Targeted attacks: China has attacked more than 600 objects in the USA in the last 5 years

The NBC television company had one interesting slide from the NTOC briefing (NSA Threat Operations Center, NSA Threats Response Center), which noted successful penetrations by Chinese hackers into government networks and organizations in the United States.
This slide was provided by an anonymous source from military intelligence, who emphasized the interest of Chinese hackers, possibly acting on instructions from the Chinese government to search and extract information.
')
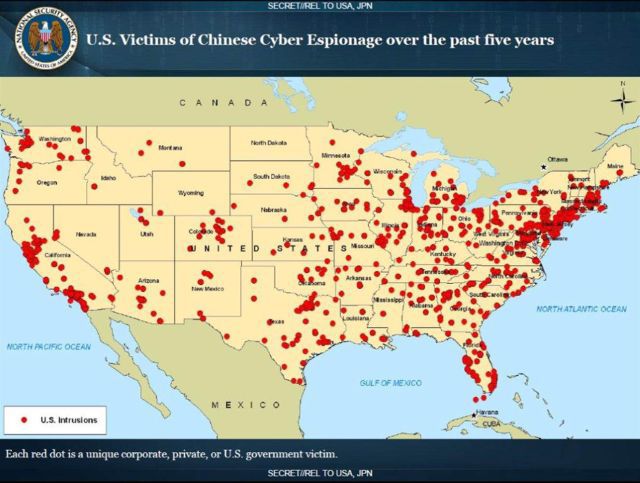
The slide shows that most of the points belong to the large cities and the east coast, where the main governmental organizations are concentrated. The report says that the NSA monitors Chinese cyber attacks for years and records all possible cases of successful attacks.
It is important to note that each red dot represents a successful attack in an attempt to steal:
- Corporate, industrial and military secrets.
- Schemes and maps of critical infrastructure in the United States.
- Schemes, location and data about power grids, telecommunication and Internet networks.
- Pharmaceutical manufacturing, chemical industry.
- Specifications for hybrid vehicles, especially cars.
- Data on civilian air traffic control systems.
Who is behind the attacks?
According to a study conducted by Mandiant , behind these attacks is the APT1 group, consisting, in turn, of more than 20 groups of Chinese hackers, most likely sponsored and controlled by the government of the PRC.
APT1 is considered to be part of the People’s Liberation Army of China as a division of 61398. Division 61398 (also known as the 2nd Bureau) is subordinate to the 3rd Administration of the PLA General Staff, which is considered to be analogous to the US National Security Agency (ANB). Sometimes this grouping is referred to as the Comment Crew or the Shanghai Group.
According to published data, division 61398 is responsible for conducting intelligence against the United States and Canada, while division 61046 (also known as the 8th Bureau) specializes in intelligence against European countries.
Although the PRC government denies the involvement of the APT1 group in government structures, there is indirect evidence. For example, supposedly in this building this unit is based, the entrance to which is guarded by paramilitary units:
According to the experts of the company Mandiant, with a high degree of probability we can assume that the hacker group APT1 is nothing more than a division of the PLA 61398. The following factors speak in favor of this:
- The scale of cyber espionage operations that this group has been conducting for a long time requires such amount of financial, human and material resources that only the state can provide;
- The technical and language skills required to perform the cyber espionage functions conducted by the Shanghai Group are identical to the corresponding competencies of division 61398 (espionage against the United States and Canada);
- The tactics, methods and procedures of the cyber espionage actions were purely intelligence-oriented, there were no cases of data destruction or financial fraud, which is typical of the actions of ordinary hackers or organized crime.
Famous APT with "Chinese trail"
There are at least three major attacks in recent years, which were carried out by the APT1 grouping:
"Titanium rain"
Since 2003, computers in the US have been subject to coordinated attacks for several years. As a result of computer espionage, companies such as Lockheed Martin, Sandia National Laboratories, Redstone Arsenal, and NASA suffered. These companies belong to the US military-industrial complex, some of them are involved in the manufacture of stealth aircraft (STEALTH).
"Operation Aurora"
The attacks began in mid-2009 and continued until December 2009. Google, Adobe Systems, Juniper Networks Rackspace, Yahoo, Symantec, Northrop Grumman, Morgan Stanley suffered. The goal is to gain access to the source codes of the software of the attacked companies and to information about Chinese dissidents. Here, in addition to the value of the software development itself, the goals of studying and searching for vulnerabilities in products that have not yet been released could be pursued to develop future attacks.
"GhostNet"
In March 2009, a network of compromised computers of embassies, foreign ministries, government agencies, political parties and economic organizations in 103 countries was discovered. The purpose of these attacks was to obtain confidential information and espionage.
Leak or intentional stuffing?
Most likely this leak is intentionally made to lobby for the “cyber-containment” policy. This kind of bill will enable the US to strengthen its defense systems, and possibly preemptive attacks in cyberspace, eliminating the source of the attack after its detection. Also, it will help extend the powers of United States Cyber Command, USCYBERCOM - US Cyber Command.
The main tasks of this division are:
- Protection of military computer networks and systems from unauthorized access;
- Providing remote access to computer networks of the likely adversary and using them to their advantage;
- Conducting electronic warfare;
- Conducting psychological operations of a military nature;
- Development and implementation of measures to mislead the enemy regarding the true plans of the US Armed Forces leadership.
Which of these can be concluded?
Every year the number of attacks grows and becomes more complex. For example, https://github.com/kbandla/APTnotes here shows the evolution of such attacks over the past few years. And on this site you can see a visual infographic of most known targeted attacks:
The Internet has become a full-scale military arena. The trend towards the development of offensive cyber-weapons of great penetrating power and manufacturability, which will be applied for its intended purpose by professionals, is becoming more and more obvious. Ability to resist modern threats is one of the fundamental doctrines of the country's defense, preservation of confidential data, technological and commercial secrets.
Source: https://habr.com/ru/post/264151/
All Articles