Glyuching, attacks on third-party channels and hacker projects on Kickstarter (continued)
Continuation of the list of hacker projects on Kickstarter, found by me during the execution of the “homework” for the course on bringing the project to Kickstarter . Start here .
 ChipWhisperer is the first open source toolkit ( GPL licenced ) for analyzing hardware security, including analyzing attacks from third-party channels and glitching.
ChipWhisperer is the first open source toolkit ( GPL licenced ) for analyzing hardware security, including analyzing attacks from third-party channels and glitching.
The closest commercial analogue of such equipment costs $ 30k - $ 400k, with closed source, which complicates research and development. The project ranked second at the Hackaday Prize 2014
')
Fees - $ 88,535 ($ 50,000)
Start of the project - February 27, 2015
Kickstarter project page


System design

Iron design
Target IO Interface

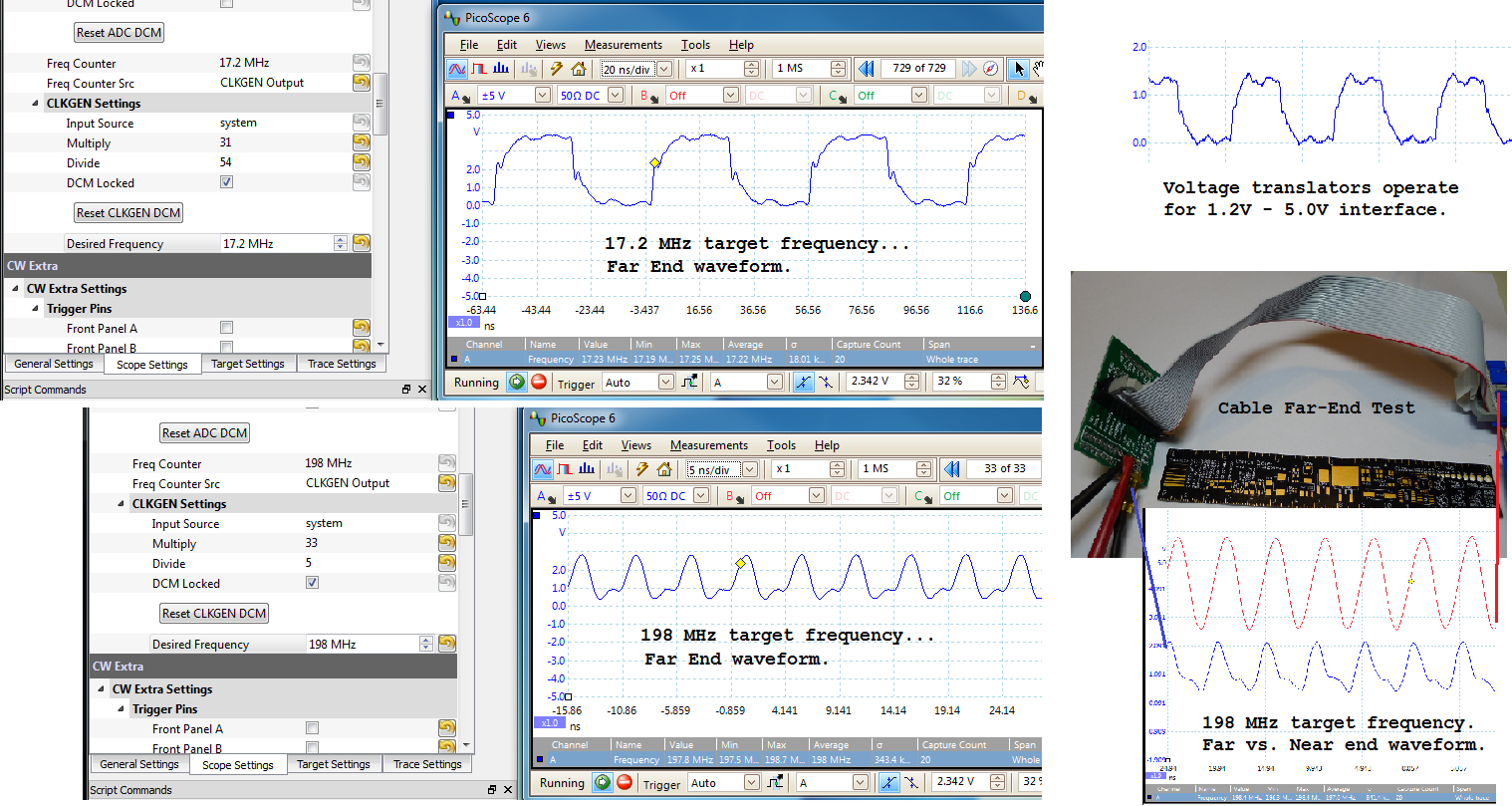
Capturing traces from the ChipWhisperer-Lite
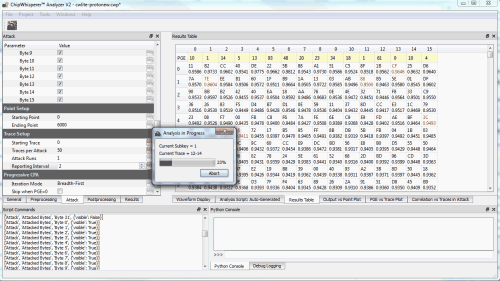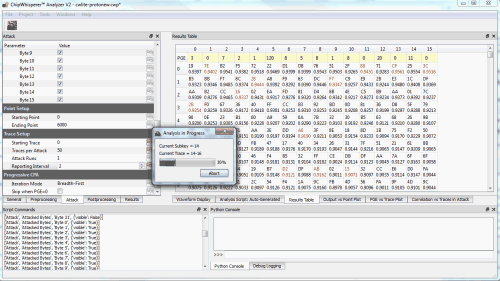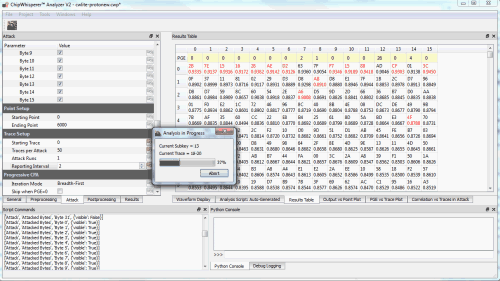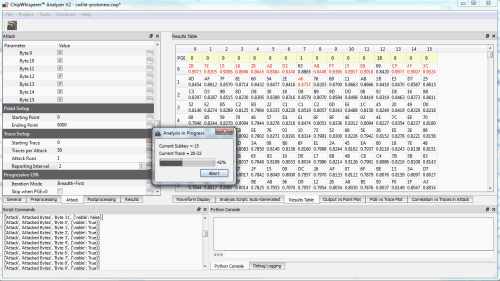
Cracking the encryption key
Video - homemade
Chips:
Developers' position regarding flexible goals:
Detailed description and open documentation
Two minute platform overview
Third-party attack - attacks aimed at vulnerabilities in the practical implementation of a cryptosystem
Tutorial:
CHES2013 Tutorial - Low Cost Side Channel Analysis (ChipWhisperer)
 Flash-fig-get it . USB Key differs from other Crypteks similar similar products by the presence of mechanical protection: in fact, the drive itself is part of a combination lock, so in order to gain access to information, you first need to bypass mechanical protection. At the same time, concerns about the security of information are not limited - the contents of the drive are hardware encrypted using the AES algorithm (256-bit hardware encryption).
Flash-fig-get it . USB Key differs from other Crypteks similar similar products by the presence of mechanical protection: in fact, the drive itself is part of a combination lock, so in order to gain access to information, you first need to bypass mechanical protection. At the same time, concerns about the security of information are not limited - the contents of the drive are hardware encrypted using the AES algorithm (256-bit hardware encryption).
Fees - $ 196,404 ($ 12,000)
Start of the project - November 23, 2011
Project site - crypteks.com ( oops , there are a lot of hieroglyphs, see the domain has already gone to another owner)
Kickstarter project page
Video - Studio
The Crypteks USB project is an “old man” and the very first on Kickstarter in the field of information security.
But then the problems started.
A 2013 article describing what's bad: Buyer Beware: Crypteks' USB Kickstarter Campaign Highlights the Perils of Crowd Funding
It happens.
 iGuardian , also known as Shield , is a network security system for home use that protects computers, tablets, smartphones and other Internet devices from malware, exploits and other harm. With lifetime updates.
iGuardian , also known as Shield , is a network security system for home use that protects computers, tablets, smartphones and other Internet devices from malware, exploits and other harm. With lifetime updates.
Modern digital or “smart” home contains many unprotected devices that very easily allow criminals to enter the home network, steal personal information and gain access to banking and other accounts. iGuardian is a small device equipped with two 1.0 GHz MIPS6 processors, with 1GB DDR3 RAM, and 64 MB of flash memory.
 The device is based on Linux and is designed to block cyber attacks, filter malware and unwanted content. It is automatically installed within 5 minutes and does not require any configuration and technological knowledge. iGuardian only protects against known attacks by comparing network traffic with patterns registered in the database of threats. In this case, iGuardian uses in its work Snort , as a linear intrusion prevention system.
The device is based on Linux and is designed to block cyber attacks, filter malware and unwanted content. It is automatically installed within 5 minutes and does not require any configuration and technological knowledge. iGuardian only protects against known attacks by comparing network traffic with patterns registered in the database of threats. In this case, iGuardian uses in its work Snort , as a linear intrusion prevention system.
Fees - $ 174,382 ($ 125,000)
Start of the project - August 7, 2014
Project site - itusnetworks.com
Kickstarter project page
Chips :
Video - Studio
 MyIDkey USB flash drive with biometric
MyIDkey USB flash drive with biometric
The data protection has a fingerprint scanner and recognizes the wearer's voice. The screen displays the necessary information on the voice command. If necessary, you can delete all the contents by clicking on the button located on the flash drive. The main task of this device is to store passwords and keys, but in principle there are no restrictions. You can connect to other devices via USB or Bluetooth.
The most interesting feature is erasing information with one button. Encryption - AES 256. It is also possible to recover lost data from a backup made in advance and stored on a PC or online cloud.

The project in a day attracted 1,281 backers, who invested $ 132,800 in the project.
Fees - $ 473,333 ($ 150,000)
Start of the project - February 20, 2013
Kickstarter project page
Video - Studio
Chips :

Fees - $ 46,420 ($ 25,000)
Start of the project - December 2013
Project page on Indiegogo
The idea to audit TrueCrypt and at the same time put in order its code, license and build procedure on all platforms arose in the wake of the story with the total listening of the Internet by the US National Security Agency, which became known thanks to Edward Snowden. Publication of information about the activities of the NSA has caused many concerns about the presence of special services bookmarks in open cryptographic products.
A group of cryptographers who were involved in auditing the source code of the disk encryption program TrueCrypt completed its work in April 2015. The full 21-page report is published on the Open Crypto Audit Project website.
During the code audit, 11 errors were found - among them not one critical, four errors of moderate degree of danger, four - low and three in the category “informational” - that is, practically insignificant from the point of view of security. In a 32-page report ( PDF ), for clarity, the found bugs are summarized in a chart based on risk and ease of use.
Chips :
Original description of awards for bakers
The peculiarity of the project is that the result of the project is “slightly ephemeral”; it is not a product, or even a training course, but a report.
Articles and discussions on Habré one , two
Computerra article: TrueCrypt: audit passed, intrigue preserved
Article in Xakep.ru: TrueCrypt audit is completed: everything is fine
Strange aftermath: The TrueCrypt site announces the closure of the project and suggests switching to BitLocker
Anonymous, protected from any surveillance bitcoin wallet. The first plan was to release a lightweight extension for the Firefox and Chrome browsers.
Behind the development of Dark Wallet are 26-year-old American programmer Cody Wilson (Cody Wilson), who received
widely known as the creator of the world's first gun, fully printed on a 3D printer , as well as the British programmer Amir Taaki. The team of several Internet activists and developers headed by them calls itself unSystem.
The basic principle of operation of the Dark Wallet is based on the so-called CoinJoin bitcoin “laundering” mechanism. With its help, any transaction - whether it be buying socks or drugs on bitcoins - is protected from tracking, mixing with the transactions of other wallet users.
The latest version of Dark Wallet contains both an independent peer bitcoin exchange. Here, users can buy and sell bitcoins, while the role of arbiters (third party) is performed by the development team.
Fees - $ 52,075 ($ 50,000)
Start of the project - autumn 2013
Project page on Indiegogo
Accepted contributions both in dollars and in Bitcoin

A laptop developed in accordance with the principles of Open Hardware.

hackaday.com/2014/01/12/bunnies-open-source-laptop-is-ready-for-production
www.crowdsupply.com/sutajio-kosagi/novena
The story began in 2012.

Andrew Huang, a well-known free hardware activist who recently won the Pioneer Award 2012, presented his new project Novena, which began the development of a laptop developed in accordance with the principles of Open Hardware. The motherboard used in the laptop, as well as the battery management board, will be delivered with full provision of the circuits and specifications distributed under free licenses. Taking advantage of the published open schemes, any manufacturer, if desired, can start production of the components prepared by the project and take part in their refinement and development.
Documentation and software development guide for Novena (including software already created) will be open. So, it will be possible to assemble from the components not only a laptop (with any size of the display, housing and a set of components), but also a router, and everything else that you want.

Novena is based on the 1.2 gigahertz quad-core ARM processor and Xilinx FPGA . But a special Linux distribution for this laptop.
Start of the project - April 2014
Fees - $ 783.055 ($ 250,000)
Crowdsupply project page
Video
Chips:

Everyone probably has acquaintances who are conducting experiments with cold nuclear fusion in the garage.
Perhaps they want to bring their project to the crowdfunding platform, or maybe they (like proud hedgehogs) should be kicked for this.
Share briefly the essence of the project (in the comments or on the email alexey.stacenko (pack) gmail.com), for our part, being biased and inadequate, we will give two invites for the Kickstarter campaign creation course . One invite to themost beautiful girl to the author of the project, and the second to the one who “passed” him. (priority for projects in the field of information security and OpenSource)
Already one project gave up on its own.
ChipWhisperer-Lite: A New Era of Hardware Security Research
ChipWhisperer laughs at your AES-256 implementation. But he laughs with you, not at you.
 ChipWhisperer is the first open source toolkit ( GPL licenced ) for analyzing hardware security, including analyzing attacks from third-party channels and glitching.
ChipWhisperer is the first open source toolkit ( GPL licenced ) for analyzing hardware security, including analyzing attacks from third-party channels and glitching.The closest commercial analogue of such equipment costs $ 30k - $ 400k, with closed source, which complicates research and development. The project ranked second at the Hackaday Prize 2014
')
Fees - $ 88,535 ($ 50,000)
Start of the project - February 27, 2015
Kickstarter project page


System design

Iron design

Target IO Interface

Capturing traces from the ChipWhisperer-Lite

Cracking the encryption key
Video - homemade
Chips:
mass media
Bang
And I did not find a list of media. The see team is working with the hacker community at conferences and events . In Russian, too, there is no material.
There is a podcast interview with # 239 creator - An Interview with Colin O'Flynn - Aspirated Adamantine Attacks
And I did not find a list of media. The see team is working with the hacker community at conferences and events . In Russian, too, there is no material.
There is a podcast interview with # 239 creator - An Interview with Colin O'Flynn - Aspirated Adamantine Attacks
attracted cool actors


visualization of awards

burned and broken
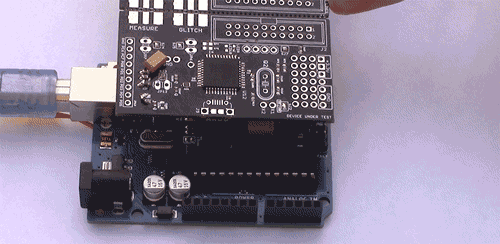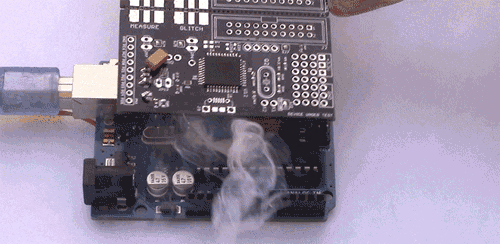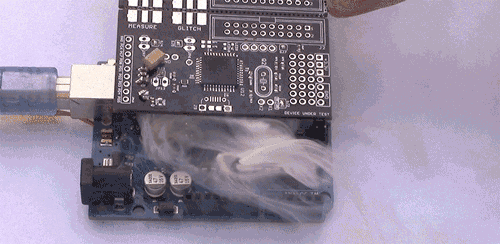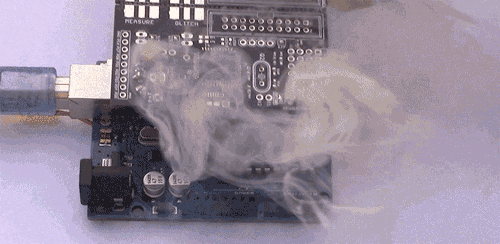
Examples of vulnerabilities are:


Side-Channel Analysis Example
This is a digital channel. We can use cryptographic implementations of otherwise secure algorithms (such as AES-128 or AES-256).
For more details of the CPA attack ,
along with a nice example of step-by-step breaking of the AES using
Python from the ChipWhisperer tutorial list. I need to tell you my encryption / decryption
If you want to monitor the output of the system.
This can be done with the device for example. For example see the AES-128 implementation in 120 seconds .
For more details of the CPA attack ,
along with a nice example of step-by-step breaking of the AES using
Python from the ChipWhisperer tutorial list. I need to tell you my encryption / decryption
If you want to monitor the output of the system.
This can be done with the device for example. For example see the AES-128 implementation in 120 seconds .
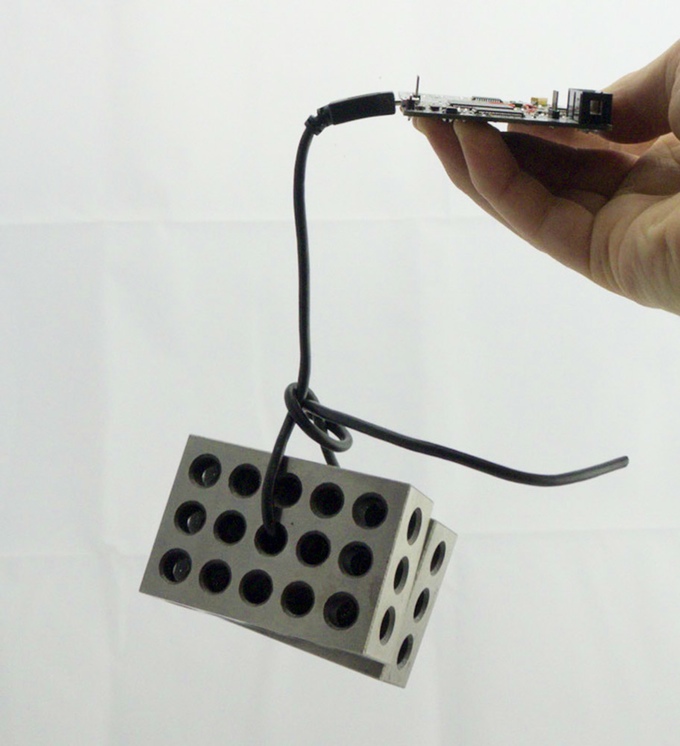
Glitching example
Glitching is another devious attack on embedded systems. In this case, it is possible to take advantage of the code. So consider we have this code:
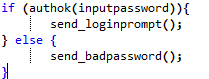
It is possible to follow the instructions. You can glitch a raspberry pi
This attack works with the ChipWhisperer-Lite too (we tested it already!).

It is possible to follow the instructions. You can glitch a raspberry pi
This attack works with the ChipWhisperer-Lite too (we tested it already!).
Developers' position regarding flexible goals:
“No stretch goals. There are no goals, none of that nonsense. If we get it, it’s 10x the amount of work it’s possible to make.
Detailed description and open documentation
Two minute platform overview
Third-party attack - attacks aimed at vulnerabilities in the practical implementation of a cryptosystem
Tutorial:
CHES2013 Tutorial - Low Cost Side Channel Analysis (ChipWhisperer)
Crypteks USB ™ - Inspired Design meets Ultra Security
 Flash-fig-get it . USB Key differs from other Crypteks similar similar products by the presence of mechanical protection: in fact, the drive itself is part of a combination lock, so in order to gain access to information, you first need to bypass mechanical protection. At the same time, concerns about the security of information are not limited - the contents of the drive are hardware encrypted using the AES algorithm (256-bit hardware encryption).
Flash-fig-get it . USB Key differs from other Crypteks similar similar products by the presence of mechanical protection: in fact, the drive itself is part of a combination lock, so in order to gain access to information, you first need to bypass mechanical protection. At the same time, concerns about the security of information are not limited - the contents of the drive are hardware encrypted using the AES algorithm (256-bit hardware encryption).Fees - $ 196,404 ($ 12,000)
Start of the project - November 23, 2011
Project site - crypteks.com ( oops , there are a lot of hieroglyphs, see the domain has already gone to another owner)
Kickstarter project page
Video - Studio
The Crypteks USB project is an “old man” and the very first on Kickstarter in the field of information security.
But then the problems started.
A 2013 article describing what's bad: Buyer Beware: Crypteks' USB Kickstarter Campaign Highlights the Perils of Crowd Funding
It happens.
Shield - Home Internet Security Appliance
 iGuardian , also known as Shield , is a network security system for home use that protects computers, tablets, smartphones and other Internet devices from malware, exploits and other harm. With lifetime updates.
iGuardian , also known as Shield , is a network security system for home use that protects computers, tablets, smartphones and other Internet devices from malware, exploits and other harm. With lifetime updates.Modern digital or “smart” home contains many unprotected devices that very easily allow criminals to enter the home network, steal personal information and gain access to banking and other accounts. iGuardian is a small device equipped with two 1.0 GHz MIPS6 processors, with 1GB DDR3 RAM, and 64 MB of flash memory.
 The device is based on Linux and is designed to block cyber attacks, filter malware and unwanted content. It is automatically installed within 5 minutes and does not require any configuration and technological knowledge. iGuardian only protects against known attacks by comparing network traffic with patterns registered in the database of threats. In this case, iGuardian uses in its work Snort , as a linear intrusion prevention system.
The device is based on Linux and is designed to block cyber attacks, filter malware and unwanted content. It is automatically installed within 5 minutes and does not require any configuration and technological knowledge. iGuardian only protects against known attacks by comparing network traffic with patterns registered in the database of threats. In this case, iGuardian uses in its work Snort , as a linear intrusion prevention system.Fees - $ 174,382 ($ 125,000)
Start of the project - August 7, 2014
Project site - itusnetworks.com
Kickstarter project page
Chips :
great job with the press

visualization of flexible targets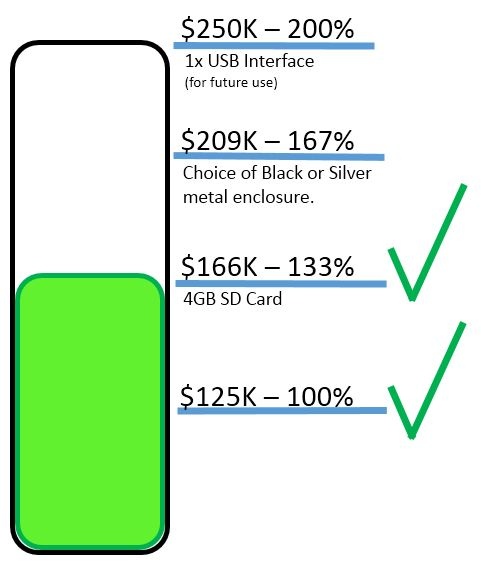

Video - Studio
myIDkey: Passwords at the tip of your finger
 MyIDkey USB flash drive with biometric
MyIDkey USB flash drive with biometric The data protection has a fingerprint scanner and recognizes the wearer's voice. The screen displays the necessary information on the voice command. If necessary, you can delete all the contents by clicking on the button located on the flash drive. The main task of this device is to store passwords and keys, but in principle there are no restrictions. You can connect to other devices via USB or Bluetooth.
The most interesting feature is erasing information with one button. Encryption - AES 256. It is also possible to recover lost data from a backup made in advance and stored on a PC or online cloud.

The project in a day attracted 1,281 backers, who invested $ 132,800 in the project.
Fees - $ 473,333 ($ 150,000)
Start of the project - February 20, 2013
Kickstarter project page
Video - Studio
Chips :
press

visualization of awards

flexible targets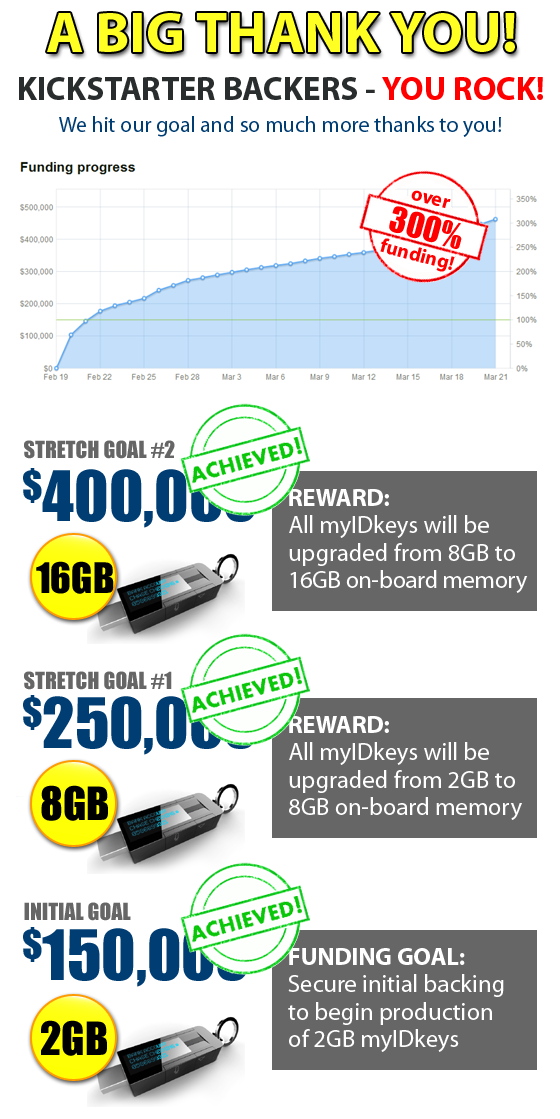

More crowdfunding projects, but not with Kickstarter
The TrueCrypt Audit (Indiegogo)

Fees - $ 46,420 ($ 25,000)
Start of the project - December 2013
Project page on Indiegogo
The idea to audit TrueCrypt and at the same time put in order its code, license and build procedure on all platforms arose in the wake of the story with the total listening of the Internet by the US National Security Agency, which became known thanks to Edward Snowden. Publication of information about the activities of the NSA has caused many concerns about the presence of special services bookmarks in open cryptographic products.
A group of cryptographers who were involved in auditing the source code of the disk encryption program TrueCrypt completed its work in April 2015. The full 21-page report is published on the Open Crypto Audit Project website.

During the code audit, 11 errors were found - among them not one critical, four errors of moderate degree of danger, four - low and three in the category “informational” - that is, practically insignificant from the point of view of security. In a 32-page report ( PDF ), for clarity, the found bugs are summarized in a chart based on risk and ease of use.
Chips :
Original description of awards for bakers

The peculiarity of the project is that the result of the project is “slightly ephemeral”; it is not a product, or even a training course, but a report.
Articles and discussions on Habré one , two
Computerra article: TrueCrypt: audit passed, intrigue preserved
Article in Xakep.ru: TrueCrypt audit is completed: everything is fine
Strange aftermath: The TrueCrypt site announces the closure of the project and suggests switching to BitLocker
Bitcoin Dark Wallet (Indiegogo)
Anonymous, protected from any surveillance bitcoin wallet. The first plan was to release a lightweight extension for the Firefox and Chrome browsers.
Behind the development of Dark Wallet are 26-year-old American programmer Cody Wilson (Cody Wilson), who received
widely known as the creator of the world's first gun, fully printed on a 3D printer , as well as the British programmer Amir Taaki. The team of several Internet activists and developers headed by them calls itself unSystem.
The basic principle of operation of the Dark Wallet is based on the so-called CoinJoin bitcoin “laundering” mechanism. With its help, any transaction - whether it be buying socks or drugs on bitcoins - is protected from tracking, mixing with the transactions of other wallet users.
“I want to have a completely anonymous means for Bitcoins to pay for any goods on the black market. These may be over-the-counter drugs, soft or hard drugs, and weapons. Yes, bad things sometimes happen on the shadow internet. Freedom is a dangerous thing. Dark Wallet - a real nightmare for law enforcement. They believe that going into the shadow is a big problem. But with bitcoins this care cannot be avoided. ” Cody Wilson, developer of Dark Wallet

The latest version of Dark Wallet contains both an independent peer bitcoin exchange. Here, users can buy and sell bitcoins, while the role of arbiters (third party) is performed by the development team.
Fees - $ 52,075 ($ 50,000)
Start of the project - autumn 2013
Project page on Indiegogo
Accepted contributions both in dollars and in Bitcoin

Novena - [BUNNIE] 's Open Source laptop (Crowdsupply)
A laptop developed in accordance with the principles of Open Hardware.

hackaday.com/2014/01/12/bunnies-open-source-laptop-is-ready-for-production
www.crowdsupply.com/sutajio-kosagi/novena
The story began in 2012.

Andrew Huang, a well-known free hardware activist who recently won the Pioneer Award 2012, presented his new project Novena, which began the development of a laptop developed in accordance with the principles of Open Hardware. The motherboard used in the laptop, as well as the battery management board, will be delivered with full provision of the circuits and specifications distributed under free licenses. Taking advantage of the published open schemes, any manufacturer, if desired, can start production of the components prepared by the project and take part in their refinement and development.
Documentation and software development guide for Novena (including software already created) will be open. So, it will be possible to assemble from the components not only a laptop (with any size of the display, housing and a set of components), but also a router, and everything else that you want.

Novena is based on the 1.2 gigahertz quad-core ARM processor and Xilinx FPGA . But a special Linux distribution for this laptop.
Start of the project - April 2014
Fees - $ 783.055 ($ 250,000)
Crowdsupply project page
Video
Chips:
thoughtful and well-written Stretch Goals
www.crowdsupply.com/kosagi/novena-open-laptop/stretch-goals
You have to get our supporters. We’ve been able to make it easier for you.
Partnering with Jon Nettleton for Open 2D / 3D Graphics Drivers on Novena: + $ 50k ($ 300k total) [COMPLETE AS OF MAY 12!]
We could really build. The hardware blueprints and software source code are available for download. It is buildable from the human-readable source. However, there are some elements of the i.MX6 SoC that lie in it, due to a lack of open source drivers. In particular, the 2D / 3D graphics accelerator in the i.MX6 has closed-source drivers. This is a list of drivers for these components.
This is a piece of jigsaw puzzle game. Here is a short statement from Jon Nettleton himself on the prospect:
Therefore, if we can raise $ 50k, we will don’t need to make it possible. The remainder of that lifted up.
Significantly, since it’s an open source effort, it’s possible to complete the process. Because of this, we’ve added a “Buy Jon a Six Pack ($ 30)” pledge tier (capped at 417 pledges). Jon Nettleton has reached at least 80 cents, regardless of his ability to reach the first stretch goal. The companion campaign costs and financial operator transaction fees.
General-Purpose Breakout Board: + $ 100k ($ 350k total) [COMPLETE AS OF MAY 16!]
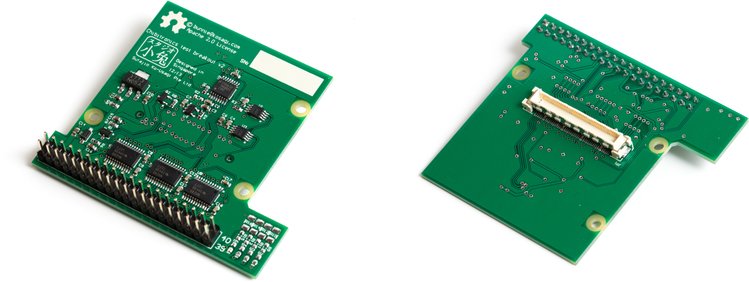
Hey, it's a little bit different. If we can give you an extra $ 50k over the previous stretch goal
The GPBB buffers 16 3.3V or 5V FPGA outputs and 8 FPGA inputs, can be gang-selectable via software. It also provides six 10-bit analog inputs (up to 200ksps sample rate) and two 10bit analog outputs (~ 100ksps max rate), 40-pin male 0.1 ”dual-row header.
The GPBB is a handy for all situations. Because the GPBB is backed by a powerful FPGA, it can be programmed for a wide range of applications. For example, an FPGA output can be configured as a PWM channel. It can be used for all LED strip lighting.
For users who need to go for Linux, go through the linux with the I2C API . You can use your favorite high level language.
Significantly, the GPBB product line. At this very moment, GPBB design is being used to drive mass production of circuit stickers.
ROMulator Breakout Board: + $ 150k ($ 400k total) [COMPLETE AS OF MAY 16!]
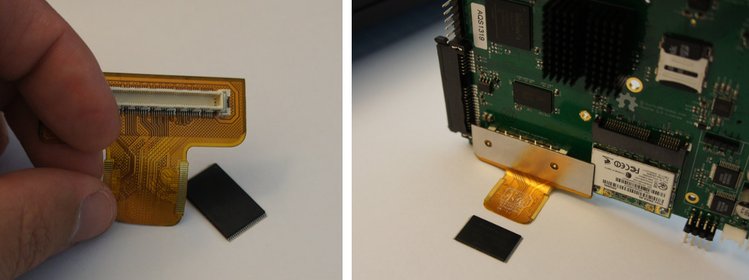
We designed the novena to be a versatile hacking tool. SD card reveals a card knock on it. Novena.
We used Novena as a ROMulator - a FLASH ROM emulator. It can be soldered in between the PCB and the underlying PCB. In this mode, we can use the FPGA built-in flash drive.
Alternately, the FPGA can be used to emulate a ROM device using its local 256 MiB of DDR3 memory. Since it was a DDR3 controller, it can be able to inspect it. This is a number of powerful applications.
If we can raise an additional $ 50k over the previous tier, we'll include a ROMulator Breakout Board (in addition to the General Purpose Breakout Board) with every piece of hardware shipped.
MyriadRF Software Defined Radio: + $ 250k ($ 500k total) or> 200 backers for the desktop / laptop / heirloom version [COMPLETE AS OF MAY 16!]
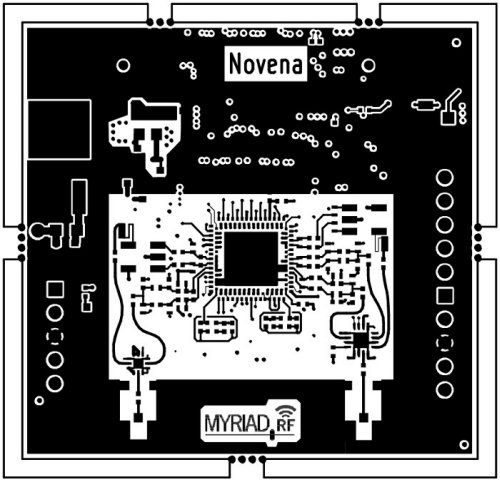
Software! Defined! Radio! We are very excited to offer a custom-made SDR solution for Novena. Their open hardware SDR is used in all major radio bands, including LTE, CDMA, TD-CDMA, W-CDMA, WiMAX, 2G and many more.
MyriadRF has been graciously pulled through a string of novena. If you can get a total of $ 500k or $ 200k back at least for your desktop / laptop / heirloom version, we’ll include your desktop version of the MyriadRF SDR board. Since this is a ticket-item, it’s not a problem.
Signed by the SDR module of the SDR module it is can comfortably hang out of the case, giving easy access to the U.FL RF connectors.
Thanks for your support!
bunnie and xobs
You have to get our supporters. We’ve been able to make it easier for you.
Partnering with Jon Nettleton for Open 2D / 3D Graphics Drivers on Novena: + $ 50k ($ 300k total) [COMPLETE AS OF MAY 12!]
We could really build. The hardware blueprints and software source code are available for download. It is buildable from the human-readable source. However, there are some elements of the i.MX6 SoC that lie in it, due to a lack of open source drivers. In particular, the 2D / 3D graphics accelerator in the i.MX6 has closed-source drivers. This is a list of drivers for these components.
This is a piece of jigsaw puzzle game. Here is a short statement from Jon Nettleton himself on the prospect:
Novena Backers and OSS enthusiasts,
Jon Nettleton (aka jnettlet, linux4kix), as a stretch-goal. Novena platforms will not be a binary userspace driver for 2D / 3D graphics acceleration.
If you’re driving, you can’t get it.
To accomplish this we are requesting an additional $ 10,000 of funding. I would like to give you my credit. If you are interested in a chipset, it can be used. There is no “US“ and “THEM” in this effort. “WE” will bring a desktop platform for the Novena Project.
Therefore, if we can raise $ 50k, we will don’t need to make it possible. The remainder of that lifted up.
Significantly, since it’s an open source effort, it’s possible to complete the process. Because of this, we’ve added a “Buy Jon a Six Pack ($ 30)” pledge tier (capped at 417 pledges). Jon Nettleton has reached at least 80 cents, regardless of his ability to reach the first stretch goal. The companion campaign costs and financial operator transaction fees.
General-Purpose Breakout Board: + $ 100k ($ 350k total) [COMPLETE AS OF MAY 16!]

Hey, it's a little bit different. If we can give you an extra $ 50k over the previous stretch goal
The GPBB buffers 16 3.3V or 5V FPGA outputs and 8 FPGA inputs, can be gang-selectable via software. It also provides six 10-bit analog inputs (up to 200ksps sample rate) and two 10bit analog outputs (~ 100ksps max rate), 40-pin male 0.1 ”dual-row header.
The GPBB is a handy for all situations. Because the GPBB is backed by a powerful FPGA, it can be programmed for a wide range of applications. For example, an FPGA output can be configured as a PWM channel. It can be used for all LED strip lighting.
For users who need to go for Linux, go through the linux with the I2C API . You can use your favorite high level language.
Significantly, the GPBB product line. At this very moment, GPBB design is being used to drive mass production of circuit stickers.
ROMulator Breakout Board: + $ 150k ($ 400k total) [COMPLETE AS OF MAY 16!]

We designed the novena to be a versatile hacking tool. SD card reveals a card knock on it. Novena.
We used Novena as a ROMulator - a FLASH ROM emulator. It can be soldered in between the PCB and the underlying PCB. In this mode, we can use the FPGA built-in flash drive.
Alternately, the FPGA can be used to emulate a ROM device using its local 256 MiB of DDR3 memory. Since it was a DDR3 controller, it can be able to inspect it. This is a number of powerful applications.
If we can raise an additional $ 50k over the previous tier, we'll include a ROMulator Breakout Board (in addition to the General Purpose Breakout Board) with every piece of hardware shipped.
MyriadRF Software Defined Radio: + $ 250k ($ 500k total) or> 200 backers for the desktop / laptop / heirloom version [COMPLETE AS OF MAY 16!]

Software! Defined! Radio! We are very excited to offer a custom-made SDR solution for Novena. Their open hardware SDR is used in all major radio bands, including LTE, CDMA, TD-CDMA, W-CDMA, WiMAX, 2G and many more.
MyriadRF has been graciously pulled through a string of novena. If you can get a total of $ 500k or $ 200k back at least for your desktop / laptop / heirloom version, we’ll include your desktop version of the MyriadRF SDR board. Since this is a ticket-item, it’s not a problem.
Signed by the SDR module of the SDR module it is can comfortably hang out of the case, giving easy access to the U.FL RF connectors.
Thanks for your support!
bunnie and xobs
mass media
WIRED
Mashable
Venturebeat
Tested
Venturebeat
The next web
Boing boing
Laptop Mag
Tecmundo
Backerjack
Adafruit
Makezine
PC World
Geek
IDG CONNECT
liliputing
Linux.com
Techcrunch
The next web
“The project is part of a larger open source hardware movement.”
Mashable
“It’s modified by the user. Anyone who owns one of the individual components. ”
Venturebeat
“The machine is designed to be open, flexible, and powerful.”
Tested
“It's a completely open hardware platform.”
Venturebeat
“It’s like a commercial laptop.”
The next web
“It’s possible that you can think of it.”
Boing boing
“I've put in for one of the laptops. I can't wait. ”
Laptop Mag
“Appealing to hardware hackers, a new build-your-own laptop kit, called Novena,
Tecmundo
“It’s made in the market.”
Backerjack
“This is a compact, modifiable solution for hardware needs.”
Adafruit
“They've worked on many laptop hardware needs to be celebrated.”
Makezine
“The World’s First Open Source Laptop Makes Its Debut.”
PC World
“It’s not a problem.”
Geek
“You could build yourself a laptop.”
IDG CONNECT
“Crowdsourcing Innovation: Andrew“ Bunnie ”Huang.”
liliputing
“Novena is up to mind.”
Linux.com
“Novena is more than just an open hardware laptop; it's designed from the compute platform ”
Techcrunch
“He doesn’t know what he has done.”
The next web
“It is a requirement that there is a need for freedom experiments.”
Competition

Everyone probably has acquaintances who are conducting experiments with cold nuclear fusion in the garage.

Perhaps they want to bring their project to the crowdfunding platform, or maybe they (like proud hedgehogs) should be kicked for this.
Share briefly the essence of the project (in the comments or on the email alexey.stacenko (pack) gmail.com), for our part, being biased and inadequate, we will give two invites for the Kickstarter campaign creation course . One invite to the
Already one project gave up on its own.
heat trap with catalytic afterburner
Direct supply of heat from the combustion of fuel (air) to a room without using heat exchangers (boilers), heat pipes (pipes), heat exchangers (radiators), with air purification (products of combustion) with a catalyst.
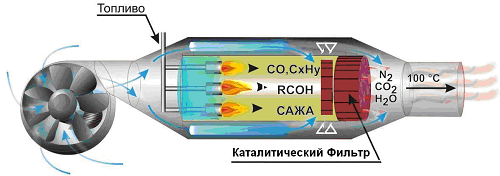

Direct supply of heat from the combustion of fuel (air) to a room without using heat exchangers (boilers), heat pipes (pipes), heat exchangers (radiators), with air purification (products of combustion) with a catalyst.

Source: https://habr.com/ru/post/264337/
All Articles