Cyber group Hacking Team specialized in compromising Apple iDevice without jailbreak
FireEye reported that the Hacking Team cyber group used the Masque vulnerability in iOS to compromise iDevice without jailbreak. To do this, fake applications were created that mimic all sorts of legitimate analogues for social services, including WhatsApp, Twitter, Facebook, Facebook Messenger, WeChat, Google Chrome, Viber, Blackberry Messenger, Skype, Telegram, VK. The applications contained the same original Bundle ID, which allowed them to access all the data of the already installed legitimate application.

The original Masque vulnerability (CVE-2014-4493) was closed by Apple with iOS 8.1.3 released earlier this year. With the release of iOS 8.4 , several other vulnerabilities are similar to Masque, which allowed applications with an existing Bundle ID to access data from an installed application.
')
Fake counterparts of the above legitimate applications have specialized in the theft of various confidential user information.
To create a fake application, a legitimate one was involved in which a special malicious content was introduced - a dynamic library (dylib) called _PkgSign . In order to force iOS to execute the code of this library, the command LC_LOAD_DYLIB was introduced into the executable file of the application (Mach-O).
The malicious dynamic library specializes in interception of a large number of various functions, due to which it is achieved to obtain confidential user data. Thus, an application that operates on user data is no longer legitimate, although it is imperceptible to the user, since it is apparently no different from normal.
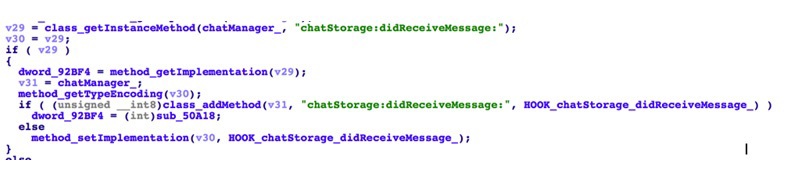
Fig. One of the hooks installed by the malware library (FireEye data).
Installing a fake application into the system using the Masque vulnerability is one of the few, if not the only, way to compromise iOS without a jailbreak. Apple has previously taken the necessary steps to close its associated vulnerabilities (CVE-2014-4493, CVE-2015-3722, CVE-2015-3725).

The original Masque vulnerability (CVE-2014-4493) was closed by Apple with iOS 8.1.3 released earlier this year. With the release of iOS 8.4 , several other vulnerabilities are similar to Masque, which allowed applications with an existing Bundle ID to access data from an installed application.
')
Fake counterparts of the above legitimate applications have specialized in the theft of various confidential user information.
- Voice recordings in Skype, Webchat, etc.
- Text messages of various instant messengers, including Skype, WhatsApp, Facebook messenger.
- The history of visited web resources for Google Chrome web browser.
- Phone calls.
- The contents of SMS and iMessage text messages.
- GPS coordinates.
- Contact Information.
- A photo.
To create a fake application, a legitimate one was involved in which a special malicious content was introduced - a dynamic library (dylib) called _PkgSign . In order to force iOS to execute the code of this library, the command LC_LOAD_DYLIB was introduced into the executable file of the application (Mach-O).
The malicious dynamic library specializes in interception of a large number of various functions, due to which it is achieved to obtain confidential user data. Thus, an application that operates on user data is no longer legitimate, although it is imperceptible to the user, since it is apparently no different from normal.

Fig. One of the hooks installed by the malware library (FireEye data).
Installing a fake application into the system using the Masque vulnerability is one of the few, if not the only, way to compromise iOS without a jailbreak. Apple has previously taken the necessary steps to close its associated vulnerabilities (CVE-2014-4493, CVE-2015-3722, CVE-2015-3725).
Source: https://habr.com/ru/post/264453/
All Articles