooms adjacent to the test area.
When an active storage unit (stowing device) is inserted into the room, in most cases its radiation will differ sharply from the background in power, amplitude and significantly exceed the threshold value. When the threshold level is set correctly, the IP will begin to pick up the radiation of the charger and output the signal parameters to the display device, according to which the operator will be able to decide whether the detected radiation source belongs to the charger. Consequently, the information displayed on the display device plays an important role in determining the belonging of the detected radiation to the work of the charger.
[ source ]
regardless of the transmission frequency.
Recently, selective IPs have appeared on the market, operating on the principle of a scanning receiver, but with a wider bandwidth.
review. Due to the wide bandwidth, the sensitivity of the power source does not exceed 10 mV, and therefore the detection range of electromagnetic radiation exceeding the threshold value is low and in practice amounts to several meters (“near zone”), and also strongly depends on the operating frequency and power of the radiation source . Thus, the PI registers electromagnetic emissions exceeding the threshold values at the monitoring site and, in accordance with the criteria laid down in the control circuit of the device, displays the data about the detected signals to the display device.
Electromagnetic environment of almost any room is characterized by many components. It includes, above all,
radiation of legal sources, which include VHF radio stations, cellular and trunking communication systems, television, radio telephones, working household electronics, etc. The combination of these radiations constitutes the electromagnetic background of a room, which determines the threshold value for most field indicators . The background values of electromagnetic radiation will be approximately the same for the rooms adjacent to the test area.
When an active storage unit (stowing device) is inserted into the room, in most cases its radiation will differ sharply from the background in power, amplitude and significantly exceed the threshold value. When the threshold level is set correctly, the IP will begin to pick up the radiation of the charger and output the signal parameters to the display device, according to which the operator will be able to decide whether the detected radiation source belongs to the charger. Consequently, the information displayed on the display device plays an important role in determining the belonging of the detected radiation to the work of the charger.
[ source ]
First, a few words about bugs simulators, then about field indicators
TEST control device

Its use allows to evaluate the performance of the following modes:
- high frequency detector frequency meter;
- wireline analyzer (NPS);
- detector of low-frequency magnetic fields;
- infrared detector.
TEST is a set of simulators assembled in one case with autonomous power.
The simulator for evaluating the performance of a high-frequency detector-frequency meter is a mini radio transmitter with quartz frequency stabilization and the ability to turn off the modulating signal, for a wire line analyzer - a signal generator with a given frequency, for a detector of low-frequency magnetic fields - a source of stable magnetic field and for an infrared detector - IR transmitter -band with a given subcarrier frequency.
TEST allows you to evaluate the sensitivity of the test path, the accuracy of related measurements (frequency meter, NPS synthesizer), the operability of detectors, an oscilloscope, a spectrum analyzer and the display of measurement results.
Specifications:
- Mini radio transmitter frequency, MHz - 270 ± 0.01
- The frequency of the simulator submarine, MHz - 8.445
- IR transmitter wavelength, nm, - within 770-1100
- IR transmitter subcarrier frequency, kHz - 100
- Frequency of the modulating signal, kHz - 1
- Type of modulating signal - AIM
- Supply voltage, V - 3 (2 AA batteries)
- Current consumption, mA, - no more than 45
- Dimensions, mm - 88X56X18
This thing is designed to test expensive professional field indicators, such as "Piranha"
TTM-700

About this thing I did not find anything in the network, but the harsh inscription on the case evokes respect.
Antijugs
I conducted a superficial testing of the field indicators and share the results and impressions.
Bughunter

Chips - price (about 10 thousand rubles)
Primitive interface (where you really can only choose the sensitivity of the device), work only in real time (which does not allow to detect delayed transmissions). In my
tth
The operating frequency range is 50-3000 MHz (the entire range on which the bugs and hidden cameras operate)
Sensitivity (minimum detectable field strength) - at least 50 mV / m
Dynamic range, not less - 48 dB
Modes of operation - search, security, acoustical
Detection range of the radio transmitter 5 mW - 5 m
Cell phone detection range - 50 m
Sensitivity (minimum detectable field strength) - at least 50 mV / m
Dynamic range, not less - 48 dB
Modes of operation - search, security, acoustical
Detection range of the radio transmitter 5 mW - 5 m
Cell phone detection range - 50 m

Raksa

Chips - portability. The size of a matchbox and convenient mount. The device is disguised as a car keychain.
Allows to detect:
- cell phones of GSM900 / 1800, UMTS (3G), CDMA450 standards
- DECT cordless phones
- Bluetooth and Wi-Fi devices
- wireless camcorders
- radio transmitters with analog modulation (AM, FM, FM)
- radio carriers with digital modulation and continuous carrier (FSK, PSK, etc.)
- radio transmitters with broadband modulation with a bandwidth of up to 10 MHz
Features:
- selective radio reception
- high speed scanning and analysis
- detection of broadband and digital signals
- adaptation to the background in the protection mode
- search capability with subtraction spectrum
- audio control signals
- frequency and signal level measurement
- alarm event log
- silent alarm indication (vibration)
- no external antenna
Security mode
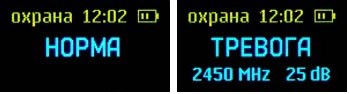
Security mode is designed to continuously monitor detected analog and digital radio signals in automatic mode (without operator intervention) and an alarm signal in case of a dangerous radio signal, i.e. radio signal with a level higher than the set threshold. Security mode is used in cases when the source of the dangerous radio signal is absent or inactive. Information about alarm events is stored in the log.
In the protection mode for analog signals, the background spectrum is subtracted. This reduces the influence of stationary (constantly present) interfering signals and interference. The background spectrum adaptation algorithm tracks slow changes in the levels of these interfering signals.
Browse mode Browse
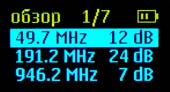
mode is designed to detect all types of analog and digital radio signals. In this mode, the display shows a list of all currently detected signals, sorted by frequency or type of signal.
Search mode

Search mode is designed to detect and locate analog and digital radio transmitters. The display shows the signal with the maximum level. This mode is used in cases where it is possible to move the field indicator to search for a radio transmitter.
In the search mode for an analog signal, the light and sound indications of the relative signal level are realized - by the repetition frequency of the LED flashes, it is possible to judge the approach or distance from the radio transmitter.
Spectrum subtraction search mode
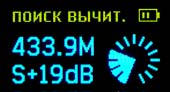
. , .
, – , . , , , , , . Since , .
.
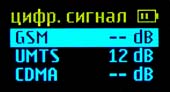
GSM900/1800, UMTS(3G), CDMA450, DECT, Bluetooth, Wi-Fi 2,4 .

The alarm event log stores information about the dangerous radio signals that were detected in the armed mode. The maximum number of records is 200. If at the same time dangerous signals of different types are detected, then information about each of them is stored in the log. When viewing a recording, the display shows the time of appearance and disappearance of the signal, its type and maximum level.
Specifications:
- received range: frequencies 50-3200 MHz
- typical sensitivity: 70 mV / m
- dynamic range: 50 dB
- bandwidth: 10 MHz
- full scan cycle time: 1.5 s
- protection time: 4-12 hours
- operating time in other modes: 3 hours
- Display: OLED, 128 x 64
- Dimensions: 77 x 43 x 18 mm
- weight: 35 g
Price: 18 000 rub The
TTM-700 bugs simulator can be detected by a usual search at a distance of 30-40 cm, in the “search with subtraction” mode at a distance of 60-70 cm.
I found the TEST simulator from a distance of 20-25 cm in the search mode, mode “search with subtraction” - 35-40 cm
ST 110

Chips - the coolest system of settings, work without false positives. Oscilloscope mode. Compatible with PC.
In general, the device looks and is made as a serious army device.
Two modes of operation:
- search for radio microphones (bugs) in the premises
- monitoring of radio microphones on visitors who come to your office, or on negotiations outside the office.
An additional RF antenna extends the frequency range to 7000 MHz.
What is it?
- radio microphones;
- telephone radio repeaters;
- radio stethoscope;
- hidden camcorders with the transfer of information over the air;
- technical means of spatial high-frequency irradiation systems;
- radio beacons of tracking systems for moving objects;
- cell phones, radios and cordless phones.
SEARCH mode:
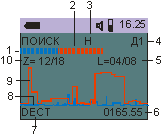
This mode is designed for quick search and positioning of the RTS. The use of this mode is based on a visual assessment of the level of signals on a 32 segment scale, for each frequency range. Additionally, a separate indication of continuous and pulse types of signals is used, the display of the identified signals is GSM, DECT, BLUETOOTH and 802.11g, as well as an indication of the frequency of a stable signal.
There are "smart bugs", there is a mode against it -
MONITORING mode:
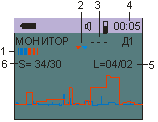
Designed to detect the RTS, by a given threshold, frequency or type of signal. During autonomous operation, information is saved in the non-volatile memory of the product (9 banks with 999 events).
Provided work on schedule.
PROTOCOL VIEWER mode:
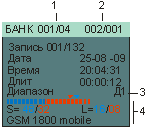
It is intended for viewing the protocol of events occurred as a result of the product operation in the MONITORING mode.
It is possible to sort the events according to the following criteria: the time of the occurrence of the event, the duration of the event, the signal level and the frequency range.
OSCILLOGRAPH mode
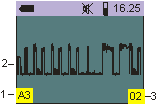
- Installation option (A - automatic P - manual) and the relative value of the vertical scan (from 1 to 7)
- Waveform
- The horizontal scan value in terms of full screen (from 1, 2,4,8, 16 and 32ms)
Work with PC:
- display in graphical form of the result of the ST 110 in real time;
- loading and displaying, both in graphic and in text format, the result of the work of ST 110 in the “Monitoring” mode (event log);
- complete control of ST 110 with a PC.
tth
, — 50-2500
, , :
75 (50 )
70 (1500 )
50 (2500 )
, :
55 (50-2000 )
40 (2000-2500 )
, :
35 (50 )
50 (500 )
20 (2500 )
, % — 0.005
, — 750
— Li-pol .
, , — 65
, — 90x54x21
, , — 0.15
– ST110.SHF
, — 2000-7000
, /c2 — (2-9)*10-10
, — 45
, , — 25
, — D=72, L=16
, — 50-2500
, , :
75 (50 )
70 (1500 )
50 (2500 )
, :
55 (50-2000 )
40 (2000-2500 )
, :
35 (50 )
50 (500 )
20 (2500 )
, % — 0.005
, — 750
— Li-pol .
, , — 65
, — 90x54x21
, , — 0.15
– ST110.SHF
, — 2000-7000
, /c2 — (2-9)*10-10
, — 45
, , — 25
, — D=72, L=16

Price: 28 000 rubles
I spotted the simulator of bugs TTM-700 at a distance of 150-170 cm, TEST at a distance of 45-50 cm.
Conclusion
- Baghanter will probably find something, but only in pure air a powerful transmitter (like a high tree in a pure field), but in modern industrial conditions it is rather useless.
- Raksa is good with herself in the pocket when negotiating
- The ST-110 is good for searching in a difficult electromagnetic environment and for searching difficult to detect transmitters.
Source: https://habr.com/ru/post/265457/
All Articles