Study: Vulnerabilities of a cryptotransponder allow keyless entry of over 100 models of machines.

Back in 2012, European researchers discovered serious vulnerabilities in the Megamos cryptotransmitter, which is installed in over 100 car models of various manufacturers (Audi, Ferrari, Cadillac, Volkswagen, etc.). The security errors they found allowed attackers to start cars with the autorun feature without a key.

')
Megamos cryptotransponder in auto key
The researchers managed to bypass all the transponder's proprietary security mechanisms, including encryption and authentication protocol, and implement three practical attack vectors that allow you to learn the device’s 96-bit secret key.
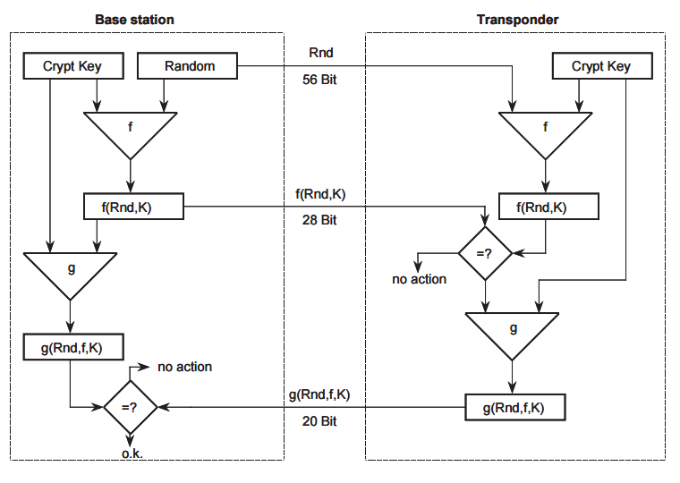
Authentication procedure
In the course of one of the attacks, they managed to start the car with the help of a device that emulates a transponder in just half an hour. Another attack is almost impossible to resist if the attacker has access to the car and the transponder for at least a short time (which is possible when renting a car or using a jack-parking ).
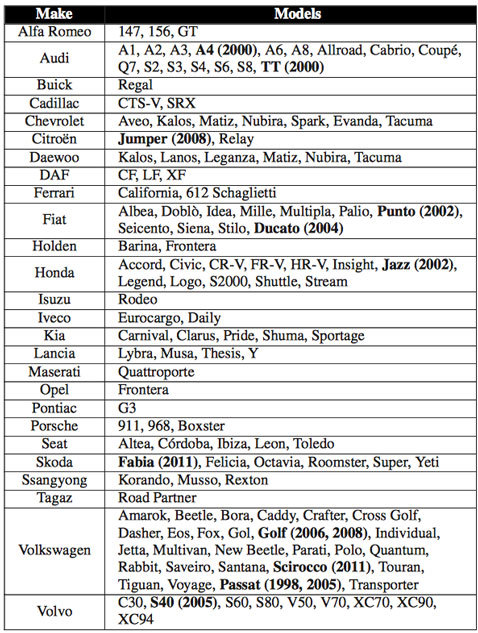
Vulnerable Car List
At the same time, according to the publication Net Security, security experts were able to publish their research only now because of the opposition of automakers. So, in 2013, their speech at the USENIX Security Symposium was blocked by Volkswagen, which appealed to the Supreme Court of Great Britain and secured a ban on the publication of key sections of the study. Now, the USENIX organizing committee has received permission to publish a version of the work, which omits information that could allow attackers to attack without deep technical skills.
Recently, the topic of information security cars occurs quite often. So in July 2015, the automaker Land Rover announced the recall of more than 65,000 cars, the software of which contained an error leading to the spontaneous unlocking of doors.
In addition, on a practical example, two researchers showed the journalist of the Wired publication the possibility of various attacks, including the remote interception of control of the brakes and gearbox of a car that drives on a highway in another state.
Jeep Cherookee 2014 release was equipped with FCA Uconnect, connecting to the mobile network Sprint. Security experts used a bug in Uconnect, which allows you to hack cars at any distance (it was originally planned that control could be seized within 100 meters of direct-WiFi operation).
Due to the vulnerability in Uconnect, they managed to get the GPS coordinates, identification number, model, date of issue and IP address of cars passing nearby.
During one of the demonstrations, the researchers remotely seized control of the Cherokee jeep, control windshield wipers, washer pump, steering wheel, and brakes. As a result, the jeep was sent to the ditch.
As a result, Chrysler released a patch and decided to withdraw more than 1.4 million vehicles. In addition, the press got information about several vulnerabilities in the electric vehicle Tesla Model S (which were later eliminated).
Earlier this year, BT launched an initiative to help automakers find out if their cars are subject to cyber attacks.
Car theft is not the only thing that might interest intruders. Another popular activity is unlocking some of the functions of the car, available only in more expensive models. In 2013, at the PHDays information security forum, Kirill Yermakov and Dmitry Sklyarov talked about hacking the ECU (Electronic Control Unit) vehicle control microcontroller to unlock functions that allow for maximum efficiency of the vehicle systems. Slides of this presentation can be viewed at the link .
Source: https://habr.com/ru/post/265233/
All Articles