New Intercepter-NG 0.9.10 Review
Intro
With great pleasure I want to present a new version of Intercepter-NG 0.9.10, which, in my opinion, greatly expands the scope of the tool. This review will not be presented as a dry listing of innovations, but rather as a description of new attack vectors, along with a number of technical details and hack-story elements. Let's start ...

')
Network scan
As always, a lot of fixes and minor improvements have been made that it makes no sense to list.
Who often uses the tool knows that one of the main modes is the network scanning mode and, in particular, the smart scan function. To the already familiar information about IP and MAC addresses, the manufacturer of the network card and the operating system, added the output of the computer name.
For the same period of time, you can now additionally find out the Netbios name or the name of the device running the iOS.
For the resolution of the latter, the MDNS protocol is used, on the basis of which Apple's Bonjour protocol works. All received names are now stored in a cache file and if subsequent scans for any reason did not dynamically retrieve the host name information, it will be taken from the cache. Here you can mention the appearance of the function Auto ARP Poison, which is included in the expert settings. In automatic mode, it is enough to add only 1 host to the list of targets, and Intercepter will scan the network itself at a certain interval and automatically add new targets.
Bruteforce Mode
In this mode, added support for TLS for SMTP and POP3 protocols, as well as brute force TELNET authorization.
Now, when a timeout occurs, the active thread is restarted from the same place and the iteration process continues.
A Single Mode has appeared, which indicates that each new L \ P pair should be checked with the establishment of a new connection, for some protocols this allows an increase in the speed of work. The log of work is saved in brute.txt.
Traffic changer
More than once there were requests to implement the function of traffic spoofing and they were not ignored, but one should not rejoice before time.
On the counter question: “why exactly do you need this opportunity?” Some users found it difficult to answer or said that for the sake of a joke to change words in web traffic. And in order not to explain to every joker why the result does not always meet expectations, you can substitute data of only equal size without changing the length of the packets. The restriction is not at all connected with the problems of technical implementation; there are no difficulties to split ethernet frames with recalculation of the corresponding tcp fields. Everything rests on the application protocols. Consider the example of HTTP.
Suppose the browser opens site.com/file.txt, which contains the string "12345". In response to a GET request, the server will return an HTTP header containing the length of the transmitted data - Content-length: 5. What will happen if we replace “12345” with “12356”? The browser downloads only 5 bytes, discarding the added “6”, and if we reduce the size of the data, replacing “12345” with “1234”, the browser will receive only 4 bytes and wait for another 1 byte from the server until the connection breaks down. timeout That is why this size limit has been made. You can change both textual and binary data, the syntax for binary patterns as in C - "\ x01 \ x02 \ x03".
If substitution is required in HTTP traffic, then the “Disable HTTP gzip encoding” option must be enabled in the settings.
HSTS Spoofing
As promised, the HSTS bypass appeared during the SSL Strip. The bypass technique is relatively simple, but it is in the implementation that there are certain difficulties, so you should not expect any special results. Consider the example of Yandex Mail using the Chrome browser. If you go to ya.ru , then in the upper right corner there will be an https link “Log in to mail”, with which the SSL Strip is easy to handle. Next, the authorization form will open, where the POST method transfers data to passport.yandex.ru . Even “stripping” https authorization will happen over SSL, because host passport.yandex.ru is listed on the preloaded chrome list. In order to still capture the data, we need to replace the host name passport.yandex.ru with something else, so that the browser does not find that this resource should be visited strictly over a secure connection. For example, you can replace passport.yandex.ru with paszport.yandex.ru, in this case, the data will be sent in plain text to the changed domain name. But since there is no such domain - paszport.yandex.ru, then DNS Spoofing is additionally required, i.e. When resolving paszport.yandex.ru, the client should receive in response the original ip address from passport.yandex.ru. This procedure is automated and does not require additional user intervention during the attack. The only thing that needs to be done is to make a list of replacements in misc \ hsts.txt. By default, there are several entries for yandex, gmail, facebook, yahoo. It is important to understand that this circumvention technique will not allow intercepting a session or authorization if the user enters facebook.com in the browser, since the browser will immediately open a secure version of the site. In this case, the attack is possible only if the link to facebook.com is taken from another resource, for example, when entering facebook on google.com . Among the main problems in the implementation of the attack, we can note the unpredictable logic of the work of sites with their subdomains and features of the web code that can negate any attempts
HSTS bypass. That is why you should not add any sites to the list, even the domains present in the Intercepter-NG have their own characteristics by default and do not work correctly at all times. I don’t want to cram down crutches for each resource, perhaps some universal improvements will be made in the future, but for now, as they say, as is.
Another caveat, in the current implementation, for DNS Spoofing, it is necessary that the DNS server is not located on the local network so that it is possible to see dns requests to the gateway and respond to them as needed.
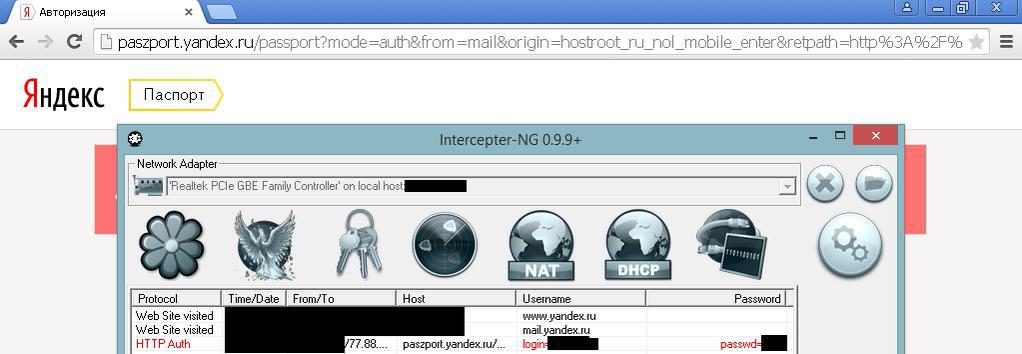
It is important to note that in the new version the work of the SSL Strip itself is noticeably improved.
Forced Download and JS Inject
Both innovations are related to HTTP Injection. In Russian, Forced Download can be translated as “forced download”, because this is exactly what happens on the target side during web surfing. When entering the site, it is proposed to download the file specified by the attacking file, depending on the browser settings, it can download itself, and the user will already choose whether to launch it or not.
As you understand, you can add an .exe file with arbitrary content to the forced download, and the source of this file will be the site that the user is currently visiting. Knowing that the target is about to open adobe.com, you can issue flashplayer.exe, and adobe.com or one of its subdomains will be specified as the source of this file.
After a one-time issue, the boost is disabled, to re-inject, you need to click on the appropriate checkbox again.
JS Inject is not explicitly present among the controls, since in fact, this is the most common http inject, but with one difference. When replacing one file with another, for example .jpg images with a given one, it is the replacement of one content by another. Replacing the .js script is likely to disrupt the resource, so in the new version js inject does not replace one script with another, but appends it to the existing one, adding the ability to inject additional code without affecting the original one.
SSL MiTM
We smoothly approach the most interesting novelties. The new version has been completely rewritten code for SSL MiTM. Now it is fast and stable. The algorithm for generating certificates has also changed, additional dns records have been added to them and all certificates are signed with a single key (misc \ server). This means that by adding this self-signed certificate to the list of targets trusted on the computer, you can listen to SSL traffic to any resource (where there is no SSL Pinning). Cookie Killer now works for SSL connections. Black (misc \ ssl_bl.txt) and white lists (misc \ ssl_wl.txt) have appeared. They can exclude or, on the contrary, strictly indicate IP addresses or domains to which SSL MiTM should or should not be used. When specifying the extra ssl port, it is no longer necessary to specify the type read \ write, it is enough to specify the port number. All traffic is written to ssl_log.txt.
Group policy hijacking
Another killer-feature in Intercepter-NG. Despite the fact that the technique is not open to me at all, this is the first public and fully functional implementation of this attack. A detailed description is available here and here .
Once again, SMB put a pig in Microsoft, because thanks to this vulnerability, in about an hour and a half, you can get access to any computer in the domain (except the domain controller). What is the essence.
Every 90+ random number from 0 to 30 minutes, the member domain requests group policies with DC. This happens via SMB, by opening the network address \\ DC \ SYSVOL \ domain.name \ Policies \ UUID \ gpt.ini.
The contents of this file are as follows:
[General]
Version = 12345
This number is a relative version of the current group policies. If the version has not changed since the last update, the process of receiving group policies is terminated, but if the version is different, it means that they need to be updated. At this stage, the client requests from the domain active CSE (client-side extensions), which include various logon scripts, tasks for the scheduler, and so on. Naturally, an attacker, standing in the middle, can replace one of the tasks that is generated by the controller as a file. In this situation, operation would be quite simple, but all these CSEs are disabled by default and the only thing you can do is modify the registry, because when updating group policies, the client requests another file, GptTmpl.inf, through which you can add or delete an entry. The authors of both articles decided to use the well-known method AppInit_Dll to demonstrate the execution of the code. They registered their dll from the network path into the necessary registry key, after which the newly created process in the system executed arbitrary code. But this method is only suitable as a proof of concept, because AppInit_Dll has been disabled by default for many years. In this regard, the task was to find another way to remotely execute the code, and without having to wait for the reboot, as in the case of adding autorun to the Run key.
To no avail, many attempts were made in one way or another to achieve the desired, until one good person (thx man) suggested a very curious registry key about which I did not know anything before.
In the [HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows NT \ currentversion \ image file execution options] key, you can set a debugger for any .exe file. For example, specify that calc.exe must be opened via c: \ path \ debuger.exe and as soon as the calculator is launched, the debugger will first open, in the command line of which there will be a path to calc. This seemed almost a ready-made solution, because we managed to execute the code without rebooting, albeit under certain conditions. At that time, I was satisfied with the restriction on the inevitability of user participation in the process of gaining access, i.e. instead of a calculator, you could execute code through a call to IE or Chrome or any other application, but a new problem appeared. If the attacked user did not have administrative rights, even after receiving the shell there was no possibility to delete the debugger that was previously added to the registry, which means that after the attack was stopped or when it was restarted, the application in use stopped working, because the network address with debuger.exe no longer existed.
It was necessary to find a way to get not just shell access, but always with administrator rights. Omitting all subsequent difficulties I will describe the result. After receiving group policies, the system should apply them, for this svchost is called and creates a new process taskhost.exe with SYSTEM rights. Having risen as a debugger for taskhost.exe, two hares were killed at once - we did not just receive the shell with SYSTEM rights, but received it immediately, without any manual intervention from the user. The attack is fully automated, you can select a group of targets at once and within one and a half to two hours get a whole set of active shell sessions with maximum rights. For this, it is not even necessary to be a member of the domain itself. The only thing that is needed is to enable Network access. When testing, in order not to wait an hour and a half, it is enough to run gpupdate from the console. Tested on patched Windows 7 \ 8.1 in domains with 2008R2 \ 2012R2 servers.
What are the protection measures? Microsoft released a patch for MS15-011, introducing the so-called UNC Hardened Access, which requires manual configuration. An interesting phrase is present in the newsletter:
"If you’re working with administrative user rights."
As it became clear, the threat is equally high for any user.
Despite the full potential of GP Hijacking, I think that another innovation of this release deserves special attention ...
Dessert
That which will be discussed at the end cannot be called a new function. Rather, it is an attack vector that opens when sharing a number of already existing solutions in Intercepter-NG.
The focus in this case is on wireless networks and mobile devices, in particular, on iOS - Iphones and Ipad's. Everyone knows that the elementary arp poison of these devices gives almost nothing. Interception of cookies from open sites in the browser is probably the only thing that can be counted on, since In most cases, the user works through proprietary applications from various services, where communication with the server takes place over SSL. Even if you try to use MiTM SSL, it will not work, applications will simply stop working with an untrusted certificate. Therefore, it is believed that phones and tablets are fairly well protected from network interception by default.
But imagine the following situation, the average user sits in the Instagram application and views the tape.
Suddenly, the application stops working, complaining about the lack of connection and the user opens instagram.com in the browser, where an alert pops up with the text “To continue working on instagram.com, install a new security certificate” and after closing the message, the screen prompts you to install a new certificate. The further development of events certainly depends on the user, but the likelihood that he will install the proposed certificate is high enough, because the situation is quite plausible: the application stopped working, went to the site, saw a warning about the required update, updated - everything worked, although the attacker substituted his certificate and now reads all SSL traffic. The implementation of Forced Download, JS Inject, and stable SSL MiTM allow implementing a similar scenario in two accounts:
1. We do .js inject with the introduction of alert ('Please install new certificate for% domain%.');
In the template% domain% will be substituted the name of the site on which the injection occurred.
2. We force downloading misc \ server.crt - root certificate in Intercepter-NG.
3. Turn on SSL MiTM (as well as ssl strip for injecting).
4. After the launch of the attack, the SSL connection will stop working on the target device, and an alert with a certificate will be issued in the browser.
A natural question arises: what to do with SSL traffic, except for passive interception of already established sessions. Cookie Killer comes to the rescue, which works fine, for example, on the Facebook application.
IOS has its own holy grail - iCloud, but resetting the cookie does not help to reset its session. It is for iCloud, as well as Instagram and VK, the iOS Killer function was added, which resets the sessions of the specified applications and allows you to intercept the re-authorization. Such a focus can not be done with the AppStore, because there seems to be SSL pinning. This vector was tested on IOS 5 \ 6 and 8.4.
Outro
The plans were to add the ability to independently create handlers on the LUA or through the DLL plugin, but judging by the reaction of users, no one has any real interest. The new version will most likely be next year, possibly in the fall a functional update for Intercepter-NG for Android will be released. Questions, feedback, feature requests are always welcome. That's all.
Demonstration of new features presented in the video.
Project contacts:
Website: sniff.su
Email: intercepter.mail@gmail.com
Blog: intercepter-ng.blogspot.ru
Twitter: twitter.com/IntercepterNG
The information is provided for informational purposes only; the author is not responsible for the consequences of the use of this material.
With great pleasure I want to present a new version of Intercepter-NG 0.9.10, which, in my opinion, greatly expands the scope of the tool. This review will not be presented as a dry listing of innovations, but rather as a description of new attack vectors, along with a number of technical details and hack-story elements. Let's start ...

')
Network scan
As always, a lot of fixes and minor improvements have been made that it makes no sense to list.
Who often uses the tool knows that one of the main modes is the network scanning mode and, in particular, the smart scan function. To the already familiar information about IP and MAC addresses, the manufacturer of the network card and the operating system, added the output of the computer name.
For the same period of time, you can now additionally find out the Netbios name or the name of the device running the iOS.
For the resolution of the latter, the MDNS protocol is used, on the basis of which Apple's Bonjour protocol works. All received names are now stored in a cache file and if subsequent scans for any reason did not dynamically retrieve the host name information, it will be taken from the cache. Here you can mention the appearance of the function Auto ARP Poison, which is included in the expert settings. In automatic mode, it is enough to add only 1 host to the list of targets, and Intercepter will scan the network itself at a certain interval and automatically add new targets.
Bruteforce Mode
In this mode, added support for TLS for SMTP and POP3 protocols, as well as brute force TELNET authorization.
Now, when a timeout occurs, the active thread is restarted from the same place and the iteration process continues.
A Single Mode has appeared, which indicates that each new L \ P pair should be checked with the establishment of a new connection, for some protocols this allows an increase in the speed of work. The log of work is saved in brute.txt.
Traffic changer
More than once there were requests to implement the function of traffic spoofing and they were not ignored, but one should not rejoice before time.
On the counter question: “why exactly do you need this opportunity?” Some users found it difficult to answer or said that for the sake of a joke to change words in web traffic. And in order not to explain to every joker why the result does not always meet expectations, you can substitute data of only equal size without changing the length of the packets. The restriction is not at all connected with the problems of technical implementation; there are no difficulties to split ethernet frames with recalculation of the corresponding tcp fields. Everything rests on the application protocols. Consider the example of HTTP.
Suppose the browser opens site.com/file.txt, which contains the string "12345". In response to a GET request, the server will return an HTTP header containing the length of the transmitted data - Content-length: 5. What will happen if we replace “12345” with “12356”? The browser downloads only 5 bytes, discarding the added “6”, and if we reduce the size of the data, replacing “12345” with “1234”, the browser will receive only 4 bytes and wait for another 1 byte from the server until the connection breaks down. timeout That is why this size limit has been made. You can change both textual and binary data, the syntax for binary patterns as in C - "\ x01 \ x02 \ x03".
If substitution is required in HTTP traffic, then the “Disable HTTP gzip encoding” option must be enabled in the settings.
HSTS Spoofing
As promised, the HSTS bypass appeared during the SSL Strip. The bypass technique is relatively simple, but it is in the implementation that there are certain difficulties, so you should not expect any special results. Consider the example of Yandex Mail using the Chrome browser. If you go to ya.ru , then in the upper right corner there will be an https link “Log in to mail”, with which the SSL Strip is easy to handle. Next, the authorization form will open, where the POST method transfers data to passport.yandex.ru . Even “stripping” https authorization will happen over SSL, because host passport.yandex.ru is listed on the preloaded chrome list. In order to still capture the data, we need to replace the host name passport.yandex.ru with something else, so that the browser does not find that this resource should be visited strictly over a secure connection. For example, you can replace passport.yandex.ru with paszport.yandex.ru, in this case, the data will be sent in plain text to the changed domain name. But since there is no such domain - paszport.yandex.ru, then DNS Spoofing is additionally required, i.e. When resolving paszport.yandex.ru, the client should receive in response the original ip address from passport.yandex.ru. This procedure is automated and does not require additional user intervention during the attack. The only thing that needs to be done is to make a list of replacements in misc \ hsts.txt. By default, there are several entries for yandex, gmail, facebook, yahoo. It is important to understand that this circumvention technique will not allow intercepting a session or authorization if the user enters facebook.com in the browser, since the browser will immediately open a secure version of the site. In this case, the attack is possible only if the link to facebook.com is taken from another resource, for example, when entering facebook on google.com . Among the main problems in the implementation of the attack, we can note the unpredictable logic of the work of sites with their subdomains and features of the web code that can negate any attempts
HSTS bypass. That is why you should not add any sites to the list, even the domains present in the Intercepter-NG have their own characteristics by default and do not work correctly at all times. I don’t want to cram down crutches for each resource, perhaps some universal improvements will be made in the future, but for now, as they say, as is.
Another caveat, in the current implementation, for DNS Spoofing, it is necessary that the DNS server is not located on the local network so that it is possible to see dns requests to the gateway and respond to them as needed.

It is important to note that in the new version the work of the SSL Strip itself is noticeably improved.
Forced Download and JS Inject
Both innovations are related to HTTP Injection. In Russian, Forced Download can be translated as “forced download”, because this is exactly what happens on the target side during web surfing. When entering the site, it is proposed to download the file specified by the attacking file, depending on the browser settings, it can download itself, and the user will already choose whether to launch it or not.
As you understand, you can add an .exe file with arbitrary content to the forced download, and the source of this file will be the site that the user is currently visiting. Knowing that the target is about to open adobe.com, you can issue flashplayer.exe, and adobe.com or one of its subdomains will be specified as the source of this file.
After a one-time issue, the boost is disabled, to re-inject, you need to click on the appropriate checkbox again.
JS Inject is not explicitly present among the controls, since in fact, this is the most common http inject, but with one difference. When replacing one file with another, for example .jpg images with a given one, it is the replacement of one content by another. Replacing the .js script is likely to disrupt the resource, so in the new version js inject does not replace one script with another, but appends it to the existing one, adding the ability to inject additional code without affecting the original one.
SSL MiTM
We smoothly approach the most interesting novelties. The new version has been completely rewritten code for SSL MiTM. Now it is fast and stable. The algorithm for generating certificates has also changed, additional dns records have been added to them and all certificates are signed with a single key (misc \ server). This means that by adding this self-signed certificate to the list of targets trusted on the computer, you can listen to SSL traffic to any resource (where there is no SSL Pinning). Cookie Killer now works for SSL connections. Black (misc \ ssl_bl.txt) and white lists (misc \ ssl_wl.txt) have appeared. They can exclude or, on the contrary, strictly indicate IP addresses or domains to which SSL MiTM should or should not be used. When specifying the extra ssl port, it is no longer necessary to specify the type read \ write, it is enough to specify the port number. All traffic is written to ssl_log.txt.
Group policy hijacking
Another killer-feature in Intercepter-NG. Despite the fact that the technique is not open to me at all, this is the first public and fully functional implementation of this attack. A detailed description is available here and here .
Once again, SMB put a pig in Microsoft, because thanks to this vulnerability, in about an hour and a half, you can get access to any computer in the domain (except the domain controller). What is the essence.
Every 90+ random number from 0 to 30 minutes, the member domain requests group policies with DC. This happens via SMB, by opening the network address \\ DC \ SYSVOL \ domain.name \ Policies \ UUID \ gpt.ini.
The contents of this file are as follows:
[General]
Version = 12345
This number is a relative version of the current group policies. If the version has not changed since the last update, the process of receiving group policies is terminated, but if the version is different, it means that they need to be updated. At this stage, the client requests from the domain active CSE (client-side extensions), which include various logon scripts, tasks for the scheduler, and so on. Naturally, an attacker, standing in the middle, can replace one of the tasks that is generated by the controller as a file. In this situation, operation would be quite simple, but all these CSEs are disabled by default and the only thing you can do is modify the registry, because when updating group policies, the client requests another file, GptTmpl.inf, through which you can add or delete an entry. The authors of both articles decided to use the well-known method AppInit_Dll to demonstrate the execution of the code. They registered their dll from the network path into the necessary registry key, after which the newly created process in the system executed arbitrary code. But this method is only suitable as a proof of concept, because AppInit_Dll has been disabled by default for many years. In this regard, the task was to find another way to remotely execute the code, and without having to wait for the reboot, as in the case of adding autorun to the Run key.
To no avail, many attempts were made in one way or another to achieve the desired, until one good person (thx man) suggested a very curious registry key about which I did not know anything before.
In the [HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows NT \ currentversion \ image file execution options] key, you can set a debugger for any .exe file. For example, specify that calc.exe must be opened via c: \ path \ debuger.exe and as soon as the calculator is launched, the debugger will first open, in the command line of which there will be a path to calc. This seemed almost a ready-made solution, because we managed to execute the code without rebooting, albeit under certain conditions. At that time, I was satisfied with the restriction on the inevitability of user participation in the process of gaining access, i.e. instead of a calculator, you could execute code through a call to IE or Chrome or any other application, but a new problem appeared. If the attacked user did not have administrative rights, even after receiving the shell there was no possibility to delete the debugger that was previously added to the registry, which means that after the attack was stopped or when it was restarted, the application in use stopped working, because the network address with debuger.exe no longer existed.
It was necessary to find a way to get not just shell access, but always with administrator rights. Omitting all subsequent difficulties I will describe the result. After receiving group policies, the system should apply them, for this svchost is called and creates a new process taskhost.exe with SYSTEM rights. Having risen as a debugger for taskhost.exe, two hares were killed at once - we did not just receive the shell with SYSTEM rights, but received it immediately, without any manual intervention from the user. The attack is fully automated, you can select a group of targets at once and within one and a half to two hours get a whole set of active shell sessions with maximum rights. For this, it is not even necessary to be a member of the domain itself. The only thing that is needed is to enable Network access. When testing, in order not to wait an hour and a half, it is enough to run gpupdate from the console. Tested on patched Windows 7 \ 8.1 in domains with 2008R2 \ 2012R2 servers.
What are the protection measures? Microsoft released a patch for MS15-011, introducing the so-called UNC Hardened Access, which requires manual configuration. An interesting phrase is present in the newsletter:
"If you’re working with administrative user rights."
As it became clear, the threat is equally high for any user.
Despite the full potential of GP Hijacking, I think that another innovation of this release deserves special attention ...
Dessert
That which will be discussed at the end cannot be called a new function. Rather, it is an attack vector that opens when sharing a number of already existing solutions in Intercepter-NG.
The focus in this case is on wireless networks and mobile devices, in particular, on iOS - Iphones and Ipad's. Everyone knows that the elementary arp poison of these devices gives almost nothing. Interception of cookies from open sites in the browser is probably the only thing that can be counted on, since In most cases, the user works through proprietary applications from various services, where communication with the server takes place over SSL. Even if you try to use MiTM SSL, it will not work, applications will simply stop working with an untrusted certificate. Therefore, it is believed that phones and tablets are fairly well protected from network interception by default.
But imagine the following situation, the average user sits in the Instagram application and views the tape.
Suddenly, the application stops working, complaining about the lack of connection and the user opens instagram.com in the browser, where an alert pops up with the text “To continue working on instagram.com, install a new security certificate” and after closing the message, the screen prompts you to install a new certificate. The further development of events certainly depends on the user, but the likelihood that he will install the proposed certificate is high enough, because the situation is quite plausible: the application stopped working, went to the site, saw a warning about the required update, updated - everything worked, although the attacker substituted his certificate and now reads all SSL traffic. The implementation of Forced Download, JS Inject, and stable SSL MiTM allow implementing a similar scenario in two accounts:
1. We do .js inject with the introduction of alert ('Please install new certificate for% domain%.');
In the template% domain% will be substituted the name of the site on which the injection occurred.
2. We force downloading misc \ server.crt - root certificate in Intercepter-NG.
3. Turn on SSL MiTM (as well as ssl strip for injecting).
4. After the launch of the attack, the SSL connection will stop working on the target device, and an alert with a certificate will be issued in the browser.
A natural question arises: what to do with SSL traffic, except for passive interception of already established sessions. Cookie Killer comes to the rescue, which works fine, for example, on the Facebook application.
IOS has its own holy grail - iCloud, but resetting the cookie does not help to reset its session. It is for iCloud, as well as Instagram and VK, the iOS Killer function was added, which resets the sessions of the specified applications and allows you to intercept the re-authorization. Such a focus can not be done with the AppStore, because there seems to be SSL pinning. This vector was tested on IOS 5 \ 6 and 8.4.
Outro
The plans were to add the ability to independently create handlers on the LUA or through the DLL plugin, but judging by the reaction of users, no one has any real interest. The new version will most likely be next year, possibly in the fall a functional update for Intercepter-NG for Android will be released. Questions, feedback, feature requests are always welcome. That's all.
Demonstration of new features presented in the video.
Project contacts:
Website: sniff.su
Email: intercepter.mail@gmail.com
Blog: intercepter-ng.blogspot.ru
Twitter: twitter.com/IntercepterNG
The information is provided for informational purposes only; the author is not responsible for the consequences of the use of this material.
Source: https://habr.com/ru/post/263789/
All Articles