Apps from Google Play specialize in stealing Facebook credentials
The application called Cowboy Adventure is quite popular in the Google Play app store with the number of installations from 500 thousand to 1 million. This application is a game and has malicious activity, as it is used by the authors to collect the credentials of user accounts of the social network Facebook. Another application we found with similar malicious capabilities is called Jump Chess.


Fig. The Cowboy Adventure app on Google Play.
')

Fig. Jump Chess application in Google Play.
Unlike the real malware for Android, which we considered earlier, these applications contain the normal capabilities indicated in the description of the application. However, when launching these applications, they show the user a window that prompts you to enter your Facebook account credentials. In the case of performing this action, the entered credentials will be sent to the attacker's remote server.

Fig. A fake Facebook credential entry window that is displayed by the application.
The bad news is that at the time of the removal of this program from Google Play, its version was already 1.3. The application itself has been available for download at least since April 16, 2015, when it was once again updated. However, we are not sure that the first versions of this application contained these malicious features, we also do not know how many Facebook accounts were compromised.
Another application from the same developer is called Jump Chess and it was available for download a little earlier, from April 14, 2015. Jump Chess was much less successful because it gained from 1 thousand to 5 thousand installations.
The good news is that Google has already removed both applications from the store, and also warns Android users about installing them on the device.
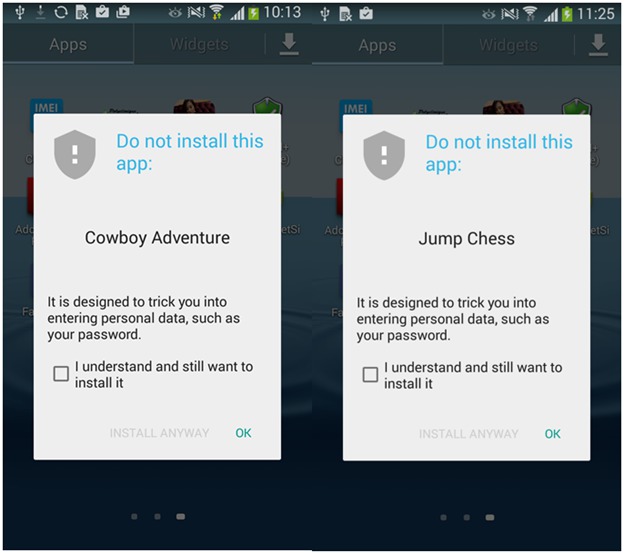
Fig. A window warning that the application you are installing contains malicious activity.
Earlier, we pointed out that Android’s security mechanisms have been significantly improved by Google, which reduces the risk of malware infection of this mobile OS. At the same time, they are still not enough to ensure complete security of the user of the mobile device.
Another good news is the fact that not all those users who installed the above software on their devices trusted him with their social network credentials. This is evidenced by negative user comments to applications.

Fig. Negative user comments to the Cowboy Adventure app.
Analysis of malicious applications shows that they were written in C # using the Mono Framework. Malicious code is located in the TinkerAccountLibrary.dll library. The application communicates with the C & C server via a secure HTTPS connection. Attackers use another server known as the “Drop Zone” to collect stolen data. The malware gets its address dynamically during its operation.
To protect against this kind of unwanted programs should be aware of the following safety rules.


Fig. The Cowboy Adventure app on Google Play.
')

Fig. Jump Chess application in Google Play.
Unlike the real malware for Android, which we considered earlier, these applications contain the normal capabilities indicated in the description of the application. However, when launching these applications, they show the user a window that prompts you to enter your Facebook account credentials. In the case of performing this action, the entered credentials will be sent to the attacker's remote server.

Fig. A fake Facebook credential entry window that is displayed by the application.
The bad news is that at the time of the removal of this program from Google Play, its version was already 1.3. The application itself has been available for download at least since April 16, 2015, when it was once again updated. However, we are not sure that the first versions of this application contained these malicious features, we also do not know how many Facebook accounts were compromised.
Another application from the same developer is called Jump Chess and it was available for download a little earlier, from April 14, 2015. Jump Chess was much less successful because it gained from 1 thousand to 5 thousand installations.
The good news is that Google has already removed both applications from the store, and also warns Android users about installing them on the device.

Fig. A window warning that the application you are installing contains malicious activity.
Earlier, we pointed out that Android’s security mechanisms have been significantly improved by Google, which reduces the risk of malware infection of this mobile OS. At the same time, they are still not enough to ensure complete security of the user of the mobile device.
Another good news is the fact that not all those users who installed the above software on their devices trusted him with their social network credentials. This is evidenced by negative user comments to applications.

Fig. Negative user comments to the Cowboy Adventure app.
Analysis of malicious applications shows that they were written in C # using the Mono Framework. Malicious code is located in the TinkerAccountLibrary.dll library. The application communicates with the C & C server via a secure HTTPS connection. Attackers use another server known as the “Drop Zone” to collect stolen data. The malware gets its address dynamically during its operation.
To protect against this kind of unwanted programs should be aware of the following safety rules.
- To download applications, use the proprietary Google Play resource, not third-party stores or other unknown sources. Even if Google Play cannot protect users from installing malware at 100%, it has serious security measures to control applications.
- Download applications only trusted developers and track their rating, as well as comments of other users to them in the store. The fraudulent actions of Cowboy Adventure were quickly noticed by users who indicated this in the comments. You should also carefully look at the permissions that the application requests for its work.
- Use anti-virus software for your device to help protect you from various kinds of malware. Antivirus product ESET Mobile Security detects specified applications as Android / Spy.Feabme.A .
Source: https://habr.com/ru/post/262265/
All Articles