EU regulators did not find a violation of the law in the activities of the Hacking Team
Earlier we published a fairly detailed post on leaked Hacking Team (HT) data. We also called the Hacking Team a cybergroup, although the term “company” is also appropriate for it. HT can be called a cyber group, if only because they specialized in purchasing exploits from third-party developers, and then used them for their own purposes. The main product of HT is the RCS Galileo remote control system, and this software package includes modules, in fact, for all platforms and operating systems, including Windows, OS X, Android, iOS, and bootkits for them.
HT was not a ceiling company, but specialized in selling Galileo to government agencies in various countries, and special agreements were drawn up for this. She also developed various cyber-schemes that allowed them to bypass antivirus software. The HT Data Archive has made all this information available to everyone. Relatively speaking, HT helped the secret services "to find and neutralize terrorists around the world," that is, their activities were legitimate within the framework of existing EU legislation.
Hacking Team specialized in buying exploits from third-party developers. In connection with the leakage of HT data, at least two well-known HT clients came under the radar of journalists, this is Russian programmer Vitaly Toropov and Netragard. They sold exploits to remotely install malware into the system for a decent amount. Using this link you can find a long-standing media agreement between HT and a Russian programmer for the purchase of exploits worth $ 45K. In turn, the company Netragard issued a press release in which it indicated the suspension of its activity on the sale of exploits to other companies.
')

Fig. Part of Netragard's statement about suspending the sale of exploits.
Another equally important and revealing information was the use of HT special BIOS / EFI implants or firmware rootkits that ensured the survival of the HT software even after the hard disk was replaced in the computer. An analysis of this complex rootkit has already been done by Intel Security and TrendMicro .
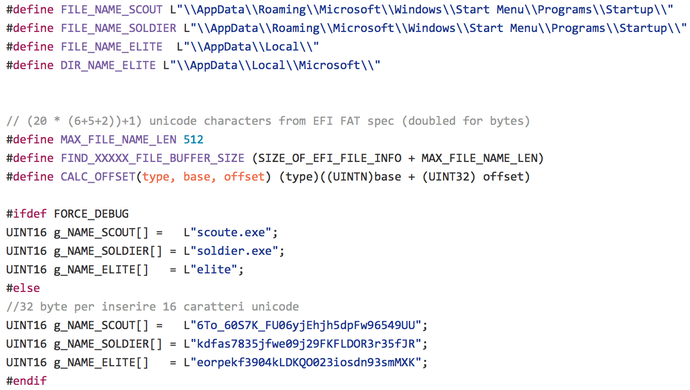
Fig. Part of the rootkit source file.
As a vector of distribution of your HT software, it was quite possible to use Remote Code Execution (RCE) zero-day exploits for both Adobe Flash Player and MS Internet Explorer 11. [ 1 ] [ 2 ] [ 3 ] [ 4 ] [ 5 ] [ 6 ]. Luck clearly turned away from HT and failed to use these exploits (apparently). Instead, they were integrated into many different sets of exploits and are used by cybercriminals to earn on unsuspecting users (drive-by download).
Other aspects of HT's activity remain unclear, for example, why company employees did not use mail encryption and other security mechanisms when working and discussing such controversial “dual-use technologies” as exploits. According to the latest information that has become available to the media (see Hacking Team goes to war against former employees, suspects some helped hackers ), the leakage could have been a simple insider. At the same time, one of the former or current employees of the HT helped those concerned to “settle scores” with HT.
The video, which accurately describes the epic Fail occurring with HT.
Earlier, we wrote that HT traded its “intrusion software” with special services from different countries, including those that are clearly not geopolitical friends of the United States and the EU. For example, one of the Russian companies affiliated with the state. The authorities, as well as the FSB, were HT clients and bought their intrusion software. It is obvious that such activities are in contradiction with the recently adopted Vassenaar agreements, which we wrote about here .
The Wassenaar Agreement introduces the notion of a regulator in the form of a state that can prohibit an EU state from trading its “intrusion software” with countries against which sanctions are imposed.
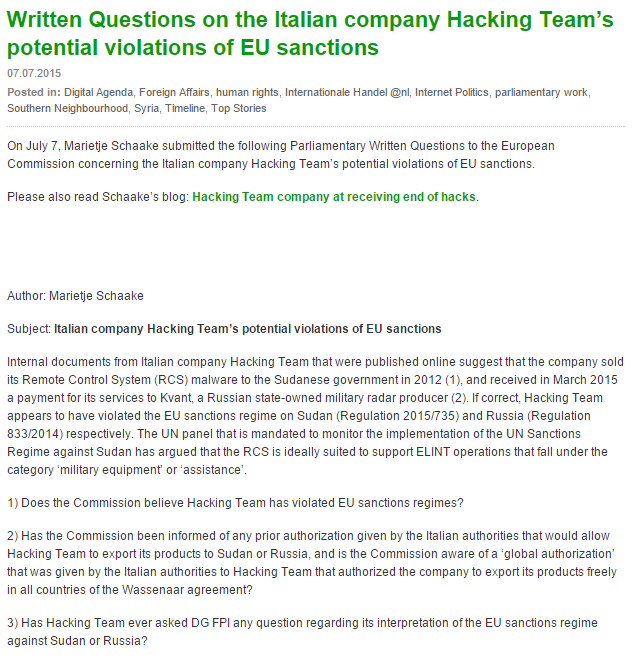
Fig. A list of questions that the EU regulator may consider in connection with the leakage of HT data. The issues of violation of EU legislation in the sale of offensive software in the sanction countries are considered.
Since the Vassenaar agreements remain still at the stage of discussion and addition, that is, they are not fully accepted, this issue requires further elaboration. In essence, HT software falls under all the “intrustion” or “surveillance” software clauses.

HT was not a ceiling company, but specialized in selling Galileo to government agencies in various countries, and special agreements were drawn up for this. She also developed various cyber-schemes that allowed them to bypass antivirus software. The HT Data Archive has made all this information available to everyone. Relatively speaking, HT helped the secret services "to find and neutralize terrorists around the world," that is, their activities were legitimate within the framework of existing EU legislation.
Hacking Team specialized in buying exploits from third-party developers. In connection with the leakage of HT data, at least two well-known HT clients came under the radar of journalists, this is Russian programmer Vitaly Toropov and Netragard. They sold exploits to remotely install malware into the system for a decent amount. Using this link you can find a long-standing media agreement between HT and a Russian programmer for the purchase of exploits worth $ 45K. In turn, the company Netragard issued a press release in which it indicated the suspension of its activity on the sale of exploits to other companies.
')

Fig. Part of Netragard's statement about suspending the sale of exploits.
Another equally important and revealing information was the use of HT special BIOS / EFI implants or firmware rootkits that ensured the survival of the HT software even after the hard disk was replaced in the computer. An analysis of this complex rootkit has already been done by Intel Security and TrendMicro .

Fig. Part of the rootkit source file.
As a vector of distribution of your HT software, it was quite possible to use Remote Code Execution (RCE) zero-day exploits for both Adobe Flash Player and MS Internet Explorer 11. [ 1 ] [ 2 ] [ 3 ] [ 4 ] [ 5 ] [ 6 ]. Luck clearly turned away from HT and failed to use these exploits (apparently). Instead, they were integrated into many different sets of exploits and are used by cybercriminals to earn on unsuspecting users (drive-by download).
Other aspects of HT's activity remain unclear, for example, why company employees did not use mail encryption and other security mechanisms when working and discussing such controversial “dual-use technologies” as exploits. According to the latest information that has become available to the media (see Hacking Team goes to war against former employees, suspects some helped hackers ), the leakage could have been a simple insider. At the same time, one of the former or current employees of the HT helped those concerned to “settle scores” with HT.
The video, which accurately describes the epic Fail occurring with HT.
Earlier, we wrote that HT traded its “intrusion software” with special services from different countries, including those that are clearly not geopolitical friends of the United States and the EU. For example, one of the Russian companies affiliated with the state. The authorities, as well as the FSB, were HT clients and bought their intrusion software. It is obvious that such activities are in contradiction with the recently adopted Vassenaar agreements, which we wrote about here .
The Wassenaar Agreement introduces the notion of a regulator in the form of a state that can prohibit an EU state from trading its “intrusion software” with countries against which sanctions are imposed.

Fig. A list of questions that the EU regulator may consider in connection with the leakage of HT data. The issues of violation of EU legislation in the sale of offensive software in the sanction countries are considered.
Since the Vassenaar agreements remain still at the stage of discussion and addition, that is, they are not fully accepted, this issue requires further elaboration. In essence, HT software falls under all the “intrustion” or “surveillance” software clauses.
Source: https://habr.com/ru/post/263321/
All Articles