New DNS Server Features in Windows Server Technical Preview 2
The author of the article is Andrey Kaptelin, a member of the IT community.
With the release of Windows Server Technical Preview 2, many services have received updates. Not bypassed the party and honored DNS name server. In addition to supporting DNS server management from PowerShell, there is a new feature - DNS policy.
DNS policy is an extension of the DNS server to adapt its work depending on the content of incoming requests. Due to the first application of policies on an incoming request, it is possible to significantly simplify the operation of the server, eliminating obviously unnecessary requests, or by specifying the server, change the content of the response in accordance with the described rules.
Principle of operation
Policies apply to three categories of requests:
- Request permission to write . All usual name resolution requests to an IP address, or getting TXT, MX, and SRV record values.
- Request to transfer zones . Requests from your secondary servers to update zone information. If such a request is made for a foreign server, it will receive all the contents of your zone.
- The query for which you want to perform a recursive query . For example, a customer has requested a name that is not in your zones. The server must re-ask the upstream server to get the result. For external clients, it is not always necessary to process such requests.
The scope of the policy can be, both on the entire server and on a specific zone, if this zone is not integrated into Active Directory.
')
DNS server policies allow you to implement the following actions:
- Create a zone with a different set of records.
- Classify the client by its IP address and use it in the policy application rules.
- Apply policies for the entire server and for zones that are not integrated into AD.
- Apply different policies depending on the interface that received the request.
- Apply policies depending on the time of day.
- Apply policies by type of records requested.
- Responding to requests for data from different versions of a zone in given proportions is similar to a managed Round Robin.
- Apply policies to forward zones.
- Apply the required filter policy if you need to perform a recursion to complete the request.
- Put the policies in the right order of processing.
All created policies are saved in the registry in the following sections:
Specified subnets used in policy enforcement rules are stored in the registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\DNS Server\ClientSubnets Policies applied to the server are stored in the registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\DNS Server\Policies Policies applied to a specific zone are stored in the registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\DNS Server\Zones\{ }\Policies Zones used in recursive query rules are stored in the registry key.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters\ServerScopes The value of the recursion state for the entire server (the zone is ".") Is stored in the
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters The key NoRecursion is “0” - recursion is enabled, “1” is disabled. Switching from on to off requires a restart of the DNS server service.
If an alternative content ( Add-DnsServerZoneScope ) is created for a zone, it is placed in a file located in
C: \ Windows \ System32 \ dns \ {zone name}
And the configuration is written to the registry.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\DNS Server\Zones\{_}\ZoneScopes\ If you delete an alternative version of a zone, the registry entry is deleted, and the alternative content file remains in place.
Despite the abundance of settings locations, several PowerShell commands are enough to change them.
To work with write permission and recursive query query policies:
Add-DnsServerQueryResolutionPolicy
Get-DnsServerQueryResolutionPolicy
Set-DnsServerQueryResolutionPolicy
Remove-DnsServerQueryResolutionPolicy
To work with requests for zone transfer:
Add-DnsServerZoneTransferPolicy
Get-DnsServerZoneTransferPolicy
Set-DnsServerZoneTransferPolicy
Remove-DnsServerZoneTransferPolicy
The steps to perform policies can be as follows:
-Action ALLOW - the query is performed by the DNS server
-Action DENY - the DNS server refuses
-Action IGNORE - the request is not processed by the DNS server
To understand the stages of policy processing, we have the following request flow diagrams.
The scheme for processing write permission requests and recursive queries:
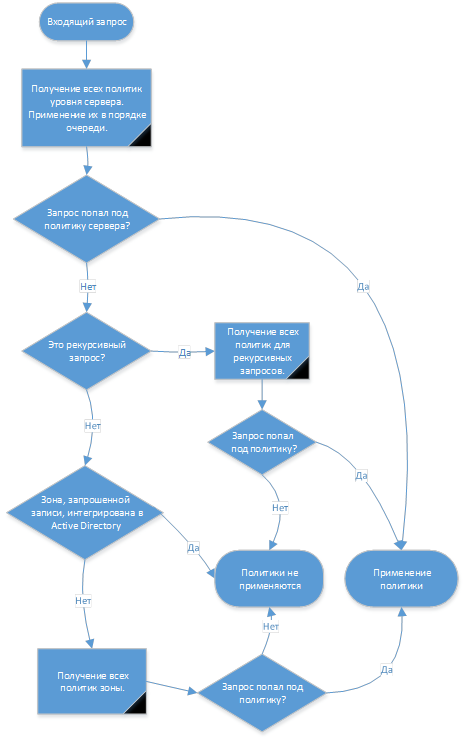
The processing of requests for transfer of zones:

Examples
Setting Restricting Recursive Queries
There is a task to configure the DNS server to perform recursive queries only for internal clients. The server has two network interfaces. The external IP address is 1.1.1.1, the internal interface has an IP address 10.0.0.39. You can accomplish this task by limiting the execution of such requests to the internal interface only. To do this, recursive queries at the server level should be disabled and allowed only for requests received by the internal interface.
# «.» - .. Set-DnsServerRecursionScope -Name . -EnableRecursion $False # Add-DnsServerRecursionScope -Name "InternalClients" -EnableRecursion $True # , Add-DnsServerQueryResolutionPolicy -Name "SplitBrainRecursionPolicy" -Action ALLOW -ApplyOnRecursion -RecursionScope "InternalClients" -ServerInterfaceIP "EQ,10.0.0.39" We will analyze the policy creation team in more detail.
Add-DnsServerQueryResolutionPolicy is a cmdlet for creating a policy for processing requests for resolving records and recursive queries.
-Name "SplitBrainRecursionPolicy" - the name of the policy
-Action ALLOW - policy action - execute request
-ApplyOnRecursion - the policy only processes requests for which you need to perform a recursive query
-RecursionScope "InternalClients - gets the value of enabling or disabling recursion of a previously specified area
-ServerInterfaceIP „EQ, 10.0.0.39“ - the rule of applying the policy - only a request that came to the server interface with an IPv4-address equal to 10.0.0.39.
Modifying the response to the name resolution request
The company has a fault-tolerant web server hosted at two sites - in Europe and in Australia. The speed of both sites is always the same, but at night the cost of rent is less. The company decided to use the site depending on the time of day. To do this, it was decided to distribute customer requests as a percentage of 80/20 at night and day data center.
# Add-DnsServerZoneScope -ZoneName "testzone.z" -Name "EuropeDC" Add-DnsServerZoneScope -ZoneName "testzone.z" -Name "AustralianDC" # - Add-DnsServerResourceRecord -ZoneName "testzone.z" -A -Name "www" -IPv4Address "1.1.1.1" -ZoneScope "EuropeDC" Add-DnsServerResourceRecord -ZoneName "testzne.oz" -A -Name "www" -IPv4Address "2.2.2.2" -ZoneScope "AustralianDC" # Add-DnsServerQueryResolutionPolicy -Name "www-6-18" -Action ALLOW -ZoneScope "AustralianDC,4;EuropeDC,1" –TimeOfDay “EQ,06:00-18:00” -ZoneName "testzone.z" –ProcessingOrder 1 Add-DnsServerQueryResolutionPolicy -Name "www-0-6" -Action ALLOW -ZoneScope "AustralianDC,1;EuropeDC,4" –TimeOfDay “EQ,00:00-06:00” -ZoneName "testzone.z" –ProcessingOrder 2 Add-DnsServerQueryResolutionPolicy -Name "www-18-24" -Action ALLOW -ZoneScope "AustralianDC,1;EuropeDC,4" –TimeOfDay “EQ,18:00-23:59” -ZoneName "testzone.z" –ProcessingOrder 3 We will analyze the policy creation team in more detail.
Add-DnsServerQueryResolutionPolicy - policy creation cmdlet
-Name "www-6-18" - policy name
-Action ALLOW - policy action - execute request
-ZoneScope „AustralianDC, 4; EuropeDC, 1“ - tells the policy to use two versions of the zone in 4 to 1 proportions, obtaining the required ratio of 80% to 20% in outputting data from the zone version for Europe and Australia
–TimeOfDay “EQ, 06: 00-18: 00” - Policy Duration
-ZoneName "testzone.z" - the name of the zone for which the policy is valid
–ProcessingOrder 1 - the order of policy application for the policies of this zone
Limiting Zone Transfer Requests
The company has a primary DNS server for external zones and two secondary DNS servers hosted by different providers. It is not possible to prohibit a firewall from accessing the main server using TCP protocol on port 53, since zones have entries larger than the UDP packet size. It was decided to use DNS policy for these purposes.
# DNS- Add-DnsServerClientSubnet -Name "DNSsecondary1" -IPv4Subnet 4.4.4.4/32 Add-DnsServerClientSubnet -Name "DNSsecondary2" -IPv4Subnet 5.5.5.5/32 # Add-DnsServerZoneTransferPolicy -Name "Allow secondary DNS" -ZoneName "testzone.z" -Action IGNORE -ClientSubnet "ne,DNSsecondary1,DNSsecondary2" We will analyze the policy creation team in more detail.
Add-DnsServerZoneTransferPolicy - create zone transfer request policy cmdlet
-Name "Allow secondary DNS" - the name of the policy
-ZoneName "testzone.z" - the name of the zone for which the policy will apply
-Action IGNORE - Policy Action
-ClientSubnet "ne, DNSsecondary1, DNSsecondary2" - the condition of use for all but our servers
As you can see, to solve many problems, you can now use the DNS policy. Having correctly described the rules for passing requests to the DNS server, you can not only optimize the services, but also reduce the load on the DNS server by filtering out unnecessary requests.
Related Links
DNS Policies Overview
Windows Networking Team [MSFT] Blog Articles
Source: https://habr.com/ru/post/262789/
All Articles