RC4 NOMORE: break the RC4 stream for tens of hours in TLS and WPA-TKIP
Researchers Mathy Vanhoef and Frank Piessens of iMinds-DistriNet and KU Leuven discovered a dangerous vulnerability in the outdated, but still widely used streaming cipher RC4. In the case of websites, the vulnerability allows decrypting a part of the encrypted HTTPS stream (for example, a session identifier transmitted in a cookie) for dozens of hours. To implement the vulnerability, you need to use the MiTM attack, listen to and save encrypted traffic, and also be able to perform a large number of requests on behalf of the victim (as was the case with POODLE ), which is easiest to get if you embed a special script on the HTTP pages of others sites, generating a large number of requests for a hacker site. In addition, the attacker needs to somehow find out or set his Cookie value, which would be located close to the desired value in the transmitted traffic.
In the course of the study, it was found that in order to carry out an attack on decrypting a typical session value of 16 characters, it takes about 75 hours of active attack, after which the desired value can be obtained in 94% of cases.
The guys improved the old attack from AlFardan, which is based on the construction and use of the distribution spread of researchers from Cisco Fluhrer and McGrew, adding the distribution option of Japanese researchers Takanori Isobe, Toshihiro Ohigashi, Yuhei Watanabe, Masakatu Morii, and combining them. The text around the cookie you are looking for is required to find the Bayesian probability.
If it’s quite problematic to organize an HTTPS attack, then in the case of Wi-Fi, the numbers are more real: it takes only 1 hour of active attack on the network, after which it turns out to decrypt the used temporary key used to transmit Unicast traffic (pairwise transient key, PTK ). The attack is greatly simplified due to the presence of cryptographically weak authentication in TKIP frames. It is noteworthy that the points should periodically (usually every hour) change the key, but most of the points update only the key that is used to transmit Broadcast traffic - the groupwise transient key (GTK). In any case, even properly working points are vulnerable, since the attack takes a little less time than it takes to update the key.
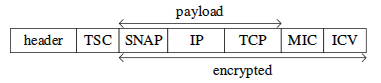
The RC4 cipher is still often used in the HTTPS protocol because of the need to support legacy OSs and software, such as Windows XP and Internet Explorer 6 and 7. WPA2-TKIP encryption is widely used for wireless data transmission over Wi-Fi.
')
To protect yourself from this vulnerability, you must disable support for the RC4 cipher on the server side. If you need to maintain compatibility with legacy software, use 3DES instead of RC4. Interestingly, a couple of years ago, everyone turned off 3DES and switched to RC4 because of attacks related to block ciphers, like Lucky 13 and BEAST, and now, it seems, you have to do the opposite. But the most correct option is to disable both of them.
Wi-Fi users can set the use of WPA2-AES (or WPA2-CCMP) in the access point settings. We recommend to do it immediately, because the possibility of this attack, it is possible, will soon appear in utilities like aircrack-ng.
All Your Biases Belong To Us: Breaking RC4 in WPA-TKIP and TLS - a detailed PDF describing the attack.
In the course of the study, it was found that in order to carry out an attack on decrypting a typical session value of 16 characters, it takes about 75 hours of active attack, after which the desired value can be obtained in 94% of cases.
The guys improved the old attack from AlFardan, which is based on the construction and use of the distribution spread of researchers from Cisco Fluhrer and McGrew, adding the distribution option of Japanese researchers Takanori Isobe, Toshihiro Ohigashi, Yuhei Watanabe, Masakatu Morii, and combining them. The text around the cookie you are looking for is required to find the Bayesian probability.
If it’s quite problematic to organize an HTTPS attack, then in the case of Wi-Fi, the numbers are more real: it takes only 1 hour of active attack on the network, after which it turns out to decrypt the used temporary key used to transmit Unicast traffic (pairwise transient key, PTK ). The attack is greatly simplified due to the presence of cryptographically weak authentication in TKIP frames. It is noteworthy that the points should periodically (usually every hour) change the key, but most of the points update only the key that is used to transmit Broadcast traffic - the groupwise transient key (GTK). In any case, even properly working points are vulnerable, since the attack takes a little less time than it takes to update the key.

The RC4 cipher is still often used in the HTTPS protocol because of the need to support legacy OSs and software, such as Windows XP and Internet Explorer 6 and 7. WPA2-TKIP encryption is widely used for wireless data transmission over Wi-Fi.
')
To protect yourself from this vulnerability, you must disable support for the RC4 cipher on the server side. If you need to maintain compatibility with legacy software, use 3DES instead of RC4. Interestingly, a couple of years ago, everyone turned off 3DES and switched to RC4 because of attacks related to block ciphers, like Lucky 13 and BEAST, and now, it seems, you have to do the opposite. But the most correct option is to disable both of them.
Wi-Fi users can set the use of WPA2-AES (or WPA2-CCMP) in the access point settings. We recommend to do it immediately, because the possibility of this attack, it is possible, will soon appear in utilities like aircrack-ng.
All Your Biases Belong To Us: Breaking RC4 in WPA-TKIP and TLS - a detailed PDF describing the attack.
Source: https://habr.com/ru/post/262897/
All Articles