NGFW. Part 3 - Demonstration of DDoS Protection
Attacks such as distributed denial of service (DDoS) attacks are still in the top lines of the anti-rating. DDoS attacks against commercial organizations have proven to be effective in disrupting business and attracting company attention. For example, through the use of massive botnets collected from compromised computers, hackers launched a series of highly publicized and highly destructive DDoS attacks against US banks.
Below is an example of protection against denial of service attacks using computers infected with malware using HP NGFW . To test this feature of the firewall, a stand was assembled, as shown in the figure below.
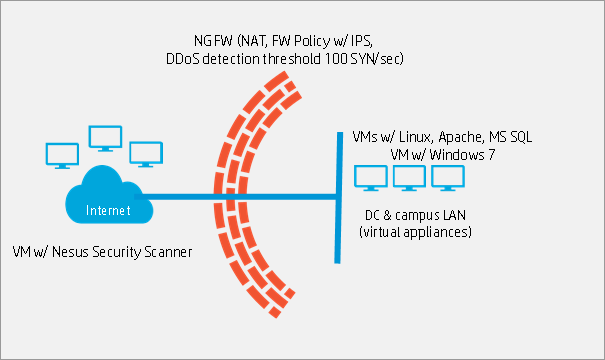
Stand layout
The stand consists of three main parts:
')
A virtual environment that simulates a local network is a virtual machine deployed on a workstation based on the Windows operating system. To simulate the operation of malicious software, a testing agent capable of generating DDoS traffic is installed on a part of virtual machines.
The firewall is installed in the gap between the Internet segment and the local network and at this stand is a third-level device that routes traffic between the segments. The basic rules and firewall settings are shown in the diagram above.
A virtual environment that mimics the Internet segment is a set of virtual machines based on the Linux operating system with specialized software installed on them - among other things, Apache web server, MySQL database server, PHP version 5 interpreter, Nessus security scanner, scan utility nmap network.
Below are the basic settings of NGFW in accordance with the developed stand scheme shown in Figure 3. All settings are shown in the NGFW's own web interface. Figure 4 shows the settings of the IP interfaces of the FW in accordance with the diagram above.
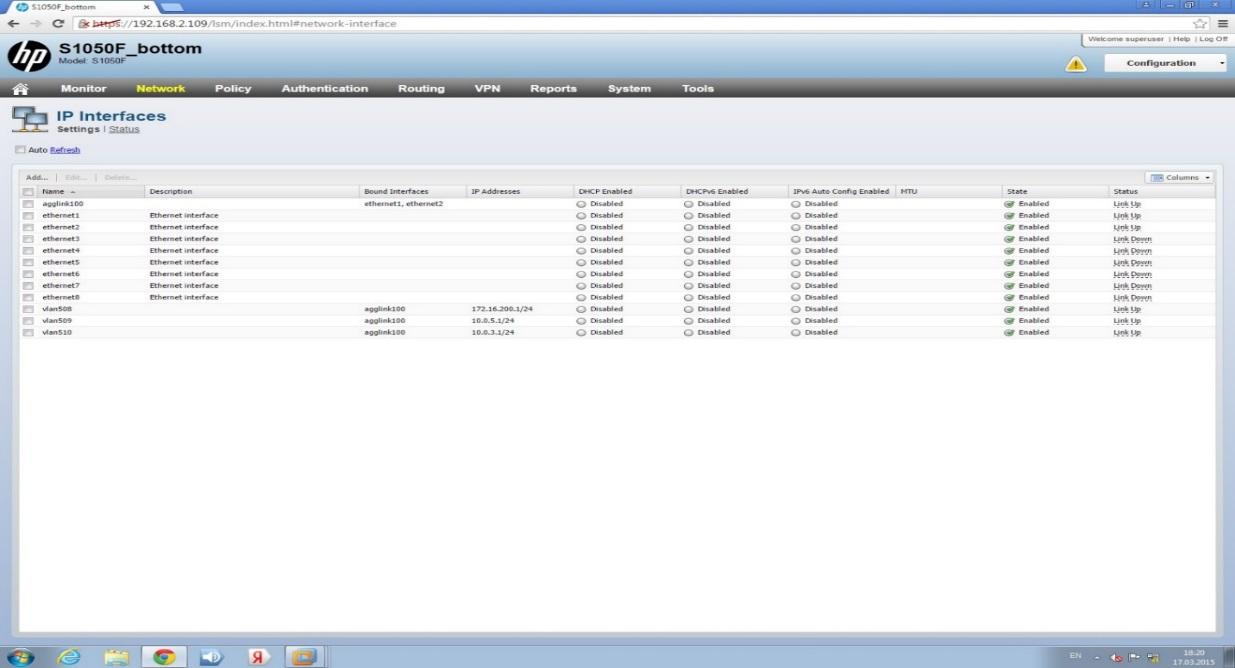
IP interface settings
Below are the security zone settings. For simplicity, the booth has three security zones set up - Inside, Outside and VPN.
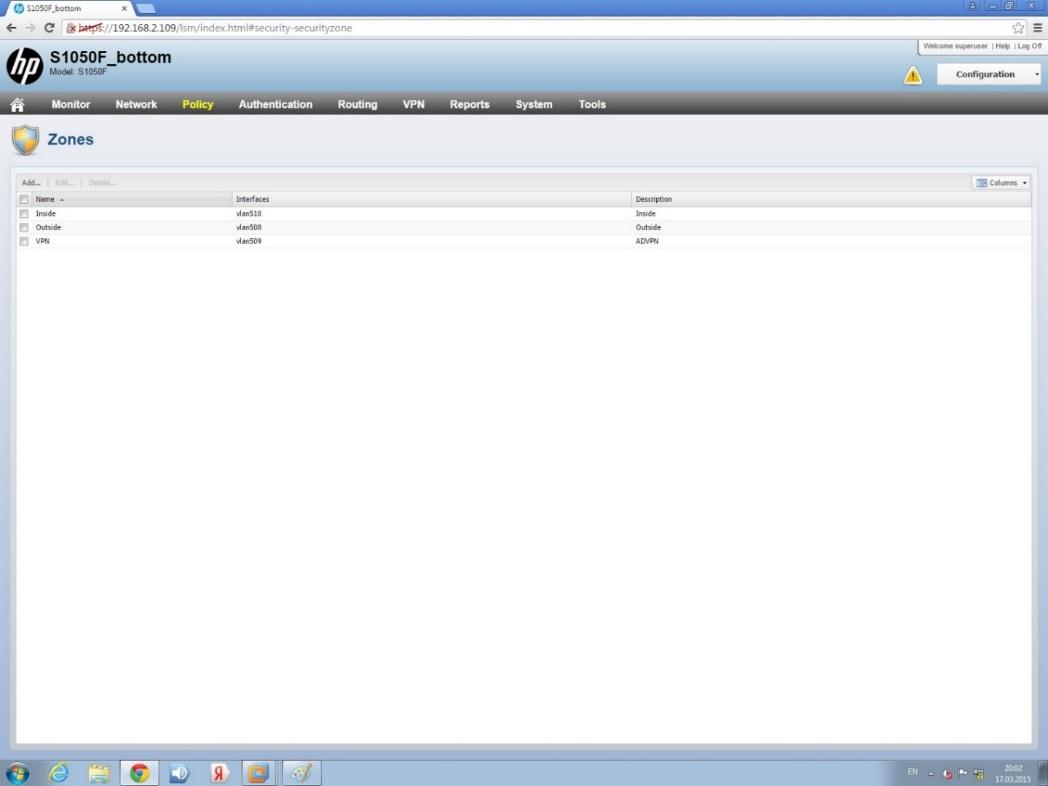
Security Zone Settings
Figure 6 shows the basic settings made for Destination NAT. Published several internal addresses of virtual machines that run various network services (HTTP / HTTPS, FTP, etc.).
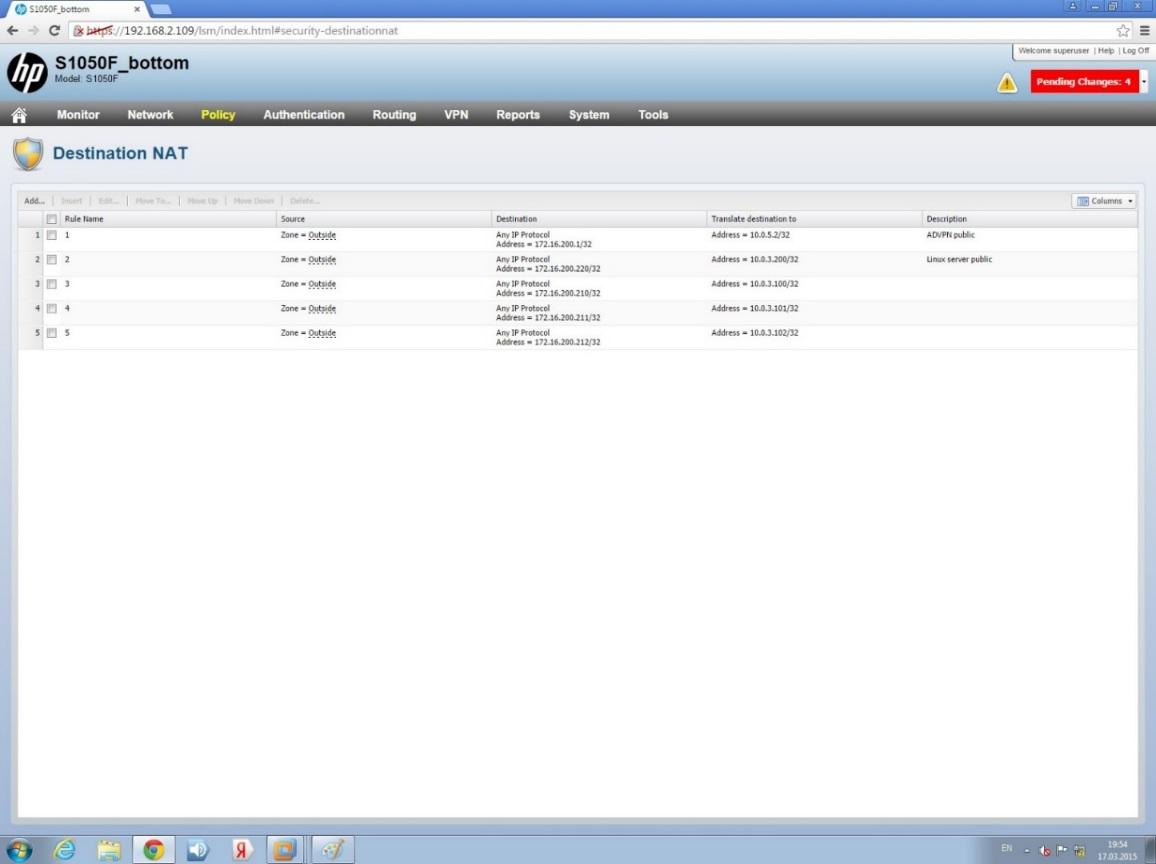
Destination NAT Settings
The following shows the basic Source NAT settings. Several virtual machine addresses are translated to external addresses in order to provide them access to the emulated malware services.
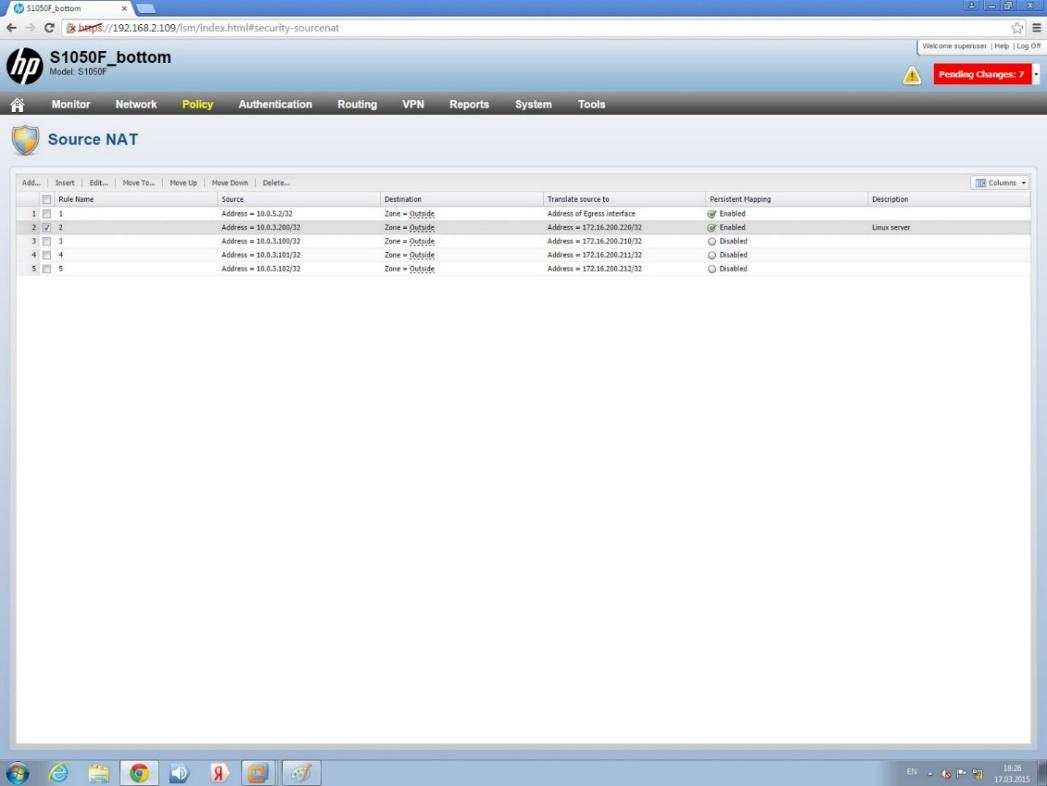
Source NAT
The basic FW Policy settings, according to which the traffic is processed, are shown in Figure 8. In order to check how the default IPS policy is processed, we will pass all traffic through the Static FW base filters transparently.
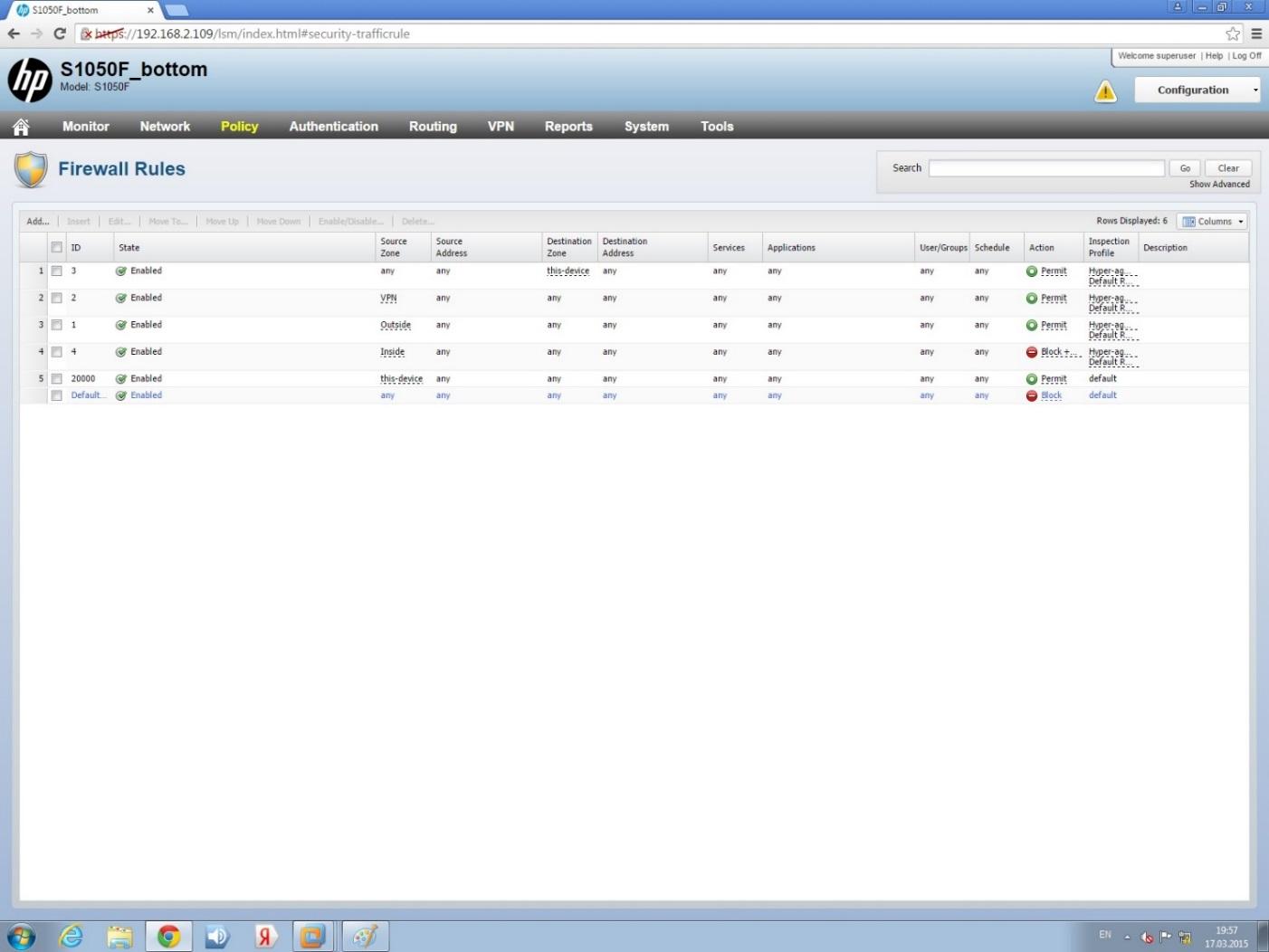
Fw policy
Basic Intrusion Prevention System (IPS) settings. All recommended IPS filtering categories are included in this test.
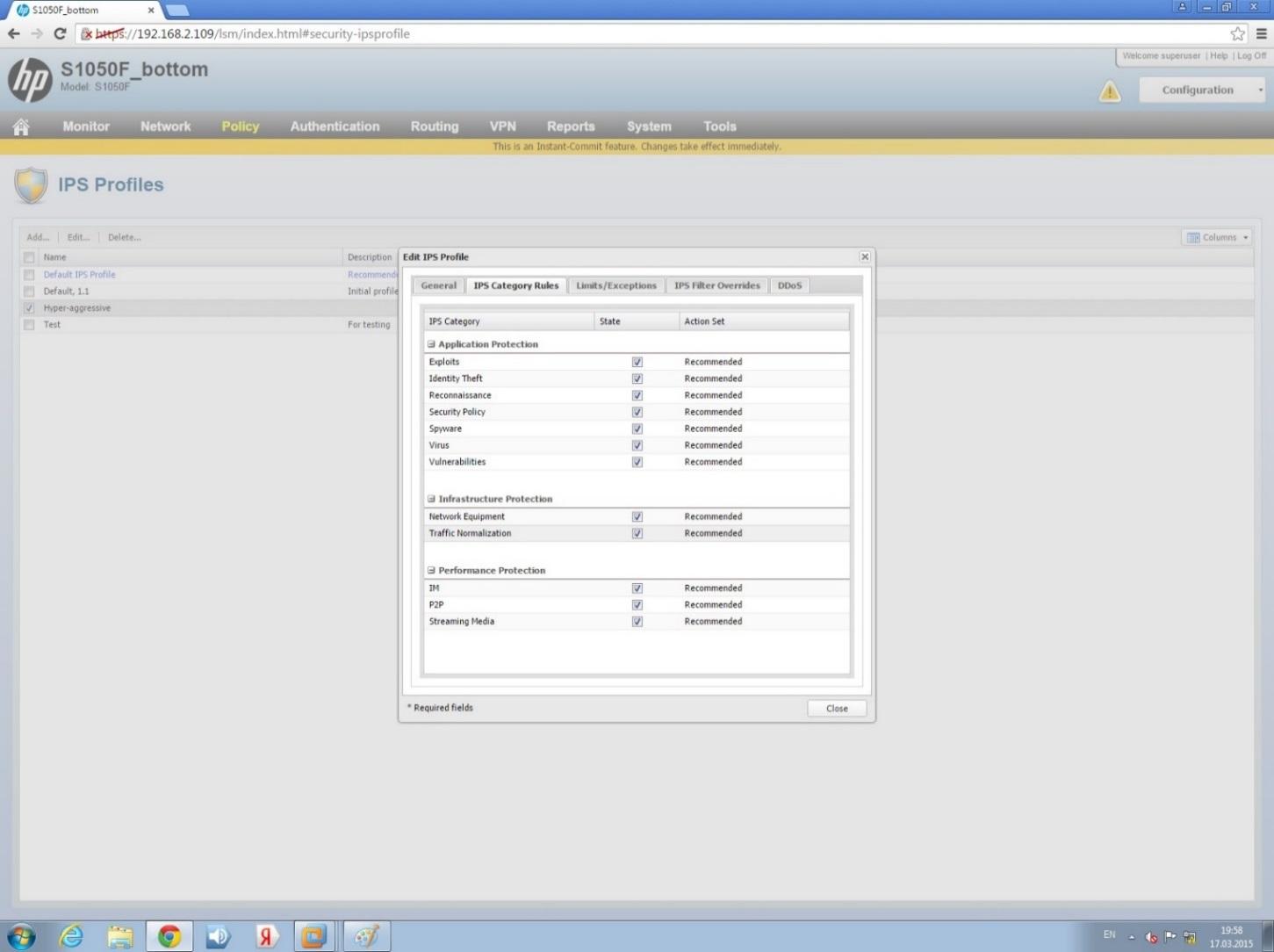
Basic IPS settings
Setting thresholds for DDoS attacks. The threshold of IPS on DDoS attack type SYN FLOOD - 100 packets per second.
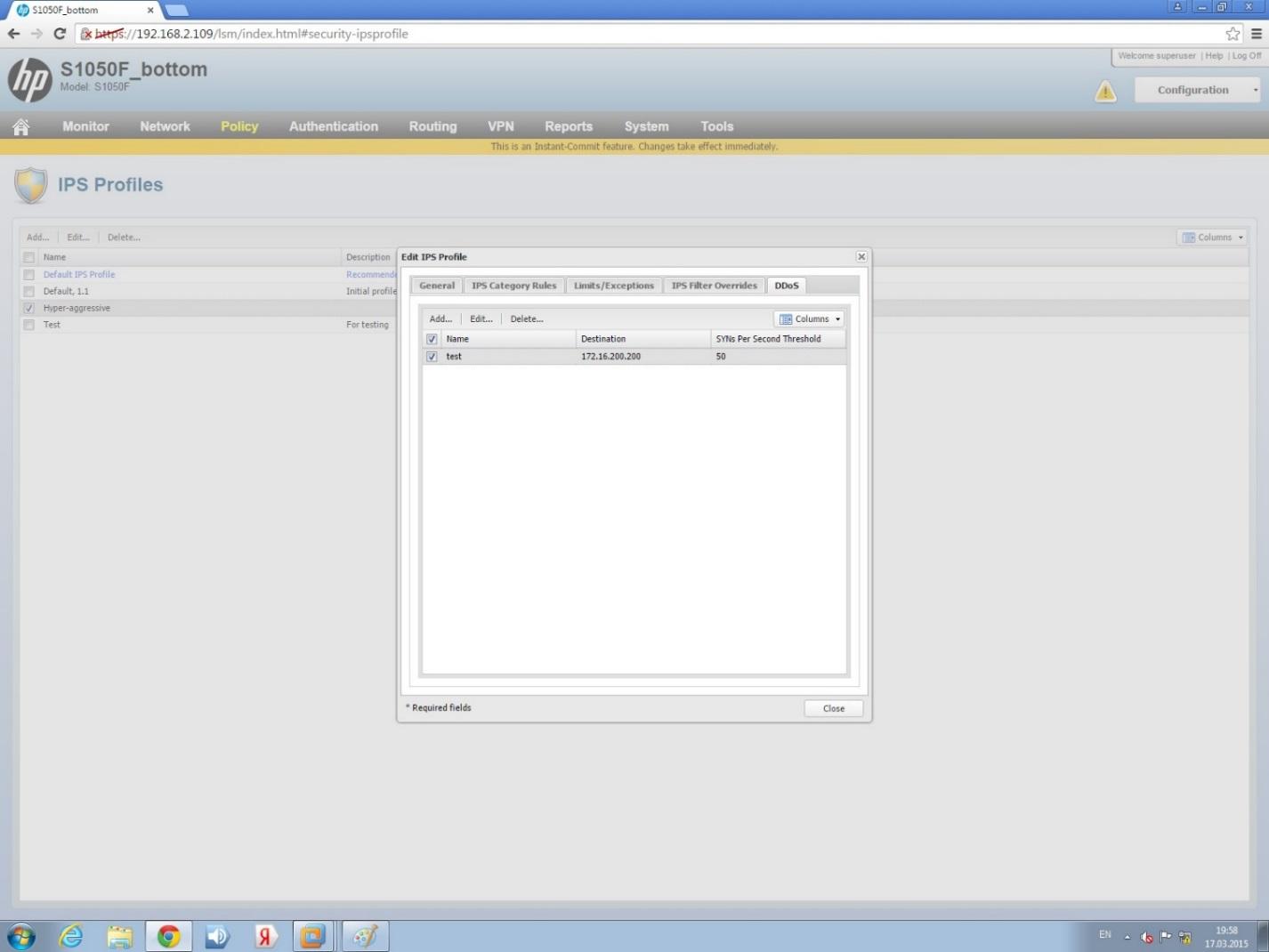
IPS DDoS
We emulate the attack according to the classical scheme given in part 2 of the series and try to defend against the attack with the help of NGFW. At the same time, in a real DDoS attack, filtering by ports / addresses is an ineffective approach, since the infected machines are scattered, as a rule, over the network and have randomly scattered addresses. Therefore, we skip all traffic to IPS and, as shown above, configure the DDoS protection rule in IPS:
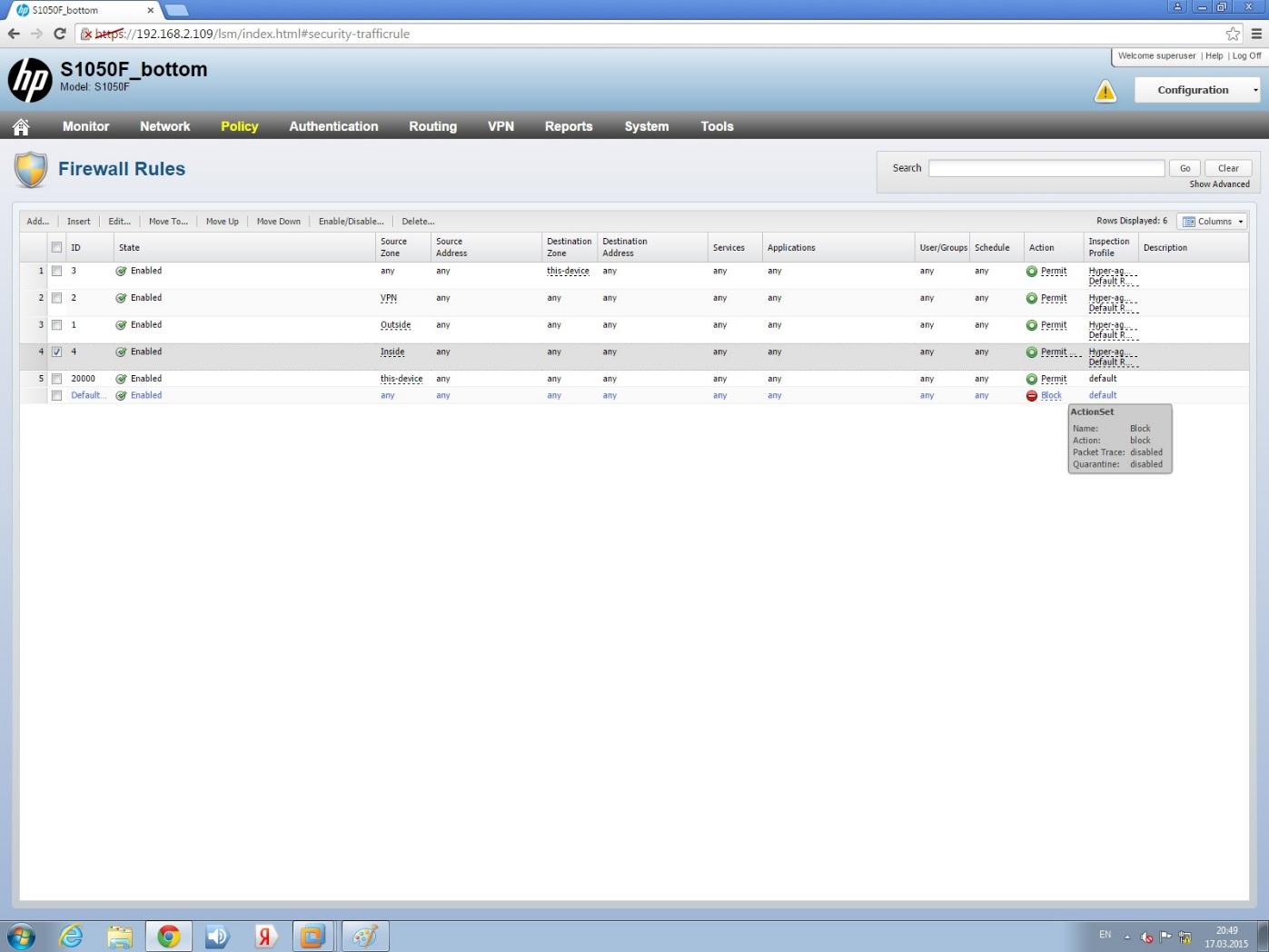
1. To make sure that IPS works, turn off the rule on NGFW, according to which the traffic of the source host of the network attack will be blocked:
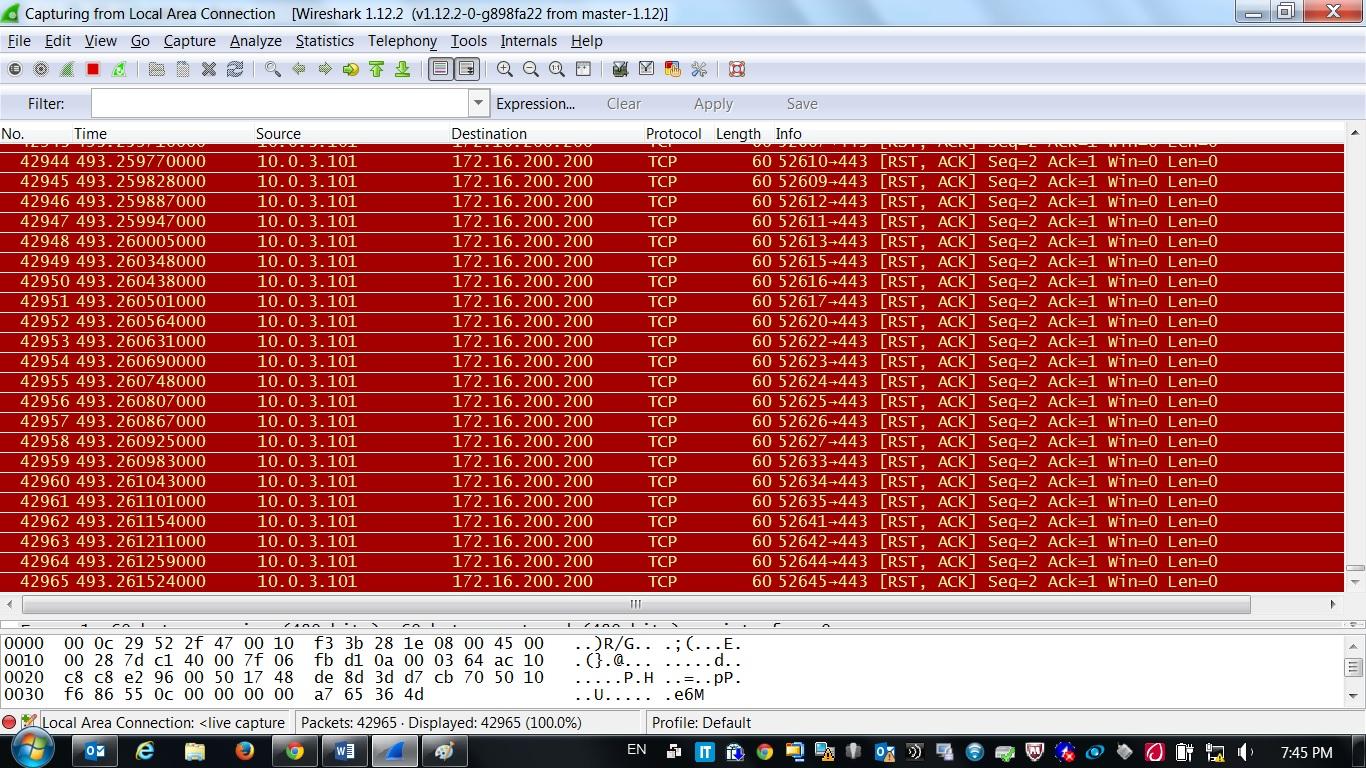
2. Start the network DDoS attack and look at the Wireshark logs and observe the classic DoS attack with the agent-infected virtual machine:
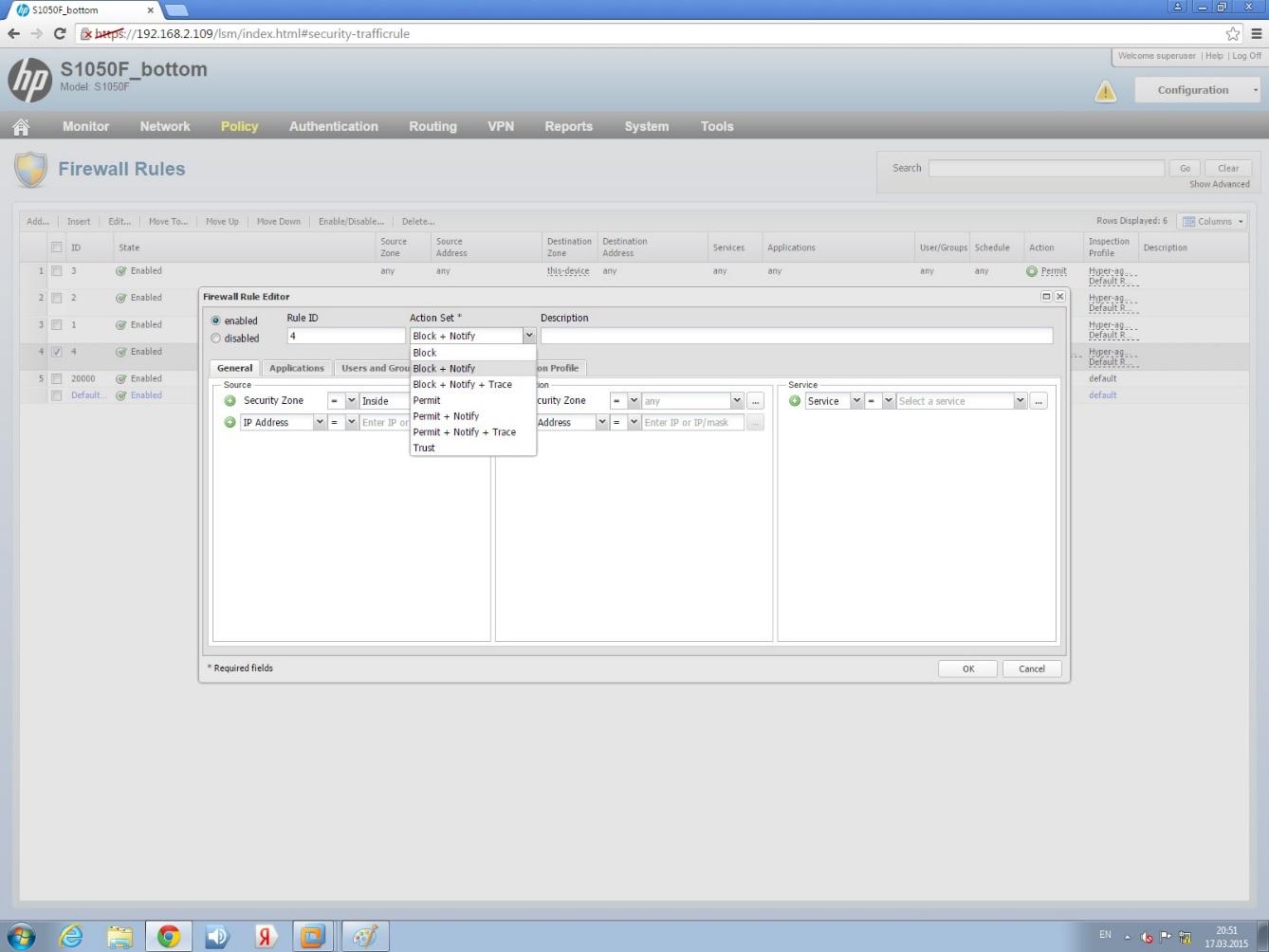
3. We enable a rule on NGFW IPS that blocks the traffic of the host from which the network attack is coming:
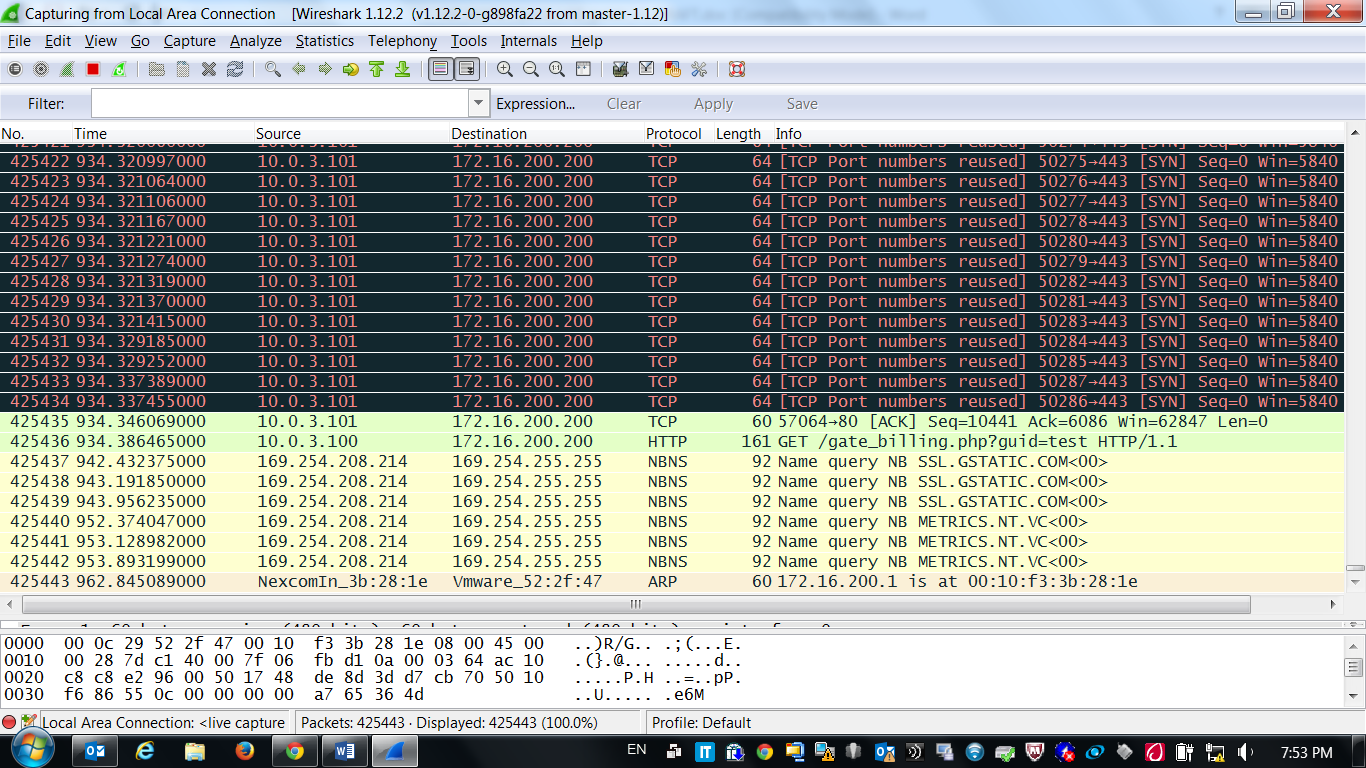
4. We are convinced in the Wireshark logs that the rule worked and the DoS attack was terminated:
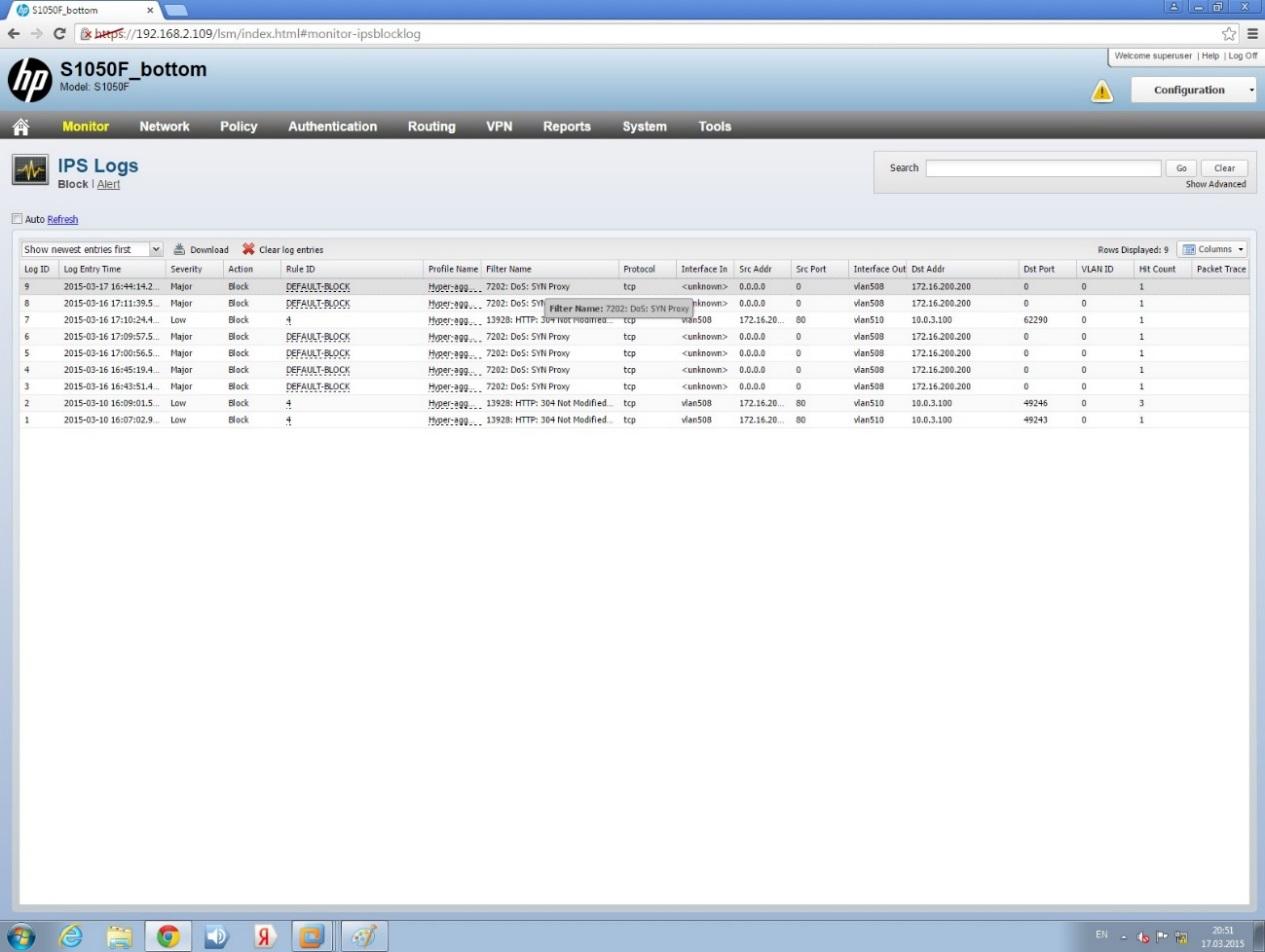
5. We look at the NGFW logs and note that the attack was detected and the traffic from the attacking host is closed:
This example shows how, using rules pre-configured in the NGFW intrusion detection system, classic DDoS attacks are detected and prevented. In conclusion, I would like to say that the functionality of NGFW to repel such threats is not limited to built-in rules (although there are enough rules in NGFW to repel most network threats). NGFW has a functional on writing and implementing its own rules in policies, which allows you to respond flexibly to the morphic threats of information security. But more about that next time.
Below is an example of protection against denial of service attacks using computers infected with malware using HP NGFW . To test this feature of the firewall, a stand was assembled, as shown in the figure below.

Stand layout
The stand consists of three main parts:
')
- VMWare-based virtual environment imitating local network + data center (on the left in the diagram)
- HP NGFW Firewall
- Virtual environment simulating a segment of the Internet (right on the diagram)
A virtual environment that simulates a local network is a virtual machine deployed on a workstation based on the Windows operating system. To simulate the operation of malicious software, a testing agent capable of generating DDoS traffic is installed on a part of virtual machines.
The firewall is installed in the gap between the Internet segment and the local network and at this stand is a third-level device that routes traffic between the segments. The basic rules and firewall settings are shown in the diagram above.
A virtual environment that mimics the Internet segment is a set of virtual machines based on the Linux operating system with specialized software installed on them - among other things, Apache web server, MySQL database server, PHP version 5 interpreter, Nessus security scanner, scan utility nmap network.
Basic Firewall Configuration
Below are the basic settings of NGFW in accordance with the developed stand scheme shown in Figure 3. All settings are shown in the NGFW's own web interface. Figure 4 shows the settings of the IP interfaces of the FW in accordance with the diagram above.

IP interface settings
Below are the security zone settings. For simplicity, the booth has three security zones set up - Inside, Outside and VPN.

Security Zone Settings
Figure 6 shows the basic settings made for Destination NAT. Published several internal addresses of virtual machines that run various network services (HTTP / HTTPS, FTP, etc.).

Destination NAT Settings
The following shows the basic Source NAT settings. Several virtual machine addresses are translated to external addresses in order to provide them access to the emulated malware services.

Source NAT
The basic FW Policy settings, according to which the traffic is processed, are shown in Figure 8. In order to check how the default IPS policy is processed, we will pass all traffic through the Static FW base filters transparently.

Fw policy
Basic Intrusion Prevention System (IPS) settings. All recommended IPS filtering categories are included in this test.

Basic IPS settings
Setting thresholds for DDoS attacks. The threshold of IPS on DDoS attack type SYN FLOOD - 100 packets per second.

IPS DDoS
We emulate the attack according to the classical scheme given in part 2 of the series and try to defend against the attack with the help of NGFW. At the same time, in a real DDoS attack, filtering by ports / addresses is an ineffective approach, since the infected machines are scattered, as a rule, over the network and have randomly scattered addresses. Therefore, we skip all traffic to IPS and, as shown above, configure the DDoS protection rule in IPS:
1. To make sure that IPS works, turn off the rule on NGFW, according to which the traffic of the source host of the network attack will be blocked:

2. Start the network DDoS attack and look at the Wireshark logs and observe the classic DoS attack with the agent-infected virtual machine:

3. We enable a rule on NGFW IPS that blocks the traffic of the host from which the network attack is coming:

4. We are convinced in the Wireshark logs that the rule worked and the DoS attack was terminated:

5. We look at the NGFW logs and note that the attack was detected and the traffic from the attacking host is closed:

This example shows how, using rules pre-configured in the NGFW intrusion detection system, classic DDoS attacks are detected and prevented. In conclusion, I would like to say that the functionality of NGFW to repel such threats is not limited to built-in rules (although there are enough rules in NGFW to repel most network threats). NGFW has a functional on writing and implementing its own rules in policies, which allows you to respond flexibly to the morphic threats of information security. But more about that next time.
Source: https://habr.com/ru/post/264047/
All Articles