Can information security increase revenue, increase customer loyalty, and solve other business problems?
Usually information security is “sold” (by manufacturers to customers, and by information security / IT services to its management) under the guise of combating fear (leaks, viruses, DDoS, etc.) or meeting regulatory requirements (FZ-152, 382-P Bank of Russia, 17th order FSTEC, the 378th order of the FSB). This is a traditional view of security and its means of realization. If you look at the descriptions of many products, we will see that this is how they are positioned. It is understandable - these are universal drivers that do not depend on the company, which is offered to buy a firewall, Internet access control tool, antivirus, intrusion prevention system or whatever. And it is true. The Cisco ASA Firewall with FirePOWER Services Firewall will deal equally with unauthorized access in Russia, Australia and the UK. And the monitoring system for anomalous activity inside the Cisco Cyber Threat Defense network will also effectively detect malicious code that has bypassed perimeter defenses in the United States, Ukraine, and Norway.

The compliance situation requires a bit more focus. Obviously, the 17th order of the FSTEC on the protection of state information systems is a purely Russian invention, but it is applicable to all state and municipal institutions of our vast Motherland. And although the legislation on the protection of information in automated process control systems is in many countries around the world, it still differs from each other. The requirements of the 31st FSTEC order and the NERC CIP standard, the ISA / IEC 62443 standard and the Qatari safety standard for critical infrastructures are albeit similar in essence, but different in terms of, for example, conformity assessments, and therefore the solutions proposed for their implementation should already have their own specifics.
')

But here we come to the fact that in the current difficult economic situation The company's management is not interested in compliance, because if it is not fulfilled, if it is punished, then not much. Not much compared with the question of the survival of the company as such. And the threats are sometimes mythical in nature. And certainly they are not so terrible compared to the threat of bankruptcy of their own and counterparties, denial of credit, currency jumps and other more business-oriented threats. Therefore, the third driver of the advancement of information technology is coming to the fore - economics and finance. It is with their help that you can show how security solutions can help increase enterprise profits, reduce costs, increase customer loyalty, speed up product launches and help achieve other business objectives.

If you think about it, the economic / financial justification does not replace, but rather complements the previous two. You just want to take another step forward. For example, DDoS attack. You can simply frighten its consequences (not to mention how), but you can try to think and explain to the leadership what the DDoS attack leads to. To idle! And downtime is money. Money lost (we pay salaries to staff when idle). Unearned money (during idle time we cannot provide service and sell goods). Extra money spent (on restoring the system to the pre-packaged state). And what is the failure of the Bank of Russia 382-P? This is not only an order to eliminate violations from banking supervision, it is also, potentially, suspension of activities and even revocation of banking licenses (fortunately, so far there have been no such examples). And again, we were able to understand the threat from us, having made a small effort over ourselves, to shift the information security into the language of finance and business. And there are plenty of such examples when threats to information security affect precisely business indicators.
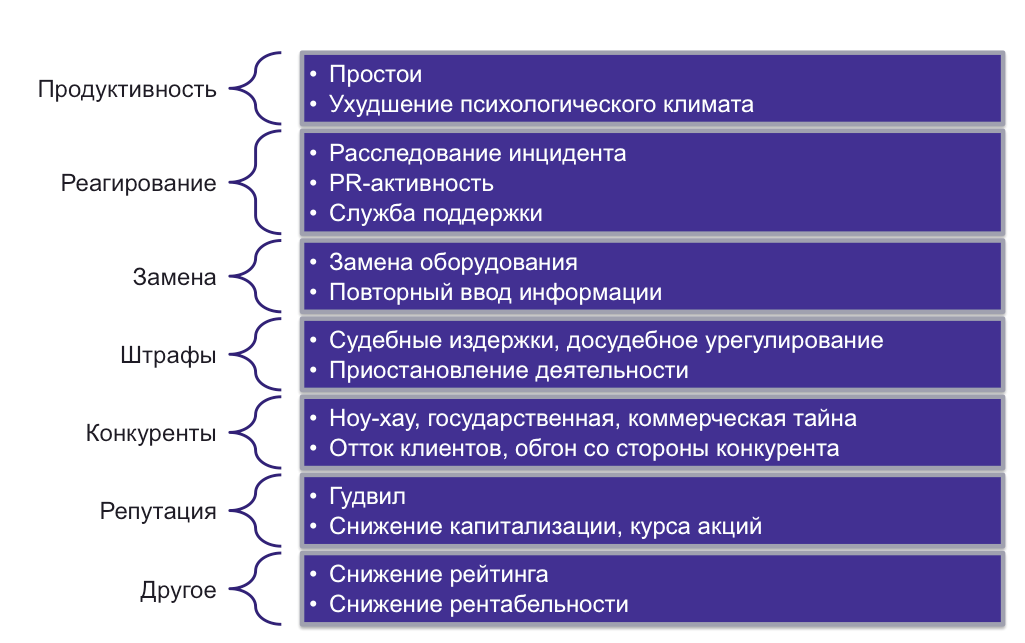
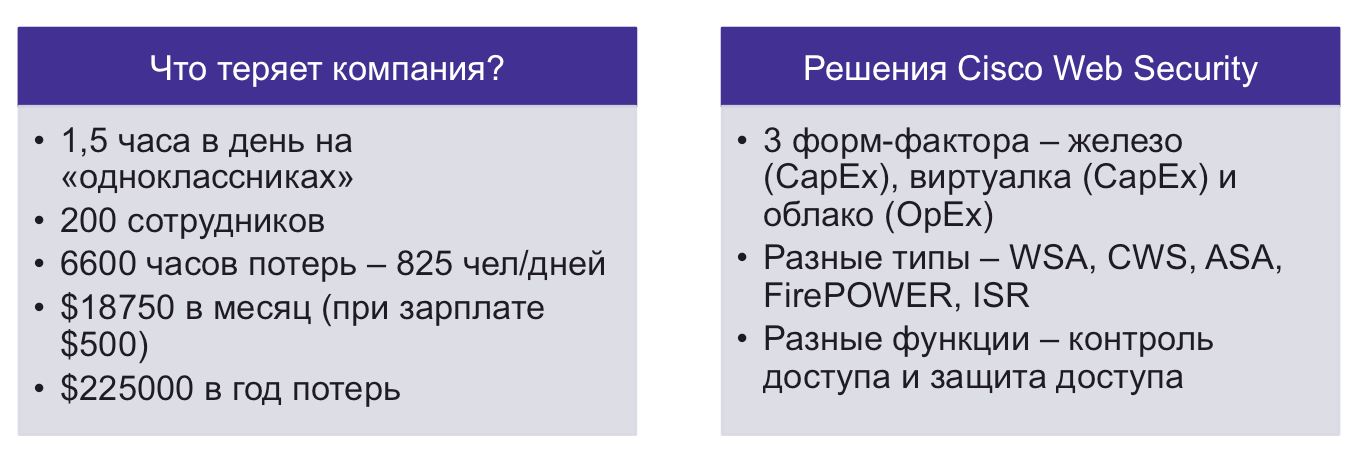
Since we were able to talk with businesses about information security in the language of money, then we can shift this language to the product line. To move away from the technical characteristics of the products in the direction of their financial efficiency. Here is just one example - a solution for protecting and controlling access to the Internet from Cisco. On one side of the scale, we have ... no, not the number of threats on the websites visited, and not the number of leaks prevented through the Web-mail. We are talking about information security from a business standpoint. Therefore, we will talk about productivity, or rather its losses from visiting sites that are unnecessary for work. And we can also talk about the violation of anti-piracy law and downloading pirated content at the expense of the company, which clogs the Internet channel and does not allow customers to reach our Web site or send us important mail. And all this is simply translated into money, which we put on one scale. On the other hand, we have a choice between a whole set of Cisco solutions - Cisco Web Security Appliance (WSA), Cisco ASA with FirePOWER Services, Cisco Cloud Web Security (CWS), Cisco FirePOWER Threat Defense for ISR. It is enough to compare the two amounts and see if it is profitable to invest in Cisco solutions or not.
And there are a lot of such examples. Especially to demonstrate the various options for financial justification for the use of Cisco information security solutions, we prepared and voiced the presentation and uploaded it to our corporate channel on YouTube. It describes 10 different scenarios that demonstrate how Cisco solutions (Cisco Web Security, ISE, VPN, Cisco Capital, Cisco Email Security, Cisco TrustSec, and others) can be demonstrated not in terms of threats (we are fighting with a large number of them), and not from the point of view of compliance with legislative requirements (here we also have something to tell ), but precisely from the point of view of financial efficiency and the implementation of business objectives.
As a result, our task is to look at information security not only from the traditional point of view - threats and normative acts, but also from the financial point of view. On one side of the “financial weights” we will have losses from non-realization of protective measures (fines, idle times, investigation and restoration costs, customer outflows), and on the other - business benefits derived from the implementation of protective measures (reduction of the transaction cycle, geographical expansion, new sales channel, increased customer loyalty, revenue growth).

And then we will have significantly increased the chances of not only acquiring the necessary security solutions, but also of our own growth within the company. It is always pleasant for the management to communicate with peers who understand the needs of the business, and not with people who only do that they block access to the Internet and read someone else's correspondence; that is how information security is often perceived in many enterprises.
Ps. Link to the presentation - http://www.slideshare.net/CiscoRu/cisco-50704113

The compliance situation requires a bit more focus. Obviously, the 17th order of the FSTEC on the protection of state information systems is a purely Russian invention, but it is applicable to all state and municipal institutions of our vast Motherland. And although the legislation on the protection of information in automated process control systems is in many countries around the world, it still differs from each other. The requirements of the 31st FSTEC order and the NERC CIP standard, the ISA / IEC 62443 standard and the Qatari safety standard for critical infrastructures are albeit similar in essence, but different in terms of, for example, conformity assessments, and therefore the solutions proposed for their implementation should already have their own specifics.
')

But here we come to the fact that in the current difficult economic situation The company's management is not interested in compliance, because if it is not fulfilled, if it is punished, then not much. Not much compared with the question of the survival of the company as such. And the threats are sometimes mythical in nature. And certainly they are not so terrible compared to the threat of bankruptcy of their own and counterparties, denial of credit, currency jumps and other more business-oriented threats. Therefore, the third driver of the advancement of information technology is coming to the fore - economics and finance. It is with their help that you can show how security solutions can help increase enterprise profits, reduce costs, increase customer loyalty, speed up product launches and help achieve other business objectives.

If you think about it, the economic / financial justification does not replace, but rather complements the previous two. You just want to take another step forward. For example, DDoS attack. You can simply frighten its consequences (not to mention how), but you can try to think and explain to the leadership what the DDoS attack leads to. To idle! And downtime is money. Money lost (we pay salaries to staff when idle). Unearned money (during idle time we cannot provide service and sell goods). Extra money spent (on restoring the system to the pre-packaged state). And what is the failure of the Bank of Russia 382-P? This is not only an order to eliminate violations from banking supervision, it is also, potentially, suspension of activities and even revocation of banking licenses (fortunately, so far there have been no such examples). And again, we were able to understand the threat from us, having made a small effort over ourselves, to shift the information security into the language of finance and business. And there are plenty of such examples when threats to information security affect precisely business indicators.

Since we were able to talk with businesses about information security in the language of money, then we can shift this language to the product line. To move away from the technical characteristics of the products in the direction of their financial efficiency. Here is just one example - a solution for protecting and controlling access to the Internet from Cisco. On one side of the scale, we have ... no, not the number of threats on the websites visited, and not the number of leaks prevented through the Web-mail. We are talking about information security from a business standpoint. Therefore, we will talk about productivity, or rather its losses from visiting sites that are unnecessary for work. And we can also talk about the violation of anti-piracy law and downloading pirated content at the expense of the company, which clogs the Internet channel and does not allow customers to reach our Web site or send us important mail. And all this is simply translated into money, which we put on one scale. On the other hand, we have a choice between a whole set of Cisco solutions - Cisco Web Security Appliance (WSA), Cisco ASA with FirePOWER Services, Cisco Cloud Web Security (CWS), Cisco FirePOWER Threat Defense for ISR. It is enough to compare the two amounts and see if it is profitable to invest in Cisco solutions or not.

And there are a lot of such examples. Especially to demonstrate the various options for financial justification for the use of Cisco information security solutions, we prepared and voiced the presentation and uploaded it to our corporate channel on YouTube. It describes 10 different scenarios that demonstrate how Cisco solutions (Cisco Web Security, ISE, VPN, Cisco Capital, Cisco Email Security, Cisco TrustSec, and others) can be demonstrated not in terms of threats (we are fighting with a large number of them), and not from the point of view of compliance with legislative requirements (here we also have something to tell ), but precisely from the point of view of financial efficiency and the implementation of business objectives.
As a result, our task is to look at information security not only from the traditional point of view - threats and normative acts, but also from the financial point of view. On one side of the “financial weights” we will have losses from non-realization of protective measures (fines, idle times, investigation and restoration costs, customer outflows), and on the other - business benefits derived from the implementation of protective measures (reduction of the transaction cycle, geographical expansion, new sales channel, increased customer loyalty, revenue growth).

And then we will have significantly increased the chances of not only acquiring the necessary security solutions, but also of our own growth within the company. It is always pleasant for the management to communicate with peers who understand the needs of the business, and not with people who only do that they block access to the Internet and read someone else's correspondence; that is how information security is often perceived in many enterprises.
Ps. Link to the presentation - http://www.slideshare.net/CiscoRu/cisco-50704113
Source: https://habr.com/ru/post/264101/
All Articles