Do the opposite or portable channel for secure data transmission
Introduction
A year ago, when I was still in the 10th grade, I took up cryptography. More precisely, how I did it: at school it was necessary to conduct research work - so I decided to investigate the RSA cipher. Due to the lack of knowledge for research on persistence, a rather dubious study was conducted (from the point of view of utility) at the time of generating keys and encrypting some text depending on the key size based on its own implementation of the algorithm. Having taken places at several scientific conferences, I almost left the whole area. It was even slightly lost code. However, while I was writing the RSA, I had been reading all sorts of things about how our data flowed into the "drainpipe." And this sad thought, having lain in my head for three months, found itself in the idea of a new project. It was decided to make a device that would allow to keep at least some part of the correspondence in secret
Planning and Implementation
As I said, it was decided to make the device. Why? Perhaps, for most people who "live" on Habré, such articles will seem like a yellow press, but still . Rumors do not come from nowhere. Therefore, such a scheme was developed:
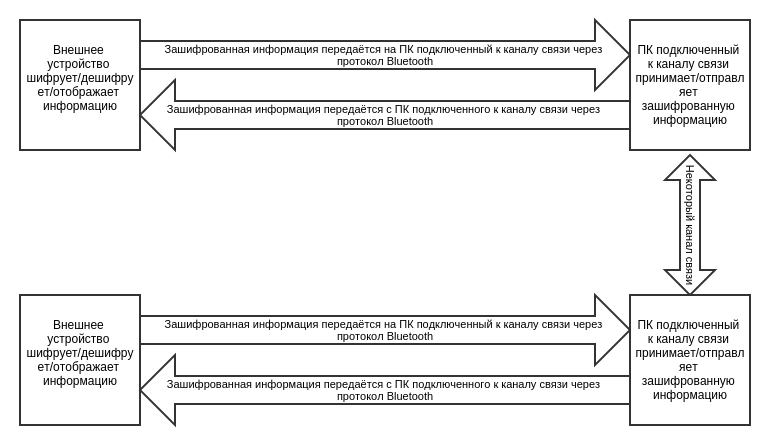
This is where we act “the opposite”. Most often (as far as I have access to this “more often”) a device that encrypts information is input / output from a computer, encrypting the entire flow of information. We are the entrance doing the computer.
')
Unfortunately, the experience in PCB layout was '-1', there was no money for specialists either, so there was no one to help, so I tried to choose the least of the evils existing. Raspberry Pi seemed the best option. There, both Linux and an external screen can be connected, UART, USB, in general, everything that could be useful. To him, I got (I was given) a DVK511 expansion board with a two-way screen and a joystick for complete PC I / O isolation.
It turned out something like this:

As one of the main ideas was the mobility of such a device. It should not have been expensive, be easily portable from PC to PC, work with the maximum number of OS. What is more important - no own channels. Poured into existing systems. Then it was decided to do so:
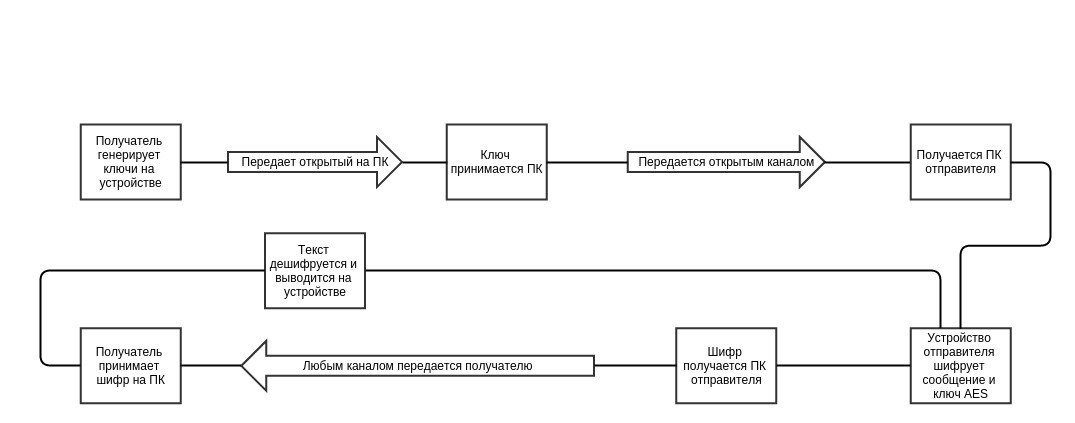
As an asymmetric cipher, I decided to use the RSA already implemented by me with a long key of 4096 bits, and symmetric chose AES 256 bits as one of the most common (I used the Open SSL implementation to save time (I was already sawed all around, so I don’t prepare )).
I decided to implement everything on QT - I bought it cross-platform.
Regarding the GUI and encryption, perhaps, the problems arose the least. I’ll never talk about GUI, with QT, implementing a simple GUI is a 15 minute task. In encryption, the main thing is to accurately convert the RAW code to numbers and vice versa, so that the cipher can be transmitted without loss in plain text.
Then it got worse. The advantages of the board include the fact that the library for C is still present and there are even examples ... Perhaps, for me, they ended up on this. It turned out that the joystick is hanging on the same ports as the screen and using them at the same time will not work. Well, more precisely, how: after each pressing of the joystick, you have to close access to it, open access to the display, then display information, close access to the display, activate the joystick. Accordingly, each operation takes time. In general, if you decide to make such a device yourself - take another board and look at its pinout in advance.
And the saddest thing is the transfer to PC. All of the above is ready, before the conference is less than a week, I am joyful running after the Bluetooth module for Raspberry. Bought. I come. And I do not understand ... From there, the files are transferred, back - no. How so? Understand it never happened. And access set for everyone, and changed the Bluetooth settings. As a result, the decision came at the last moment. Well, not a solution, but a crutch. In order for everything to work, it was decided to mount part of the PC disk, from where the files are taken and collected.
It makes no sense to spread the full cycle of work. But entering text for encryption looks like this:
Conclusion
Is it possible to guarantee that such a device will fully protect your information? I will not dissemble: my - no. However, the very concept of taking out input information on a completely isolated device should work. However, if you decide to plan a global plot or encrypt the correspondence with your mistress from your wife working in the FSB, then I would recommend adding a hardware random number generator and layering others on top of some algorithms (for example , on elliptic curves (for example, GOST R 34.10-2012)), which will increase the chance that the whole backdoors will not be found. It would also be ideal to erase the board yourself.
One more. If you are more successful than me with OBEX technology, you can teach the device to work with absolutely any other device that has a text editor. You can simply send commands and encrypted messages with text files.
Are there analogs? A good question ... I was asked the same by the “distinguished” guests who came to the last conference in which I participated. We all understand that information protection devices, despite all the Kirkgoffs principles, for the most part remain classified, but I could not find such devices in the public domain, which I reported, complaining that little is known about them. In response, they told me that maybe you should not keep information on such information publicly available? But they seemed interested in the work, took the phone, email. Only here it was a long time ago, and no one got involved.
In general, I support the fact that the right to privacy of personal information is no less important than the right to freedom of speech. When writing an article, I faced the question: is it worth it to publish a link to the source? It seems to me that any professional programmer can implement such a device in no more than 10 long winter evenings, and then why would he need my code, which for the most part is “for it to work”. However, if anyone needs it, I can share the repository: write to the LAN.
At the moment, work has been postponed to a distant repository due to lack of funds and insufficient theoretical training.
Source: https://habr.com/ru/post/262469/
All Articles