Attack on archivers. Hiding in one archive from three programs
The article shows how you can trick an attentive user who is familiar with the basics of social engineering, watching even file extensions and in no way encourages the use of this information for illegal purposes. The goal is to run the executable file, issuing it as a text document in a zip archive, and if you run it is unlikely to work, then do not give unzip or hide the file.
On Habré there is already an article about the possibility of changing the order of reading Unicode characters using the RLO byte. It says that, using the standard Windows Explorer, it is difficult to notice the substitution (spoofing) of the file name. It deals with the shelter of a real file extension. There is also an article about the features of the archiver built into Explorer.
I, as a person who always keeps track of the extensions of the files being opened, wondered if there are any programs warning of this? In particular, are archivers protected? And what intruders can do to bypass the defense.
As an experimental, we take an executable file with the exe extension, let's call it “On txt.exe ”.
')
After the letter “n” in the file name editing mode in the context menu of the explorer, select “Insert Unicode Control Character” and select RLO. As a result, the display name of the file will change to “On uspexe.txt”.
Next, archive it. I used the most popular compression method - Zip. And we will start to open in different archivers.
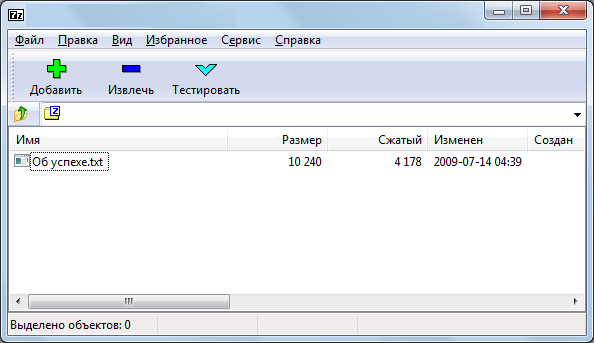
7-Zip 9.20 / 15.06
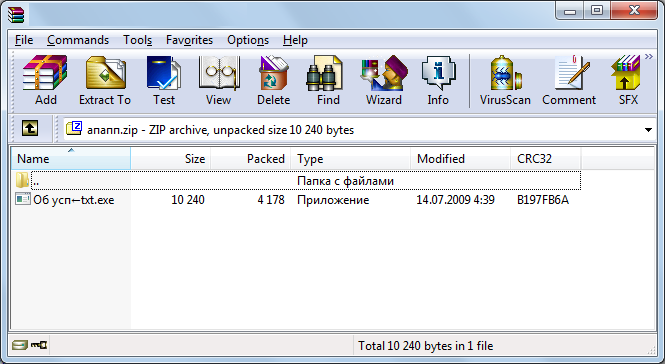
WinRAR 5.3
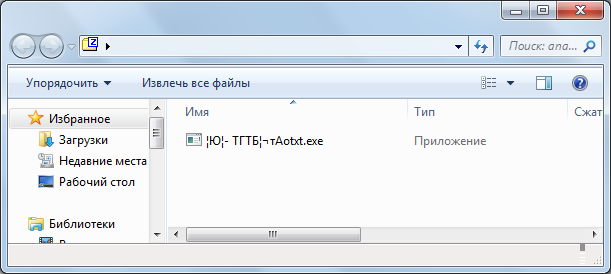
Built in Windows Explorer
As you can see, 7-zip immediately gave up, WinRAR pleased with the arrow, and the archiver built into the explorer does not support RLO. Now we are thinking, is it possible to spoof somehow with the last two archivers? To do this, open the archived file in the HEX-editor, while reading the specification format ZIP.
When compressing a file in zip, the file name is duplicated 2 times.
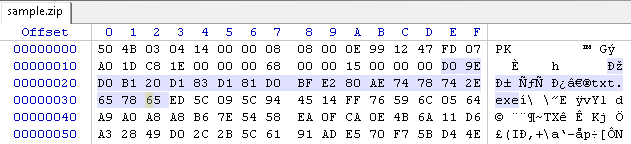
First entry
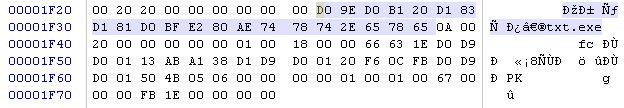
Second entry
And here there is a large field for creativity.
Firstly, it is possible to wipe the characters of the RLO byte in the second entry. Then WinRAR will display the name of the file “On uspexe.txt” and open it as a text document. However, if you go on changing the .txt extension to .jpg, then up to the WinRAR version 4.20 this pseudo-picture will be launched as an application. This vulnerability no longer exists in WinRAR 5.3b2.
Having opened the file with the RLO that was erased in the second entry in the archiver built into Windows Explorer, one can observe that the file name has become almost readable - only Russian letters are not readable. To make the name readable, we will replace their coding or write Latin ones. However, we do not need the user to open the program as a text document.
In order for the Explorer's archiver to stop seeing the file, it is enough to specify one of the NTFS characters reserved in the file name (for example, <). However, this will not save you from viewing the WinRAR archive. What to do? Add null-byte to the beginning of the file name!

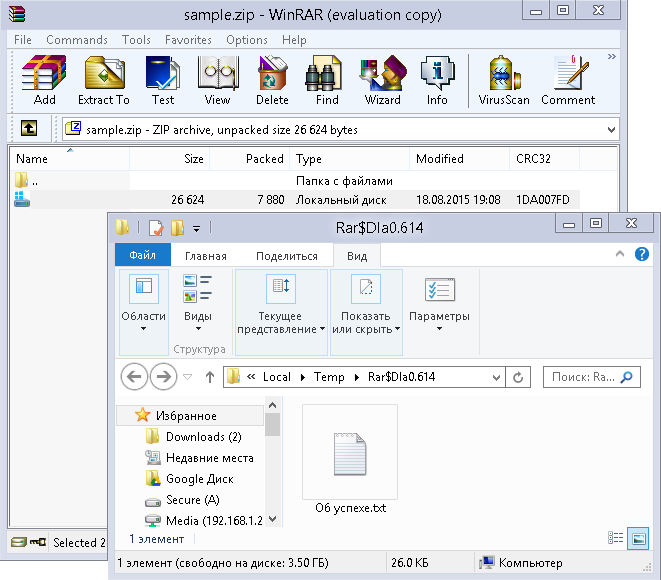
Then a small miracle will happen: WinRAR 5.3b will display the file as a folder “Local disk”, after moving into which inside the archiver, WinRAR automatically unpacks our file with the RLO symbol in the name (the name to unpack takes from the first entry!) Into the directory “Temp \ Rar $ * ”And will carefully show the executable file in the explorer as a text document! Note that after closing, the archiver will carefully try to delete this file like any other unpacked into a temporary directory.
You can simultaneously make it so that it is readable by the Explorer archiver. Then, instead of null, you need to prescribe another non-printable character.
But not everything is so sad. 7-Zip, for example, up to version 9.20 displays the name of the file from the second entry. However, if the file name in the second entry does not change and make not a Zip-archive, but some rare one, from these three archivers open only 7-Zip, and put it in our Zip-archive (do not find the familiar template - release a broken program where is usually a bunch of archives with files readme.txt?), then the attack will turn on him. Moreover, version 9.20 also incorrectly displays the name of a file starting with null, and will not allow it to be either read or unpacked.
Also in the review is not specified WinZip archiver. To be honest, I did not like the size, appearance and advertising in the unregistered version. However, in terms of warning the user about executable files and files with incorrect names, he passed all checks.
The sample.zip file is an example of creating such an archive. Inside is a program with a notepad icon that launches a notepad. Does nothing more. Hides from the archiver built into Explorer, forces WinRAR 5.3 to automatically decompress, displays the .txt extension in 7-zip version 15.
Another example is Sample 2 for all versions of 7-zip, WinRAR 3.8, Windows Explorer. Everywhere a file with * .txt extension:
On Habré there is already an article about the possibility of changing the order of reading Unicode characters using the RLO byte. It says that, using the standard Windows Explorer, it is difficult to notice the substitution (spoofing) of the file name. It deals with the shelter of a real file extension. There is also an article about the features of the archiver built into Explorer.
I, as a person who always keeps track of the extensions of the files being opened, wondered if there are any programs warning of this? In particular, are archivers protected? And what intruders can do to bypass the defense.
As an experimental, we take an executable file with the exe extension, let's call it “On txt.exe ”.
')
After the letter “n” in the file name editing mode in the context menu of the explorer, select “Insert Unicode Control Character” and select RLO. As a result, the display name of the file will change to “On uspexe.txt”.
Next, archive it. I used the most popular compression method - Zip. And we will start to open in different archivers.

7-Zip 9.20 / 15.06

WinRAR 5.3

Built in Windows Explorer
As you can see, 7-zip immediately gave up, WinRAR pleased with the arrow, and the archiver built into the explorer does not support RLO. Now we are thinking, is it possible to spoof somehow with the last two archivers? To do this, open the archived file in the HEX-editor, while reading the specification format ZIP.
When compressing a file in zip, the file name is duplicated 2 times.

First entry

Second entry
And here there is a large field for creativity.
Firstly, it is possible to wipe the characters of the RLO byte in the second entry. Then WinRAR will display the name of the file “On uspexe.txt” and open it as a text document. However, if you go on changing the .txt extension to .jpg, then up to the WinRAR version 4.20 this pseudo-picture will be launched as an application. This vulnerability no longer exists in WinRAR 5.3b2.
Having opened the file with the RLO that was erased in the second entry in the archiver built into Windows Explorer, one can observe that the file name has become almost readable - only Russian letters are not readable. To make the name readable, we will replace their coding or write Latin ones. However, we do not need the user to open the program as a text document.
In order for the Explorer's archiver to stop seeing the file, it is enough to specify one of the NTFS characters reserved in the file name (for example, <). However, this will not save you from viewing the WinRAR archive. What to do? Add null-byte to the beginning of the file name!

Then a small miracle will happen: WinRAR 5.3b will display the file as a folder “Local disk”, after moving into which inside the archiver, WinRAR automatically unpacks our file with the RLO symbol in the name (the name to unpack takes from the first entry!) Into the directory “Temp \ Rar $ * ”And will carefully show the executable file in the explorer as a text document! Note that after closing, the archiver will carefully try to delete this file like any other unpacked into a temporary directory.

You can simultaneously make it so that it is readable by the Explorer archiver. Then, instead of null, you need to prescribe another non-printable character.
Summary
- 7-Zip 15.06 displays the file name from the first entry (with the RLO symbol). The executable file is presented as a text document. Even if you have enabled the display of extensions of registered file types. Double click in the archiver window will launch the executable file.
- Windows internal archiver does not see this particular file. See other files.
- WinRAR 5.3b displays the file as a folder called “Local Disk”, and when it is inside the archiver, WinRAR automatically unpacks our file with a substitute name (with the RLO symbol) —the name to unpack takes from the first entry — to the Temp directory and carefully displays it in the explorer executable file as a text document!
But not everything is so sad. 7-Zip, for example, up to version 9.20 displays the name of the file from the second entry. However, if the file name in the second entry does not change and make not a Zip-archive, but some rare one, from these three archivers open only 7-Zip, and put it in our Zip-archive (do not find the familiar template - release a broken program where is usually a bunch of archives with files readme.txt?), then the attack will turn on him. Moreover, version 9.20 also incorrectly displays the name of a file starting with null, and will not allow it to be either read or unpacked.
Also in the review is not specified WinZip archiver. To be honest, I did not like the size, appearance and advertising in the unregistered version. However, in terms of warning the user about executable files and files with incorrect names, he passed all checks.
The sample.zip file is an example of creating such an archive. Inside is a program with a notepad icon that launches a notepad. Does nothing more. Hides from the archiver built into Explorer, forces WinRAR 5.3 to automatically decompress, displays the .txt extension in 7-zip version 15.
Another example is Sample 2 for all versions of 7-zip, WinRAR 3.8, Windows Explorer. Everywhere a file with * .txt extension:
Source: https://habr.com/ru/post/265051/
All Articles