Wallix vs balabit. Comparison of admin control software [rdp]
Increasingly, large companies are thinking about controlling and tracking access to business-critical servers. Who went in, what did and when? Integrated logging is not always convenient and “readable”, and now products for the “control of privileged users” gradually began to enter the Russian market. It seemed to me interesting to compare the two "main" products of this line, namely, Balabit Shell Control Box and Wallix Admin Bastion.
Note: To reduce the length of the article, the comparison will be only in the context of the rdp protocol and the functional as a whole, resulting in a relatively general character. The ssh protocol is also supported by these products, but in this article it is NOT considered, so as not to interfere with everything "in one pile".
In our computerized time, the system administrator became almost the “king and god” of the Company's IT space. As a result of this, the management prefers not to interfere with them and, if possible, to make concessions, because leaving “in a bad way”, the former administrator can cause decent damage to the business. Therefore, the phrase “admin control” itself may seem to many top 5 employees to get rid of a delicate problem and a great solution, but ... is everything so simple? Of course not. Therefore, in the first place, I would like to briefly identify the companies in which really similar products can bring some kind of positive exhaust. The list was born on the basis of its own experience and does not claim to be the ultimate truth, i.e. is initially subjective.
So, "control admins" useful:
')
In other cases, the use of software to control admins, as a rule, is not advisable.
Both of the systems described below are a hardware or virtual appliance based on several modified unix systems: Wallix is deployed based on Debian, Balabit is ZorpOS. The required hardware capacity depends on the number of active users and the number of protected servers.
Wallix can only work in the "bastion" mode at the application level of the OSI model, i.e. put in a network break in an explicit form visible to the administrator. On the Wallix server, rules are configured (about them below), on the basis of which he skips \ blocks administrator connections. The administrator connects to the wallix server using the rdp protocol (standard port) and logs in with the help of the created local account (or imported from AD). After that, he is provided with an available list of pairs of server + final accounting, and he chooses the server he needs. Wallix itself can substitute the password for the final account, but you can also request this password from the administrator. For clarity, the logical connection diagram is shown below:
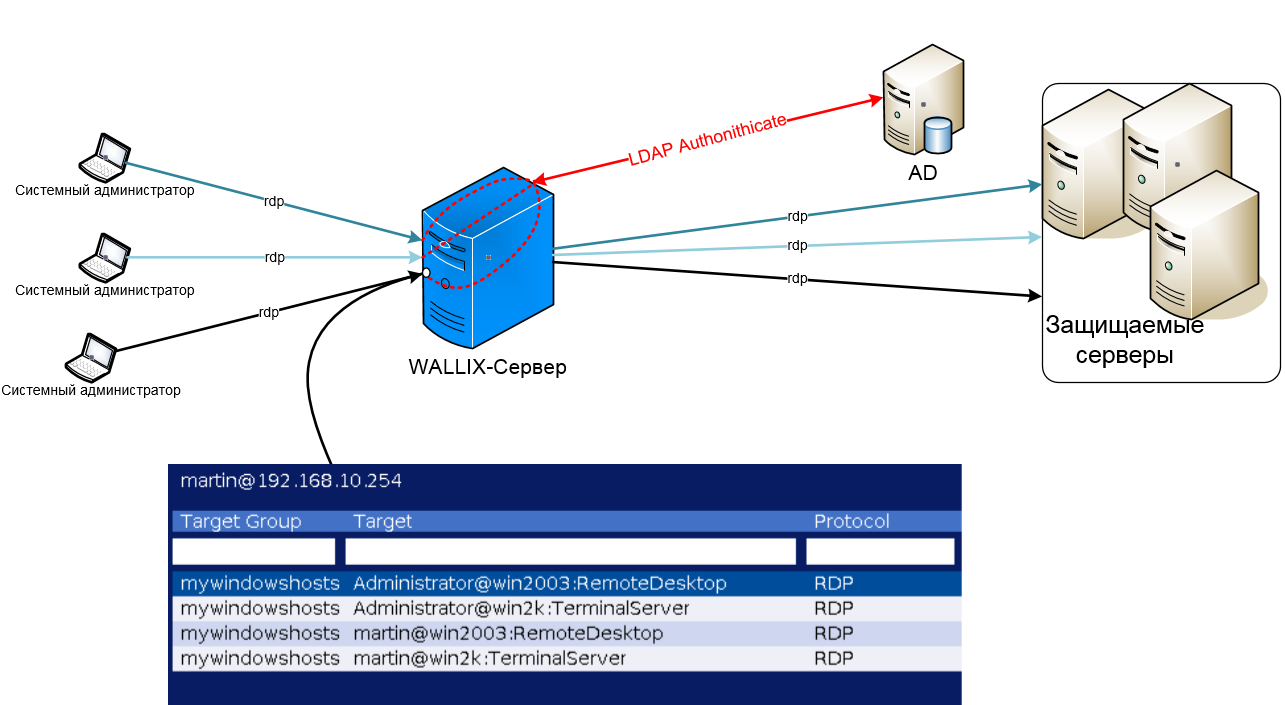
Logic diagram for connecting admins to protected servers via Wallix
The Wallix settings are binary (true-false \ can-not) mappings between two types of groups: groups of user accounts on Wallix itself (can be replaced with user accounts imported from AD) and a group of Server + final account pairs.
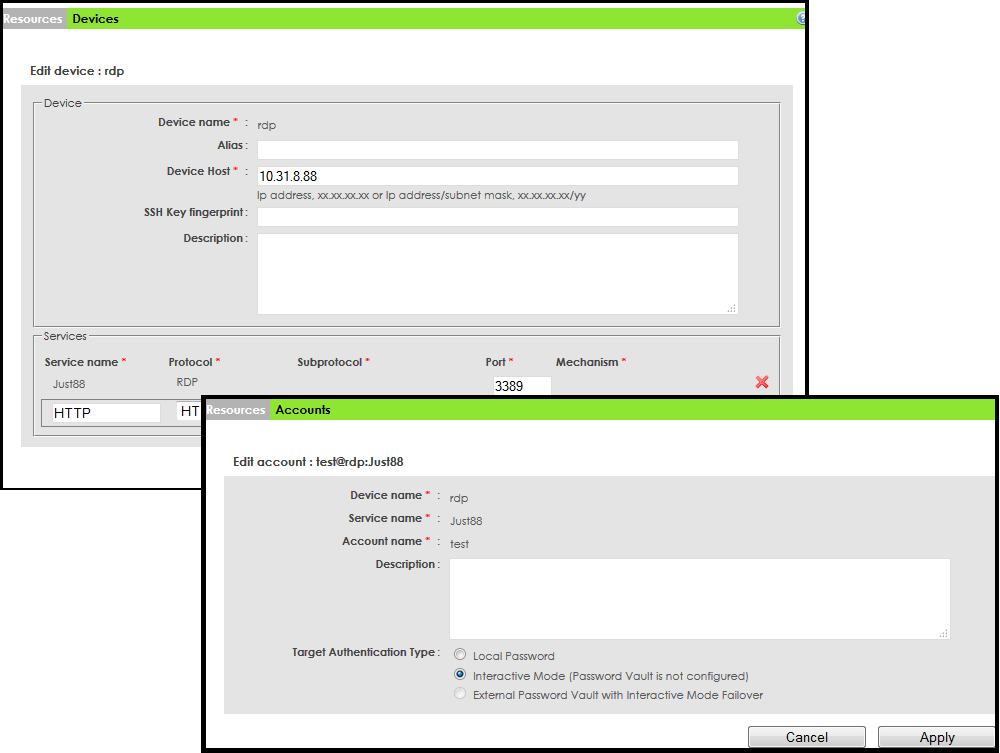
The form of adding / editing the protected server and the final account
The number of such comparisons, as well as the groups themselves, is not limited and on their basis an access matrix is built up to whom and where to connect.
Wallix stores rdp records in the form of video clips (in file form) that can be driven through the built-in text recognizer (ocr), and then searched by titles (search by titles within more than one video was promised to be screwed in the next versions).
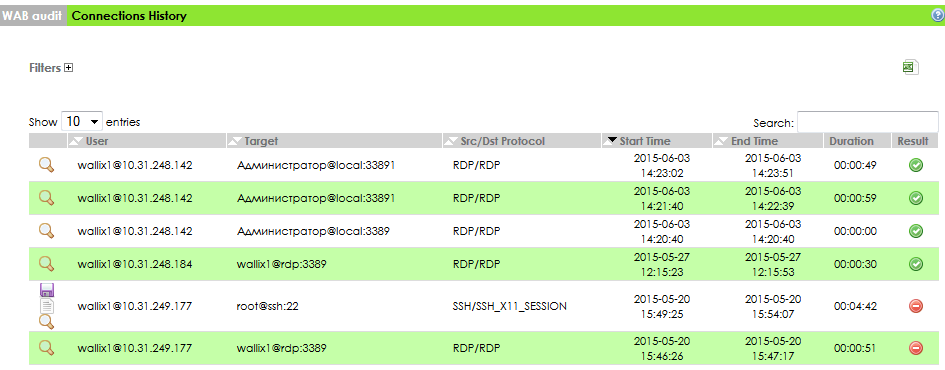
List of saved video records rdp-sessions
How can you "force" the admin to go to the right servers through wallix?
Product Benefits
Product cons
Balabit is also put in a “gap”, but it can work in several modes on different OSI models. At the same time, the setting of the "transparent" \ "opaque" mode is made directly in the connection itself, which is very convenient from the point of view of the "fine" setting of a particular connection.
The main advantage of Balabit is that it can work in a “transparent” mode, staying on the network in a form hidden to administrators. IP spoofing allows you to make it “invisible” even for FW and routers, substituting the PC administrator's IP address as ip-src, so there is no need to configure separate permissions for it on the network equipment.
For balabit to work in transparent mode, the corresponding routes are written on the router (that all traffic from the subnetwork N is sent to the Balabit IP address). At the same time, traffic that balabit cannot recognize (to detect controlled protocols in it) will be passed on without any further changes (to the specified gateway).
Note: in transparent mode, authorization is not performed on the balabit server, however, the system records, under what account, the administrator logged in to the protected server, which allows you to subsequently set the required filters and find the desired video clip.
The balabit settings have a cut on the protected servers - each server has its own instantaneous settings and access rights (for transparent mode: from which network you can connect to the protected server). The option of settings is presented below:
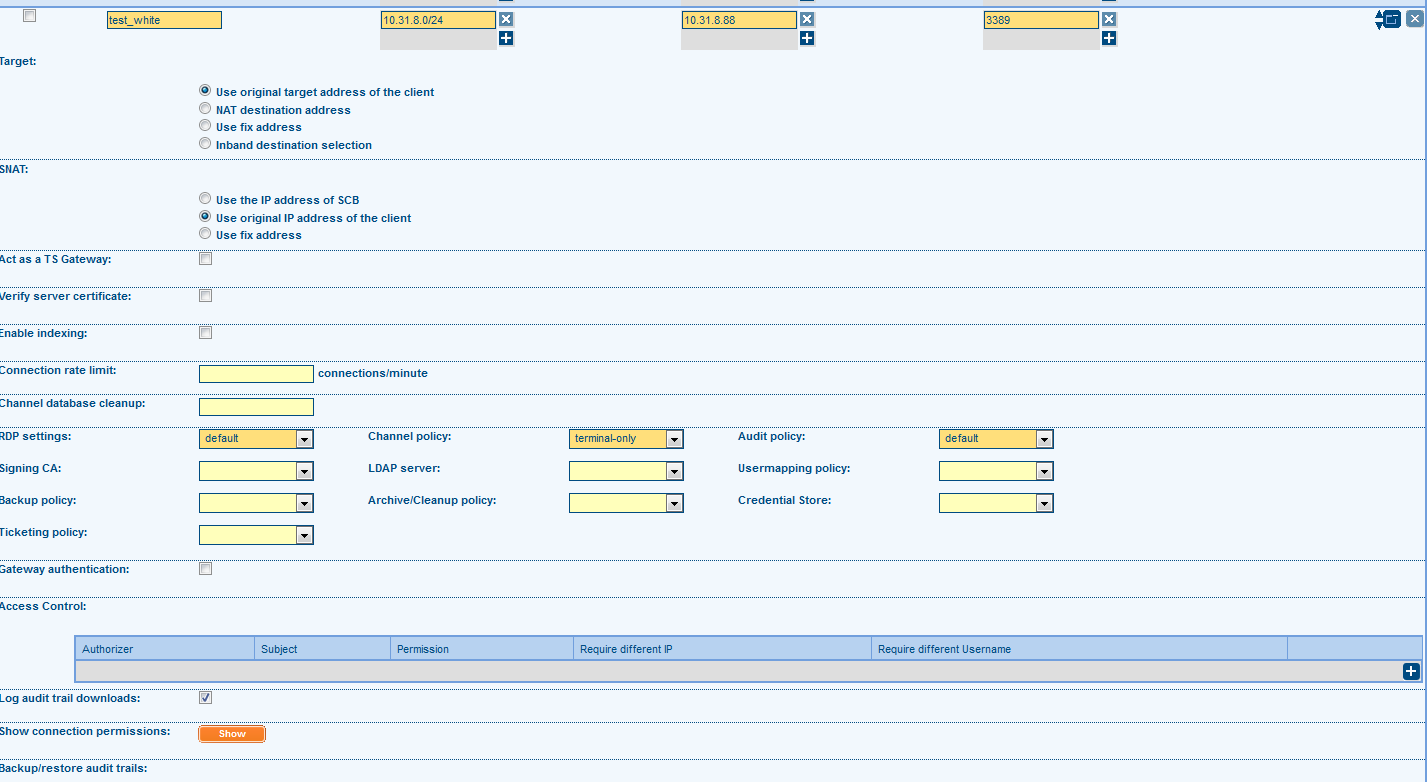
Settings for access to the protected server via balabit
In transparent mode, the main layer of settings falls on the routing of traffic and setting up network equipment. The settings on balabit itself are minimal and operate with ip-addresses from which they access protected servers, and not users and their rights, as implemented in Wallix.
Bastion mode has several implementations:
For each mode, there are their own settings, which now would not want to go deep. Suffice it to say that sometimes the eyes of the number of fields run up :))
The system also stores all the sessions in the form of video clips. OCR is produced once. The search for the recognized text in all videos is already present. To view the session, you need client software (Audit Player), which comes with the distribution kit and is installed on the operator's PC with MS-OS onboard.
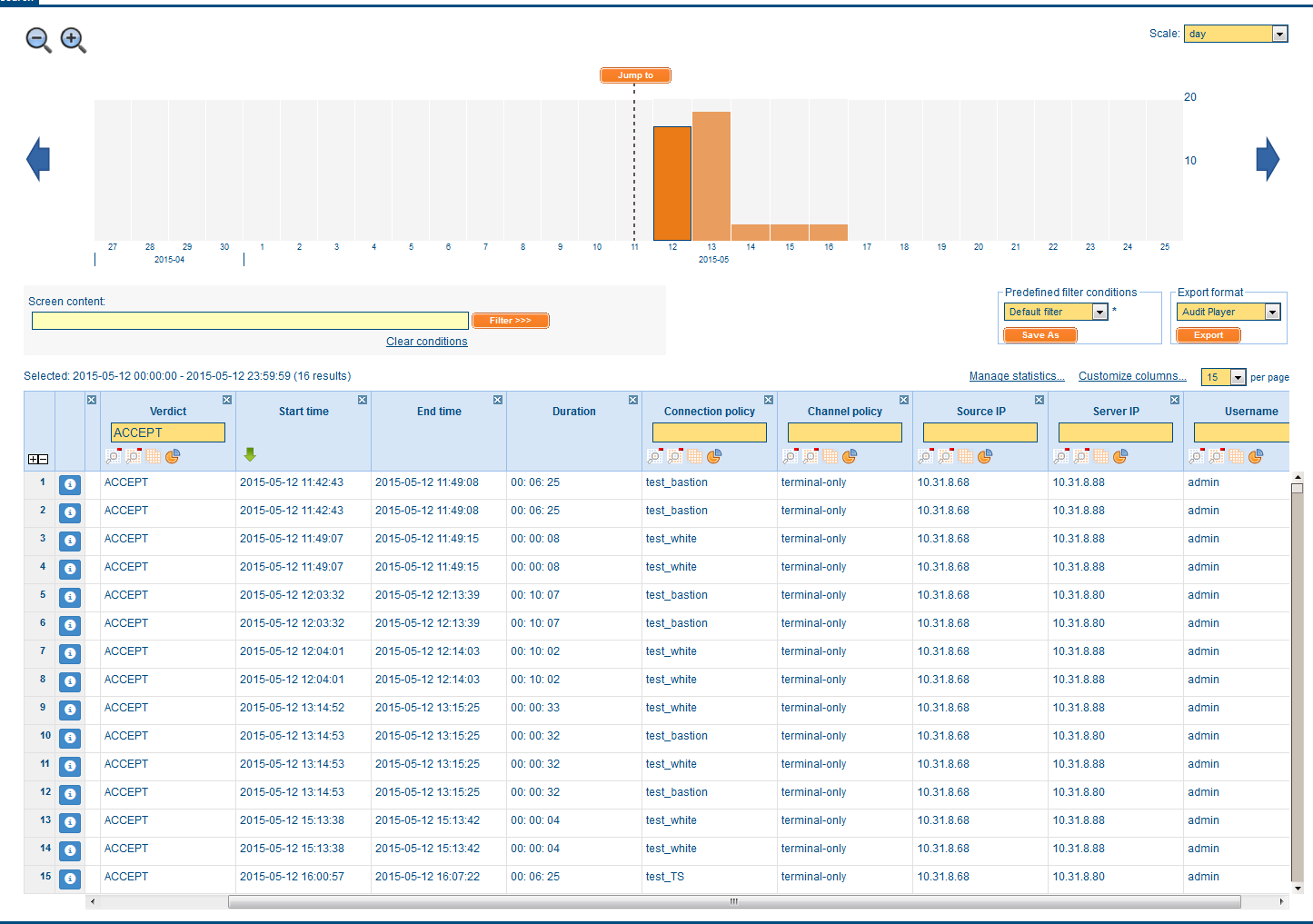
List of saved video records rdp-sessions
Product Benefits
Product cons
As can be seen from the text above, each product has its own strengths and weaknesses - it all depends on the pool of tasks assigned to it. The comparison did not involve all the capabilities of the systems.
I would also like to separately note that, by the type of Wallix, the CyberArk system is present on the market, which has a similar but more advanced functionality in the "bastion" mode. The basis of its work is the mechanism of MS Remote Application, which has increased the number of supported protocols and connectivity. Unfortunately, the author does not have sufficient competence to add it to the comparison, however, he considers it to be silent about it as criminal.
Note: To reduce the length of the article, the comparison will be only in the context of the rdp protocol and the functional as a whole, resulting in a relatively general character. The ssh protocol is also supported by these products, but in this article it is NOT considered, so as not to interfere with everything "in one pile".

Who needs admin control systems?
In our computerized time, the system administrator became almost the “king and god” of the Company's IT space. As a result of this, the management prefers not to interfere with them and, if possible, to make concessions, because leaving “in a bad way”, the former administrator can cause decent damage to the business. Therefore, the phrase “admin control” itself may seem to many top 5 employees to get rid of a delicate problem and a great solution, but ... is everything so simple? Of course not. Therefore, in the first place, I would like to briefly identify the companies in which really similar products can bring some kind of positive exhaust. The list was born on the basis of its own experience and does not claim to be the ultimate truth, i.e. is initially subjective.
So, "control admins" useful:
')
- Companies, the number of system administrators in which exceeds ~ 7-10 people;
- For companies whose IT support is provided by a third-party organization (outsourcing);
- Companies with specific software that need to be sent to the target servers of the vendor \ distributor;
- Companies that are tormented by regulators and require them to comply with different standards (did not encounter, but do not rule out).
In other cases, the use of software to control admins, as a rule, is not advisable.
Both of the systems described below are a hardware or virtual appliance based on several modified unix systems: Wallix is deployed based on Debian, Balabit is ZorpOS. The required hardware capacity depends on the number of active users and the number of protected servers.
How it works - Wallix Admin Bastion
Wallix can only work in the "bastion" mode at the application level of the OSI model, i.e. put in a network break in an explicit form visible to the administrator. On the Wallix server, rules are configured (about them below), on the basis of which he skips \ blocks administrator connections. The administrator connects to the wallix server using the rdp protocol (standard port) and logs in with the help of the created local account (or imported from AD). After that, he is provided with an available list of pairs of server + final accounting, and he chooses the server he needs. Wallix itself can substitute the password for the final account, but you can also request this password from the administrator. For clarity, the logical connection diagram is shown below:

Logic diagram for connecting admins to protected servers via Wallix
The Wallix settings are binary (true-false \ can-not) mappings between two types of groups: groups of user accounts on Wallix itself (can be replaced with user accounts imported from AD) and a group of Server + final account pairs.

The form of adding / editing the protected server and the final account
The number of such comparisons, as well as the groups themselves, is not limited and on their basis an access matrix is built up to whom and where to connect.
Wallix stores rdp records in the form of video clips (in file form) that can be driven through the built-in text recognizer (ocr), and then searched by titles (search by titles within more than one video was promised to be screwed in the next versions).

List of saved video records rdp-sessions
How can you "force" the admin to go to the right servers through wallix?
- The closure of routes at the network level, coupled with the organizers, “either way or the other way, otherwise severe measures will follow ...”;
- Allow access to protected servers only under specially created domain accounts, the password for which Wallix will change once per hour \ day \ week \ month (passwords are sent in encrypted form to the specified box. You need a GPG certificate and a ZK for it).
Product Benefits
- Simple, uncomplicated setup;
- Stable operating mode "bastion", the possibility of dual authorization and the preparation of an appropriate access matrix based on it;
- Ability to integrate with multiple AD.
Product cons
- There is no consistently working "transparent" mode. The one that is declared works with a tambourine and through a stump-deck or does not work at all;
- There are unrecorded production nuances (version 4.2), which have to be closed with crutches and on the run.
How it works - Balabit Shell Control Box
Balabit is also put in a “gap”, but it can work in several modes on different OSI models. At the same time, the setting of the "transparent" \ "opaque" mode is made directly in the connection itself, which is very convenient from the point of view of the "fine" setting of a particular connection.
"Transparent mode"
The main advantage of Balabit is that it can work in a “transparent” mode, staying on the network in a form hidden to administrators. IP spoofing allows you to make it “invisible” even for FW and routers, substituting the PC administrator's IP address as ip-src, so there is no need to configure separate permissions for it on the network equipment.
For balabit to work in transparent mode, the corresponding routes are written on the router (that all traffic from the subnetwork N is sent to the Balabit IP address). At the same time, traffic that balabit cannot recognize (to detect controlled protocols in it) will be passed on without any further changes (to the specified gateway).
Note: in transparent mode, authorization is not performed on the balabit server, however, the system records, under what account, the administrator logged in to the protected server, which allows you to subsequently set the required filters and find the desired video clip.
The balabit settings have a cut on the protected servers - each server has its own instantaneous settings and access rights (for transparent mode: from which network you can connect to the protected server). The option of settings is presented below:

Settings for access to the protected server via balabit
In transparent mode, the main layer of settings falls on the routing of traffic and setting up network equipment. The settings on balabit itself are minimal and operate with ip-addresses from which they access protected servers, and not users and their rights, as implemented in Wallix.
Bastion Mode
Bastion mode has several implementations:
- TS Gateway mode. In this mode, the DNS name of the balabit server is set up in the rdp client as the gateway server of remote desktops. This mode uses certificates, encrypting traffic both to TS GW (balabit server certificate), and from balabita to the protected server (either a certificate generated on the fly, or downloaded to balabit). With this connection, it is possible to substitute the password of the final account set up in advance on the balabit server, so the administrator may not know the credentials for connecting to the protected server. However, balabit itself does not automatically know how to change passwords and somehow “manage” them. Integrates with a separate SSO system Thycotic Secret Server.
Note: Such a scheme is quite capricious in its performance, because requires a fairly decent amount of fine tuning and understanding what is being configured and why. Sometimes there can be some unpredictable “gags” (for example, when a proxy is written in the browser properties, the rdp-client refused to resolve the DNS name of the server balabit). - Mode "Authorization on GW". In this mode, the administrator
needs to have two monitors, youwill need to start connecting to the protected server, after initializing the connection, log in to the balabit web interface and “allow” your connection. This connection option also requires network traffic routing and corresponding settings on the router (s). - Mode "4 eyes." The principle of operation is the same as in paragraph 2, but here another person should “allow”.
For each mode, there are their own settings, which now would not want to go deep. Suffice it to say that sometimes the eyes of the number of fields run up :))
The system also stores all the sessions in the form of video clips. OCR is produced once. The search for the recognized text in all videos is already present. To view the session, you need client software (Audit Player), which comes with the distribution kit and is installed on the operator's PC with MS-OS onboard.

List of saved video records rdp-sessions
Product Benefits
- Able to work stably and professionally in transparent-MiTM mode;
- It has many subtle settings for almost every taste;
Product cons
- Integrates with only one AD (requires input to AD);
- The "bastion" mode sometimes requires dances with a tambourine and long-term smoking of manulas;
- Cannot manage passwords;
- Dual authorization has a rather confusing character and temper;
Summarizing
As can be seen from the text above, each product has its own strengths and weaknesses - it all depends on the pool of tasks assigned to it. The comparison did not involve all the capabilities of the systems.
I would also like to separately note that, by the type of Wallix, the CyberArk system is present on the market, which has a similar but more advanced functionality in the "bastion" mode. The basis of its work is the mechanism of MS Remote Application, which has increased the number of supported protocols and connectivity. Unfortunately, the author does not have sufficient competence to add it to the comparison, however, he considers it to be silent about it as criminal.
Source: https://habr.com/ru/post/262083/
All Articles