Hacker projects on Kickstarter
I was preparing for a course on the withdrawal of the project at Kickstarter and I had to analyze successful projects as a “homework”. (I gasped a bit when I learned that there are 1,250 active crowdfunding platforms in the world.) Since I have a habr defect, I found all the projects in the field of information security (and a couple of projects were suggested by the hackerspace guys).
10% is the share of technology startups at Kickstarter (they eventually collected about 118,000,000 dollars).
Yes, crowdfunding is perfectly sharpened on any useless, but cool crap. Kickstarter collects loot for salad and rubber handles (16 barreled wooden machine gun of the Gatling system), and on other platforms they implement the “rule 34” for space and for the joy of the old Freud type
')
I propose to evaluate the ideas of the projects (the depth of technical descriptions) and the sense of humor of the developers.
Myths and Facts about Kickstarter
I saw with my own eyes how the guys from CubicRobotics updated the page with statistics on IGG every minute. I also helped a little with the draft book about Venus , and now I'm carrying out plans to launch a
Therefore, I wonder what pieces the campaign on Kickstarter consists of. I made a selection of projects using the following examples: work with the media, video quality, game mechanics, visualization of awards and goals, interaction with the community, sense of humor, depth of technical descriptions.
Independent analysis of projects - a powerful thing. For example, there is a myth that only gadgets or desktops are successful at Kickstarter. I found okolokhakerskie projects, tutorials, research, software projects, iron and paper solutions. Or another misconception that the video must be expensive - I witnessed how they spent 10,000 dollars on the set. Examples of IB projects demonstrate that you can shoot video both in the studio and on a webcam.
During the preparation, I was able to talk a bit with “our man” in Silicon Valley, which helps to “hack citizenship restrictions on Kickstarter”, here he is a real myth destroyer and a specialist in cultural codes. Who knows why you can not congratulate the girls on March 8 Kickstarter?
A record holder in the field of information security collected more than $ 700,000, and another project was notable for attracting 1,200 backers (those who "voted with money") in the first 24 hours. Russian activity on Kikstarter is as follows: 15,000 Russians contributed a total of 3,350,000 dollars.
Wednesday is the most active day of the week for Kickstarter users. Date of the month - 13.
I publish an article on Thursday, the 6th, but in the article I use one of the popular game mechanics - “stretch goals”. This is such a thing, borrowed from the games, when after taking the next height, a new nishtyachok opens.
Cybersecurity projects
Cybrary MOOC IT and Cyber Security
 Cybrary : The world's first free MOOC (Multi-user online course) about information technology and cybersecurity. For each. For any level. Is free. Forever and ever.
Cybrary : The world's first free MOOC (Multi-user online course) about information technology and cybersecurity. For each. For any level. Is free. Forever and ever.The Cybrary.IT platform offers free MOOCs for IT specialists. There are now 20 online courses on system and network administration and cybersecurity available for obtaining certification from beginner to advanced levels (Ethical Hacker, CISSP, CCNA, CompTIA A +) and niche skills (deployment of Microsoft Exchange).
The idea of the Cybrary.IT project is to eliminate financial barriers for IT professionals in constantly improving their skills and make the field accessible to talented professionals from low-income segments of the population.
A teacher with a class of 20 students will be able to use additional tools for free, and if you use Cybrary.it for the whole school, you will have to pay from two to ten thousand dollars a year. For this money, it will be possible to follow the progress in passing pupils' material, organize the activities of several teachers at once, and make up complete curricula from the materials of the site.

 Chips: filling in advance with the content of your channel on YouTube , where you can find several demos with teachers.
Chips: filling in advance with the content of your channel on YouTube , where you can find several demos with teachers.The amount collected, continue to be published on hacker resources . On May 29, 2015, the project exceeded 100,000 registered.
Collection - $ 25,803 ($ 25,000)
Start of the project - March 4, 2015
Project site - www.cybrary.it
Kickstarter page
Our Mission:
It becomes a rule, forever.
It’s a real-life challenge.
It is not the case that there is no cost. We have been deserting, at the very least, the opportunity. It’s not a problem.
It’s a real-life challenge.
It is not the case that there is no cost. We have been deserting, at the very least, the opportunity. It’s not a problem.
A video is a simple one shot on an ordinary camera and for some reason it causes confidence, more than a video from Coursera, where sometimes teachers teach their books or services. I even want to learn from the guys, and the course is also free, which is in harmony with the hacker worldview about the dissemination of knowledge and competencies.
Enigmaze - Secure Internet Password Log Book
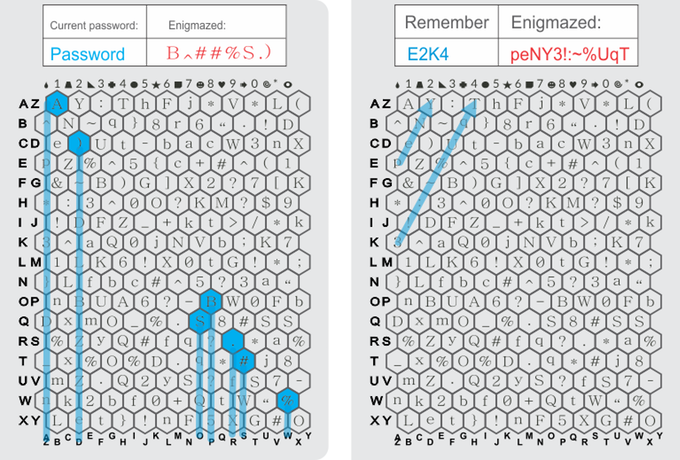
 Enigmaze is a cool notebook specially designed to quickly and easily create and store strong passwords.
Enigmaze is a cool notebook specially designed to quickly and easily create and store strong passwords.A password about “forty thousand monkeys” and their relationship with bananas is easy to remember, but what to do with this xXkleG! 8 + Ke $? Mcd ? Given that these need to have a few dozen for each project.
The authors of the project offer such "Enigma" on paper. It can be used in different ways - from an invisible ultraviolet marker, to mnemofrases, from which a strong password is “output” using a cipher-notebook.
The chip is a great solution, especially for organizations where you can / need to implement strong passwords for all employees. Developers quickly communicate with bakers and even during the campaign, responding to the reviews, added choice options - a notebook without letter-indexing of pages.
mass media

Fees $ 18,927 ($ 3,000)
Start of the project - May 11, 2015
Project site - enigmaze.org
Kickstarter page
Video - Studio
OneRNG - an open source entropy generator
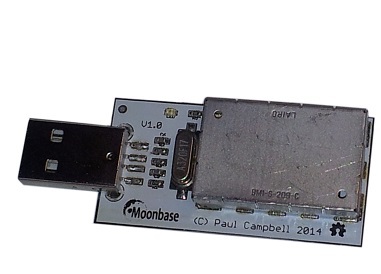 OneRNG is a reliable hardware source of entropy for random number generators.
OneRNG is a reliable hardware source of entropy for random number generators.The device is designed in the form of a keyfob with a USB interface.
All diagrams, specifications, and software are distributed (https://github.com/MoonbaseOtago/) under free licenses and are available for independent auditing and reliability testing. According to the authors of the project, assurances of trust are worth nothing, only complete openness and the provision of self-verification can guarantee the security of the system.
For the formation of random entropy in OneRNG, a circuit based on a Zener diode and a radio frequency hopping receiver are used. For isolation from external interference, electronic components are insulated with a special metal screen.
" Openness is important, we fully disclose the design of our equipment and our firmware, our board is even designed with removable noise protection (" foil cap "), so you can check and make sure that the circuits inside are exactly the same as those that we build and sell. In order to make sure that our boards cannot be compromised during transportation, we make sure that the internal firmware will be signed and cannot be forged.
The board cannot be reprogrammed via USB using malicious software on the host computer. However, we also believe that you do not actually own your equipment if you cannot open it and tinker with it, and, more importantly, you cannot verify that what we promise.
Therefore, we offer the same programmer that we use, plus a cable for an additional fee - we hope that you can do something even more reliable than what we have created. " Paul Campbell
Chips: cool title, sincere video, the solution to the actual problem. They put pressure on the corn that "the NSA hacked some of the random number generators in the OpenSSL software."
Fees - $ 48,551 ($ 10,000)
Start of the project - December 15, 2014
Project site - onerng.info
Kickstarter page
Video is a simple video describing how it works.
tru gikovsky fotochki

Production
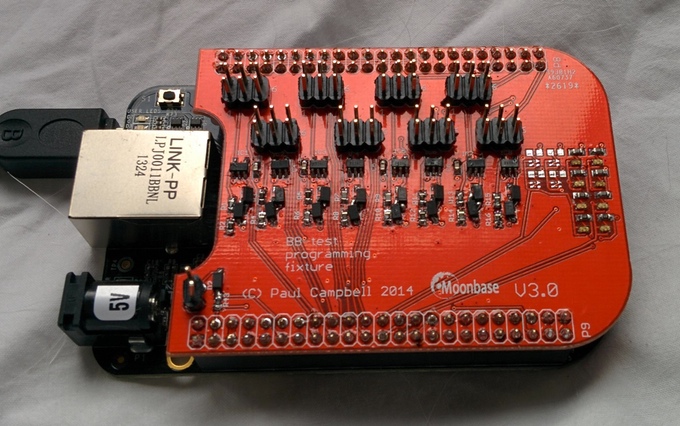
Programmer



Production

Programmer
Big project lecture
JackPair: secure your voice phone calls wiretapping
 JackPair encrypts voices over GSM telephony with protection against man-in-the-middle attacks.
JackPair encrypts voices over GSM telephony with protection against man-in-the-middle attacks.It works with any phones, does not require passwords, does not require installation of any software. Cost $ 89 per device or $ 139 per pair.
All software is open source and open to audit (open source security).
Bruce Schneier claims: " The crypto looks competent, it is well-thought-out. I'd use it. "
Concept: one device connects to the phone, be it a smartphone, a landline phone or a VoIP client on a PC via a standard 3.5mm headphone jack - and then, if the subscriber has a second JackPairs, the devices will establish a secure connection and encrypt the audio signal before sending over any network. The JackPair software uses a synthesized voice to play the decoded audio signal.
For each communication session, a One-Time-Secret-Key (OTSK) is generated, generated using the Diffie-Hellman protocol . For encryption is used stream cipher Salsa20 .
Chips : before launch, the developers have enlisted the support of the popular information security specialist - Bruce Schneier. There is a description and pictures of the main stages of prototyping.
Edward Snowden's revelations (Edward Snowden) showed how vulnerable user data is, especially in the face of state intelligence. The developers used a quote from Snowden as a justification of the need for this device:

Fees - $ 44,661 ($ 35,000)
Start of the project - September 5, 2014
Project site - jackpair.com
Kistarter page
Video - "semi-studio"
mass media

team

visualization of awards

The Glitch: Security / Pen-Testing Hardware Platform
 Hooked up and hacked.
Hooked up and hacked.Glitch makes life easier for Pentester . Now the information security specialist does not have to go into the device and write firmware for it. Glitch is a reprogrammable Open Source Hardware device / platform. Took out of the box and turned it on.
Glitch can emulate keyboard operation and, when connected to a computer, quickly type text (which can be used both for fast configuration of Windows / Linux and for playing some payloads).
The advantage of this device over Teensy and Rubber Ducky is that it can log - that is, it can be connected to a USB keyboard and it will record all keystrokes on the microSD card.
Hacking with hardware for non-hardware hackers
 “I'm JP and I'm a security researcher who loves to tinker. I have a special interest in wireless security and portable security projects. ”
“I'm JP and I'm a security researcher who loves to tinker. I have a special interest in wireless security and portable security projects. ” (“I’m a JP and I’m a security professional who likes to make things. I’m interested in wireless and portable security projects”)
Also due to the small size of the Glitch can be hidden inside other electronics, for example, inside the mouse. To detect such a third-party device will be extremely difficult.

The chip is a cool sticker for those who contributed at least $ 10

The author of the project used the services of the community, they helped him to make a video: “Thanks to gigafide (http://youtube.com/gigafide) for helping me make the video”
Fees - $ 30,137 ($ 14,500)
Start of the project - August 5, 2012
Project site - theglitch.sf.net
Kickstarter project page
Video - home made
Webcloak: Advanced Web Security and Online Privacy
 Webcloak is a small USB device that is a physical shield to work safely on the web. Protects against viruses and data theft. Provides anonymous access.
Webcloak is a small USB device that is a physical shield to work safely on the web. Protects against viruses and data theft. Provides anonymous access.How Does Webcloak Work?
When connected to a computer, Webcloak creates a protected virtual “machine inside the machine”. All data is encrypted (AES) 256. The developers promise users absolute invulnerability and protection of all transactions, payments, protection against viruses and vandalism.
Webcloak blocks any incoming access, and you don’t need to install or reboot anything, protection starts as soon as you plug the device into the computer.

The device protects against "SideJacking" (Wi-Fi hacking), traffic sniffing (Network Traffic Sniffing), DNS Spoofing, Key-loggers and Screen Scrapers, man-in-the-middle attacks, Site Visit Tracking Code, Cryptolocker, as well as all viruses and exploits.
Chips - a lot of video instructions and pictures that explain the principle of operation and use of the device. Detailed description of the development team with live photos.

Command description
Our team has been committed to making it possible for us to work for the last 3 years.
Martin Dawson, Chief Technology Officer:
This is a list of Internet technologies, LearnFlow and Xstream Media. Mr. There is also a multi-media content available on the Internet. He has been pioneered by the web browser.
Mr. Dawson has developed and developed proprietary software for companies such as Microsoft, Intel and Citrix. Additionally, software created by Mr. Dawson has been pre-installed on Dell, Micron and Gateway computers.
“My first“ shrink wrap ”product is“ Quickstudy for Lotus 1-2-3 ”, which included over 60. Complete simulation of the software. If you had 1–2–––––––––––––– –––––––––––––––––––––––––––––––––––– In the early 90s, it was a meeting with a graphical “Web Browser” called Mosaic. I was intrigued and immediately acquired a copy. I couldn’t make it possible to realize the world’s world wide web. I succeeded and “LearnFlow” was born. Audio Multi-media Forms for a common modem connection. When it’s released, we’ve asked for our online demos. This was years before Flash and Shockwave. I didn't stop there ”- Read more ...
Mr. William Shopoff - Chief Executive Officer:
CEO Bill Shopoff has a gift for building, motivating and managing teams to succeed in entrepreneurial ventures. He graduated from Edward W. Deming who emphasized quality control and systems-based business management.
Bill Shopoff has also been instrumental in technology-based projects including co-founding eBridge Technology Ventures I and II. ITV Capital and Voyager Capital, two companies were launched in the late 1990's.

The team
Our team has been committed to making it possible for us to work for the last 3 years.
Martin Dawson, Chief Technology Officer:
This is a list of Internet technologies, LearnFlow and Xstream Media. Mr. There is also a multi-media content available on the Internet. He has been pioneered by the web browser.
Mr. Dawson has developed and developed proprietary software for companies such as Microsoft, Intel and Citrix. Additionally, software created by Mr. Dawson has been pre-installed on Dell, Micron and Gateway computers.
“My first“ shrink wrap ”product is“ Quickstudy for Lotus 1-2-3 ”, which included over 60. Complete simulation of the software. If you had 1–2–––––––––––––– –––––––––––––––––––––––––––––––––––– In the early 90s, it was a meeting with a graphical “Web Browser” called Mosaic. I was intrigued and immediately acquired a copy. I couldn’t make it possible to realize the world’s world wide web. I succeeded and “LearnFlow” was born. Audio Multi-media Forms for a common modem connection. When it’s released, we’ve asked for our online demos. This was years before Flash and Shockwave. I didn't stop there ”- Read more ...
Mr. William Shopoff - Chief Executive Officer:
CEO Bill Shopoff has a gift for building, motivating and managing teams to succeed in entrepreneurial ventures. He graduated from Edward W. Deming who emphasized quality control and systems-based business management.
Bill Shopoff has also been instrumental in technology-based projects including co-founding eBridge Technology Ventures I and II. ITV Capital and Voyager Capital, two companies were launched in the late 1990's.
mass media

Fees - $ 61,215 ($ 60,000)
Start of the project - November 19, 2014
Project website - webcloak.com
Kickstarter page
Video - Studio
Here it is long-awaited
Continued - Gluching, attacks on third-party channels and hacker projects on Kickstarter (continued)
If you know crowdfunding projects in the field of information security , which I missed, share.
tips on analyzing projects from a professional carter maker Evgeny Zhukov , a serial entrepreneur in Silicon Valley, CEO & Founder Digitilus, founder of the accelerator SV Booster
Evgeny Zhukov , a serial entrepreneur in Silicon Valley, CEO & Founder Digitilus, founder of the accelerator SV Booster
I would like to highlight a few important points:
 Evgeny Zhukov , a serial entrepreneur in Silicon Valley, CEO & Founder Digitilus, founder of the accelerator SV Booster
Evgeny Zhukov , a serial entrepreneur in Silicon Valley, CEO & Founder Digitilus, founder of the accelerator SV BoosterI would like to highlight a few important points:
- Iron a priori collects more than software. For example, the same CYBRARY collected, rather, contrary to, and not thanks to the efforts of its authors. This is evident in the schedule of fees
- Flash drives were collected well in past years. Recently, they clearly go out of fashion.
- Spy stuff always attracts attention. Therefore, all kinds of “bugs” will attract more attention than security solutions, especially against online threats. The goals should be simple and clear: “take over the world and not let anyone see their passwords”.
- Not always what seems to be true, everyone lies. If you compare the schedules of fees for Cybrary, JackPair, Webcloak and The Glitch projects, Enigmaze, you can see that the first ones have a broken schedule, with sharp jumps, especially at the end of the campaign, and with a slight excess of a goal (except for JackPair, where they clearly did not calculate forces) sign of boost, i.e. a sharp injection of large amounts for the "successful" completion of the project. The authors clearly realized that if they did not throw some of their money through the cards of friends, they would leave with nothing. The second group of projects has a smooth and organic growth schedule, with a significant excess of the amount of the goal. It means there was a correct work with the press and the correct hit in the expectations of the audience.
- The price of a standard lot is important. Phenomenally high fees at Novena are explained only by the phenomenally high price of prizes. It is obvious that the cost of this project is the highest. In fact, it is necessary to compare the amount of fees with the number of project backers. The second higher, the more successful the project.
- Video. Contrary to steadily retransmitted urban legends about the most advanced availability of high-quality video, as often happens, cause and effect are confused here. High-quality studio video can afford projects that easily can afford to buy a large amount of advertising and participate in numerous exhibitions and conferences. Therefore, I deliberately omit video analysis in all the listed projects. Let me just say that the presence of a video within 2-3 minutes should be normal, in which clearly, in English without an accent, the product itself is told and you can look into the honest eyes of its creators before giving them your money. In addition, in the Enigmaze project at the moment I don’t watch any video at all. And its total amount of fees is comparable to Cybrary and The Glitch, not to mention relative to the initial goal amount.
- For a more accurate analysis, it is necessary to monitor the mention of each project in the press, look at how much the marketing campaign has started before the start of the fees, check for the presence of well-known personalities in the team, and many other factors that directly affect the results of the fees.
- Kicktraq.com Need to take a lot of parameters and sit down to check. Kicktraq should be mastered first of all in order to understand on schedule what is going on behind the scenes. But it is necessary to be able to “read” it - this is the same as the exchange players try to understand the growth / decline trends according to the graphs. There can not be taught, you just have to do it regularly. Then googling is connected on the subject of articles about the project, according to where they wrote and what they wrote, you can try to make a picture about the creators, how long they have been promoting the project and what they had before the start of the campaign at the COP. In general, here reverse engineering, only in terms of investigation.
Competition

Everyone probably has acquaintances who are conducting experiments with cold nuclear fusion in the garage.

Perhaps they want to bring their project to the crowdfunding platform, or maybe they (like proud hedgehogs) should be kicked for this.
Share briefly the essence of the project (in the comments or on the email alexey.stacenko (pack) gmail.com), for our part, being biased and inadequate, we will give two invites for the Kickstarter campaign creation course . One invite to the
Source: https://habr.com/ru/post/263845/
All Articles