How to turn the network itself into a complete security system?
Many enterprises are still building their protection system based on the already outdated perimeter approach, concentrating all the security features in one or two network control points, completely forgetting about the presence of bypass channels - Wi-Fi, flash drives, 4G, ActiveSync, etc. And about the internal violator, which is already inside the network and can perform its “black deed”, without being afraid of being detected by perimeter means of protection, many also forget. What to do in this situation?
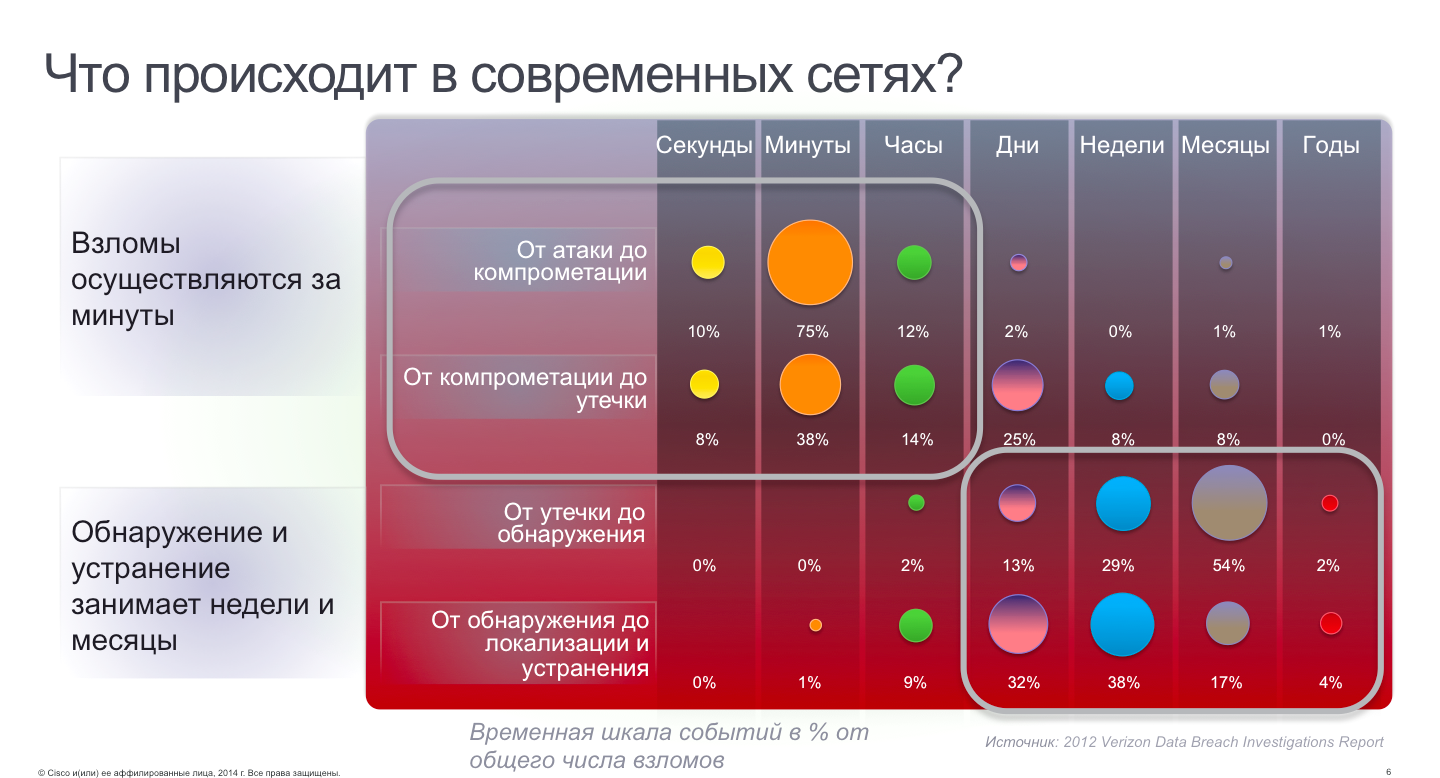
There are three options. The first is to build another one in the internal network, but already a superimposed network of security tools? I think any security vendor will be happy to prepare a proposal for this option, including many IPS sensors and firewalls, which will monitor and control internal network traffic and detect malicious code and unauthorized applications. But this option poses a number of difficulties. First, the not always existing network design allows such a connection to be realized. The network operates at speeds that are not subject to protection, the span ports for connecting IDS are already taken, the enterprise actively uses virtualization, and the protection tools cannot effectively control traffic that does not go beyond the limits of the physical server. Secondly, the installation of additional devices in the internal network requires considerable financial resources, which is not always realizable in a difficult economic situation.
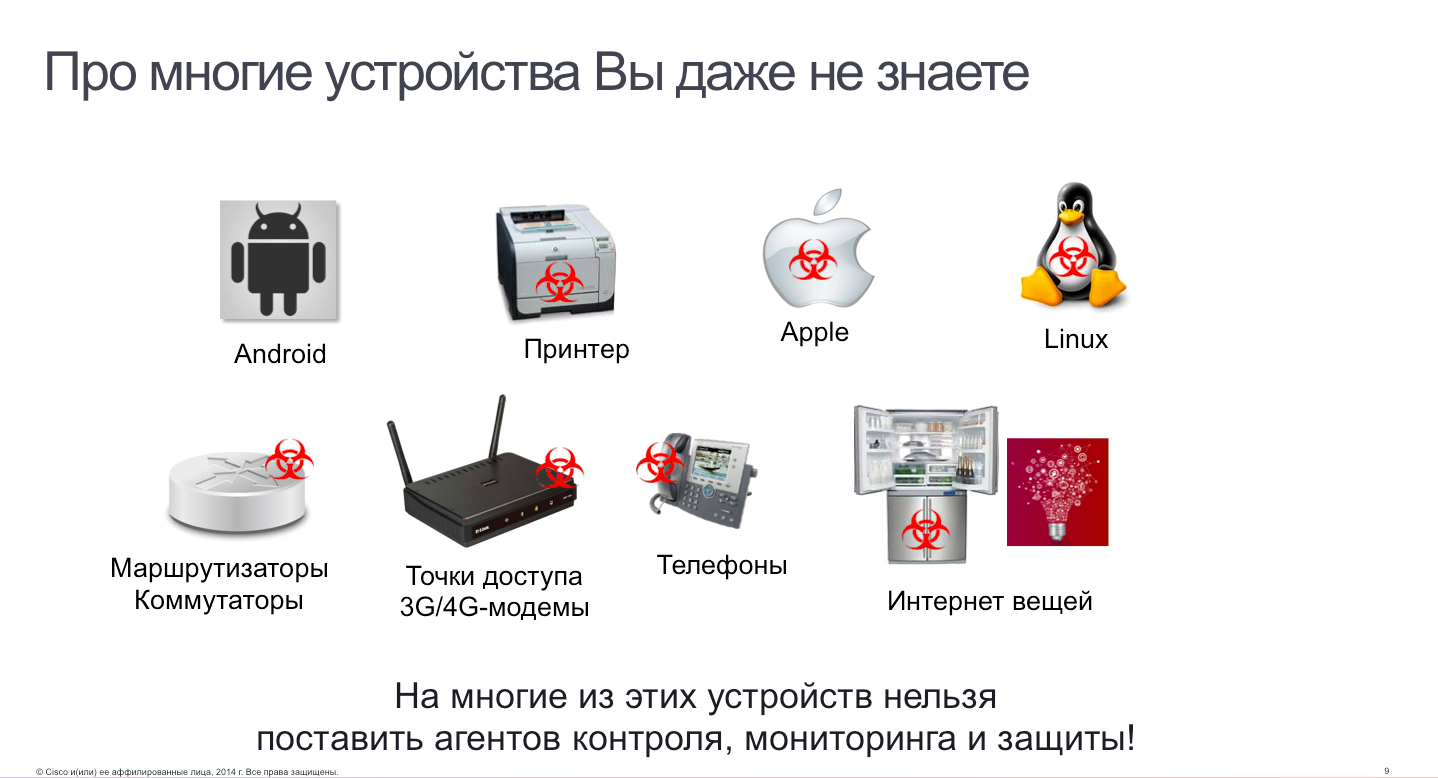
The second often recommended option is to install protections on servers and workstations, detecting and blocking unauthorized activity of users or against users. That's right, but ... What to do with printers, scanners, industrial controllers, IP video surveillance systems and access control? After all, users do not work behind them (and they cannot be authenticated by traditional methods) and neither antivirus, nor HIPS, nor other means of protection can be installed on them. It has already happened that often these devices, and there may even be more of them than user computers, become targets for attackers or a platform for further advancement in the internal network of an enterprise. On such devices, you can install a traffic interceptor and it will sniff everything it can reach. And no means of protecting PCs and servers, such violations of security policy will not notice in principle. And the presence of bypass channels in the form of unprotected Wi-Fi or 4G-modem will lead to the fact that confidential data can flow away bypassing the corporate perimeter protection.
')
Or maybe try to assign this task to what is already there and in which a lot of money has been invested? We are talking about network infrastructure, routers, switches and access points, which can not only transmit traffic from point A to point B, but also effectively protect this traffic, simultaneously playing the role of a sensor, a protective wall and a security incident response tool. Indeed, in essence, each network device is a network protection sensor - traffic passes through it, traffic is identified and classified, traffic is sent to the destination. Why not take another step and add the phrase “in terms of information security policy” to each of these points? Why can't applications be identified at the router or switch level without bringing their traffic to the ITU at the perimeter? Why it is impossible to identify attacks without commuting traffic through the span-port on IDS, but using the capabilities of infrastructure equipment? Why it is impossible to block the traffic on the switch port to which the offender is connected, and not to wait for the traffic to reach the ITU? Why can't we dynamically change access control lists depending on the location of the user or device, and not close our eyes to the uncontrolled movement of traffic within the network and unlimited user access to internal resources?
And why, actually, it is impossible? Can! This is exactly what Cisco does in its network infrastructure, serving not only as a protection system sensor (Network as a Sensor), but also as a protection system (Network as a Enforcer) and a system of investigating information security incidents. We use the Netflow protocol as the source data, which gives us all the necessary data about the traffic going through, answering all the important for the information security policy questions - who, what, when, where / where, how. With NetFlow, we can classify traffic, recognize applications, identify attacks and leaks, detect the use of unauthorized applications or the appearance of extraneous nodes, investigate incidents, and identify attackers' entry points to the network. All this allows you to make Netflow, which is superimposed on the security analytics embedded in the Cisco Cyber Threat Defense solution. Differentiation and blocking of unauthorized access is implemented using access control lists and security tags SGT (Security Group Tag), laying the foundation for Cisco TrustSec technology, and the Cisco Identity Service Engine (ISE) helps to manage all security settings on tens of thousands of devices.
What is interesting about such a network security solution built into the network infrastructure itself? In addition to solving the security problems of the internal network and localizing problems at the moment of their occurrence, and not when they reach the perimeter or some control points in the network in which protection is put, we also have another advantage - the protection of investments made in infrastructure and the ability to provide protection of the enterprise in terms of budget cuts. After all, we already have the infrastructure. All we need is the Netflow analytics and visualization system from the point of view of the Cisco Cyber Threat Defense IB, as well as the Dynamic Access Control List (Cisco Identity Service Engine) management system.
A little more detail about Cisco's approach to network security with the built-in infrastructure mechanisms can be seen in our presentation:
Shl. And the perimeter protection and the installation of IDS / IPS / ITU inside the network still has not been canceled. Just by itself, she no longer saves. Ideally, it should be integrated with the protection of the internal network and function according to uniform policies.

There are three options. The first is to build another one in the internal network, but already a superimposed network of security tools? I think any security vendor will be happy to prepare a proposal for this option, including many IPS sensors and firewalls, which will monitor and control internal network traffic and detect malicious code and unauthorized applications. But this option poses a number of difficulties. First, the not always existing network design allows such a connection to be realized. The network operates at speeds that are not subject to protection, the span ports for connecting IDS are already taken, the enterprise actively uses virtualization, and the protection tools cannot effectively control traffic that does not go beyond the limits of the physical server. Secondly, the installation of additional devices in the internal network requires considerable financial resources, which is not always realizable in a difficult economic situation.
The second often recommended option is to install protections on servers and workstations, detecting and blocking unauthorized activity of users or against users. That's right, but ... What to do with printers, scanners, industrial controllers, IP video surveillance systems and access control? After all, users do not work behind them (and they cannot be authenticated by traditional methods) and neither antivirus, nor HIPS, nor other means of protection can be installed on them. It has already happened that often these devices, and there may even be more of them than user computers, become targets for attackers or a platform for further advancement in the internal network of an enterprise. On such devices, you can install a traffic interceptor and it will sniff everything it can reach. And no means of protecting PCs and servers, such violations of security policy will not notice in principle. And the presence of bypass channels in the form of unprotected Wi-Fi or 4G-modem will lead to the fact that confidential data can flow away bypassing the corporate perimeter protection.

')
Or maybe try to assign this task to what is already there and in which a lot of money has been invested? We are talking about network infrastructure, routers, switches and access points, which can not only transmit traffic from point A to point B, but also effectively protect this traffic, simultaneously playing the role of a sensor, a protective wall and a security incident response tool. Indeed, in essence, each network device is a network protection sensor - traffic passes through it, traffic is identified and classified, traffic is sent to the destination. Why not take another step and add the phrase “in terms of information security policy” to each of these points? Why can't applications be identified at the router or switch level without bringing their traffic to the ITU at the perimeter? Why it is impossible to identify attacks without commuting traffic through the span-port on IDS, but using the capabilities of infrastructure equipment? Why it is impossible to block the traffic on the switch port to which the offender is connected, and not to wait for the traffic to reach the ITU? Why can't we dynamically change access control lists depending on the location of the user or device, and not close our eyes to the uncontrolled movement of traffic within the network and unlimited user access to internal resources?
And why, actually, it is impossible? Can! This is exactly what Cisco does in its network infrastructure, serving not only as a protection system sensor (Network as a Sensor), but also as a protection system (Network as a Enforcer) and a system of investigating information security incidents. We use the Netflow protocol as the source data, which gives us all the necessary data about the traffic going through, answering all the important for the information security policy questions - who, what, when, where / where, how. With NetFlow, we can classify traffic, recognize applications, identify attacks and leaks, detect the use of unauthorized applications or the appearance of extraneous nodes, investigate incidents, and identify attackers' entry points to the network. All this allows you to make Netflow, which is superimposed on the security analytics embedded in the Cisco Cyber Threat Defense solution. Differentiation and blocking of unauthorized access is implemented using access control lists and security tags SGT (Security Group Tag), laying the foundation for Cisco TrustSec technology, and the Cisco Identity Service Engine (ISE) helps to manage all security settings on tens of thousands of devices.
What is interesting about such a network security solution built into the network infrastructure itself? In addition to solving the security problems of the internal network and localizing problems at the moment of their occurrence, and not when they reach the perimeter or some control points in the network in which protection is put, we also have another advantage - the protection of investments made in infrastructure and the ability to provide protection of the enterprise in terms of budget cuts. After all, we already have the infrastructure. All we need is the Netflow analytics and visualization system from the point of view of the Cisco Cyber Threat Defense IB, as well as the Dynamic Access Control List (Cisco Identity Service Engine) management system.
A little more detail about Cisco's approach to network security with the built-in infrastructure mechanisms can be seen in our presentation:
Shl. And the perimeter protection and the installation of IDS / IPS / ITU inside the network still has not been canceled. Just by itself, she no longer saves. Ideally, it should be integrated with the protection of the internal network and function according to uniform policies.
Source: https://habr.com/ru/post/263615/
All Articles