Trouble came from not waiting, XSS vulnerability in Yandex.Metrica
Good time habravchane! Just the other day I published an article on the Web API documentation and there were people who tried to use XSS on a service that was on the same domain. But especially it did not work. More precisely it turned out, but not on this service. For details, I ask under the cat.

Somehow I was sitting looking through statistics on Yandex.Metrica and wanted to see the requests people came to the site with. It seems nothing terrible, I did not see. But still here are the data.

')
After I chose to display requests in ascending order, I saw something interesting. That is, the very XSS vulnerabilities in the GET request, which the respected habravchane left, worked not in the service, which, apparently, was aimed, but on the Yandex.Metrica platform.
What I finally saw on Yandex.Metrica:

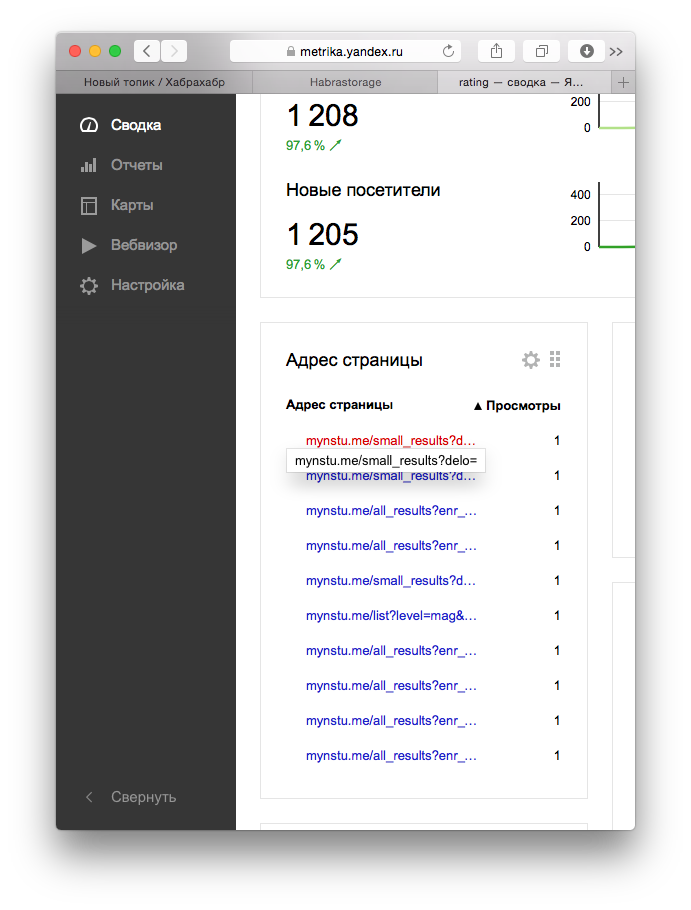
A little scratching my head, I decided to see what all the same requests were for and where. There was no limit to surprise when I did not see these requests. But literally in a minute I realized that those requests — requests with an empty parameter — those vulnerable requests. Actually, they are presented below:
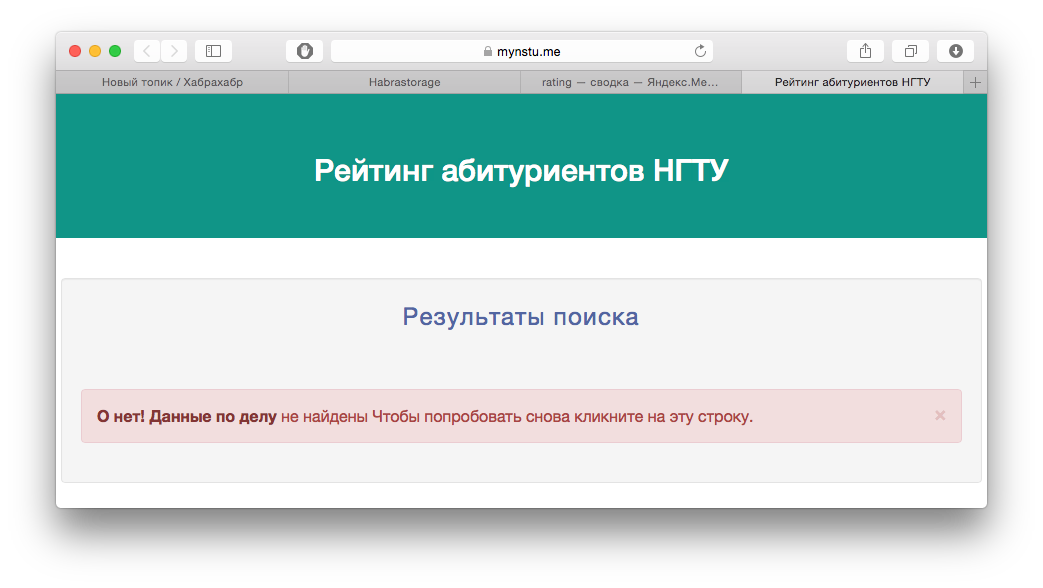
But you ask, they are empty, what is in them and what they look like. One has only to click on them and we will go to the page, where the error will be shown, saying that the data is incorrect. Indeed it is:
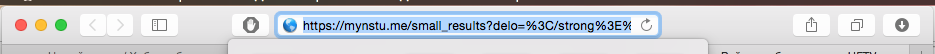
But actually that fateful request:
Sorry for the rather short article, I just wanted to warn you about an interesting assumption in the Yandex.Metrica platform and that this could lead to sad consequences. Be careful!
PS
Do not judge strictly! I just want to help you. And please do not break my service.
PPS Vulnerability closed 07/17/15.

Somehow I was sitting looking through statistics on Yandex.Metrica and wanted to see the requests people came to the site with. It seems nothing terrible, I did not see. But still here are the data.

')
After I chose to display requests in ascending order, I saw something interesting. That is, the very XSS vulnerabilities in the GET request, which the respected habravchane left, worked not in the service, which, apparently, was aimed, but on the Yandex.Metrica platform.
What I finally saw on Yandex.Metrica:

A little scratching my head, I decided to see what all the same requests were for and where. There was no limit to surprise when I did not see these requests. But literally in a minute I realized that those requests — requests with an empty parameter — those vulnerable requests. Actually, they are presented below:

But you ask, they are empty, what is in them and what they look like. One has only to click on them and we will go to the page, where the error will be shown, saying that the data is incorrect. Indeed it is:

But actually that fateful request:
https://mynstu.me/small_results?delo=%3C/strong%3E%3C/a%3E%3Cscript%3Ealert('antoha%20privet')%3C/script%3E 
findings
Sorry for the rather short article, I just wanted to warn you about an interesting assumption in the Yandex.Metrica platform and that this could lead to sad consequences. Be careful!
PS
Do not judge strictly! I just want to help you. And please do not break my service.
PPS Vulnerability closed 07/17/15.
Source: https://habr.com/ru/post/263113/
All Articles