What problems do we face when introducing and operating Microsoft Exchange and how to solve them effectively?
The exchange of e-mails has long and densely entered our lives. And if in a private application, e-mail is supplanted by various kinds of instant messaging and social networking services, then at the corporate level, e-mail stably maintains its position.
In the corporate systems market, one of the leading places is occupied by the Microsoft Exchange solution, which has long grown out of short pants and has stepped beyond the scope of tasks for delivering correspondence.
This could not but affect the complexity of the product and the volume of tasks solved by administrators during the implementation and operation of the solution. We will try to consider some of these tasks.
On September 12, 2012, Microsoft announced the end date of Forefront TMG sales, as well as a schedule for the end of service and technical support for this product. Despite this, pre-authorization and prohibiting direct access to CAS servers is still a good idea. Implementing a reverse proxy, if you do not already have one, will allow you to organize secure access to your web services from the public Internet. In the world of MS Exchange 2013, these are OWA, ActiveSync, Exchange Web Services, and Outlook Anywhere. Pre-authorization allows you to be sure that data from an unauthorized user will not get to the protected system. In addition, a “good” reverse proxy supports two-factor authentication. So, if your network still does not have a reverse proxy, it may be time to think about it. Especially, considering the fact that a reverse proxy can add a different level of additional security to other corporate Web applications, such as SharePoint or Lync, for example.
You can often hear the phrase "Connecting client software to the server occurs over a secure SSL connection." But will it save you from leaking user credentials, will it allow you to inspect the transferred data and be sure that the established SSL connection from the public network is really reliable? As practice shows, the answer to all the questions asked is negative - SSL, by itself, cannot protect you.
The growth in the number of mobile devices and their capabilities, such as smartphones and tablets, contributes to the growth of the use of the latter for solving not only personal, but also corporate tasks by company employees. At the same time, devices still remain personal, and the ability to administer the state of these devices by IT services is extremely difficult, if not to say more, completely absent. In this case, without inspecting the device itself and its interaction with corporate applications, it becomes clearly unsafe.
In addition, do not forget that OWA allows the user to work with the application in the absence of access to the network, which means storing the contents of mail correspondence on a mobile device. This is one of the security risks.
')
New architectural solutions (consolidation of the namespace, failure to monitor the state in CAS, etc.), used by developers in MS Exchange 2013, made it possible to use the information available at the network level to decide on the distribution of users across CAS servers without the need to analyze data of the application itself. However, this solution does not guarantee the optimal choice of both the CAS itself, servicing the user, and the mailbox server, which, in turn, will be accessed by the CAS server. In addition, in MS Exchange there are many service web-services, through which the individual components of the solution interact (OA, OWA, EAS, EWS, AutoDiscovery, etc.). These services can be used to monitor the status of each of the services separately. With the growth of the cluster, on the basis of which the MS Exchange solution is deployed, both within a single data center and in distributed installations, all of the above leads to a high probability of non-optimal distribution of user traffic between the components of the solution. For example, a user whose mailbox is stored in data center A is sent to be serviced by a CAS server located in data center B. In addition, the load balancing technique using the DNS service does not resolve issues of promptly excluding from the namespace that came from building a solution component.
The list of the above questions was formed on the basis of consulting requests from our partners and their customers, which arose both during the planning of the implementation of solutions based on MS Exchange or updating to the new version, and during the operation.
In our answers to these questions, we recommend that partners and customers pay attention to the products of F5 Networks as a comprehensive solution that allows scalability, security and high availability of MS Exchange deployments.
The F5 product line consists of a platform (BIG-IP / VIPRION) and software (TMOS). The platform includes both virtual and hardware implementations managed by a single modular software. The software includes all possible modules, the use of which is governed by the installed license.
Among the modules of functions available in the product line, in this case it should be noted:
• Local Traffic Manager (LTM) —a highly accessible and productive load balancer providing flexible distribution algorithms and methods.
• Termination of HTTPS connections reduces the load on the computing resources of CAS servers and simplifies the management of TLS / SSL certificates in solutions based on MS Exchange 2010, 2013, as well as the following releases.
• Access Policy Manager (APM) allows you to organize preliminary, including two factorial, user authorization, a single point of one-time authorization (SSO), control over devices from which access to Exchange services based on the HTTP protocol is performed.
• The functions of TCP Express and LTM data compression make it possible to take into account the characteristics of the data transfer network through which the application is accessed and to configure the network stack in an optimal way, as well as to reduce the amount of data transmitted over the network.
• GTM and AAM modules can be used in cases of deploying a geographically dispersed MS Exchange cluster. The GTM module is designed to provide fault-tolerant, geographically-based users, access to the application, and the AAM module helps optimize internal, service traffic between geographically separated components of the MS Exchange solution.
There are many scenarios for cooperative implementation of F5 and MS Exchange. We would like to focus your attention on several of the most common schemes.
In this solution, the F5 equipment will be used to control and optimize the traffic between the client and the application access service. Optionally, APM and AFM modules can be used to enhance security. This scenario is depicted in Fig. one.
In this scenario:
1. All client traffic goes through BIG-IP
2. Optional modules licensed and activated on this device allow you to implement the following functionality:
a. BIG-IP Access Policy Manager - pre-authorization of users when accessing Outlook Web App, Outlook Anywhere, ActiveSync and AutoDiscover services. Pre-authorization can only be done in the traditional way using the Active Directory user database or using two-factor authorization mechanisms. In addition, it is possible to audit the user's device from which access is being made, for compliance with corporate standards.
b. BIG-IP Advanced Firewall Manager is a high-performance proxying firewall with connection state monitoring.
3. BIG-IP Local Traffic Manager - distribution and optimization of client traffic, including the traffic of services such as RPC, POP3 and IMAP4, i.e. traffic applications that are not based on the HTTP protocol.

Picture 1
As the load on a solution grows, several ways of its development are possible. One of them is the distribution of functional load between several devices. This scenario can also be used in the sequential development of functionality. Schematically, this scenario is depicted in Fig. 2 and 3.
In this part of the script, client traffic is processed according to the following algorithm:
1. The traffic of applications based on the HTTP protocol is pre-processed on BIG-IP APM (for details of processing, see the next part of the script).
2. A BIG-IP device with an LTM module distributes and optimizes the HTTP traffic received from a BIG-IP device with an APM module. The traffic of applications that are not based on the HTTP protocol (RPC, POP3, IMAP4, etc.) goes directly to this device.
3. The traffic of clients located in the local computer network of the enterprise also goes directly to the BIG-IP device with the LTM module, where it is distributed and optimized.
4. BIG-IP Local Traffic Manager - distribution and optimization of client traffic, including the traffic of such services as RPC, POP3 and IMAP4, i.e. traffic applications that are not based on the HTTP protocol.
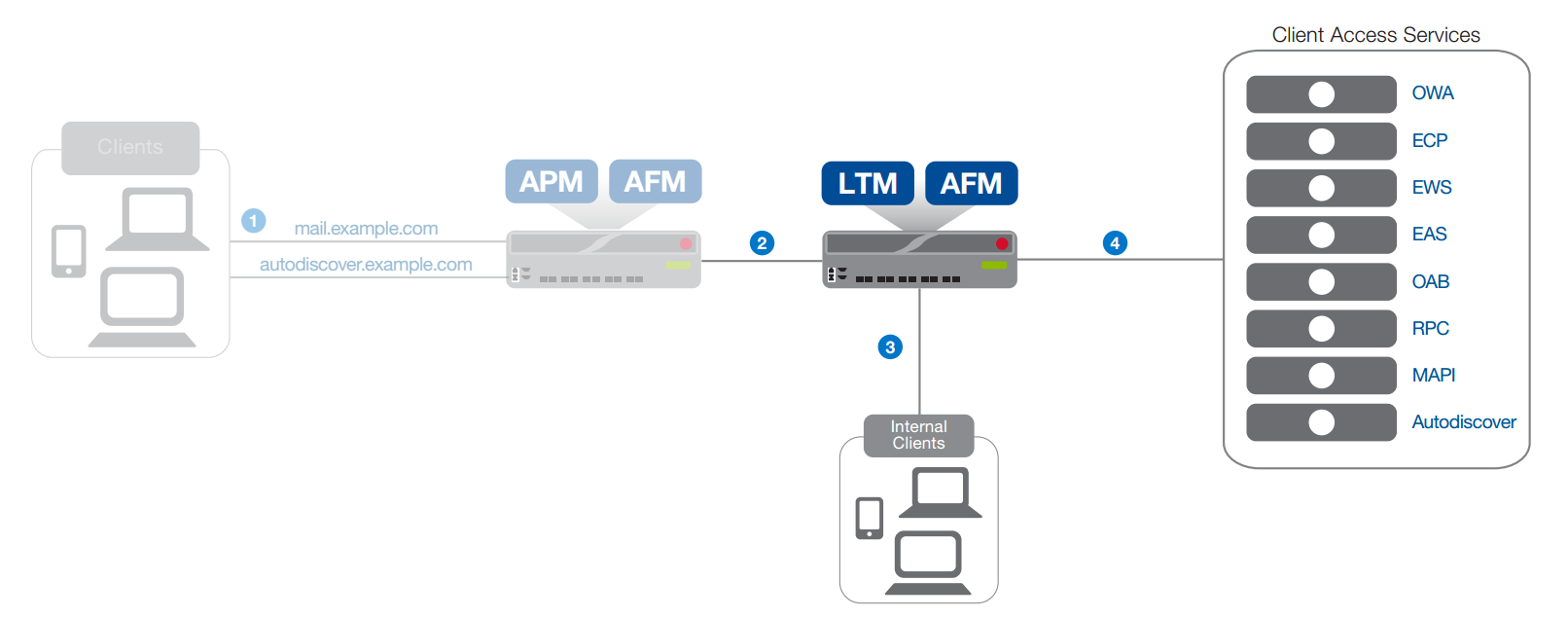
Figure 2
This part of the overall scenario implements the following functionality:
1. A BIG-IP device with an activated APM module pre-authorizes users when accessing Outlook Web App, Outlook Anywhere, ActiveSync, and AutoDiscover services. Pre-authorization can only be done in the traditional way using the Active Directory user database or using two-factor authorization mechanisms.
In addition, it is possible to audit the user's device from which access is being made, for compliance with corporate standards.
2. The legitimate traffic of authorized clients is sent to a BIG-IP device with an LTM module for further distribution and optimization.
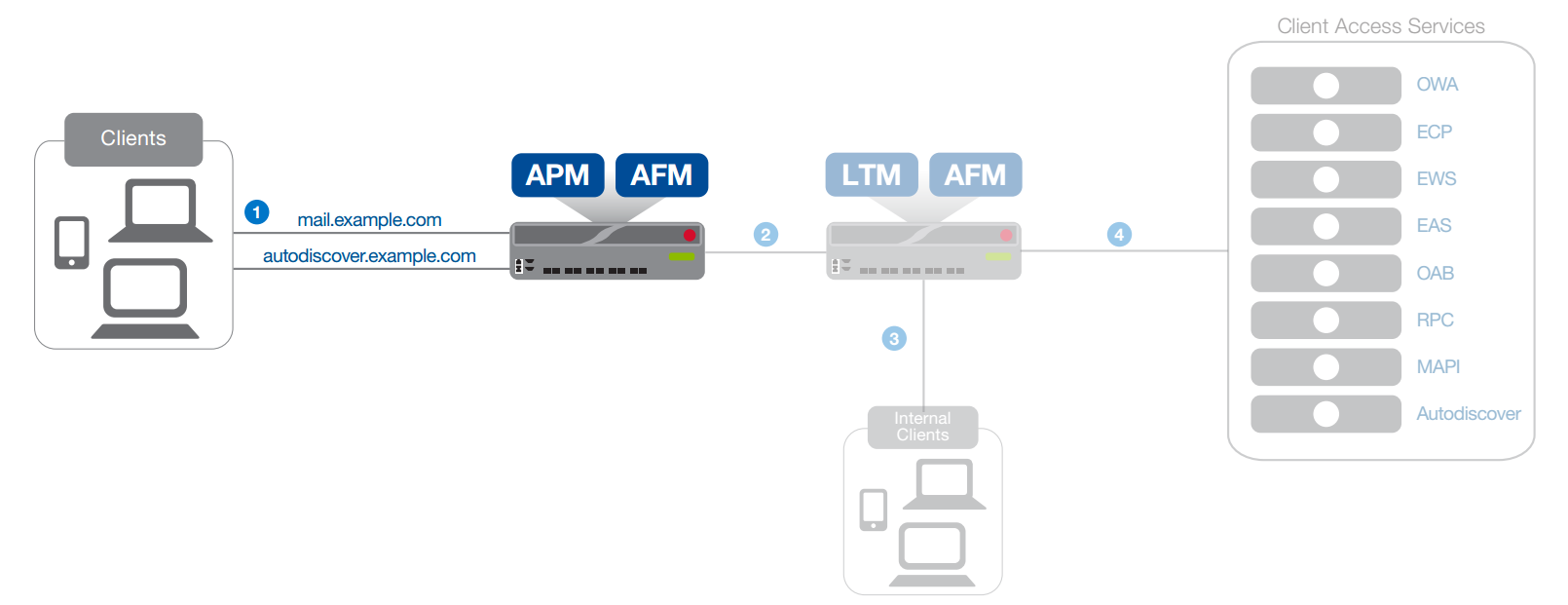
Figure 3
Modern solutions seem simple to the end user, but they pose complex tasks for solution administrators, which can be solved using a lot of scenarios, using products from one or several equipment manufacturers and software developers. The introduction of such solutions, only at first glance, seems simple and understandable, but in fact, faces a lot of implicit and unobvious subtasks that may complicate the subsequent operation and use.
If you are interested in the described integrated solution, and you want to learn more about the technical details of the implementation, or you are interested in getting closer acquainted with the F5 product line, we will be happy to help you with this. Send your questions to f5@comptek.ru
In the corporate systems market, one of the leading places is occupied by the Microsoft Exchange solution, which has long grown out of short pants and has stepped beyond the scope of tasks for delivering correspondence.
This could not but affect the complexity of the product and the volume of tasks solved by administrators during the implementation and operation of the solution. We will try to consider some of these tasks.
Reverse proxy
On September 12, 2012, Microsoft announced the end date of Forefront TMG sales, as well as a schedule for the end of service and technical support for this product. Despite this, pre-authorization and prohibiting direct access to CAS servers is still a good idea. Implementing a reverse proxy, if you do not already have one, will allow you to organize secure access to your web services from the public Internet. In the world of MS Exchange 2013, these are OWA, ActiveSync, Exchange Web Services, and Outlook Anywhere. Pre-authorization allows you to be sure that data from an unauthorized user will not get to the protected system. In addition, a “good” reverse proxy supports two-factor authentication. So, if your network still does not have a reverse proxy, it may be time to think about it. Especially, considering the fact that a reverse proxy can add a different level of additional security to other corporate Web applications, such as SharePoint or Lync, for example.
Secure access to OWA
You can often hear the phrase "Connecting client software to the server occurs over a secure SSL connection." But will it save you from leaking user credentials, will it allow you to inspect the transferred data and be sure that the established SSL connection from the public network is really reliable? As practice shows, the answer to all the questions asked is negative - SSL, by itself, cannot protect you.
The growth in the number of mobile devices and their capabilities, such as smartphones and tablets, contributes to the growth of the use of the latter for solving not only personal, but also corporate tasks by company employees. At the same time, devices still remain personal, and the ability to administer the state of these devices by IT services is extremely difficult, if not to say more, completely absent. In this case, without inspecting the device itself and its interaction with corporate applications, it becomes clearly unsafe.
In addition, do not forget that OWA allows the user to work with the application in the absence of access to the network, which means storing the contents of mail correspondence on a mobile device. This is one of the security risks.
')
Traffic distribution
New architectural solutions (consolidation of the namespace, failure to monitor the state in CAS, etc.), used by developers in MS Exchange 2013, made it possible to use the information available at the network level to decide on the distribution of users across CAS servers without the need to analyze data of the application itself. However, this solution does not guarantee the optimal choice of both the CAS itself, servicing the user, and the mailbox server, which, in turn, will be accessed by the CAS server. In addition, in MS Exchange there are many service web-services, through which the individual components of the solution interact (OA, OWA, EAS, EWS, AutoDiscovery, etc.). These services can be used to monitor the status of each of the services separately. With the growth of the cluster, on the basis of which the MS Exchange solution is deployed, both within a single data center and in distributed installations, all of the above leads to a high probability of non-optimal distribution of user traffic between the components of the solution. For example, a user whose mailbox is stored in data center A is sent to be serviced by a CAS server located in data center B. In addition, the load balancing technique using the DNS service does not resolve issues of promptly excluding from the namespace that came from building a solution component.
F5 Network solutions and their integration with MS Exchange solution
The list of the above questions was formed on the basis of consulting requests from our partners and their customers, which arose both during the planning of the implementation of solutions based on MS Exchange or updating to the new version, and during the operation.
In our answers to these questions, we recommend that partners and customers pay attention to the products of F5 Networks as a comprehensive solution that allows scalability, security and high availability of MS Exchange deployments.
The F5 product line consists of a platform (BIG-IP / VIPRION) and software (TMOS). The platform includes both virtual and hardware implementations managed by a single modular software. The software includes all possible modules, the use of which is governed by the installed license.
Among the modules of functions available in the product line, in this case it should be noted:
• Local Traffic Manager (LTM) —a highly accessible and productive load balancer providing flexible distribution algorithms and methods.
• Termination of HTTPS connections reduces the load on the computing resources of CAS servers and simplifies the management of TLS / SSL certificates in solutions based on MS Exchange 2010, 2013, as well as the following releases.
• Access Policy Manager (APM) allows you to organize preliminary, including two factorial, user authorization, a single point of one-time authorization (SSO), control over devices from which access to Exchange services based on the HTTP protocol is performed.
• The functions of TCP Express and LTM data compression make it possible to take into account the characteristics of the data transfer network through which the application is accessed and to configure the network stack in an optimal way, as well as to reduce the amount of data transmitted over the network.
• GTM and AAM modules can be used in cases of deploying a geographically dispersed MS Exchange cluster. The GTM module is designed to provide fault-tolerant, geographically-based users, access to the application, and the AAM module helps optimize internal, service traffic between geographically separated components of the MS Exchange solution.
There are many scenarios for cooperative implementation of F5 and MS Exchange. We would like to focus your attention on several of the most common schemes.
BIG-IP LTM - balancing and optimizing CAS services traffic
In this solution, the F5 equipment will be used to control and optimize the traffic between the client and the application access service. Optionally, APM and AFM modules can be used to enhance security. This scenario is depicted in Fig. one.
In this scenario:
1. All client traffic goes through BIG-IP
2. Optional modules licensed and activated on this device allow you to implement the following functionality:
a. BIG-IP Access Policy Manager - pre-authorization of users when accessing Outlook Web App, Outlook Anywhere, ActiveSync and AutoDiscover services. Pre-authorization can only be done in the traditional way using the Active Directory user database or using two-factor authorization mechanisms. In addition, it is possible to audit the user's device from which access is being made, for compliance with corporate standards.
b. BIG-IP Advanced Firewall Manager is a high-performance proxying firewall with connection state monitoring.
3. BIG-IP Local Traffic Manager - distribution and optimization of client traffic, including the traffic of services such as RPC, POP3 and IMAP4, i.e. traffic applications that are not based on the HTTP protocol.

Picture 1
Scenario with distribution of functional load across multiple devices
As the load on a solution grows, several ways of its development are possible. One of them is the distribution of functional load between several devices. This scenario can also be used in the sequential development of functionality. Schematically, this scenario is depicted in Fig. 2 and 3.
BIG-IP device with LTM module distributes HTTP traffic access to client services after preliminary processing by BIG-IP device with activated APM module
In this part of the script, client traffic is processed according to the following algorithm:
1. The traffic of applications based on the HTTP protocol is pre-processed on BIG-IP APM (for details of processing, see the next part of the script).
2. A BIG-IP device with an LTM module distributes and optimizes the HTTP traffic received from a BIG-IP device with an APM module. The traffic of applications that are not based on the HTTP protocol (RPC, POP3, IMAP4, etc.) goes directly to this device.
3. The traffic of clients located in the local computer network of the enterprise also goes directly to the BIG-IP device with the LTM module, where it is distributed and optimized.
4. BIG-IP Local Traffic Manager - distribution and optimization of client traffic, including the traffic of such services as RPC, POP3 and IMAP4, i.e. traffic applications that are not based on the HTTP protocol.

Figure 2
BIG-IP device with activated APM module provides secure remote access to services.
This part of the overall scenario implements the following functionality:
1. A BIG-IP device with an activated APM module pre-authorizes users when accessing Outlook Web App, Outlook Anywhere, ActiveSync, and AutoDiscover services. Pre-authorization can only be done in the traditional way using the Active Directory user database or using two-factor authorization mechanisms.
In addition, it is possible to audit the user's device from which access is being made, for compliance with corporate standards.
2. The legitimate traffic of authorized clients is sent to a BIG-IP device with an LTM module for further distribution and optimization.

Figure 3
Epilogue
Modern solutions seem simple to the end user, but they pose complex tasks for solution administrators, which can be solved using a lot of scenarios, using products from one or several equipment manufacturers and software developers. The introduction of such solutions, only at first glance, seems simple and understandable, but in fact, faces a lot of implicit and unobvious subtasks that may complicate the subsequent operation and use.
If you are interested in the described integrated solution, and you want to learn more about the technical details of the implementation, or you are interested in getting closer acquainted with the F5 product line, we will be happy to help you with this. Send your questions to f5@comptek.ru
Source: https://habr.com/ru/post/264921/
All Articles