Network Security, Part 2. Next-Generation Firewall
If you look at the interactive map of current cyber attacks taking place in the world, in real time, it becomes obvious that the only place where there is no criminal cyber activity on Earth is Antarctica. 2014 was rich in loud hacks and data leaks. Hacking Apple iCloud followed by uploading intimate photos of various famous people to the network, data leakage of 80 million customers from JP Morgan, Trojan in Regin on computers of the EU administration, hacking eBay, hacking Home Depot, DDoS attack on the Kremlin website, hacking the Moscow Metro network and etc. However, Sony Entertainment's hacking is remarkable for the fact that over the past three years, the company's infrastructure has been hacked for at least a third time. Therefore, before talking about modern network protection tools, I will briefly describe the strategy for implementing a network attack using the example of one of the most famous attacks of the last time - the attack on Sony Pictures Entertainment 2014.
A few words about what actually happened. On Friday, November 21, 2014, Sony executives received a letter inviting them to pay a certain amount for Sony’s IT infrastructure to avoid "massive bombardment." The letter did not attach importance, many managers got it in spam, but already on November 24, 2014, Sony employees came to work on Monday morning and saw the following picture on their monitors:

Most of the company's computers and IT services were inoperable. According to some sources, over the next few days, Sony employees did not use work computers and worked with a pen and paper. In the course of this attack (it is believed that the hidden phase of the attack developed from several months to a year), Sony leaked data (according to some estimates, with a total volume of up to 100 terabytes) to millions of dollars. Subsequently, the hackers posted on the network a few new, not yet released on the screens of films and a large amount of confidential information, including personal data of employees. According to various estimates, the approximate cumulative damage from this attack was about $ 100 million.
')
How did this happen and, most importantly, why?
The malicious program that participated in the attack on Sony Entertainment is called the Destover Trojan; This is wiper -type malware that can delete data from hard drives and rewrite the MBR as needed. A wave of similar attacks using various wipers has swept since 2012 in Central Asian countries (an attack on Saudi Aramco, with data destruction on more than 30,000 computers, an attack on Qatari Rasgas, etc.) and has ended with a loud story with Sony .
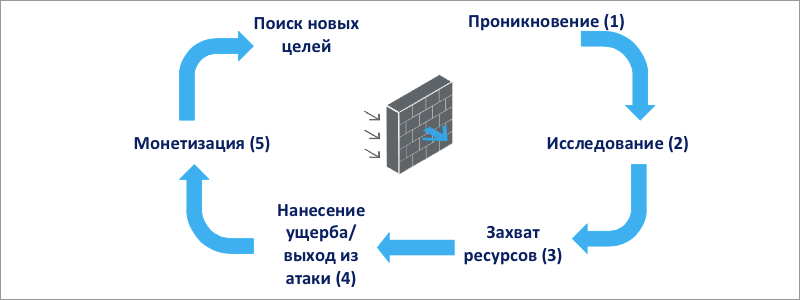
According to experts, the attackers apparently got full access to the Sony Entertainment internal network before they started distributing this Trojan to computers within the network. They acted according to the classic attack pattern shown in the figure below.
Attack life cycle:
The question remains - why is it not the first time that happens with such a large and well-known company like Sony? According to experts, one of the key security problems at Sony is that their protection system was built on reactive principles and, as the subsequent audit of the infrastructure showed, potential threats were not recognized and prevented in time. The third loud hacking for three years clearly says that Sony needs to change something in the structure of network security and focus, apparently, on pro-active processing and prevention of threats.
Sony's case and the rest of the hacking and data breaches of recent years confidently confirm that in order to combat emerging threats, businesses need to invest in next-generation network security tools that eliminate the shortcomings of traditional security technologies. For example, the next generation firewall (NGFW) was created primarily as a response to the inability of traditional Stateful FW to detect threats in application traffic, for example, in http traffic. In addition, an important feature of NGFW is the ability to identify traffic and bind it to a specific user.
GARTNER defines NGFW like this: new generation firewalls (NGFWs) are devices that perform deep packet inspection (going beyond the port / protocol), with the ability to inspect and block application-level traffic, including embedded intrusion prevention systems and intelligent processing traffic based on integration with external systems. At the same time, NGFW should not be confused with isolated Intrusion Prevention System (IPS) or IPS, which includes a regular firewall that is not integrated with IPS in one solution. To summarize this definition briefly, the NGFW is a device with application-level traffic control, a built-in intrusion detection system and identification of the traffic user identity .
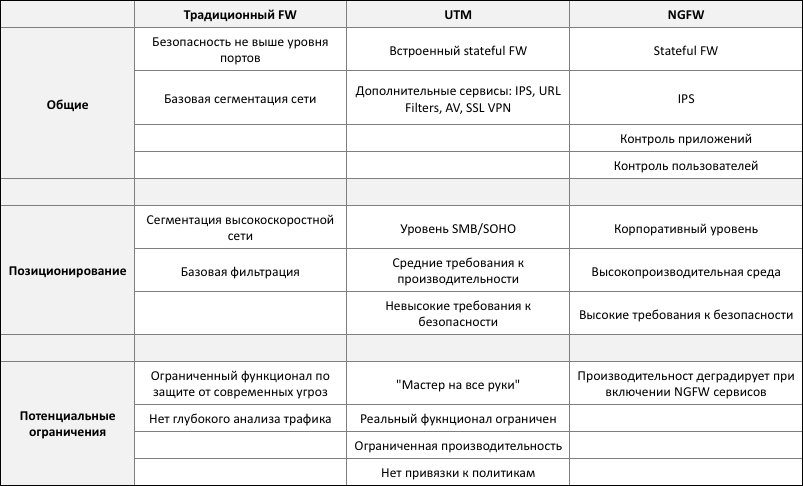
For some, the emergence of the NGFW concept causes a “déjà vu” effect, there is a feeling of similarity between NGFW and the UTM (Unified Threat Management) concept common in the recent past. These are really similar approaches, attempts to effectively combine protection against several types of threats in one device at once. However, there are significant differences that allow us to unambiguously separate these classes of devices among themselves and separate them from the traditional Stateful Firewall (hereinafter referred to as simply FW). The table below summarizes the basic parameters and positioning of the FW, UTM and NGFW devices.
Thus, UTM and NGFW are different classes of equipment designed to solve different types of problems. And as GARTNER predicts to us, the time of traditional devices providing network protection is gradually leaving and new devices of a new type, NGFW, are coming to replace them.
In 2013, HP announced the release of the HP TippingPoint Next-Generation Firewall (NGFW). HP NGFW is built in accordance with the above concept and is designed to meet the needs of enterprises of different sizes in terms of network security, taking into account modern requirements for network efficiency, reliability and scalability of solutions. NGFW is implemented on the NGIPS platform with a reliability of 7 nines (99.99999% uptime) and allows you to identify and control network applications, reducing the potential risks of the company from the implementation of complex network threats. In addition, for those who already have HP TippingPoint products installed (NGIPS, for example) or someone plans to deploy a large number of NGFW, it would be convenient for such enterprises to use a single centralized console based on their security management system (SMS) for managing network security.
A remarkable feature of the HP NGFW solution is the presence in HP of a structure (DVLabs), which is engaged in the search for vulnerabilities in software of various manufacturers and in the release of corresponding updates closing them. Summary statistics on the work of DVLabs, today:
Participation in the development of filters by external experts allows you to develop truly high-quality filters. By focusing on the root cause, such a filter allows you to identify threats leaking through predefined pattern attacks. Moreover, the filters are designed in such a way that their application has a minimal effect on the overall performance of the solution.
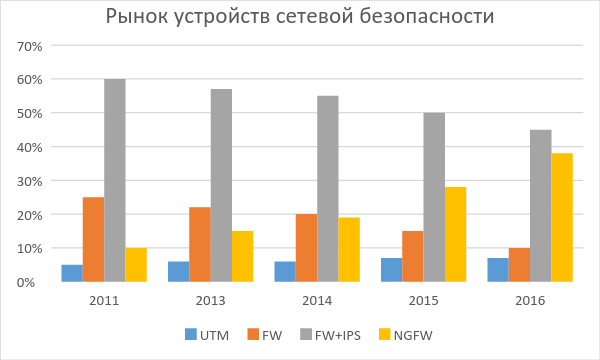
Regarding the processing of application traffic, HP TippingPoint NGFW can control traffic at the type of application as well as at the level of its various sub-types. At the same time, HP focuses on key business applications relevant to the corporate environment. The graph below confirms that this policy is bearing fruit - in this area HP is the leader.
Let's say a few words separately about the Zero Day Initiative (ZDI) program - what it is and why it is important. In Zero Day Exploit is a software vulnerability that is not yet known to the vendor and this is a security hole that can be exploited by hackers even before the vendor realizes it and tries to fix it. Attempts to exploit a vulnerability may be different and include attempts to introduce malware / spyware into the infrastructure, attempts to access user information, etc. As soon as it becomes known about the vulnerability, the race begins between the attackers and developers, who will release the appropriate software faster - exploit hackers or patch developers. And hackers in this race often win, for various reasons (the inertia of the developer’s company, users do not immediately install the corresponding patches, etc.). With the ZDI program, HP is proactive in this race and tries to act proactively, detecting and closing vulnerabilities before attackers find and implement them. Recalling the case of Sony, which was discussed at the beginning of the article, I dare to suggest that using ZDI could significantly help in the implementation of a pro-active strategy to protect the company and perhaps the last attack would not have such devastating consequences.
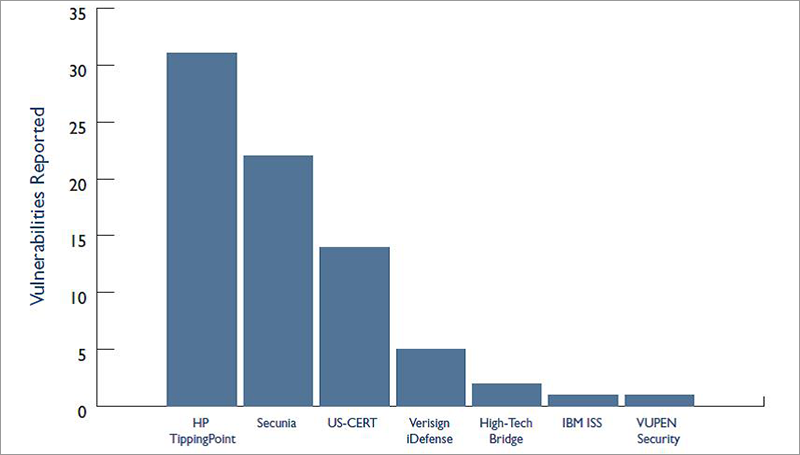
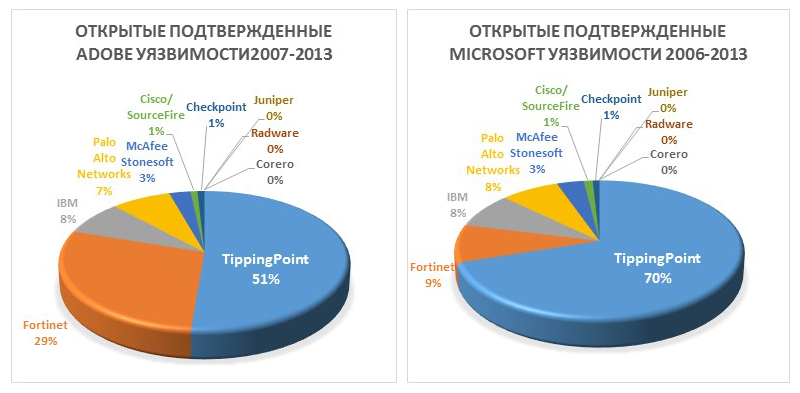
This program has significantly expanded the scope of information security research, as well as significantly reduced the number of vulnerabilities entering black markets. As a result of the ZDI program, HP is recognized as the leading reporter for vulnerabilities, as shown in the diagrams below.

Further a bit more in detail about product HP NGFW. To date, on sale there are 5 different models of the device, which differ primarily in performance. The table below shows devices with brief characteristics and recommended options for their use.

Key functional features of NGFW are summarized below:
Thank you for your attention, to be continued.
A few words about what actually happened. On Friday, November 21, 2014, Sony executives received a letter inviting them to pay a certain amount for Sony’s IT infrastructure to avoid "massive bombardment." The letter did not attach importance, many managers got it in spam, but already on November 24, 2014, Sony employees came to work on Monday morning and saw the following picture on their monitors:

Most of the company's computers and IT services were inoperable. According to some sources, over the next few days, Sony employees did not use work computers and worked with a pen and paper. In the course of this attack (it is believed that the hidden phase of the attack developed from several months to a year), Sony leaked data (according to some estimates, with a total volume of up to 100 terabytes) to millions of dollars. Subsequently, the hackers posted on the network a few new, not yet released on the screens of films and a large amount of confidential information, including personal data of employees. According to various estimates, the approximate cumulative damage from this attack was about $ 100 million.
')
How did this happen and, most importantly, why?
The malicious program that participated in the attack on Sony Entertainment is called the Destover Trojan; This is wiper -type malware that can delete data from hard drives and rewrite the MBR as needed. A wave of similar attacks using various wipers has swept since 2012 in Central Asian countries (an attack on Saudi Aramco, with data destruction on more than 30,000 computers, an attack on Qatari Rasgas, etc.) and has ended with a loud story with Sony .
According to experts, the attackers apparently got full access to the Sony Entertainment internal network before they started distributing this Trojan to computers within the network. They acted according to the classic attack pattern shown in the figure below.
Attack life cycle:

- Penetration (infiltration) - it is not known for certain (at least, it has not been disclosed publicly) how the hackers initially penetrated the Sony network this time. Three versions are supposed - insider help, classic phishing, or exploiting a vulnerability in web services followed by backdoor. Ultimately, hackers gained access to the Sony network with administrator privileges.
- Research - further hackers built a network map and IT resources of Sony Entertainment, received account names and administrator passwords, access certificates, etc.
- Resource Capturing - having a resource map and all the necessary credentials to access it, hackers began to deploy malware on company resources and in parallel to steal / transfer beyond the limits of the Sony infrastructure valuable data.
- Damage and exit from attack - at this stage the wiper installed on the resources overwrites the data on the company's hard drives and eliminates traces.
- Monetization - the hackers tried to monetize the attack by offering Sony Entertainment executives a ransom to prevent the destruction of IT infrastructure and the disclosure of confidential information. After the refusal, hackers began to spread the stolen confidential data to the public network.
The question remains - why is it not the first time that happens with such a large and well-known company like Sony? According to experts, one of the key security problems at Sony is that their protection system was built on reactive principles and, as the subsequent audit of the infrastructure showed, potential threats were not recognized and prevented in time. The third loud hacking for three years clearly says that Sony needs to change something in the structure of network security and focus, apparently, on pro-active processing and prevention of threats.
Sony's case and the rest of the hacking and data breaches of recent years confidently confirm that in order to combat emerging threats, businesses need to invest in next-generation network security tools that eliminate the shortcomings of traditional security technologies. For example, the next generation firewall (NGFW) was created primarily as a response to the inability of traditional Stateful FW to detect threats in application traffic, for example, in http traffic. In addition, an important feature of NGFW is the ability to identify traffic and bind it to a specific user.
GARTNER defines NGFW like this: new generation firewalls (NGFWs) are devices that perform deep packet inspection (going beyond the port / protocol), with the ability to inspect and block application-level traffic, including embedded intrusion prevention systems and intelligent processing traffic based on integration with external systems. At the same time, NGFW should not be confused with isolated Intrusion Prevention System (IPS) or IPS, which includes a regular firewall that is not integrated with IPS in one solution. To summarize this definition briefly, the NGFW is a device with application-level traffic control, a built-in intrusion detection system and identification of the traffic user identity .
For some, the emergence of the NGFW concept causes a “déjà vu” effect, there is a feeling of similarity between NGFW and the UTM (Unified Threat Management) concept common in the recent past. These are really similar approaches, attempts to effectively combine protection against several types of threats in one device at once. However, there are significant differences that allow us to unambiguously separate these classes of devices among themselves and separate them from the traditional Stateful Firewall (hereinafter referred to as simply FW). The table below summarizes the basic parameters and positioning of the FW, UTM and NGFW devices.

Thus, UTM and NGFW are different classes of equipment designed to solve different types of problems. And as GARTNER predicts to us, the time of traditional devices providing network protection is gradually leaving and new devices of a new type, NGFW, are coming to replace them.

In 2013, HP announced the release of the HP TippingPoint Next-Generation Firewall (NGFW). HP NGFW is built in accordance with the above concept and is designed to meet the needs of enterprises of different sizes in terms of network security, taking into account modern requirements for network efficiency, reliability and scalability of solutions. NGFW is implemented on the NGIPS platform with a reliability of 7 nines (99.99999% uptime) and allows you to identify and control network applications, reducing the potential risks of the company from the implementation of complex network threats. In addition, for those who already have HP TippingPoint products installed (NGIPS, for example) or someone plans to deploy a large number of NGFW, it would be convenient for such enterprises to use a single centralized console based on their security management system (SMS) for managing network security.
A remarkable feature of the HP NGFW solution is the presence in HP of a structure (DVLabs), which is engaged in the search for vulnerabilities in software of various manufacturers and in the release of corresponding updates closing them. Summary statistics on the work of DVLabs, today:
- 8,200+ out-of-the-box filters
- Approximately 20 new filters per week
- Every 12th filter is a Zero Day filter.
- 379 zero day filters released in 2014
- Average pre-vulnerability coverage with a zero day filter of 50 days
- 10% application filters
- 40% of filters are run by default in recommended settings.
- 3,000 researchers participate in HP Security Research Zero Day
Participation in the development of filters by external experts allows you to develop truly high-quality filters. By focusing on the root cause, such a filter allows you to identify threats leaking through predefined pattern attacks. Moreover, the filters are designed in such a way that their application has a minimal effect on the overall performance of the solution.
Regarding the processing of application traffic, HP TippingPoint NGFW can control traffic at the type of application as well as at the level of its various sub-types. At the same time, HP focuses on key business applications relevant to the corporate environment. The graph below confirms that this policy is bearing fruit - in this area HP is the leader.

Let's say a few words separately about the Zero Day Initiative (ZDI) program - what it is and why it is important. In Zero Day Exploit is a software vulnerability that is not yet known to the vendor and this is a security hole that can be exploited by hackers even before the vendor realizes it and tries to fix it. Attempts to exploit a vulnerability may be different and include attempts to introduce malware / spyware into the infrastructure, attempts to access user information, etc. As soon as it becomes known about the vulnerability, the race begins between the attackers and developers, who will release the appropriate software faster - exploit hackers or patch developers. And hackers in this race often win, for various reasons (the inertia of the developer’s company, users do not immediately install the corresponding patches, etc.). With the ZDI program, HP is proactive in this race and tries to act proactively, detecting and closing vulnerabilities before attackers find and implement them. Recalling the case of Sony, which was discussed at the beginning of the article, I dare to suggest that using ZDI could significantly help in the implementation of a pro-active strategy to protect the company and perhaps the last attack would not have such devastating consequences.
This program has significantly expanded the scope of information security research, as well as significantly reduced the number of vulnerabilities entering black markets. As a result of the ZDI program, HP is recognized as the leading reporter for vulnerabilities, as shown in the diagrams below.


Further a bit more in detail about product HP NGFW. To date, on sale there are 5 different models of the device, which differ primarily in performance. The table below shows devices with brief characteristics and recommended options for their use.
| Branches / small networks | Corporate Networks | Data center |
| HP NGFW S1050F | HP NGFW S3010F / S3020F | HP NGFW S8005F / S8010F |
| 1RU | 2RU | 2RU |
| 500 Mbps | 1-2 Gbit / s | 5-10 Gbit / s |
| 10K new connections per second | 20K new connections per second | 50K new connections per second |
| 250K competitive compounds | 500K / 1M competitive compounds | 10M / 20M competitive compounds |



Key functional features of NGFW are summarized below:
- Easy to install, configure, and manage:
- Installs in minutes;
- “Install and forget” using the recommended IPS settings;
- Intuitive web interface;
- Central management using SMS:
- Manage NGFW and IPS in one console;
- Reuse of IPS and NGFW policies;
- Fast and convenient reports;
- Convenient analysis of events;
- RBAC based access;
- Over 8,000 predefined filters
- Focusing on vulnerabilities, not on implemented attacks
- Large investment in safety research;
- Built-in highly reliable (7 nines) IPS
- Policy size does not significantly affect performance.
- Fault tolerance (support of work in the “Active-Passive” mode)
Thank you for your attention, to be continued.
Source: https://habr.com/ru/post/262123/
All Articles