Operation Potao: an analysis of malware for cyber espionage, part 2
In terms of its capabilities, the Win32 / Potao malware has many common characteristics with the BlackEnergy Trojan. Before starting to look at the technical capabilities of Potao, consider the origin of the name of this malware family.
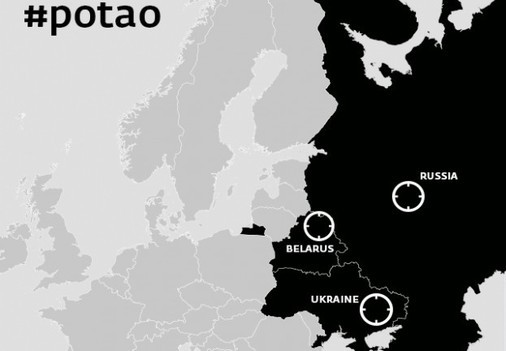
The first samples of Potao contained in their body an encrypted GlobalPotao string. Other Potao samples that are also detected by ESET antivirus products include the names Sapotao and node69 . These words were used in the names of the Potao DLL files, as well as in the PDB paths inside the executable files. The following are examples of lines with paths to a PDB file with Potao debugging symbols.
')
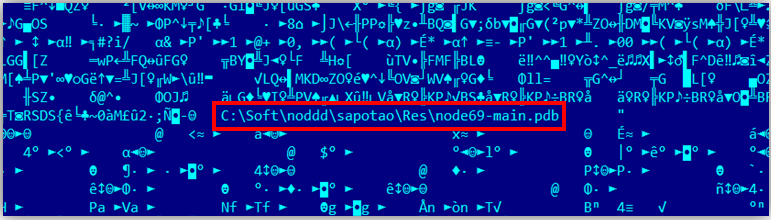
Fig. 21. Path to the PDB file in the body of the malware file.

Fig. 22. Path to the PDB file in the body of the malware file.
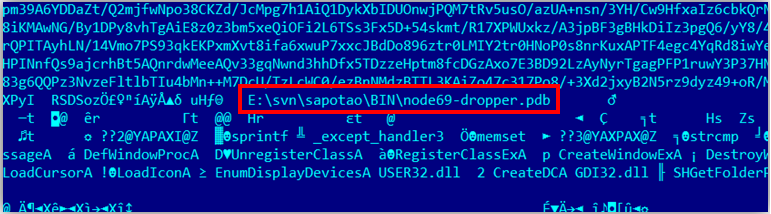
Fig. 23. Path to the PDB file in the body of the malware file.
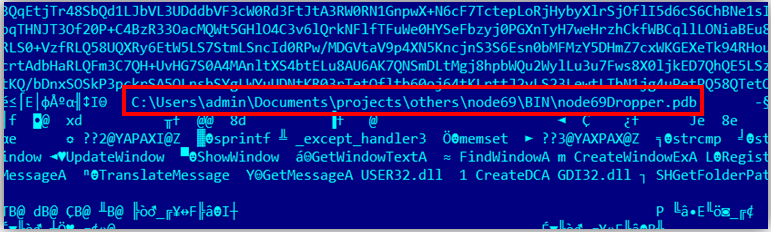
Fig. 24. Path to the PDB file in the body of the malware file.
The Potao malware family is a typical example of a tool that is used by cybercriminals for cyber espionage operations and for extracting (exfiltration) various confidential information from an infected computer and then sending them to a remote attacker server.
Like many other malicious programs, Potao is installed into the system through a special malicious file called a dropper. Below are the possible distribution vectors for Potao droppers.
Dropper Potao performed in two stages. At the first stage, it extracts the executable PE file from itself and dumps it into the directory with temporary files% temp%. It also resets the decoy-document file to the current directory and opens it in order to mask the actions in the OS to install malware into the system. The executable file extracted by the dropper extracts the DLL library from itself using the RtlDecompressBuffer API function. The library is reset to the following location:
% APPDATA% \ Microsoft \% LUID% .dll
Then the library will be implemented in the explorer.exe process. Before directly resetting the DLL to disk, the executable file of the malicious program performs special actions. It corrects one of the names of the exported function in the associated export table entry with the special value of the LUID. The screenshot below shows the code of the malware function that performs this operation and renames the specified function name to “_85fc”. As a result, each DLL loaded onto a disk will have a different hash.

Figure 25. Potao dropper function, which specializes in modifying the name of the export DLL in memory.
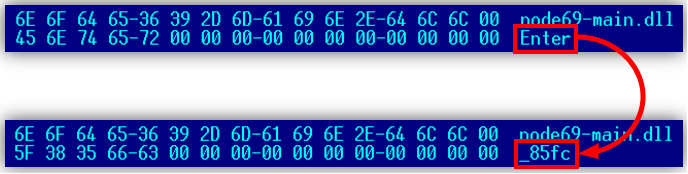
Figure 26. The result of the modification of the name of the exported library function.
To execute its DLL, Potao uses a standard Windows application called rundll32.exe, and to ensure its survival in the system, the following registry key with the% LUID% parameter.
HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Run
As we have already indicated, Potao uses a modular architecture and its capabilities can be expanded using additional plug-ins.

Fig. 27. The overall architecture of Win32 / Potao.
During the installation of the malware into the system, the dropper will inject the above DLL library into the explorer.exe process. After checking the presence of a special mutex in the system, the malicious code will also be embedded in the address space of such working processes as web browsers, Skype, uTorrent. The part of the malicious code that is embedded in the explorer.exe context will be responsible for downloading and executing Potao plug-ins, and the code embedded in programs with a network connection will be responsible for interaction with the C & C server. The interaction between these parts is carried out through the named pipe.
Plugin Overview
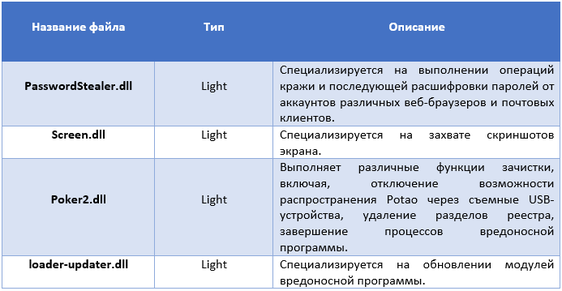
The main DLL library mentioned above performs only the most basic functions of a malicious program. Responsibility for the implementation of espionage functions rests on downloadable plugins (modules). Malicious code loads plugins every time it is launched on the system, which indicates that they are not stored on the hard disk. There are two types of plug-ins, the first Full, and the second Light. Executable files of plugins of the first type export a function named Plug , and plug-in files of the second type export the Scan function. The difference between the two types is in how each of them collects the necessary information and returns it to the client. Full plug-ins work continuously until the system is rebooted, Light plug-ins finish their work immediately after returning the buffer with the required information.
In the process of tracking the activity of the Potao botnet, we found plugins signed with a digital signature (Fig. 28).

Fig. 28. Information about the digital certificate that signed some of the Potao plugins.
The name of the organization “Grand Torg”, which issued the certificate, can be interpreted as “Big Market”. However, we could not find an organization with that name. The serial number of the certificate (Serial Number) is equal to the value 0453B96EB039AFD6C9988C8CB698E7C9, and its revocation (Revocation Time) was carried out in the following time: Aug 19 00:00:00 2014 GMT Since the revocation date actually coincides with the date of issue, all digital signatures that were made by this certificate were invalid. This fact leads us to the conclusion that the certificate was used from the beginning by attackers for malicious purposes and was not stolen from any vendor.
The table below lists the known Potao plugins.

Interaction with the C & C Server Manager
The Win32 / Potao samples that we analyzed contained several different IP addresses of the C & C control servers. Addresses were encrypted in the body of the malware. Below is a list of these addresses.
87.106.44.200:8080
62.76.42.14:443
62.76.42.14:8080
94.242.199.78:443
178.239.60.96:8080
84.234.71.215:8080
67.103.159.141:8080
62.76.184.245:80
62.76.184.245:443
62.76.184.245:8080
The malware selects one of these addresses and attempts to establish a connection. As you can see from the list of used ports, the interaction can be performed both via HTTP and HTTPS. The interaction with the server is accompanied by the use of strong cryptographic algorithms in two stages. At the first stage, key exchange takes place, and at the second stage, direct data exchange takes place. In fig. 29 this process is presented more clearly.

Fig. 29. Key exchange processes between a bot and a C & C server, as well as network interaction between them.
When a bot first interacts with a C & C server (1), it sends a request in the POST format of the HTTP protocol. The data sent by the bot is encapsulated using the XML-RPC protocol. It is interesting to note that the methodName parameter, equal to 10a7d030-1a61-11e3-beea-001c42e2a08b, was always present in the traffic we analyzed.
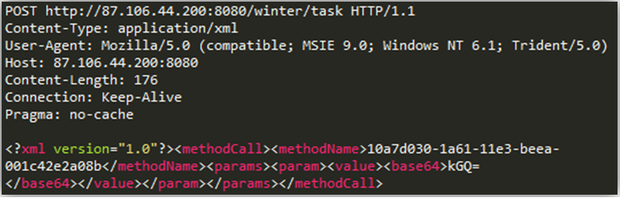
Fig. 30. The initial POST request of the HTTP protocol that the bot sends to the server.
After receiving the above request, the C & C server generates the public key RSA-2048 (2) and signs it with another, private static key RSA-2048 (3).

Figure 31. C & C server response to the first bot request, which is the public key RSA-2048, signed with a private key, encoded using base64.
When a bot receives the RSA-2048 public key signed by the server, it performs verification of its signature (s) using the corresponding static public key, which is located in the malicious program file (5). If the verification is successful (the key signature is valid), the received key (6) will be used to encrypt the data in the next step. The public RSA-2048 key that is hard-wired into the body of the malware has the appearance.

At the second stage, the bot generates an AES-256 symmetric key (7). This so-called. The session key is encrypted using the received public RSA-2048 key (8) and sent to the C & C server (9).
The data transmitted from the server to the bot is encrypted using the AES-256 key (12) (13) and decrypted by it on the server side (14).
Leaving aside the technical details of the implementation of the above-mentioned cryptographic algorithms in the malware code, consider the format of the interaction protocol between the bot and the server. The bot sends the request to the server in encrypted form, the format of the request is shown below.
id = 4699807581825067201mapt & code = 0 & sdata = ver: 5.1.2600 lv: 2.8.0002 comp: COMPUTER adm: 1 x: 0 p: firefox.exe & md5 = & dlen = 0
It can be seen that the request contains the identifier (ID) of the computer, the campaign ID, the OS version, the malware version, the computer name, current privileges of the user account, OS width (32 or 64 bits), and the name of the current process.
The server responds with the following format.
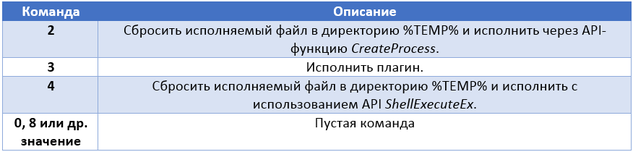
code =% cmd% & data =% PAYLOAD_BASE64_ENCODED% & dlen =% PAYLOAD_LENGTH% & md5 =% MD5%
The value of the code parameter represents the type of command that the bot should execute. The list of commands that a bot can execute is listed in the table below.
Spread via removable USB media
In several malicious campaigns, the attackers used another Potao propagation vector, using the infection of removable USB drives. Potao uses a different way to infect removable media from other worms (autorun worm). Instead of creating an autorun.inf file in the root of the drive's file system, it uses a simple and efficient way of storing its executable file on the media with its subsequent launch. Malware code, which is responsible for infecting removable media, copies the dropper to the root directory of all drives connected to the system. In this case, the label of the removable media is selected as the name of the dropper file, and the system icon of this media is selected as the icon. The remaining directories and files in the root directory on this media are assigned the attributes Hidden (hidden) and System (system). For the user, it seems that he needs to click the icon again to open the disk. As a result of this action, he launches a dropper for execution.

Fig. 32. The dropper icon and its file name in the root directory of the removable media are the same as the removable media.
Obviously, with the default settings in Windows, which I allow to hide the extension for registered file types, the user will not see the extension of the dropper executable file. He also will not see other files in the root of the disk, as their attributes have been modified. This malware trick can be attributed to the “social engineering” method.
The malware contains special methods in its arsenal that make it difficult for it to analyze the executable file. One of these methods is to use hashes of API function names to call them.
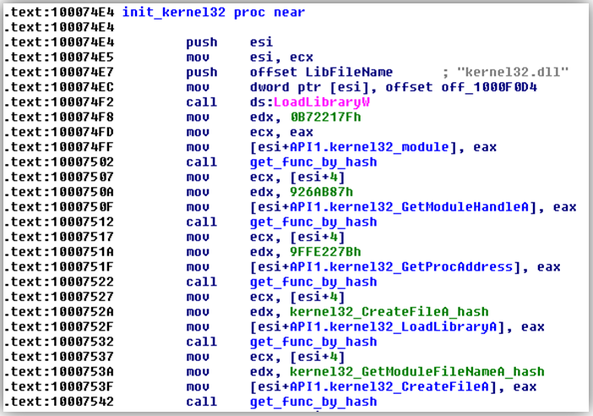
Fig. 33. Getting the addresses of WinAPI functions using the hash values of their names.
This practice of obtaining addresses of Windows API functions is used in many malicious programs; it allows malware authors not to leave the names of functions in the body of a malicious program, which significantly complicates the analysis process for analysts of antivirus companies. To calculate the hash values of the names of API functions, the malware uses the MurmurHash2 algorithm.
The authors also used an encryption mechanism for strings that should have been present in the body of Potao. In fig. 34 shows the string decryption function.

Fig. 34. The function of decoding lines.
The strings are encrypted using the XOR operation and a 4-byte key. The key may vary from one malicious file to another.
Win32 / FakeTC - Malware TrueCrypt Analysis
We have already mentioned that attackers used malicious modification of legitimate TrueCrypt software for their cyber campaigns. This modification is detected by our anti-virus products as Win32 / FakeTC and is used by attackers to extract files from the victim's encrypted disks. FakeTC is associated with Potao only by the fact that the former may, in some cases, download the dropper of the latter onto an infected computer.
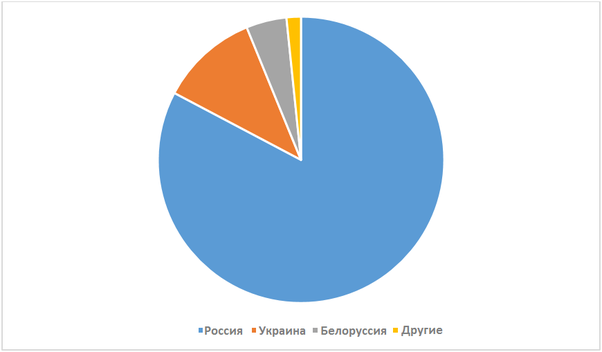
Fig. 35. Win32 / FakeTC detection statistics in various countries.
In fig. 36 shows the interface of the malicious version of TrueCrypt.

Fig. 36. The interface of the malicious version of TrueCrypt.
Malware code is executed in a separate thread from other legitimate functions of TrueCrypt. The stream is created at the end of the Mount function and specializes in getting a list of files on an encrypted disk that was mounted to the system. If certain conditions are met, he connects to the manager of the C & C server and expects commands from him for execution. The malicious code was added by the attackers only to the user-mode TrueCrypt executable files containing the digital signature kernel-mode drivers remained intact.
The following conditions must be met to connect the bot to the C & C server.
The list of supported FakeTC commands is given in the table below.

As can be seen from the list of commands supported by FakeTC, it is used by attackers as spyware malware and can be expanded by using additional plug-ins. The attackers used special FakeTC hiding mechanisms from prying eyes, carrying it out on the website only to selected users. This allowed the attackers to go unnoticed for a long time.
Conclusion
Above, we described the analysis of malware that is detected by ESET antivirus products like Win32 / Potao and Win32 / FakeTC, and we also looked at various cyber campaigns of intruders. We have shown that Win32 / Potao malware is an example of a tool for cyber espionage, and cyber attacks with its use can be attributed to the APT type, although, at the same time, Potao itself cannot be attributed to sophisticated advanced malware.
The group of cybercriminals behind Potao’s use of cyber attacks demonstrated the effectiveness of using carefully thought-out social engineering techniques instead of using exploits. Such well-considered techniques include the use of special SMS messages that contain a link to the malware file, as well as a special trick to infect removable media. One of the most interesting features of this cyber campaign was the use of a malicious version of the legitimate encryption software TrueCrypt by attackers. The program itself with malicious features was posted on the website truecryptrussia.ru and not all users could receive it. In addition, the site itself acted as the manager of the C & C server for the malware.
The above facts characterize the Potao cyber campaign as “purely directed.” The question of interest remains open, that is, who would benefit from carrying out such a cyber espionage operation on the staff of the Ukrainian military and government departments, the news agency, as well as participants in the MMM financial pyramid. The latter is popular both in Ukraine and in Russia. Since we would not like to speculate on the search for an answer to this question, without having any weighty evidence in hand, this question remains open.
Below are the comparative characteristics of Potao and BlackEnergy.

The first samples of Potao contained in their body an encrypted GlobalPotao string. Other Potao samples that are also detected by ESET antivirus products include the names Sapotao and node69 . These words were used in the names of the Potao DLL files, as well as in the PDB paths inside the executable files. The following are examples of lines with paths to a PDB file with Potao debugging symbols.
')

Fig. 21. Path to the PDB file in the body of the malware file.

Fig. 22. Path to the PDB file in the body of the malware file.

Fig. 23. Path to the PDB file in the body of the malware file.

Fig. 24. Path to the PDB file in the body of the malware file.
The Potao malware family is a typical example of a tool that is used by cybercriminals for cyber espionage operations and for extracting (exfiltration) various confidential information from an infected computer and then sending them to a remote attacker server.
Like many other malicious programs, Potao is installed into the system through a special malicious file called a dropper. Below are the possible distribution vectors for Potao droppers.
- Phishing emails and SMS messages that contain links to the dropper files. The dropper executable file is masked using the icon of documents such as Word, Excel, PDF.
- Infection using previously compromised removable USB media.
- Distribution with the use of malicious software modifications to encrypt TrueCrypt (Win32 / FakeTC).
Dropper Potao performed in two stages. At the first stage, it extracts the executable PE file from itself and dumps it into the directory with temporary files% temp%. It also resets the decoy-document file to the current directory and opens it in order to mask the actions in the OS to install malware into the system. The executable file extracted by the dropper extracts the DLL library from itself using the RtlDecompressBuffer API function. The library is reset to the following location:
% APPDATA% \ Microsoft \% LUID% .dll
Then the library will be implemented in the explorer.exe process. Before directly resetting the DLL to disk, the executable file of the malicious program performs special actions. It corrects one of the names of the exported function in the associated export table entry with the special value of the LUID. The screenshot below shows the code of the malware function that performs this operation and renames the specified function name to “_85fc”. As a result, each DLL loaded onto a disk will have a different hash.

Figure 25. Potao dropper function, which specializes in modifying the name of the export DLL in memory.

Figure 26. The result of the modification of the name of the exported library function.
To execute its DLL, Potao uses a standard Windows application called rundll32.exe, and to ensure its survival in the system, the following registry key with the% LUID% parameter.
HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Run
As we have already indicated, Potao uses a modular architecture and its capabilities can be expanded using additional plug-ins.

Fig. 27. The overall architecture of Win32 / Potao.
During the installation of the malware into the system, the dropper will inject the above DLL library into the explorer.exe process. After checking the presence of a special mutex in the system, the malicious code will also be embedded in the address space of such working processes as web browsers, Skype, uTorrent. The part of the malicious code that is embedded in the explorer.exe context will be responsible for downloading and executing Potao plug-ins, and the code embedded in programs with a network connection will be responsible for interaction with the C & C server. The interaction between these parts is carried out through the named pipe.
Plugin Overview
The main DLL library mentioned above performs only the most basic functions of a malicious program. Responsibility for the implementation of espionage functions rests on downloadable plugins (modules). Malicious code loads plugins every time it is launched on the system, which indicates that they are not stored on the hard disk. There are two types of plug-ins, the first Full, and the second Light. Executable files of plugins of the first type export a function named Plug , and plug-in files of the second type export the Scan function. The difference between the two types is in how each of them collects the necessary information and returns it to the client. Full plug-ins work continuously until the system is rebooted, Light plug-ins finish their work immediately after returning the buffer with the required information.
In the process of tracking the activity of the Potao botnet, we found plugins signed with a digital signature (Fig. 28).

Fig. 28. Information about the digital certificate that signed some of the Potao plugins.
The name of the organization “Grand Torg”, which issued the certificate, can be interpreted as “Big Market”. However, we could not find an organization with that name. The serial number of the certificate (Serial Number) is equal to the value 0453B96EB039AFD6C9988C8CB698E7C9, and its revocation (Revocation Time) was carried out in the following time: Aug 19 00:00:00 2014 GMT Since the revocation date actually coincides with the date of issue, all digital signatures that were made by this certificate were invalid. This fact leads us to the conclusion that the certificate was used from the beginning by attackers for malicious purposes and was not stolen from any vendor.
The table below lists the known Potao plugins.


Interaction with the C & C Server Manager
The Win32 / Potao samples that we analyzed contained several different IP addresses of the C & C control servers. Addresses were encrypted in the body of the malware. Below is a list of these addresses.
87.106.44.200:8080
62.76.42.14:443
62.76.42.14:8080
94.242.199.78:443
178.239.60.96:8080
84.234.71.215:8080
67.103.159.141:8080
62.76.184.245:80
62.76.184.245:443
62.76.184.245:8080
The malware selects one of these addresses and attempts to establish a connection. As you can see from the list of used ports, the interaction can be performed both via HTTP and HTTPS. The interaction with the server is accompanied by the use of strong cryptographic algorithms in two stages. At the first stage, key exchange takes place, and at the second stage, direct data exchange takes place. In fig. 29 this process is presented more clearly.

Fig. 29. Key exchange processes between a bot and a C & C server, as well as network interaction between them.
When a bot first interacts with a C & C server (1), it sends a request in the POST format of the HTTP protocol. The data sent by the bot is encapsulated using the XML-RPC protocol. It is interesting to note that the methodName parameter, equal to 10a7d030-1a61-11e3-beea-001c42e2a08b, was always present in the traffic we analyzed.

Fig. 30. The initial POST request of the HTTP protocol that the bot sends to the server.
After receiving the above request, the C & C server generates the public key RSA-2048 (2) and signs it with another, private static key RSA-2048 (3).

Figure 31. C & C server response to the first bot request, which is the public key RSA-2048, signed with a private key, encoded using base64.
When a bot receives the RSA-2048 public key signed by the server, it performs verification of its signature (s) using the corresponding static public key, which is located in the malicious program file (5). If the verification is successful (the key signature is valid), the received key (6) will be used to encrypt the data in the next step. The public RSA-2048 key that is hard-wired into the body of the malware has the appearance.

At the second stage, the bot generates an AES-256 symmetric key (7). This so-called. The session key is encrypted using the received public RSA-2048 key (8) and sent to the C & C server (9).
The data transmitted from the server to the bot is encrypted using the AES-256 key (12) (13) and decrypted by it on the server side (14).
Leaving aside the technical details of the implementation of the above-mentioned cryptographic algorithms in the malware code, consider the format of the interaction protocol between the bot and the server. The bot sends the request to the server in encrypted form, the format of the request is shown below.
id = 4699807581825067201mapt & code = 0 & sdata = ver: 5.1.2600 lv: 2.8.0002 comp: COMPUTER adm: 1 x: 0 p: firefox.exe & md5 = & dlen = 0
It can be seen that the request contains the identifier (ID) of the computer, the campaign ID, the OS version, the malware version, the computer name, current privileges of the user account, OS width (32 or 64 bits), and the name of the current process.
The server responds with the following format.
code =% cmd% & data =% PAYLOAD_BASE64_ENCODED% & dlen =% PAYLOAD_LENGTH% & md5 =% MD5%
The value of the code parameter represents the type of command that the bot should execute. The list of commands that a bot can execute is listed in the table below.

Spread via removable USB media
In several malicious campaigns, the attackers used another Potao propagation vector, using the infection of removable USB drives. Potao uses a different way to infect removable media from other worms (autorun worm). Instead of creating an autorun.inf file in the root of the drive's file system, it uses a simple and efficient way of storing its executable file on the media with its subsequent launch. Malware code, which is responsible for infecting removable media, copies the dropper to the root directory of all drives connected to the system. In this case, the label of the removable media is selected as the name of the dropper file, and the system icon of this media is selected as the icon. The remaining directories and files in the root directory on this media are assigned the attributes Hidden (hidden) and System (system). For the user, it seems that he needs to click the icon again to open the disk. As a result of this action, he launches a dropper for execution.

Fig. 32. The dropper icon and its file name in the root directory of the removable media are the same as the removable media.
Obviously, with the default settings in Windows, which I allow to hide the extension for registered file types, the user will not see the extension of the dropper executable file. He also will not see other files in the root of the disk, as their attributes have been modified. This malware trick can be attributed to the “social engineering” method.
The malware contains special methods in its arsenal that make it difficult for it to analyze the executable file. One of these methods is to use hashes of API function names to call them.

Fig. 33. Getting the addresses of WinAPI functions using the hash values of their names.
This practice of obtaining addresses of Windows API functions is used in many malicious programs; it allows malware authors not to leave the names of functions in the body of a malicious program, which significantly complicates the analysis process for analysts of antivirus companies. To calculate the hash values of the names of API functions, the malware uses the MurmurHash2 algorithm.
The authors also used an encryption mechanism for strings that should have been present in the body of Potao. In fig. 34 shows the string decryption function.

Fig. 34. The function of decoding lines.
The strings are encrypted using the XOR operation and a 4-byte key. The key may vary from one malicious file to another.
Win32 / FakeTC - Malware TrueCrypt Analysis
We have already mentioned that attackers used malicious modification of legitimate TrueCrypt software for their cyber campaigns. This modification is detected by our anti-virus products as Win32 / FakeTC and is used by attackers to extract files from the victim's encrypted disks. FakeTC is associated with Potao only by the fact that the former may, in some cases, download the dropper of the latter onto an infected computer.

Fig. 35. Win32 / FakeTC detection statistics in various countries.
In fig. 36 shows the interface of the malicious version of TrueCrypt.

Fig. 36. The interface of the malicious version of TrueCrypt.
Malware code is executed in a separate thread from other legitimate functions of TrueCrypt. The stream is created at the end of the Mount function and specializes in getting a list of files on an encrypted disk that was mounted to the system. If certain conditions are met, he connects to the manager of the C & C server and expects commands from him for execution. The malicious code was added by the attackers only to the user-mode TrueCrypt executable files containing the digital signature kernel-mode drivers remained intact.
The following conditions must be met to connect the bot to the C & C server.
- The number of files on the encrypted disk must be more than 10.
- The encrypted disk must be mounted more than 4 times.
The list of supported FakeTC commands is given in the table below.

As can be seen from the list of commands supported by FakeTC, it is used by attackers as spyware malware and can be expanded by using additional plug-ins. The attackers used special FakeTC hiding mechanisms from prying eyes, carrying it out on the website only to selected users. This allowed the attackers to go unnoticed for a long time.
Conclusion
Above, we described the analysis of malware that is detected by ESET antivirus products like Win32 / Potao and Win32 / FakeTC, and we also looked at various cyber campaigns of intruders. We have shown that Win32 / Potao malware is an example of a tool for cyber espionage, and cyber attacks with its use can be attributed to the APT type, although, at the same time, Potao itself cannot be attributed to sophisticated advanced malware.
The group of cybercriminals behind Potao’s use of cyber attacks demonstrated the effectiveness of using carefully thought-out social engineering techniques instead of using exploits. Such well-considered techniques include the use of special SMS messages that contain a link to the malware file, as well as a special trick to infect removable media. One of the most interesting features of this cyber campaign was the use of a malicious version of the legitimate encryption software TrueCrypt by attackers. The program itself with malicious features was posted on the website truecryptrussia.ru and not all users could receive it. In addition, the site itself acted as the manager of the C & C server for the malware.
The above facts characterize the Potao cyber campaign as “purely directed.” The question of interest remains open, that is, who would benefit from carrying out such a cyber espionage operation on the staff of the Ukrainian military and government departments, the news agency, as well as participants in the MMM financial pyramid. The latter is popular both in Ukraine and in Russia. Since we would not like to speculate on the search for an answer to this question, without having any weighty evidence in hand, this question remains open.
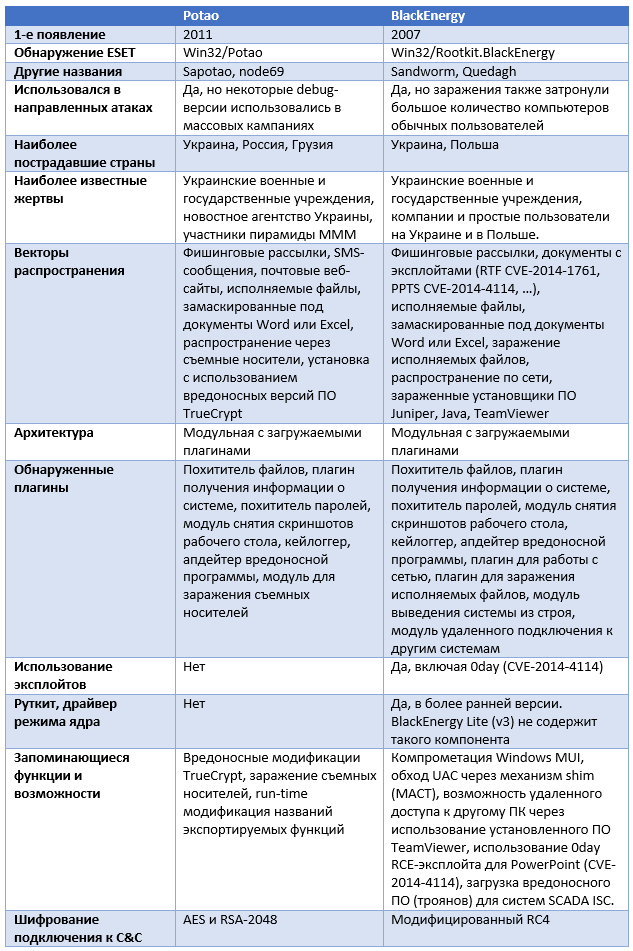
Below are the comparative characteristics of Potao and BlackEnergy.

Source: https://habr.com/ru/post/264165/
All Articles