SCADA and mobile phones: an assessment of the safety of applications that turn a smartphone into a plant control panel

Today, mobile technology is an integral part of our lives, and sometimes penetrate where they should not be used. Convenience is often more important than safety. Now you can monitor the state of the process control system (automated process control system) or even manage it from a new Android or iOS smartphone. Look for “HMI” (man-machine interface), “SCADA” (supervisory control and data acquisition system) or “PLC” (programmable logic controller) in the Google Play store, and you will be surprised at the number of results. Moreover, many of these applications are developed by serious manufacturers: Siemens, GE, Omron, etc., and provide access, control and management of HMI, PLC, DCS (distributed control system) and SCADA-systems in the infrastructure of the industrial control system. Are they safe? Can an attacker harm by gaining access to an engineer’s tablet? What vulnerabilities exist in these applications? What attack vectors are possible?
The goal is not only to find security errors in mobile applications for the process control system, but also to try to extrapolate the risks of these applications being compromised to the risks of compromising the entire infrastructure of the process control systems. This approach differs from the usual view of mobile application security assessment: vulnerabilities with traditionally low levels of risk can expose the process control system to great risk, and vulnerabilities that are usually considered critical threats, on the contrary, are dangerous for the process control system with a very low probability.
Little about the process control system
Modern infrastructures for automated process control systems have a complex architecture consisting of such well-known elements as servers, PCs, network switches, software technologies (.Net, DCOM, XML, etc.), and more complex components: programmable controllers, transmitters, power drives, analog control signals, etc.
')
Lower level (1)
Here are the field devices. As mentioned above, they are suitable for dirty work: for example, they can control the temperature and pressure in the reactor, control operations such as opening and closing valves, turning pumps on and off, etc. Many devices are often used at this level. These can be low-level programmable logic controllers.
In addition, at this level there can be transmitters and drives controlled by a remote terminal device (RTU, electronic device under the control of a microprocessor, which translates physical objects into signals understandable to a distributed control system or SCADA system by transmitting telemetry data to the host system and from the leading dispatching system to controlled objects). This layer is the realm of low-level industrial protocols, such as Modbus, Modbus TCP, HART, Wireless HART, Profibus DP or PA, Foundation Fieldbus H1. The engineers of the lower level of the process control system, electricians, technicians and other specialists work at this level of the process control system.
Intermediate Level (2)
At this level, you can find high-level PLCs, distributed control systems (DCS, process control systems, characterized by building distributed I / O systems and data processing decentralization), supervisory control and Data Acquisition systems (SCADA), software package designed to develop or provide real-time systems for collecting, processing, displaying and archiving information about a monitoring or control object) and human-machine interfaces (Hu man-Machine Interface (HMI)), as well as servers such as OPC (Open Platform Communications, formerly OLE for Process Control - OLE for process control). All intellectual activities are carried out here. Based on data from lower levels, operators and automated systems make decisions and send commands to field devices. Here goes the whole process of automation of production. Operators, process engineers, process control system engineers, PLC programmers and software work with systems at this level.
Top Level (3)
It integrates business and industrial processes. This layer provides a link to the corporate network and enterprise resource planning (ERP) systems. At this level there are various production asset management systems (PAS) and production process management systems (MES, providing the right information at the right time and showing decision-makers in the workplace how workshop conditions can be optimized to increase productivity). Here, managers and engineering and technical personnel of the highest level work with the automated process control system.
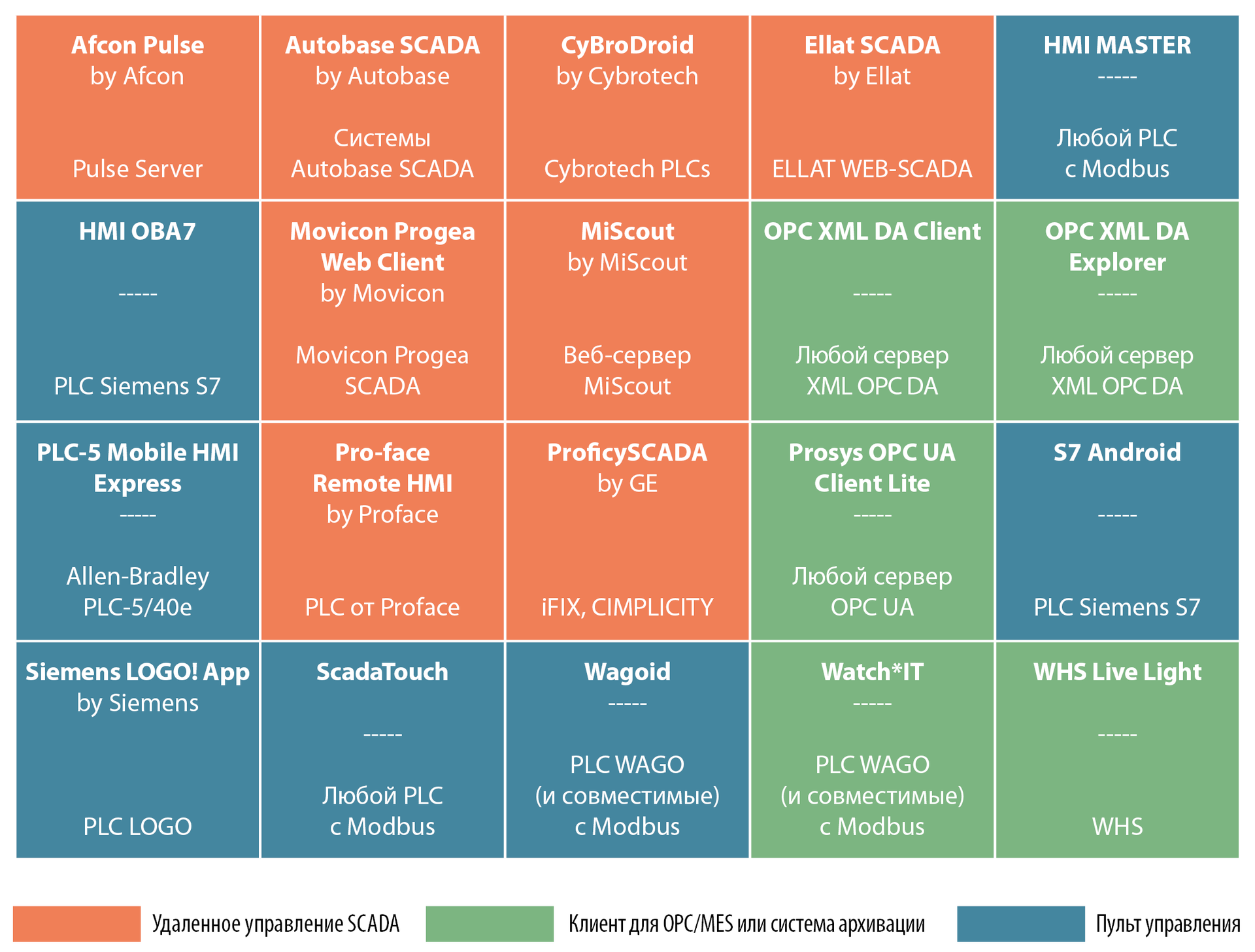
Types of Mobile Applications for Process Control Systems and Associated Risks
Control panel (1) : directly configuration / monitoring / control of the production process and / or its components. Roles in the process control system infrastructure:
- PLC configuration. Setting up and / or controlling the components of the process control system: PLC, HMI, connected to the PLC, RTU and others. The mobile application connects to the process control system component via the industrial network (lower and middle levels of infrastructure). It controls the state of the component or its (re) adjustment. It can be considered an analogue of a standard portable terminal, hidden inside a Nexus or Xperia.
- Client for SCADA. Control over the industrial process using SCADA-client or a virtual interface to connect to SCADA. These applications allow process engineers to connect from a phone or tablet to a SCADA application and, if necessary, control the production process.
- Mobile HMI panel. HMI-panel inside the mobile device to control or control several industrial components. Allows the engineer to configure (and even program!) The HMI panel and connect its components to the PLC or other devices via Modbus / TCP, OPC or other protocols and interfaces.
All these applications have one important feature - the connection between the application and the industrial component occurs in a supposedly safe environment , somewhere at the lower and middle levels of the process control system.
OPC / MES client or archiving system (2) : archiving applications allow an engineer or process owner to read and interpret some information from the middle and top level of the process control system components. The data is read-only, and the user does not even have direct access to the PLC, HMI or SCADA - only the ability to view certain variables. We included mobile clients for MES applications in this category. They are usually used to read data from the archive server or aggregated data from the MES system. A typical application from this category is a client (browser) for OPC. It is connected not directly to the components of the process control system, but to the OPC server. Connection usually occurs at the highest levels of infrastructure. In addition, the connection can be made remotely. This means that in such an application, encryption and authentication mechanisms should be implemented. Although reading the aggregated data does not in itself pose a threat, this information can be used by an attacker to understand (reverse engineer) the industrial process and create a specialized attack scenario. In addition, if the application is used outside the factory network, new threats appear: for example, the compromise of the engineer’s or manager’s phone through an application vulnerability.
Remote control SCADA (3) : applications that allow remotely (from outside the factory network) to monitor / control the production process. Although the solutions of the first category are suitable for this, the developers do not promote or even advertise this opportunity. For all applications of this group, we have found the images / schemes / architectural drawings / documents from the developer, where the mobile client is used for remote control outside the industrial network (higher and lower levels). Therefore, we assume that potential users will sometimes (or always) connect to the industrial process from public networks, unreliable home networks or via cellular communications. It is also unclear in what environment such an application will work on Android and whether there will be any malware, root system and other risk factors. The security and reliability requirements for such applications are the most stringent.
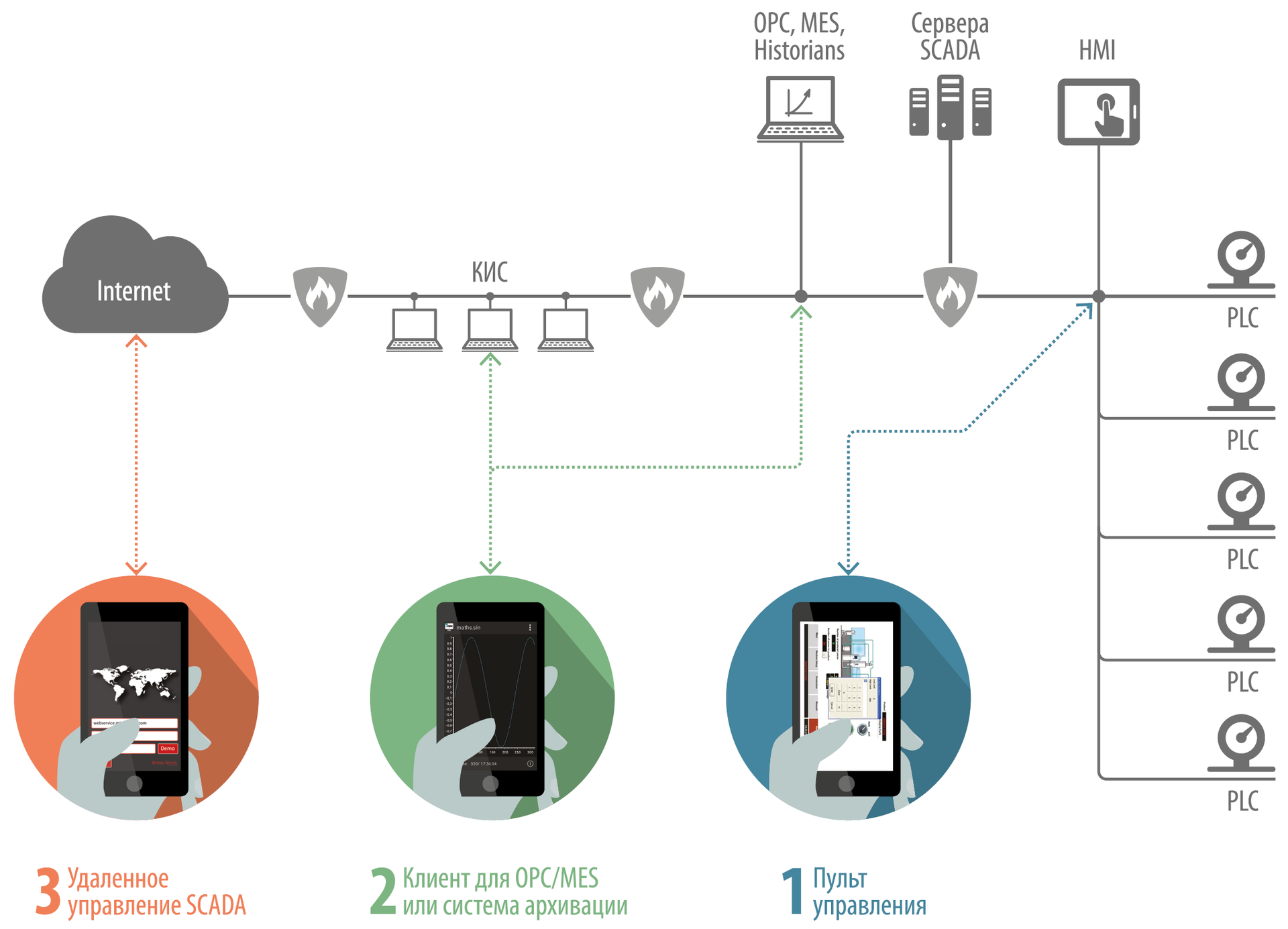
Typical locations of mobile applications for process control systems
Threats for different types of applications

Remote Control
The absence of server-side data verification from the point of view of the industrial process. Due to the fact that the server application completely trusts the data that came from the operator, and the correctness of the technological process depends entirely on the actions and commands that it sends, any shortcomings in data validation can lead to serious consequences. At the same time, in a mobile application it is easier to make a mistake in discharging a number or accidentally set a negative parameter value. Incorrect interpretation of values can also lead to a denial of service for both the server and client applications.
Compromise of data stored on an SD card — many applications store data on an SD card: logs, HMI projects, and other data. Accordingly, they all have access to general information. An application installed from third-party sources (or a fake from an official store) can read or modify this information — for example, change the interface or functionality of a mobile HMI application.
OPC / MES client or archiving system
Since these applications are no longer in a protected circuit and are transmitted over general-purpose networks (the Internet), the server and the application can be compromised by intercepting data that goes from application to server. An attacker can gain access to the authorization information, the configuration of the end device, any information about the state of the system, as well as replace the control commands.
Hiding alarms. Using the ability to intercept traffic, the attacker is able to change the response from the server in such a way that instead of information about the incident at the enterprise, the operator will receive a message that everything is in order, or, worse, opposite information. In turn, untimely or false information can lead to the suspension of the technological process, while the operator understands where the problem is: in the equipment or still in the application.
Denial of service to the client and server system can lead to delays in informing.
Remote control SCADA
Since applications of this type are positioned by software manufacturers precisely as a tool for remote control of SCADA servers, it is possible to intercept and change control commands, leak critical information, intercept and modify traffic in order to compromise the process.
List of applications: the table below lists all tested mobile applications (sorted by type).
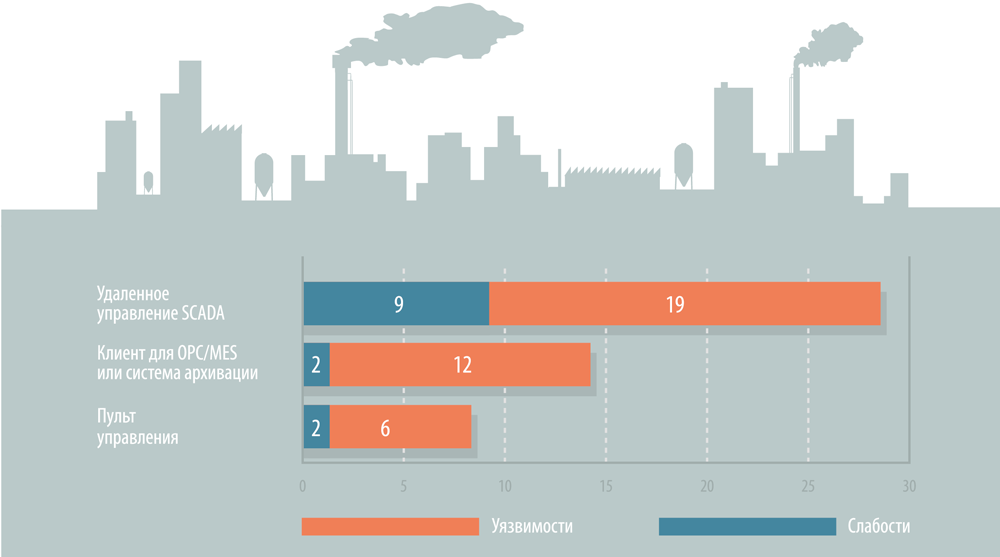
Vulnerabilities and attack example
In general, 50 vulnerabilities were found, among which: unprotected or insufficiently protected data transfer and storage methods (including incorrect use of SSL or “homemade” cryptoalgorithms), remote attack on denial of access to the client and server, SQL injection, use of untrusted input data as technical process setup parameters, etc. Operating these security issues potentially allows for a series of dangerous attacks on both the application and the operator. In the latter case, it is realistic to create a false idea of the current state of the process, which can lead to the adoption of wrong decisions with serious consequences for the enterprise.
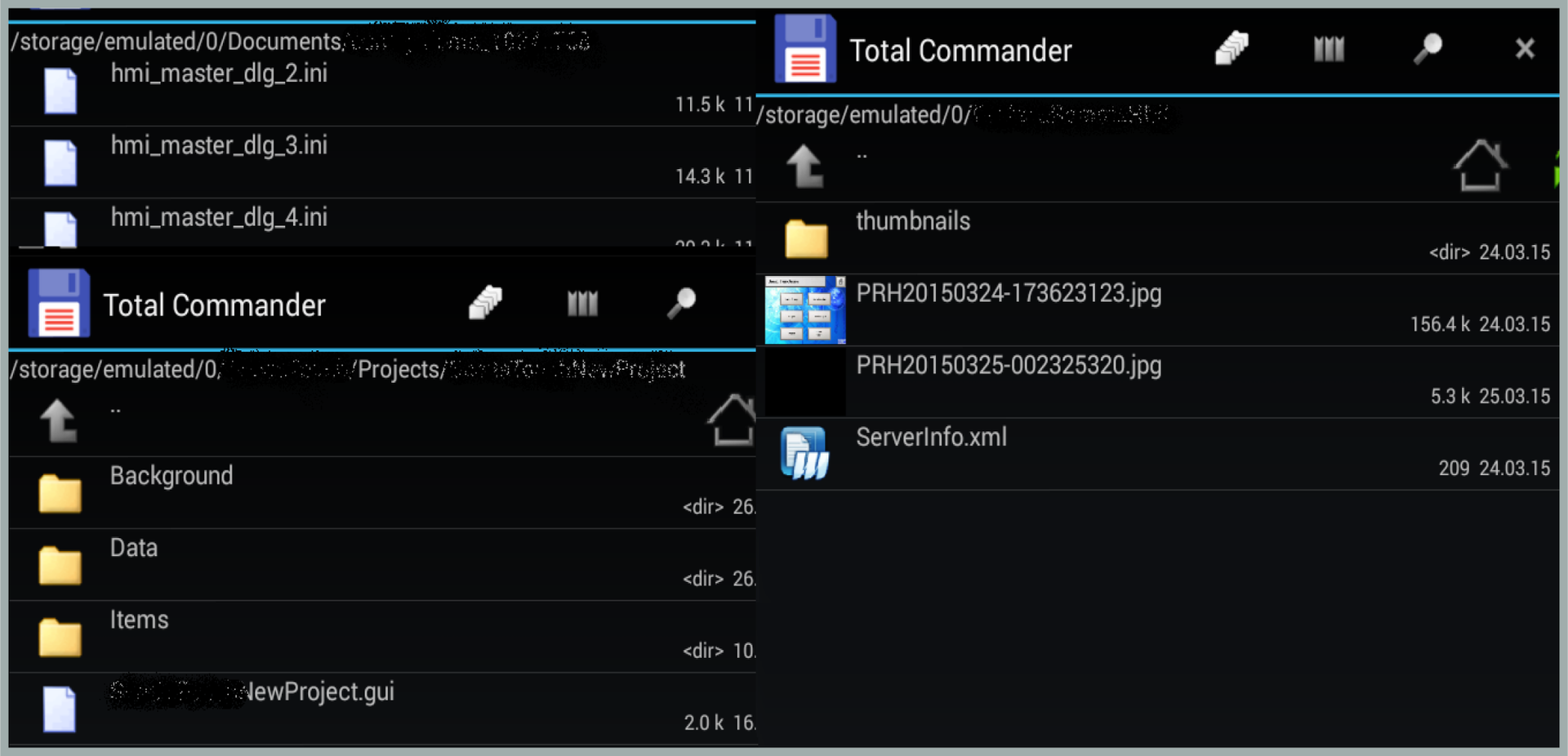
HMI Database Compromise
The data stored on the SD card can be accessed as follows:
- Through physical access to the SD card;
- Thanks to the virus on the device;
- Any vulnerability of the platform or third-party application. That is, by compromising a third-party application that is not related to the target mobile application, you can also access the SD card and modify the data.
During testing, it was revealed that a number of applications store the HMI database (electrical circuits, interfaces, connection parameters, HMI projects) on an SD card. The figure shows how it might look on a smartphone.
HMI project repository
As an example, take a very real HMI project. This application moves some liquid from one container to another. To control the process are buttons Start / Stop and flow sensor. If the HMI project data is compromised (virus, other application vulnerability, direct access to the SD card memory from a PC, etc.), the attacker is able to slightly change its configuration or interface.
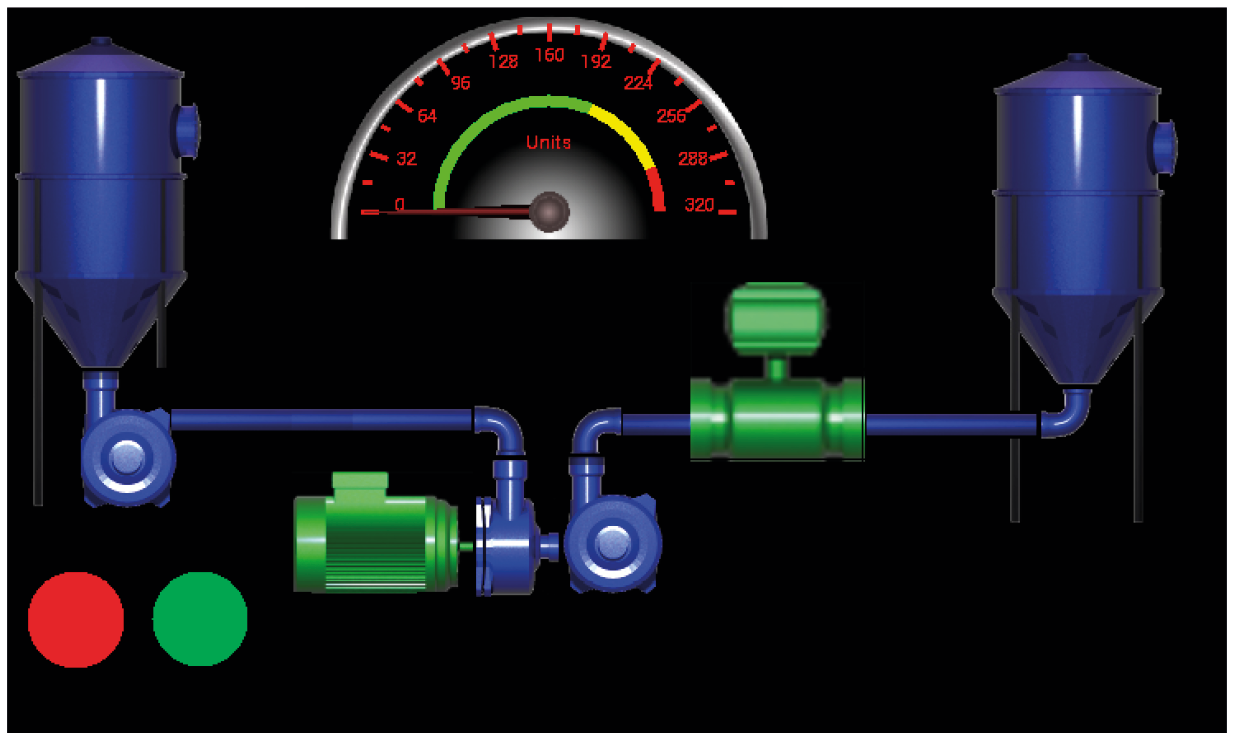
HMI flow sensor
It can replace events and the logic of components or, for example, data sources from sensors. When the operator launches the application the next time, he will see, for example, something like this.
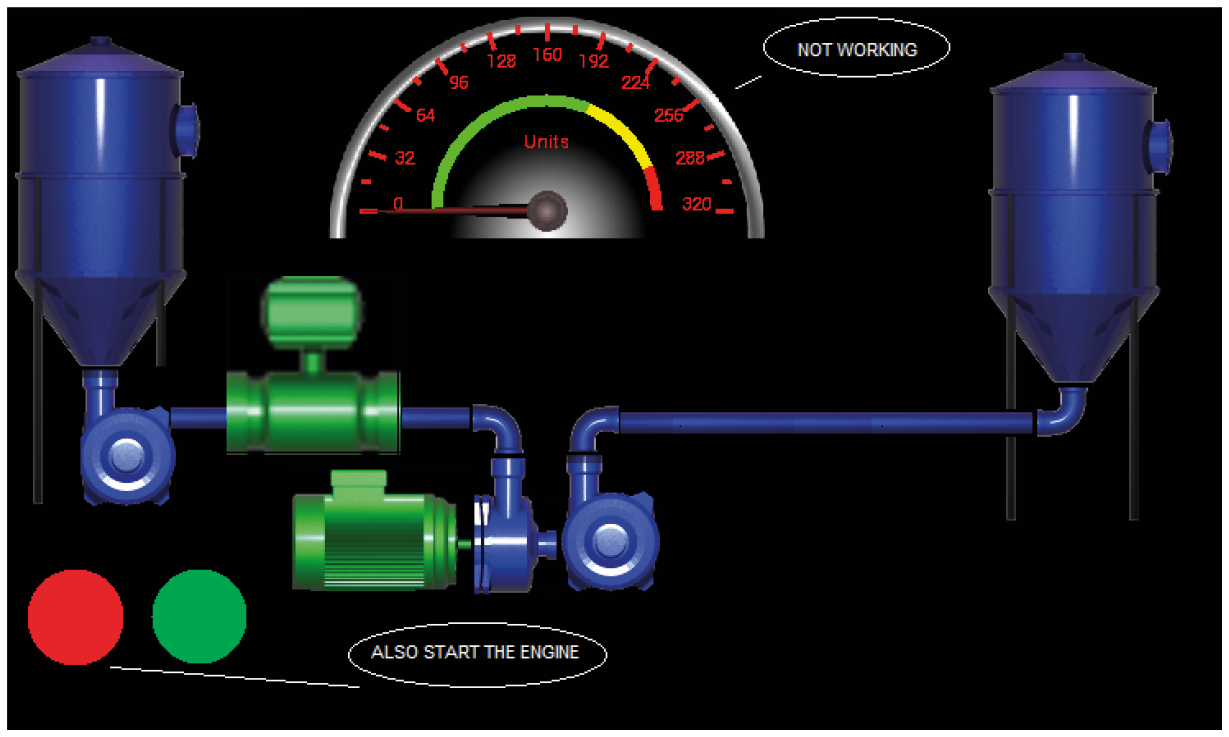
Changed interface
Now BOTH buttons start the process. Of course, it can be hoped that physical or low-level regulators will prevent danger, but an attack will at least lead to an alarm or even a technological malfunction.
Storage and transfer of data in open form
Even if all the data that the application stores and transfers is encrypted, the encryption keys are often stored in the code of the application itself and are static.
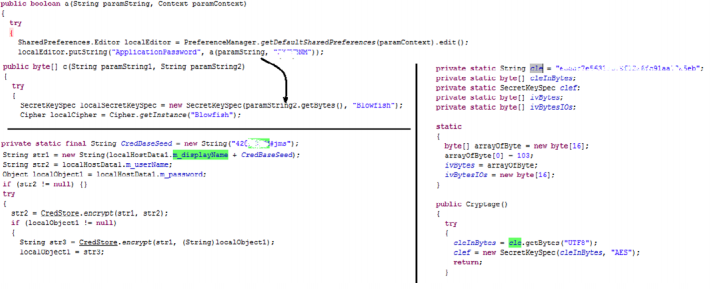
Encryption keys "wired" in the application code
That is, an attacker, having access to critical information that is encrypted, knowing what kind of application it is, can easily decrypt it.
findings
In the course of the study, we examined 20 Android applications that in one way or another interact with the infrastructure of an industrial control system. We studied management solutions for PLC, OPC and MES clients, clients for remote SCADA control. It should be noted that we could not find a single application without flaws and / or vulnerabilities. Most of them have demonstrated problems with authentication and data integrity at the local or network level. The most dangerous consequence of the exploitation of these vulnerabilities is the “compromise” of the operator, who inspires a false understanding of the current state of the technological process.
The full text of the study can be found at the following link:
http://dsec.ru/ipm-research-center/research/scada_and_mobile_phones_the_security
Source: https://habr.com/ru/post/265021/
All Articles