Vulnerabilities of security systems of the Ministry of Defense, FSB, FSIN, NPP, metro and federal highways

Everyone remembers the story, as one video has served as a detonator for a series of international scandals.
Hackers have already cracked the rocket launcher (for training purposes), the air defense system and the oil company , and hackers enslaved by the American special services turned off the Internet in Syria and rummaged in the Iranian atomic program .
According to the study, even a
')
In short, download Shodan and train to test the
Systems that ensure the safety of critical infrastructure (for example, categorized fuel and energy facilities, transport and stadiums), as well as special-purpose facilities of law enforcement agencies, should not use foreign software with closed-source software.
The main problems with foreign closed software:
1. The presence of undocumented features ( NDV ). The US government has special means for access.
What is your evidence?
Yes, and any google on request "Snowden"
The NSA took part in the development of WINDOWS 7 ( Russian , English )
German security services fear backdoors in Windows 8
From the NSA budget, it follows that the agency spends about $ 250 million a year on third-party commercial software sabotage programs. Of course, Microsoft is one of the agency’s main partners. It is reliably known that in the office of the company there are regular meetings of developers with representatives of the FBI, the NSA and other agencies, where specialists jointly resolve current issues.
[ source ]
FBI demanded that Apple and Google leave “holes” for special services to access user data
Disabling the Internet in Syria - by the forces of the NSA? ( rus , engl )
Supervised by the NSA: how to stay protected (Bruce Schneier Recommendations)
Snowden has shed light on the cryptographic hacking situation. Everything is bad

Yes, and any google on request "Snowden"
The NSA took part in the development of WINDOWS 7 ( Russian , English )
German security services fear backdoors in Windows 8
From the NSA budget, it follows that the agency spends about $ 250 million a year on third-party commercial software sabotage programs. Of course, Microsoft is one of the agency’s main partners. It is reliably known that in the office of the company there are regular meetings of developers with representatives of the FBI, the NSA and other agencies, where specialists jointly resolve current issues.
[ source ]
FBI demanded that Apple and Google leave “holes” for special services to access user data
Disabling the Internet in Syria - by the forces of the NSA? ( rus , engl )
Supervised by the NSA: how to stay protected (Bruce Schneier Recommendations)
Snowden has shed light on the cryptographic hacking situation. Everything is bad
1.1. The impossibility of deep verification and state certification of solutions for the absence of undocumented features and protection against unauthorized access to information.
a little about the requirements for the level of control, levels of secrecy and regulations
Requirements for the level of control. List of requirements.
METHODICAL DOCUMENT INFORMATION PROTECTION MEASURES IN GOVERNMENTAL INFORMATION SYSTEMS
(Approved by the FSTEC of Russia on February 11, 2014)
The level of significance of information is determined by the degree of possible damage to the information owner (customer) and / or operator from
violations of confidentiality, integrity or availability of information:
KM = [(confidentiality, degree of damage) (integrity, degree of damage) (availability, degree of damage)] ,
where the degree of possible damage is determined by the owner of the information (the customer) and (or) the operator independently by expert or other methods and can be:
 Guidance document Protection against unauthorized access to information
Guidance document Protection against unauthorized access to information
(Approved by the decision of the Chairman of the State Technical Commission under the President of the Russian Federation No. 114 dated June 4, 1999)
Set four levels of control the lack of undeclared capabilities. Each level is characterized by a certain minimum set of requirements.
For software used in the protection of information classified as state secrets, a control level of at least third must be provided.
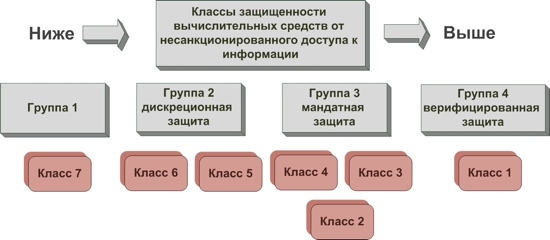
Seven classes of security from unauthorized access are collected in four groups, characterized by different methods of protection.

The four levels of control over the absence of NDV determine which stamped documents the information system can process.
Read more here: A star named Linux: why are the “military” OSs stronger?
METHODICAL DOCUMENT INFORMATION PROTECTION MEASURES IN GOVERNMENTAL INFORMATION SYSTEMS
(Approved by the FSTEC of Russia on February 11, 2014)
The level of significance of information is determined by the degree of possible damage to the information owner (customer) and / or operator from
violations of confidentiality, integrity or availability of information:
KM = [(confidentiality, degree of damage) (integrity, degree of damage) (availability, degree of damage)] ,
where the degree of possible damage is determined by the owner of the information (the customer) and (or) the operator independently by expert or other methods and can be:
- high , if as a result of violation of one of the security properties of information (confidentiality, integrity, availability), significant negative consequences in social, political, international, economic, financial or other areas of activity and / or information system and / or operator (information owner) are possible can perform the functions assigned to them;
- moderate if a violation of one of the security properties of information (confidentiality, integrity, availability) may have moderate negative consequences in social, political, international, economic, financial or other areas of activity and / or the information system and / or operator (owner of information) can perform at least one of the functions assigned to them;
- low , if as a result of violation of one of the security properties of information (confidentiality, integrity, accessibility), slight negative consequences in social, political, international, economic, financial or other areas of activity are possible and / or the information system and / or operator (information owner) can perform the functions assigned to them with insufficient efficiency or the performance of functions is possible only with the involvement of additional forces and means.
 Guidance document Protection against unauthorized access to information
Guidance document Protection against unauthorized access to information(Approved by the decision of the Chairman of the State Technical Commission under the President of the Russian Federation No. 114 dated June 4, 1999)
Set four levels of control the lack of undeclared capabilities. Each level is characterized by a certain minimum set of requirements.
For software used in the protection of information classified as state secrets, a control level of at least third must be provided.
- The highest level of control, the first , is sufficient for software used in the protection of information marked “OB”.
- The second level of control is sufficient for software used in the protection of information marked “CC”.
- The third level of control is sufficient for software used in the protection of information marked "C".
- The lowest level of control - the fourth , is sufficient for software used in the protection of confidential information

Seven classes of security from unauthorized access are collected in four groups, characterized by different methods of protection.

The four levels of control over the absence of NDV determine which stamped documents the information system can process.
Read more here: A star named Linux: why are the “military” OSs stronger?
2. Dependence on foreign supplier
2.1. The possibility of limiting the supply due to sanctions
example
"Obama ordered to disable Windows, Skype and Gmail in Crimea"
When implementing such a scenario for the whole of Russia, banks, shops, cellular communications, etc. will stop working (“Fall of repeaters” according to Vinzh)
There are precedents when, for example, PCs running MS Windows were turned off at the request of the manufacturer (Yugoslavia before the start of the conflict with NATO), executed certain commands regardless of the wishes of the PC user (forced updating of the software by the Microsoft command, even if the PC user prohibited any updates). The latter case suggests that, if necessary, any PC running Windows can update and launch any program sent from Microsoft. If necessary, it can be a program to delete all data, lock the system, search for the necessary documents, etc.
[ source ]

"Obama ordered to disable Windows, Skype and Gmail in Crimea"
When implementing such a scenario for the whole of Russia, banks, shops, cellular communications, etc. will stop working (“Fall of repeaters” according to Vinzh)
There are precedents when, for example, PCs running MS Windows were turned off at the request of the manufacturer (Yugoslavia before the start of the conflict with NATO), executed certain commands regardless of the wishes of the PC user (forced updating of the software by the Microsoft command, even if the PC user prohibited any updates). The latter case suggests that, if necessary, any PC running Windows can update and launch any program sent from Microsoft. If necessary, it can be a program to delete all data, lock the system, search for the necessary documents, etc.
[ source ]
2.2. Additional significant costs in addition to the initial purchase of software licenses for the upgrade and service, as well as due to a jump in the dollar.
2.3. Changing the terms of use unilaterally, for example, downloading updates without the user's knowledge.
Example
About updating Windows 10 without coordination with the user.
Windows 10 auto updates are a necessary evil
Microsoft was hit by a barrage of criticism because of the shadowing of Windows 10 by users
Hacker News Talk
Windows XP discontinued today
China abandoned Windows 8 in government

About updating Windows 10 without coordination with the user.
Windows 10 auto updates are a necessary evil
Microsoft was hit by a barrage of criticism because of the shadowing of Windows 10 by users
Hacker News Talk
Windows XP discontinued today
China abandoned Windows 8 in government
3. Holes
do you really use java in security systems?
Distributing vulnerabilities in cyber attacks to applications [ Vulnerabilities and zero-days ]
“Malefactors choose JAVA!”
"Hacking a random number generator JAVA"
From fresh:
“A 0-day vulnerability has been discovered in JAVA”
It is clear that you can follow and all the time to update. But the software maker does not always work quickly, and during the sanctions they may even stop updating the product.
The manufacturer is often a dictator, and not always generous: “Oracle's actions are the neutron bomb to the Open Source camp”
With Open Source, too, not everything is so rosy about holes ( Heartbleed and misconceptions about Open Source ), but in a strategic perspective, open software has advantages.
Meanwhile, in Russia
The TOBOL-TV television surveillance system developed by FCNIVT JSC Eleron (Rosatom Corporation, Moscow) uses JAVA as the runtime environment .

Distributing vulnerabilities in cyber attacks to applications [ Vulnerabilities and zero-days ]
“Malefactors choose JAVA!”
"Hacking a random number generator JAVA"
From fresh:
“A 0-day vulnerability has been discovered in JAVA”
It is clear that you can follow and all the time to update. But the software maker does not always work quickly, and during the sanctions they may even stop updating the product.
The manufacturer is often a dictator, and not always generous: “Oracle's actions are the neutron bomb to the Open Source camp”
With Open Source, too, not everything is so rosy about holes ( Heartbleed and misconceptions about Open Source ), but in a strategic perspective, open software has advantages.
Meanwhile, in Russia
The TOBOL-TV television surveillance system developed by FCNIVT JSC Eleron (Rosatom Corporation, Moscow) uses JAVA as the runtime environment .
“And these people forbid me to poke around in my nose?”
Some departments, such as MO, MIA, FSIN, etc. declare that their systems do not have direct access to the Internet. In this case, there is a threat of new vulnerabilities when updating the system software or installing a printer driver. It is also worth keeping in mind the human factor: often users quietly from the authorities install games and USB modems to access the Internet.
A friend of my acquaintance suggested that "in the USA there is a directive on a categorical ban on the use of software in government bodies (especially the State Department), which is developed outside the borders of NATO member countries." Because of this, a friend broke a major contract.
It is clear that while the tail of the dinosaur was torn off, the signal on the relic nervous system goes a long time, but perhaps it would be time to introduce a symmetrical response.
What do we have in reality?
Corporate infrastructure vulnerabilities
Statistics of corporate information systems vulnerabilities (2013). Positive Technologies
Full Report (PDF)
Disadvantages of network perimeter protection
Disadvantages of internal network protection
Lack of awareness of staff in information security issues
Disadvantages of network perimeter protection
- In 9 out of 10 systems, any external intruder acting on the part of the Internet is able to gain access to the internal network nodes. Moreover, in 55% of cases, an external attacker could develop an attack and gain complete control over the entire infrastructure of the company.
- On average, an external attacker needs to exploit two different vulnerabilities to overcome the network perimeter, and in order to carry out an attack in 82% of cases, it is enough to have an average or low qualification.
- In 40% of cases, the intrusion vector in the internal network is based on weak password protection. Just as in the previous two years, this vulnerability is the most widespread, it was found on the network perimeter of 82% of the systems studied, and in each of these systems the vocabulary passwords were also present in web applications. In 67% of companies, vocabulary passwords were used for privileged accounts.
- In every third system, access to the internal network is carried out through web application vulnerabilities. Thus, vulnerabilities like "Download arbitrary files" and "Implementation of SQL statements" are found in 55% of systems. In general, web application vulnerabilities were found in 93% of the systems studied. The overall level of security in this area remains extremely low, as was the case in the previous two years.
- Compared to 2011–2012. The average level of network perimeter security has gone down. The share of systems increased by 17%, where it was possible to gain access to the internal network (from 74% to 91%). To conduct attacks to an outside attacker, lower qualifications are now required, overcoming the perimeter on average requires the exploitation of fewer vulnerabilities (2 vs. 3 in the previous two years). The current picture indicates that the protective measures used are developing more slowly than modern methods of attack and cannot provide a sufficiently high level of security. For example, the share of systems where actual security updates are not installed on the network perimeter nodes has significantly increased (from 10 to 64%).
Disadvantages of internal network protection
- In all the systems studied, an unprivileged internal intruder located in the user segment of the network may somehow extend its privileges and gain unauthorized access to critical resources. At the same time, in 71% of cases, an internal violator can gain complete control over the entire information infrastructure of the organization.
- Only in 17% of cases, the internal attacker must be highly qualified to gain access to critical resources, whereas in half of all systems studied, successful attacks are possible from any unqualified user of the internal network. On average, if you have access to the internal network, an attacker needs to exploit 5 different vulnerabilities to control critical resources.
- The most common vulnerability of internal network resources is still the use of weak passwords, which are found in 92% of systems. The next most common ones are weaknesses in filtering and protecting service protocols (ARP, STP, CDP, etc.), leading to the interception and redirection of traffic, and storing important data in the open form. These vulnerabilities are found in 67% of systems.
- The level of security of internal networks has decreased compared to 2011–2012. Obtaining complete control over important resources from the internal network has now been possible for 100% of the systems reviewed, whereas previously a similar result was obtained in 84% of cases. As for attacks from an external attacker, the average number of vulnerabilities that are necessary for a successful attack decreased from 7 to 5. The required skill of the attacker also decreased: for 50% of attacks with a sufficiently low qualification, whereas previously this qualification was sufficient for 40 % attacks. In general, despite some improvements in certain areas (increased, for example, the level of anti-virus protection), the measures applied are not enough to counter modern attacks.
Lack of awareness of staff in information security issues
- In 66% of cases, as a result of assessing the awareness of users in matters of information security, one or other shortcomings were found. In every third system, the level of user awareness was assessed as low; in these systems, over 20% of the phishing mailing recipients followed the suggested links and launched the proposed file or entered their credentials.
- On average, every tenth user navigated through the proposed link, while 3% of users attempted to enter into dialogue, and 4% of the subjects downloaded executable files or entered their credentials in the proposed authentication form.
- Staff awareness in information security issues has increased. In 2013, in every third system, the level of awareness was rated as acceptable.
Industrial control systems
In total, the study identified 691 vulnerabilities in the components of the process control system. A sharp increase after 2009 is noticeable: over the next three years (2010–2012), the number of detected vulnerabilities of the automated process control system increased 20 times (from 9 to 192). After that, the average annual number of detected vulnerabilities stabilized (181 in 2014).
Research: vulnerabilities in industrial control systems in 2014
- Every fifth vulnerability is fixed longer than a month.
- 50% of vulnerabilities allow a hacker to run code execution
- A quarter of the vulnerabilities are due to the lack of required security updates.
- Vulnerable 50% of systems published in the global network of Russia
Safety of industrial systems in numbers (2012, PDF)
Objects of critical infrastructure
Key findings from the 2011 Symantec survey (sadly):
[ ]
- Objects of critical infrastructure are the objects of attacks. Representatives of 1 of 13 objects of the critical infrastructure of the Russian Federation suspect that they have become victims of cyber attacks committed with a specific purpose, and at every hundredth enterprise they are absolutely sure of this.
- Russian enterprises rely more on their own strength than on state programs to protect critical infrastructure facilities. The attitude of enterprises to these programs is rather skeptical (this was stated by 35% of respondents). Nevertheless, Russian critical infrastructure facilities, although to a lesser extent than the world average, are willing to cooperate with the state (most companies expressed a neutral or positive attitude about this)
- Potential to improve the readiness of enterprises. Research data shows:
- 20% of objects of critical infrastructure of the Russian Federation do not react properly to information security incidents;
- 26% of critical infrastructure facilities do not apply sufficient measures to control access to infrastructure based on credentials;
- 30% of critical infrastructure do not have a disaster recovery plan for information systems, or it is in a low state of readiness;
- 30% of critical infrastructure do not apply sufficient measures to ensure the security of websites;
- 33% of critical infrastructure facilities do not properly monitor information security;
- 34% of critical infrastructure does not apply sufficient measures to protect the network;
- Executive management 35% of critical infrastructure facilities are not aware of the importance of information security threats adequately;
- 37% of critical infrastructure objects do not apply sufficient measures to ensure the security of electronic messages;
- At 39% of critical infrastructure facilities, safety training is not conducted at an adequate level;
- 45% of critical infrastructure facilities do not conduct a sufficiently high level security audit;
- (51%) ( , , ..), .
- . : , . , , , . , , .
- . , -7% +25% . — 41%, 70% .
[ ]

?
If we talk about the control on the absence of NDV levels 3 and below, involving the analysis of source codes, then get it for closed software is not formally possible. A Windows-based system usually does not have a control level below 4.
Despite the fact that some Windows-based systems and JAVA have been certified by FSTEC (and only for personal data protection, they are not suitable for working with information marked “C”, “ SS "," OV "), their use in state structures and backbone enterprises can be risky in the current geopolitical and economic conditions. (See the example of the Crimea above).
Talk about replacing Windows with Linux in government structures.
What is good for a Russian is death for a German: Munich's municipality will get rid of Linux at workstations

Take an example with the ISS
The ISS is moving to LinuxKeith Chuvala (Keith Chuvala), an employee of the United Space Alliance and the head of the unit responsible for laptops and networks on the ISS, recently explained why NASA decided to transfer all computers to the ISS to Linux:
"We moved key functions from Windows to Linux, because they needed a stable and reliable operating system, one that would allow us to gain complete control . And if we needed to fix something, adjust or adapt - we could do it. ”
What options?
The basic option is to take the vanilla Linux kernel, build the special-purpose systems on it yourself.

Alt Linux distribution has received FSTEC certificate

Astra Linux Common Edition 1.10 review


Astra Linux has two editions of the Common Edition and Special Edition . The latter is just for critical objects.
Some examples of potentially vulnerable purchases.


Delivery "Deployment of video surveillance equipment at the facilities of the Ministry of Defense of Russia (according to specifications)" for the needs of the Ministry of Defense of the Russian Federation ( order 0173100000814000723 ). Used by Windows.
The cost of 575 105 938 rubles.
Despite the fact that the PACK runs on Linux, the operator workstation uses Windows, which is a critical component. See page 6 “Changes to the Notification and Documentation of the electronic auction for the supply of“ Deployment of video surveillance equipment at the facilities of the Russian Ministry of Defense (according to specification) ”.

Provision of services for installation and commissioning in idle autonomous post video and thermal surveillance "Video-Dozor" for the military unit 2148 ( purchase No. 0373100125315000033 ).Used by Windows.
The cost of 2 000 000 rubles.

Installation of the video surveillance system “Video-Frontier” ( Purchase No. 0306100000215000201 ) for the “Border Guard Directorate of the Federal Security Service of the Russian Federation in the Republic of Karelia”. Used by Windows.
The cost of 12 424 687 rubles.
 Supply of an integrated security system (1200 meters perimeter kit) for the Federal Penitentiary Service of Russia. ( Purchase No. 0373100065014000126 ). Used by Windows.
Supply of an integrated security system (1200 meters perimeter kit) for the Federal Penitentiary Service of Russia. ( Purchase No. 0373100065014000126 ). Used by Windows.The cost is 98,270,819 rubles.
Supply of equipment for video surveillance and security systems for FSIN in the Krasnoyarsk Territory (Purchase No. 0319100023215000049 ). Used by Windows.
The cost of 1 363 119 rubles.
Supply of equipment for video surveillance systems for the needs of the federal state institution "Correctional colony No. 1 of the Federal Penitentiary Service of the Kostroma region." ( Purchase No. 0341100008615000244 ). Used by Windows.
The cost of 374,081 rubles.

A complex of works (development of working documentation, construction and installation works, commissioning works) on the implementation of a video surveillance system for Smolensk NPP . Used foreign software "CMS" and Windows is used.
 Modernization of video surveillance systems at the Small Sports Arena for the needs of AO "Luzhniki" ( purchase No. 31502412367 ). Used by Windows and video surveillance company Milestone, Denmark.
Modernization of video surveillance systems at the Small Sports Arena for the needs of AO "Luzhniki" ( purchase No. 31502412367 ). Used by Windows and video surveillance company Milestone, Denmark.The cost of 12 million rubles.
 Construction, commissioning and commissioning works on equipping the transport infrastructure and LTS 1, Lines 2 and Severnoye Electropanel with the Unified Digital Radio Communication System as part of the Comprehensive Transport Safety Program for the population St. Petersburg ( purchase number 072200002514000087 ). Used by Windows.
Construction, commissioning and commissioning works on equipping the transport infrastructure and LTS 1, Lines 2 and Severnoye Electropanel with the Unified Digital Radio Communication System as part of the Comprehensive Transport Safety Program for the population St. Petersburg ( purchase number 072200002514000087 ). Used by Windows.Cost 197 106 801rubles.

Implementation of engineering and engineering systems to ensure transport safety of the most vulnerable transport infrastructure on the M-29 Kavkaz highway ( purchase No. 0318100043415000069 ). Used by Windows.
The cost of 139 164 194 rubles.

Open tender for the right to conclude a Contract for the execution of works on the installation of engineering and technical security systems at the most vulnerable objects of transport infrastructure on the highway of the State Company Avtodor M-4 "Don" - from Moscow through Voronezh, Rostov-on-Don, Krasnodar to Novorossiysk “Bridge across the Don River km 1061 + 569 (left, right)” ( №31502313606 ).Used by Windows.
| Developer | - | / | |||
|---|---|---|---|---|---|
| AxxonNext | ITV | Windows | Windows | JAVA | a source |
| Domination | Linux | Windows | HTML | a source | |
| Macroscop | Macroscop | Windows | Windows | HTML | a source |
| Orwell 2k | «- ()» | Windows | Windows | not | a source |
| SecurOS | ISS | Windows | Windows | JAVA | a source |
| TRASSIR | DSSL | Linux | Windows , MacOS | not | a source |
| ITV | Windows | Windows | JAVA | a source | |
| Windows | Windows | not | a source | ||
| Linux | Linux , Windows | HTML | a source | ||
| - | « ()» | JAVA | JAVA | not | a source |

Conclusion
- Windows, JAVA
- 90%
- , ,
Add. :
A star named Linux: why are the “military” OSs stronger than May 10, 2011 The
document that was waited for May 25, 2015
Protection of automated process control systems in Russia: investigating new requirements of FSTEC November 11, 2014
Cryptography - FSTEC! June 5, 2014
Crowdsourcing in the development of state standards May 20, 2013
Protection in a virtual environment: the threat list of threats March 15, 2012
Alt Linux distribution received FSTEC certificate April 21, 2011
Reflections on state certification of antiviruses April 14, 2011
Astra Linux Common Edition 1.10 Review February 16, 2015
Astra Linux Special Edition
Source: https://habr.com/ru/post/262535/
All Articles