Mobile phones for / against special services
- Hello, this is a call from the FSB.
- I know.
- From where?
- You got me on the switched off mobile phone.

What is the most secure phone?
These are the phones the last 2 weeks have become residents of my backpack. Knowledgeable people will immediately understand what these two pipes are to the left.
The more I dug, the sadder I got. Every (second?) Person on Earth carries a bug with him and for just so gives all his communication on a silver platter to third parties. And nobody cares about it except professional paranoids.
')
Given that there are more telephones on the planet than all the other devices combined (bent a little, but almost so), materials are catastrophically low. For example, I still have not really found the descriptions of those operator commands that secretly turn on the phone to wiretap. Or how do operators and organs fight (and are they fighting) with scramblers?
Why there are no hacker / open-source phone projects? Vaughn, the laptop was washed down , than the mobile phone more difficult?
(Although there are some discussions here ).
Let's think for a second, what would a hacker phone look like?
Whatever functions he had, what he would have been stuffed with iron and software.
In the meantime, let's see what is on the market, what piece decisions have already been implemented, what can they spy on.
Let me
The weight is good. The severity is secure.

Yes, this is the phone
How is this phone connected with IB?
First, he got me by the method of "soft" social engineering. But I can not write about it yet.
Secondly, it will now be easier for me to shoot video and photos of spy devices.

(to the article about detectors of bugs, field indicators and legal emulators of bugs)
For example, the acoustic safe is squealing like this:
For reference, Dexp Snatch costs 7,500 rubles (although there are models with a large battery for both 4,500 and 14,000 rubles in the Dexp line), and an acoustic safe costs about 10,000 rubles.

I really respect long-playing phones. Always enjoyed old xeniums. It seems that Vladivostok residents have this in their blood - they are too lazy to recharge every day, so they washed down a whole line of 10 models with powerful batteries. 4000 mAh battery (6-8 video reports with DEF CON) and a case thicker than a centimeter. (Near the old, kind, faithful phone "for bribes", which has served me as a flashlight for over 5 years.)
Looking at Borisdick you get the Razor, I come to the conclusion that very often a simple and crude method can be effective. For example, to protect yourself from a hidden microphone on, you can stupidly put a mechanical toggle switch on / off the microphone.
Right on the very top of the photo is a smart phone case for Cocoon (acoustic safe), which I was given to play at Detector Systems when I took from them an armful of field indicators and bug emulators. (There will be a review soon.)
Acoustic safe - a product designed to protect the voice information circulating in the places where the owner of a cell phone stays in the event of its activation for the purpose of listening through cellular channels. Protection is provided by automatic acoustic noise transmission of the voice information transmission path during an attempt to tacitly activate the microphone of a cell phone handset. “Ladia” and “Kokon” products have passed certification tests according to the requirements of the State Technical Commission of the Russian Federation (Certificates No. 697, 698) and can be used in designated rooms up to category 1 inclusive.
The cell phone is placed inside the Cocoon. In the case of tacit remote activation of the phone in the listening mode, the only indication of a unmasking sign is a change in the intensity of the electromagnetic field (i.e., the cellular phone transmitter is unauthorized to transmit). This change is fixed by the field indicator, which is part of the product, which gives the command to automatically turn on the acoustic noise generator. At the same time, the entire voice information transmission path is noisy in such a way that there are no signs of speech at the receiving end.
Specifications:
Secondly, it will now be easier for me to shoot video and photos of spy devices.

(to the article about detectors of bugs, field indicators and legal emulators of bugs)
For example, the acoustic safe is squealing like this:
For reference, Dexp Snatch costs 7,500 rubles (although there are models with a large battery for both 4,500 and 14,000 rubles in the Dexp line), and an acoustic safe costs about 10,000 rubles.

I really respect long-playing phones. Always enjoyed old xeniums. It seems that Vladivostok residents have this in their blood - they are too lazy to recharge every day, so they washed down a whole line of 10 models with powerful batteries. 4000 mAh battery (6-8 video reports with DEF CON) and a case thicker than a centimeter. (Near the old, kind, faithful phone "for bribes", which has served me as a flashlight for over 5 years.)
Looking at Boris
Right on the very top of the photo is a smart phone case for Cocoon (acoustic safe), which I was given to play at Detector Systems when I took from them an armful of field indicators and bug emulators. (There will be a review soon.)
Acoustic safe - a product designed to protect the voice information circulating in the places where the owner of a cell phone stays in the event of its activation for the purpose of listening through cellular channels. Protection is provided by automatic acoustic noise transmission of the voice information transmission path during an attempt to tacitly activate the microphone of a cell phone handset. “Ladia” and “Kokon” products have passed certification tests according to the requirements of the State Technical Commission of the Russian Federation (Certificates No. 697, 698) and can be used in designated rooms up to category 1 inclusive.
The cell phone is placed inside the Cocoon. In the case of tacit remote activation of the phone in the listening mode, the only indication of a unmasking sign is a change in the intensity of the electromagnetic field (i.e., the cellular phone transmitter is unauthorized to transmit). This change is fixed by the field indicator, which is part of the product, which gives the command to automatically turn on the acoustic noise generator. At the same time, the entire voice information transmission path is noisy in such a way that there are no signs of speech at the receiving end.
Specifications:
- The noise level at the location of the microphone cell phone: at least 100 dB
- Effective noise signal spectrum: 250 - 4000 Hz
- Time of continuous operation from one set of batteries: at least 6 months
- Power supply of the Cocoon product: CR 2032 lithium battery
- Time of continuous work from one set of batteries: at least 2 months
Story
The first mentions of the confrontation between the special services and “hackers” in the field of telephony appeared in 1993-1995.
Clipper chip (1993)
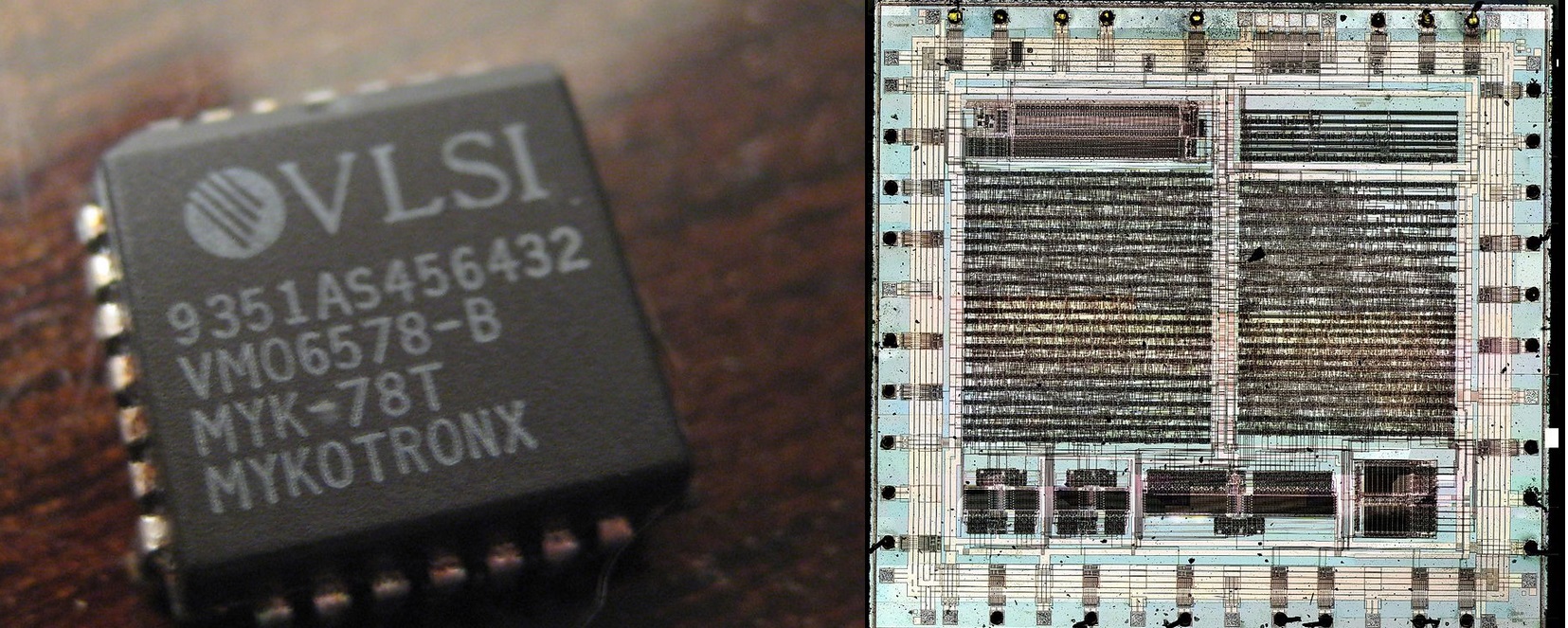
NSA made a chip for encryption Clipper chip . Of course with backdoor.
Hackers reacted and filed Nautilus with strong cryptography and then PGPfone.
Nautilus 1995
Wired Article
PGPfone (1995)
PGPfone - secure telephony from PGP developer Philip Zimmerman.
1999
Alex Biryukov and Adi Shamir publish a report on the successful attack on the A5 / 1 algorithm used in the GSM standard for data protection.
Israeli programmers have discovered a hole in the security system of mobile telephony, allowing any user who has a personal computer with 128 megabytes of RAM and a large hard drive to decipher telephone conversations or transmitted data.
[source: rus , eng ]
ZRTP (2006)

A cryptographic encryption key negotiation protocol used in Voice over IP (VoIP) systems. ZRTP describes the Diffie-Hellman key acquisition method for the Secure Real-time Transport Protocol (SRTP). ZRTP negotiates keys in the same RTP stream over which the audio / video connection is established, that is, it does not require a separate communication channel. Designed by Philip Zimmermann (Phil Zimmermann, author Pretty Good Privacy), John Callas (Jon Callas) and Alan Johnston (Alan Johnston) in 2006. The protocol description was filed with the IETF on March 5th, 2006.
2009
Karsten Nohl, a member of the German hacker group CCC (Chaos Computer Club), announced at a group conference on December 28 that he was able to crack the data encryption algorithm in GSM networks.
Nol published the results of his work on the Internet by posting a book of codes on one of the torrent trackers. According to him, this should force mobile operators to reconsider the security measures of the cellular communications they provide. [ source ]
At the Black Hat conference, software for decrypting calls in GSM networks is presented.
Hackers introduced "Kraken" to break the encryption algorithm in GSM-networks
Zfone (2009)
Zfone is software for the secure transmission of voice data over the Internet (VoIP). The program allows you to conduct private negotiations anywhere, with anyone, anytime. The Zfone project was founded by Philip Zimmermann, the creator of Pretty Good Privacy (PGP), a widespread encryption software. The development was carried out with the participation of Svitla Systems, Soft Industry and the Ukrainian Hi-tech Initiative.
2010
All your baseband are belong to us:
2013
750 million mobile phones vulnerable to intruders due to inadequately protected SIM cards
Karsten Nohl, the founder of Security Research Labs, announced the discovery of the vulnerability of SIM cards with the DES (Data Encryption Standard) encryption standard. This is an outdated standard, which, however, is used by a large number of manufacturers, and hundreds of millions of SIM-cards support DES. So, this vulnerability allows, when sending a fake message from a carrier to a phone, to receive a 56-bit key in the reply message (the answer is sent automatically, and about 25% of DES-cards are subject to such “deception”).
(A small and not very hardcore note that flashed on Habré)
Listening to and protecting mobile phones
How do operators protect their networks?
In the development of GSM technology, as well as at the stage of its implementation, all requirements from the controlling state were taken into account. authorities to the level of protection. It is precisely because of these requirements that the sale and purchase of special equipment, like powerful encryptors, crypto equipment, scramblers, as well as very protected technologies for public communication, is prohibited in many countries of the world. But mobile operators themselves protect their radio channels using signal encryption methods. Encryption uses very complex algorithms. What kind of cryptographic algorithm will be encrypted is selected at the stage when the connection is established between the base station and the subscriber. The degree of probability of a subscriber’s information leakage from the operator’s equipment, as MTS employees assured the journalists, that it is practically zero. Why to zero, we asked - and all because of the complexity and control over access to the facilities and equipment of the operator.
How can you "listen" to mobile phones?
In total there are two methods of wiretapping subscribers - this is the active method and the passive method. When listening to a subscriber passively, you need to use very expensive equipment and have specially trained employees. If you have money (read - big money) on the “black market” you can purchase special complexes, using which you can listen to conversations of any subscriber within a radius of up to 500 meters. Ask why you need to have a lot of money? The answer is simple - the price of one such set starts from several hundreds of thousands of euros. What this kit looks like is seen in the following photo. In the network there are many sites where you can find a description and principle of operation of such sets and listening systems.

As manufacturers of such listening systems convince, their systems can track GSM-conversations in real time, because the principle of operation of the equipment is based on access to the SIM card of a mobile subscriber, or directly to the database of the cellular operator itself. Although, if there is no such access for those who listen to you, they can listen to all your conversations with some delay. The amount of delay depends on the level of encryption of the communication channel that an operator uses. Similar systems can also be mobile centers for listening and tracking the movement of objects.
The second method of wiretapping is active intervention directly on the air on the authentication process and control protocols. For this purpose, special mobile complexes are used. Such mobile systems, which, in fact, are a pair of specially modified phones and a laptop, despite their apparent simplicity and small size, are also an expensive pleasure - their price varies from a couple of tens of thousands to several hundred thousand US dollars. And again, only highly qualified specialists in the field of communications can work on such equipment.
The attack on the subscriber is carried out according to the following principle: since the complex is mobile and is located close to the subscriber - up to 500 meters - it “intercepts” the signals for establishing a connection and transmitting data, replacing the base station of the operator. In essence, the complex itself becomes a “bridge” between the nearest base station and the subscriber himself.
After “capturing” the desired mobile subscriber in this way, this complex can actually perform any control function over the intercepted channel: for example, connect the listener with any number necessary for those who listen to the number, lower the crypto-encryption algorithm, or disable this encryption altogether for a specific communication session and t .d
How about looks like a similar complex - seen in the photo below.
 image
image
As the experts shared, 100% to determine that the subscriber’s phone is tapped at this particular moment is impossible. But, it is possible to obtain indirect evidence that may indicate that there is such a probability. In the recent past, some mobile models (namely, push-button telephones) had in their functionality a special character-icon in the form of a lock. If the lock was closed, then the signal goes in encrypted form, and vice versa - if the lock is open ... well, you yourself understood everything.
But already in the phones over the past 5-6 years there is no such function ... A pity. Although, for some models of smartphones special applications are provided that will signal to the owner of the phone about the configuration of the settings used in the current communication session. One of the options is to notify the user about the mode in which his conversation is transmitted - using encryption algorithms or openly. Listed below are a few of these applications:
EAGLE Security
It is one of the most powerful applications to protect your mobile from wiretapping. This program prevents any connections to false base stations. To determine the reliability of the station, verification of signatures and station identifiers is used. In addition, the program independently monitors and remembers the location of all base stations and if it detects that a base is moving around the city, or its signal disappears from time to time from its location - this base is marked as false and suspicious and the application will notify the owner phone. Another useful feature of the program is the ability to show which of the applications and programs installed on the phone have access to the video camera and microphone of your phone. There is also a function to disable (prohibit) access of any unnecessary software to the camera.
Darshak
This program is different from the previous one and its main function is to track any suspicious activity on the network, including when using SMS, which can be sent without the permission of the phone owner. The application in real time assesses how your network is secure and what encryption algorithm is used at that moment, and much more.
Android IMSI-Catcher Detector
This application also helps protect your smartphone from any connections to pseudo-bases. The only drawback of this program is that you will not find it on Google Play and if you want to install it yet, you will have to tinker with this procedure.
CatcherCatcher
The CatcherCatcher program, like its counterparts above, is engaged in identifying spurious base stations that attackers (or special services?) Use as intermediate “intermediary bridges” between the subscriber and the real base station.
And finally, experts also recommended using special applications to ensure the security of personal conversations and data, including - to encrypt your conversations. Such analogs are the anonymous web browsers Orbot or Orweb, for example. There are also special programs that encrypt your telephone conversations, photos, and many already use secure messengers.
Source - Listening to mobile phones and protecting them
In the development of GSM technology, as well as at the stage of its implementation, all requirements from the controlling state were taken into account. authorities to the level of protection. It is precisely because of these requirements that the sale and purchase of special equipment, like powerful encryptors, crypto equipment, scramblers, as well as very protected technologies for public communication, is prohibited in many countries of the world. But mobile operators themselves protect their radio channels using signal encryption methods. Encryption uses very complex algorithms. What kind of cryptographic algorithm will be encrypted is selected at the stage when the connection is established between the base station and the subscriber. The degree of probability of a subscriber’s information leakage from the operator’s equipment, as MTS employees assured the journalists, that it is practically zero. Why to zero, we asked - and all because of the complexity and control over access to the facilities and equipment of the operator.
How can you "listen" to mobile phones?
In total there are two methods of wiretapping subscribers - this is the active method and the passive method. When listening to a subscriber passively, you need to use very expensive equipment and have specially trained employees. If you have money (read - big money) on the “black market” you can purchase special complexes, using which you can listen to conversations of any subscriber within a radius of up to 500 meters. Ask why you need to have a lot of money? The answer is simple - the price of one such set starts from several hundreds of thousands of euros. What this kit looks like is seen in the following photo. In the network there are many sites where you can find a description and principle of operation of such sets and listening systems.

As manufacturers of such listening systems convince, their systems can track GSM-conversations in real time, because the principle of operation of the equipment is based on access to the SIM card of a mobile subscriber, or directly to the database of the cellular operator itself. Although, if there is no such access for those who listen to you, they can listen to all your conversations with some delay. The amount of delay depends on the level of encryption of the communication channel that an operator uses. Similar systems can also be mobile centers for listening and tracking the movement of objects.
The second method of wiretapping is active intervention directly on the air on the authentication process and control protocols. For this purpose, special mobile complexes are used. Such mobile systems, which, in fact, are a pair of specially modified phones and a laptop, despite their apparent simplicity and small size, are also an expensive pleasure - their price varies from a couple of tens of thousands to several hundred thousand US dollars. And again, only highly qualified specialists in the field of communications can work on such equipment.
The attack on the subscriber is carried out according to the following principle: since the complex is mobile and is located close to the subscriber - up to 500 meters - it “intercepts” the signals for establishing a connection and transmitting data, replacing the base station of the operator. In essence, the complex itself becomes a “bridge” between the nearest base station and the subscriber himself.
After “capturing” the desired mobile subscriber in this way, this complex can actually perform any control function over the intercepted channel: for example, connect the listener with any number necessary for those who listen to the number, lower the crypto-encryption algorithm, or disable this encryption altogether for a specific communication session and t .d
How about looks like a similar complex - seen in the photo below.
 image
imageAs the experts shared, 100% to determine that the subscriber’s phone is tapped at this particular moment is impossible. But, it is possible to obtain indirect evidence that may indicate that there is such a probability. In the recent past, some mobile models (namely, push-button telephones) had in their functionality a special character-icon in the form of a lock. If the lock was closed, then the signal goes in encrypted form, and vice versa - if the lock is open ... well, you yourself understood everything.
But already in the phones over the past 5-6 years there is no such function ... A pity. Although, for some models of smartphones special applications are provided that will signal to the owner of the phone about the configuration of the settings used in the current communication session. One of the options is to notify the user about the mode in which his conversation is transmitted - using encryption algorithms or openly. Listed below are a few of these applications:
EAGLE Security
It is one of the most powerful applications to protect your mobile from wiretapping. This program prevents any connections to false base stations. To determine the reliability of the station, verification of signatures and station identifiers is used. In addition, the program independently monitors and remembers the location of all base stations and if it detects that a base is moving around the city, or its signal disappears from time to time from its location - this base is marked as false and suspicious and the application will notify the owner phone. Another useful feature of the program is the ability to show which of the applications and programs installed on the phone have access to the video camera and microphone of your phone. There is also a function to disable (prohibit) access of any unnecessary software to the camera.
Darshak
This program is different from the previous one and its main function is to track any suspicious activity on the network, including when using SMS, which can be sent without the permission of the phone owner. The application in real time assesses how your network is secure and what encryption algorithm is used at that moment, and much more.
Android IMSI-Catcher Detector
This application also helps protect your smartphone from any connections to pseudo-bases. The only drawback of this program is that you will not find it on Google Play and if you want to install it yet, you will have to tinker with this procedure.
CatcherCatcher
The CatcherCatcher program, like its counterparts above, is engaged in identifying spurious base stations that attackers (or special services?) Use as intermediate “intermediary bridges” between the subscriber and the real base station.
And finally, experts also recommended using special applications to ensure the security of personal conversations and data, including - to encrypt your conversations. Such analogs are the anonymous web browsers Orbot or Orweb, for example. There are also special programs that encrypt your telephone conversations, photos, and many already use secure messengers.
Source - Listening to mobile phones and protecting them
Review of solutions for the protection of telephone conversations
(Some materials are taken from promotional leaflets, so common skepticism and comments are welcome)
The tubes of the world
booklet

TopSec GSM, created on the basis of the Siemens S35 phone by the German firm Rohde & Swartz, provides “full traffic protection”.
The device is a regular phone Siemens S35, upgraded with a special crypto chip. Encryption is enabled by a special option in the phone menu. In the protected mode, the phone can work both with the second TopSec phone and with the ISLC-phone ELCRODAT 6-2 of the same company.
Protection is provided by encrypting traffic with a 128-bit key, and the session key is calculated using a 1024-bit key, which provides additional protection. A distinctive feature of this phone is that encrypted packets are created in it in such a way that they are transparently perceived and transmitted over GSM networks, just like ordinary GSM packets.
The price of this phone: $ 2,700. Such a high price, however, did not prevent the high popularity of TopSec GSM. So, the Bundeswehr (German armed forces) signed a contract for the supply of such phones for their own needs.

A slightly more fashionable version from the same company is a wireless headset.
 Short description:
Short description:TopSec Mobile is a voice encryption device that can be connected to any mobile phone via Bluetooth. TopSec Mobile provides privacy and protection against telephone tapping anywhere in the world.
Features:
- Connecting to the user's phone via Bluetooth interface
- TopSec Mobile works with almost all modern mobile phones.
- Can also be used with Bluetooth modem and satellite phones.
- Cannot be identified by the mobile operator.
- Voice encryption with Advanced Encryption Standard (AES), 256-bit key
The device uses a combination of asymmetric 1024-bit and symmetric 128-bit encryption to ensure a high level of protection.
To establish a secure connection, the user, after dialing the number, simply press the button labeled crypto ("encryption"). The other subscriber must also use a TopSec GSM telephone - or a landline telephone equipped with similar equipment, such as the ELCRODAT 6-2 ISDN model from Rohde & Schwarz. This company began to sell such devices after purchasing hardware encryption from Siemens Information & Communication Mobile.
The TopSec GSM phone operates in two frequency bands - 900 and 1800 MHz, so that it can be used in any region where GSM 900/1800 networks are available. The company sells new models in many countries around the world for about $ 3,000.
[ source ]
The disadvantage of this approach is the presence of a dedicated call control server between subscribers registered on the server. But this is a necessary condition for building distributed interaction systems:
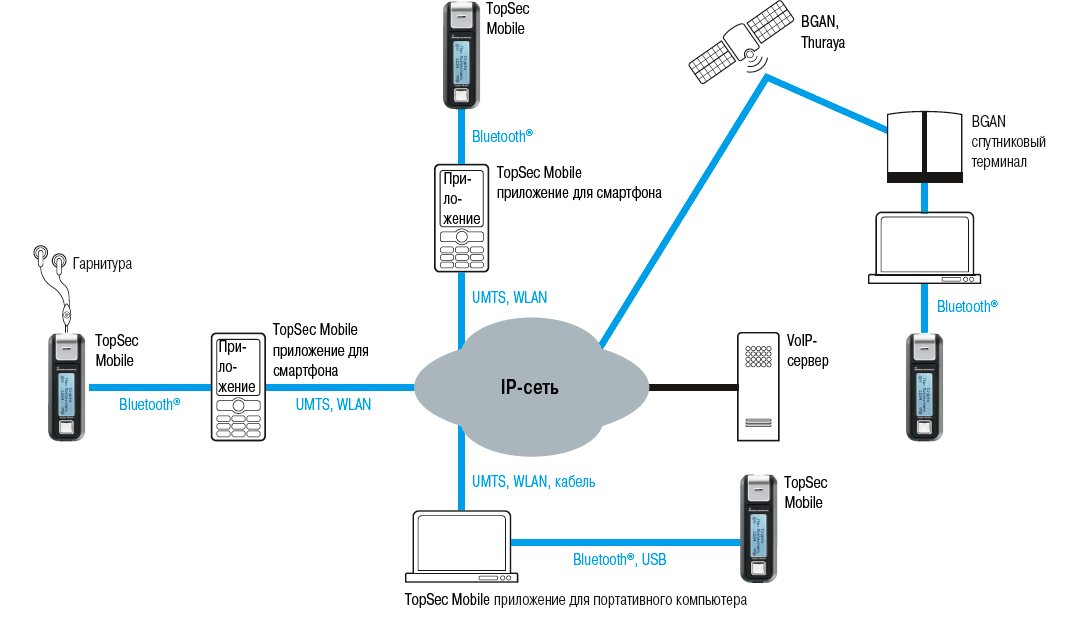
www.cryptophone.de
A strange German device, about which I can not say anything:

HC-2413
 The device of the Swiss company Crypto AG - HC-2413. As far as can be judged from the photo, it is made on the basis of the Sagem MC-850 phone, in the lower part of which a scrambling device is added.
The device of the Swiss company Crypto AG - HC-2413. As far as can be judged from the photo, it is made on the basis of the Sagem MC-850 phone, in the lower part of which a scrambling device is added.The HC-2413 provides a full duplex secure connection not only with similar devices, but also with the stationary telephone terminals HC-2203 of the same company. For encryption, the device uses a 128-bit key and Crypto AG's own development algorithm.
Using such a device allows you to protect your conversations from listening at any part of the transmission (of course, except for direct listening to ultra-sensitive microphones in the immediate vicinity of the subscriber).
Sectra tiger
 In April 2000, the Swedish company Sectra Communications launched an export model for its Tiger mobile digital phone.
In April 2000, the Swedish company Sectra Communications launched an export model for its Tiger mobile digital phone.Sectra Tiger models using encryption technology with keys from 56 to 256 bits in length provide secure communication over public GSM networks.
Sectra offers both centralized and distributed key management systems, either using SmartKey smart cards of the company itself, or using the KeyBeam infrared communication feature implemented in Tiger models. Keys can be generated in the phone itself and sent directly to a narrow circle of users. In the future, Sectra intends to develop versions of its phones for other wireless standards, in particular for the CDMA standard, which is widely used in the United States.
Strict government regulation of the import and export of encryption technologies, in the opinion of company representatives, significantly limits the sales opportunities of such mobile phones. In addition to the permission from the government, buyers also need a lot of money. “Civilian” versions of Tiger mobile phones will cost about 5 thousand dollars, the discount is given only to those buyers who purchase a batch of devices of several hundred pieces.
The device has the dimensions of a modern cell phone and weighs 197 g, but it is distinguished from traditional devices by the unusual arrangement of the antenna, which is installed at the bottom rather than at the top. The mobile phone also has a slot for installing smart cards from which the encryption key is read.
Blackphone

Blackphone 2: New Crypto Smartphone Details
The most secure BlackPhone smartphone was vulnerable
no comments, except perhaps cool, that they create "their own appstore" for secure applications
Russian tubes
Scrambler
(Meanwhile in the
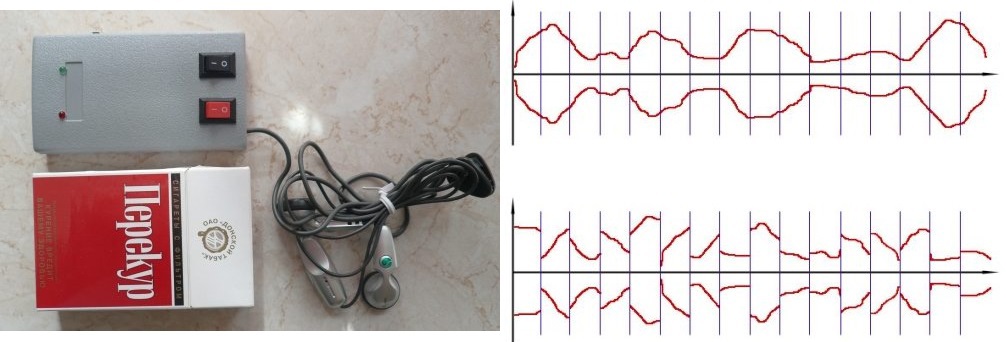
"GUARD Bluetooth" from the company LOGOS.
I will quote Lukatsky :
Original sovok device. There is no design as such. Headsets tightly "sewn" in the device and replace it only with the device. But the protection of negotiations is guaranteed - the device connects via Bluetooth to a transmitter - a computer or a phone (not a word about the protection of the Bluetooth channel using E0). The device is not tested, but on the network you can find its review. The appearance of “GUARD Bluetooth” in comparison with the same TopSec Mobile gives a very good idea of how domestic and western SKZI relate (both in appearance, and in terms of user experience, and functionality). But for the operation of this device does not require any external server - it is possible to work “point-to-point”.
Description from the user
Description from the manufacturer
PDA referee
Software and hardware kit for protection of negotiations in GSM networks
 The hardware and software product “Referent-PDA” is designed for devices like a smartphone (communicator) that are running the Windows Mobile 2003/2005 operating system. The PDA Referee helps prevent interception of negotiations between two communicators. The kit consists of SD / miniSD - module, software and Qtek-8500 smartphone.
The hardware and software product “Referent-PDA” is designed for devices like a smartphone (communicator) that are running the Windows Mobile 2003/2005 operating system. The PDA Referee helps prevent interception of negotiations between two communicators. The kit consists of SD / miniSD - module, software and Qtek-8500 smartphone.The program interface contains: dial pad, call control buttons, the button for canceling the last digit and the indicator that displays the number to be dialed, the caller’s number on the incoming call, the state when the call is established, etc.
The program starts automatically when the SDA mini-SD module is connected, and the icon indicating that the program is launched into the background mode appears on the communicator screen in the lower right corner. To call another subscriber in the protected mode, you must click on the indication icon, and then perform the same actions in the opened “Assistant PDA” program as in a normal call. When a call comes from another set of PDA Referent, instead of the “phone” program, the PDA Referent program interface automatically opens, then all the actions are the same as during a normal call.
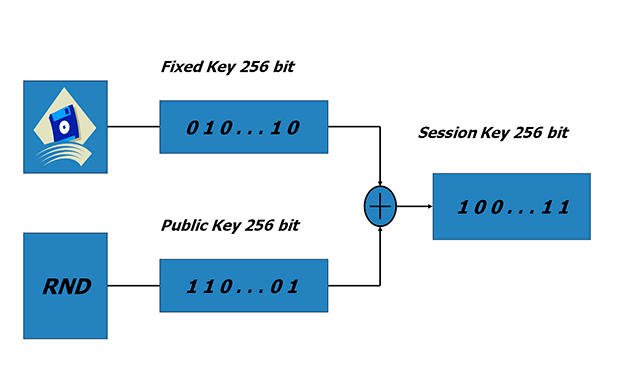
In the process of establishing a connection, special information is exchanged for mutual authentication of devices and generation of a session key.
Accepting and making an unprotected voice call is performed using standard communicator software.
The main difference between the product and its analogs is the use of a low-speed data transmission channel (up to 1600 baud), which allows working with a weak GSM signal (in places of poor reception), in roaming, with the use of various operators, etc.
Let's just call it “phone”

(I “squeezed” this phone from Kostya, which is represented by Hideport.com )
Chips - mechanical acoustics control (on / off button for microphone), body integrity control (hidden alarm when trying to get inside the pipe)
It seems that this thing has a means of accessing other networks (cable modem, analog / digital modem, radio modem, satellite terminal or GSM modem). But I still have to find out about this.
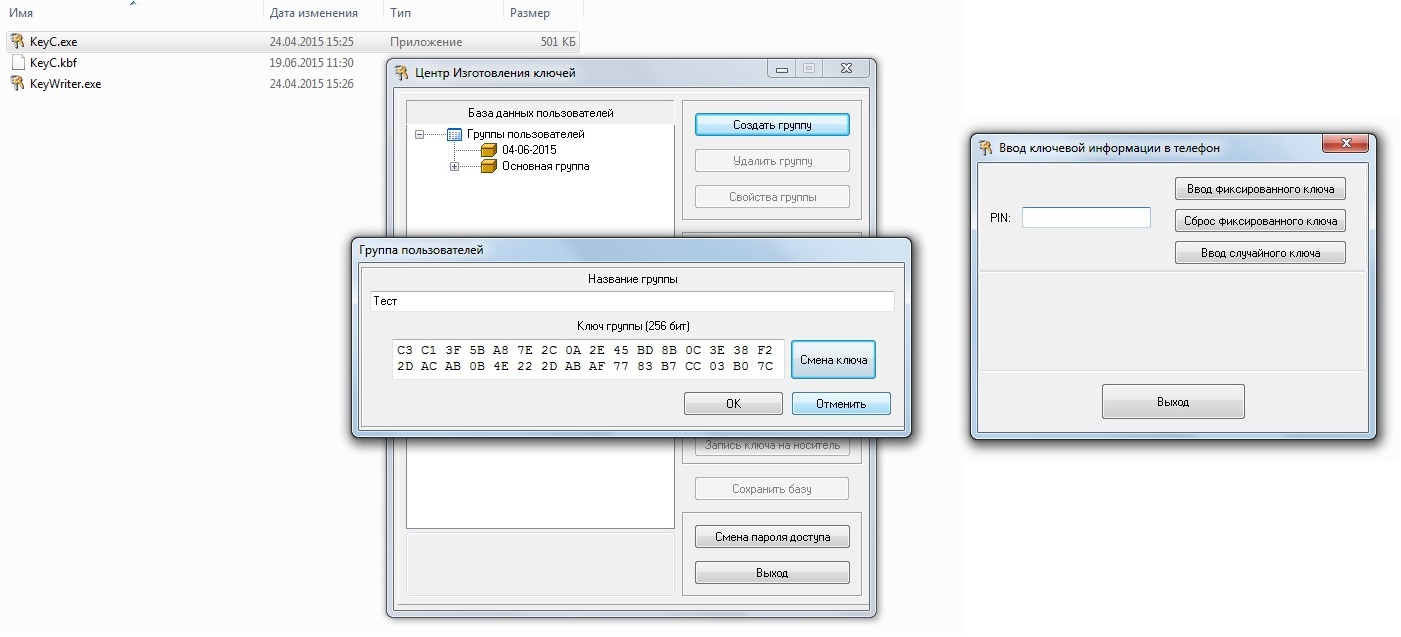
I got into the production of telephones for special services, allowed to make a couple of pictures:


crumbs of details
(850, 900, 1800 1900 ), , ACELP 4800 /, , ; – , 28147 1989 . , , , , 10 , . .
, . – 4 , – 4,5, , script-.
, , (, ), , , ; 850/1900, – 900/1800. , , BS26T. , , – , .
, GSM , , .
, : , , , 12 . , . , 64 , – , . . , . , , , ( ), . GSM BS26T – 9600 /. , , , . , .
, , , , – GSM, 12 , , 4,8 /. , – , – - , - , , .
, , , . , BS26T.
, , . SMS, , .
, , , ; Wi-Fi, . : , ( ), , . , , : , .
, . – 4 , – 4,5, , script-.

, , (, ), , , ; 850/1900, – 900/1800. , , BS26T. , , – , .
, GSM , , .
, : , , , 12 . , . , 64 , – , . . , . , , , ( ), . GSM BS26T – 9600 /. , , , . , .
, , , , – GSM, 12 , , 4,8 /. , – , – - , - , , .
, , , . , BS26T.
, , . SMS, , .

, , , ; Wi-Fi, . : , ( ), , . , , : , .

StealthPhone
Held in the hands of StealthPhone Touch

I saw this model here.
 As an encryption algorithm, we use the symmetric encryption algorithm of Tiger guaranteed strength, which is the company's own development.
As an encryption algorithm, we use the symmetric encryption algorithm of Tiger guaranteed strength, which is the company's own development.The key length is 256 bits.
The algorithm belongs to the class of synchronous stream cipher gamming. Synchronization is carried out using an initialization vector (synchrum), which is transmitted (or stored) in clear text with ciphertext. The length of the synchro send varies from 4 to 12 bytes and is determined by the context of the use of the encoder.
To bring the encoder into working condition, the procedure of its initialization is performed, to the input of which a secret key and a synchronizing signal are supplied. The output of the initialization procedure are the values of all elements of the state of the encoder, determining its operation.
The basic algorithm for calculating the data authentication code is the HMAC-SHA256 algorithm.
The Stealthphone and Stealthphone Tell systems use 384-bit elliptic curves (the NSA approved the use of asymmetric cryptographic algorithms on elliptic curves with a key length of 384 bits for processing top-secret documents).
more details
VoGSM
GSM - , .
:
.
( ) 2.5 .
IP-
IP-, Skype Viber, - , .
:
( , ) .
.
1 3–5 .
1 . 300 – 3400 . N 24.
-, . 2 . - , . .
, Stealthphone .
GSM - , .
:
- ;
- ;
- ;
- AMR GSM.
- ( ) .
.
( ) 2.5 .
IP-
IP-, Skype Viber, - , .
:
- N ( );
- ( );
- N.
( , ) .
.
1 3–5 .
1 . 300 – 3400 . N 24.
-, . 2 . - , . .
, Stealthphone .

Invisible phone
His is not visible on the Internet, but he is.
Features:
- Change IMEI (international identification phone number)
- Protection against active and passive complexes (interception of negotiations and remote control of the phone and other attacks on the device by the operator or the mobile GSM complex)
- Deletion of information about calls from the phone’s memory (deleted information is stored in special memory compartments and is accessible to specialists)
- The impossibility of localizing the phone and its owner (as well as determining the number of the main phone and the associated numbers of other phones)
Additional functions
Using a virtual number for calls
, . . . , ( ). ( ). , .
From the description of the tube
False base stations
A special device, called the IMSI trap (a unique identifier registered in the SIM card, IMSI - International Mobile Subscriber Identity), pretends for nearby mobile phones as a real base station of a cellular telephone network. This kind of trick is possible because in the GSM standard a mobile phone is obliged to authenticate itself at the request of the network, but the network itself (base station) does not have to confirm its authenticity with the telephone.
As soon as the mobile phone accepts the IMSI trap as its base station, this repeater can deactivate the encryption function enabled by the subscriber and work with the usual open signal, transferring it further than the real base station.
With the help of IMSI traps, false calls or SMS can be sent to the phone, for example, with information about the new service of the false operator, which may contain the activation code of the microphone of the mobile device. It is very difficult to determine that the microphone is on in the standby mobile phone, and an attacker can easily hear and record not only telephone conversations, but also conversations in the room where the mobile phone is located.
As soon as the mobile phone accepts the IMSI trap as its base station, this repeater can deactivate the encryption function enabled by the subscriber and work with the usual open signal, transferring it further than the real base station.
With the help of IMSI traps, false calls or SMS can be sent to the phone, for example, with information about the new service of the false operator, which may contain the activation code of the microphone of the mobile device. It is very difficult to determine that the microphone is on in the standby mobile phone, and an attacker can easily hear and record not only telephone conversations, but also conversations in the room where the mobile phone is located.
Falsification of personal identification
In recent years, the use of a mobile phone as evidence of personal identification has become increasingly popular. For example, a way to recover a lost account password to Google is to send an SMS with confirmation of the code to the owner of the phone. Some banks use similar two-step authentication, sending codes to special mobile numbers in order to verify the identity of the client before the transaction. Mobile versions of trojans were detected that could intercept SMS messages with passwords sent by banks and destroy two-step authentication.
Materials:
Cryptography in GSM networks
Crypto phones
All Your Baseband Are Belong To Us
TopSec Product Family. Voice encryption at the highest security level
TopSec Mobile. Anti-listening phone calls
Officials will be banned from using non-certified mobile phones (2014)
How to avoid wiretapping? There is a way
Shh-ss. This is not on the phone
MINISTRY OF RUSSIA. On approval of the Rules for application of equipment of switching systems, including software, ensuring the implementation of established actions during operational investigative activities. ( Pdf )
If there is a mobile phone near you (around 10 meters), behave as if you are live on the first channel.
So, are we going to make an open source DIY phone with strong software and hardware cryptography?
- Open source
- mechanical control of the transmitters
- built-in sonic indicator of receiver-transmitter activity
- strong cryptography (hardware and software)
- base station selection control
- acoustic steganography, masking the fact of encryption
- integrity control of the phone
- channel leakage checking
What else to add?
Source: https://habr.com/ru/post/264235/
All Articles