How to steal a control plane or cooking EIGRP for Juniper
As you know, SDN was originally defined as the ability to physically separate control and data plane. I want to show the realization of this idea without openflow and special controllers. The control plane will be the ODROID-C1 debugging board with IOS running inside Dynamips. As the data plane stands Juniper EX-2200.
The EIGRP protocol will work on the board, build the routing table, and the switch will send data based on this table.
First, I will explain why this choice:
')
How it will work in 2 words:
there is a network built on the equipment cisco, the routing protocol EIGRP. Add a Juniper EX-2200 switch, connect it as "as needed" (that is, as a combat router). We switch on the debug board with Dynamips to the Switch, redirect all the routing protocol service traffic to it. Virtual cisco builds the routing table and redistribute it to the switch. As a result, all traffic with data will be sent to the routing table built by the EIGRP protocol.
So, the test circuit:

for simplicity, the networks are attached to the links, and the last octet of the address always coincides with the device number.
configurations for tsisok:
Configure the switch:
For the redirection of service traffic, port mirroring is used in VLAN with an IP filter overlay (EIGRP).
Dynamyps and Dynagen are installed on the debug board,
collected from source codes, it was emulated 7200.
R15 (virtual cisco)
thus, a direct correspondence of the interfaces between K15 and R15 is obtained:
vlan.1001 - fa0 / 1
vlan.1010 - fa0 / 1.1010
vlan.1011 - fa0 / 0.1011
vlan.1014 - fa1 / 1
Now service traffic gets to odroid with a double tag,
and the responses from our control plane should go to K15 with only one, “second” tag.
for this we stand linux bridges:
now we need the packets to be transmitted in accordance with the logic shown by arrows in the figure, and no more.
To do this, we will transfer the bridge to the hub mode (stops learning Macs):
and we filter everything unnecessary:
in this place we are confronted with the fact that K15 and R15 have the same IP addresses, but different MAC addresses,
which leads to interesting problems, we solve this with the help of ebtables too, for a start we will learn the poppy with which K15 works:
now we need all the packages to leave with this poppy:
Everything, our “control plane” built RIB:
now we need to send this routing information to Juniper,
to do this, we use OSPF and the features of its implementation in the default vendor.
We also add a link and interfaces for the exchange of information between R15 and K15:
K15
R15
We add rules to ebtables so that the traffic in the 4000th VLAN is passed without changes.
add to the beginning of the chain.
Check the availability of the necessary routes in the RIB at K15:
routes are in place, all servers are pinging.
launch iperf and pump traffic between S1-S3 and S2-S4:
make sure that normal traffic runs wire speed.
at the same time, during the entire testing time, the EIGRP neighborhood is not broken.
and that’s what they wanted.
limitations:
1. link aggregation is not considered.
2. Considered option only for RVI (Routed VLAN Interface).
3. Traffic balancing does not work, only one route is given to the switch.
4. slow convergence of the routing protocol, since based only on hello packages (the control plane does not see the port status and there is no BFD)
5. about 6-7 times the complicated configuration, since instead of one protocol on one device, we set up a whole set of protocols and rules on actually 3 entities.
The EIGRP protocol will work on the board, build the routing table, and the switch will send data based on this table.
First, I will explain why this choice:
- EIGRP is a well-known protocol fully implemented only on cisco devices.
- Juniper - because second most popular vendor
- The Juniper EX-2200 is the youngest model, so the method will work with all the older ones.
- ODROID-C1 was chosen due to the “fair” 1G network card (you can use any server with linux).
- The EX-2200 is smaller than a unit in width, and the debug board fits completely in the free space, so the whole structure fits in 1U and does not require additional rack space
')
How it will work in 2 words:
there is a network built on the equipment cisco, the routing protocol EIGRP. Add a Juniper EX-2200 switch, connect it as "as needed" (that is, as a combat router). We switch on the debug board with Dynamips to the Switch, redirect all the routing protocol service traffic to it. Virtual cisco builds the routing table and redistribute it to the switch. As a result, all traffic with data will be sent to the routing table built by the EIGRP protocol.
So, the test circuit:

for simplicity, the networks are attached to the links, and the last octet of the address always coincides with the device number.
configurations for tsisok:
R10 - Cisco 2811
R10 # sho running-config
Building configuration ...
Current configuration: 1006 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R10
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
!
resource policy
!
ip subnet-zero
!
!
ip cef
!
!
!
voice-card 0
no dspfarm
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0 / 0
description S2
ip address 10.2.0.10 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0 / 1
description K15-ge0 / 0/8
no ip address
duplex auto
speed auto
!
interface FastEthernet0 / 1.1010
encapsulation dot1Q 1010
ip address 10.10.0.10 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0 / 0/0
!
interface FastEthernet0 / 0/1
!
interface FastEthernet0 / 0/2
!
interface FastEthernet0 / 0/3
!
interface vlan1
no ip address
!
router eigrp 1
network 0.0.0.0
auto-summary
!
ip classless
!
!
ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
line aux 0
line vty 0 4
login
!
scheduler allocate 20000 1000
!
end
R10 #
Building configuration ...
Current configuration: 1006 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R10
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
!
resource policy
!
ip subnet-zero
!
!
ip cef
!
!
!
voice-card 0
no dspfarm
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0 / 0
description S2
ip address 10.2.0.10 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0 / 1
description K15-ge0 / 0/8
no ip address
duplex auto
speed auto
!
interface FastEthernet0 / 1.1010
encapsulation dot1Q 1010
ip address 10.10.0.10 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0 / 0/0
!
interface FastEthernet0 / 0/1
!
interface FastEthernet0 / 0/2
!
interface FastEthernet0 / 0/3
!
interface vlan1
no ip address
!
router eigrp 1
network 0.0.0.0
auto-summary
!
ip classless
!
!
ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
line aux 0
line vty 0 4
login
!
scheduler allocate 20000 1000
!
end
R10 #
R11 - Cisco 2851
R11 # sho running-config
Building configuration ...
Current configuration: 897 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R11
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
!
resource policy
!
ip subnet-zero
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0 / 0
description R12-gi0 / 2
ip address 10.12.1.11 255.255.255.0
duplex auto
speed auto
no mop enabled
!
interface GigabitEthernet0 / 1
description K15-ge0 / 0/9
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0 / 1.1011
description K15
encapsulation dot1Q 1011
ip address 10.11.0.11 255.255.255.0
no snmp trap link-status
!
router eigrp 1
network 0.0.0.0
no auto-summary
!
ip classless
!
no ip http server
no ip http secure-server
!
snmp-server community public RO
!
!
control-plane
!
!
!
line con 0
line aux 0
line vty 0 4
password cisco
login
!
scheduler allocate 20000 1000
!
end
R11 #
Building configuration ...
Current configuration: 897 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R11
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
!
resource policy
!
ip subnet-zero
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0 / 0
description R12-gi0 / 2
ip address 10.12.1.11 255.255.255.0
duplex auto
speed auto
no mop enabled
!
interface GigabitEthernet0 / 1
description K15-ge0 / 0/9
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0 / 1.1011
description K15
encapsulation dot1Q 1011
ip address 10.11.0.11 255.255.255.0
no snmp trap link-status
!
router eigrp 1
network 0.0.0.0
no auto-summary
!
ip classless
!
no ip http server
no ip http secure-server
!
snmp-server community public RO
!
!
control-plane
!
!
!
line con 0
line aux 0
line vty 0 4
password cisco
login
!
scheduler allocate 20000 1000
!
end
R11 #
R12 - WS-C3560-48TS
R12 # sho running-config
Building configuration ...
Current configuration: 2289 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
service unsupported-transceiver
!
hostname R12
!
!
no aaa new-model
system mtu routing 1500
vtp mode transparent
ip subnet-zero
ip routing
!
!
!
!
!
!
!
no errdisable detect cause gbic-invalid
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface FastEthernet0 / 1
!
interface FastEthernet0 / 2
!
interface FastEthernet0 / 3
!
interface FastEthernet0 / 4
!
interface FastEthernet0 / 5
!
interface FastEthernet0 / 6
!
interface FastEthernet0 / 7
!
interface FastEthernet0 / 8
!
interface FastEthernet0 / 9
!
interface FastEthernet0 / 10
!
interface FastEthernet0 / 11
!
interface FastEthernet0 / 12
!
interface FastEthernet0 / 13
!
interface FastEthernet0 / 14
!
interface FastEthernet0 / 15
!
interface FastEthernet0 / 16
!
interface FastEthernet0 / 17
!
interface FastEthernet0 / 18
!
interface FastEthernet0 / 19
!
interface FastEthernet0 / 20
!
interface FastEthernet0 / 21
!
interface FastEthernet0 / 22
!
interface FastEthernet0 / 23
!
interface FastEthernet0 / 24
!
interface FastEthernet0 / 25
!
interface FastEthernet0 / 26
!
interface FastEthernet0 / 27
!
interface FastEthernet0 / 28
!
interface FastEthernet0 / 29
!
interface FastEthernet0 / 30
!
interface FastEthernet0 / 31
!
interface FastEthernet0 / 32
!
interface FastEthernet0 / 33
!
interface FastEthernet0 / 34
!
interface FastEthernet0 / 35
!
interface FastEthernet0 / 36
!
interface FastEthernet0 / 37
!
interface FastEthernet0 / 38
!
interface FastEthernet0 / 39
!
interface FastEthernet0 / 40
!
interface FastEthernet0 / 41
!
interface FastEthernet0 / 42
!
interface FastEthernet0 / 43
!
interface FastEthernet0 / 44
!
interface FastEthernet0 / 45
!
interface FastEthernet0 / 46
!
interface FastEthernet0 / 47
!
interface FastEthernet0 / 48
!
interface GigabitEthernet0 / 1
no switchport
ip address 10.12.2.12 255.255.255.0
!
interface GigabitEthernet0 / 2
no switchport
ip address 10.12.1.12 255.255.255.0
!
interface GigabitEthernet0 / 3
no switchport
ip address 10.3.0.12 255.255.255.0
!
interface GigabitEthernet0 / 4
!
interface vlan1
no ip address
!
router eigrp 1
network 0.0.0.0
!
ip classless
ip http server
ip http secure-server
!
!
!
control-plane
!
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
end
R12 #
Building configuration ...
Current configuration: 2289 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
service unsupported-transceiver
!
hostname R12
!
!
no aaa new-model
system mtu routing 1500
vtp mode transparent
ip subnet-zero
ip routing
!
!
!
!
!
!
!
no errdisable detect cause gbic-invalid
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface FastEthernet0 / 1
!
interface FastEthernet0 / 2
!
interface FastEthernet0 / 3
!
interface FastEthernet0 / 4
!
interface FastEthernet0 / 5
!
interface FastEthernet0 / 6
!
interface FastEthernet0 / 7
!
interface FastEthernet0 / 8
!
interface FastEthernet0 / 9
!
interface FastEthernet0 / 10
!
interface FastEthernet0 / 11
!
interface FastEthernet0 / 12
!
interface FastEthernet0 / 13
!
interface FastEthernet0 / 14
!
interface FastEthernet0 / 15
!
interface FastEthernet0 / 16
!
interface FastEthernet0 / 17
!
interface FastEthernet0 / 18
!
interface FastEthernet0 / 19
!
interface FastEthernet0 / 20
!
interface FastEthernet0 / 21
!
interface FastEthernet0 / 22
!
interface FastEthernet0 / 23
!
interface FastEthernet0 / 24
!
interface FastEthernet0 / 25
!
interface FastEthernet0 / 26
!
interface FastEthernet0 / 27
!
interface FastEthernet0 / 28
!
interface FastEthernet0 / 29
!
interface FastEthernet0 / 30
!
interface FastEthernet0 / 31
!
interface FastEthernet0 / 32
!
interface FastEthernet0 / 33
!
interface FastEthernet0 / 34
!
interface FastEthernet0 / 35
!
interface FastEthernet0 / 36
!
interface FastEthernet0 / 37
!
interface FastEthernet0 / 38
!
interface FastEthernet0 / 39
!
interface FastEthernet0 / 40
!
interface FastEthernet0 / 41
!
interface FastEthernet0 / 42
!
interface FastEthernet0 / 43
!
interface FastEthernet0 / 44
!
interface FastEthernet0 / 45
!
interface FastEthernet0 / 46
!
interface FastEthernet0 / 47
!
interface FastEthernet0 / 48
!
interface GigabitEthernet0 / 1
no switchport
ip address 10.12.2.12 255.255.255.0
!
interface GigabitEthernet0 / 2
no switchport
ip address 10.12.1.12 255.255.255.0
!
interface GigabitEthernet0 / 3
no switchport
ip address 10.3.0.12 255.255.255.0
!
interface GigabitEthernet0 / 4
!
interface vlan1
no ip address
!
router eigrp 1
network 0.0.0.0
!
ip classless
ip http server
ip http secure-server
!
!
!
control-plane
!
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
end
R12 #
R14 - WS-C3560-24TS
R14 # sho running-config
Building configuration ...
Current configuration: 1805 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
service unsupported-transceiver
!
hostname R14
!
!
no aaa new-model
system mtu routing 1500
vtp mode transparent
ip subnet-zero
ip routing
!
!
!
!
!
!
no errdisable detect cause sfp-config-mismatch
no errdisable detect cause gbic-invalid
no file verify auto
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
vlan 100,200,300
!
!
interface FastEthernet0 / 1
!
interface FastEthernet0 / 2
!
interface FastEthernet0 / 3
!
interface FastEthernet0 / 4
!
interface FastEthernet0 / 5
!
interface FastEthernet0 / 6
!
interface FastEthernet0 / 7
!
interface FastEthernet0 / 8
!
interface FastEthernet0 / 9
!
interface FastEthernet0 / 10
!
interface FastEthernet0 / 11
!
interface FastEthernet0 / 12
!
interface FastEthernet0 / 13
!
interface FastEthernet0 / 14
!
interface FastEthernet0 / 15
!
interface FastEthernet0 / 16
!
interface FastEthernet0 / 17
!
interface FastEthernet0 / 18
!
interface FastEthernet0 / 19
!
interface FastEthernet0 / 20
!
interface FastEthernet0 / 21
!
interface FastEthernet0 / 22
!
interface FastEthernet0 / 23
!
interface FastEthernet0 / 24
no switchport
ip address 10.4.0.14 255.255.255.0
!
interface GigabitEthernet0 / 1
description K15-ge0 / 1/0
no switchport
ip address 10.14.0.14 255.255.255.0
!
interface GigabitEthernet0 / 2
description r12-gi0 / 1
no switchport
ip address 10.12.2.14 255.255.255.0
!
interface vlan1
no ip address
shutdown
!
router eigrp 1
network 0.0.0.0
no auto-summary
!
ip classless
ip http server
ip http secure-server
!
!
ip access-list standard public
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
line vty 0 4
password cisco
login
line vty 5 15
password cisco
login
!
end
R14 #
Building configuration ...
Current configuration: 1805 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
service unsupported-transceiver
!
hostname R14
!
!
no aaa new-model
system mtu routing 1500
vtp mode transparent
ip subnet-zero
ip routing
!
!
!
!
!
!
no errdisable detect cause sfp-config-mismatch
no errdisable detect cause gbic-invalid
no file verify auto
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
vlan 100,200,300
!
!
interface FastEthernet0 / 1
!
interface FastEthernet0 / 2
!
interface FastEthernet0 / 3
!
interface FastEthernet0 / 4
!
interface FastEthernet0 / 5
!
interface FastEthernet0 / 6
!
interface FastEthernet0 / 7
!
interface FastEthernet0 / 8
!
interface FastEthernet0 / 9
!
interface FastEthernet0 / 10
!
interface FastEthernet0 / 11
!
interface FastEthernet0 / 12
!
interface FastEthernet0 / 13
!
interface FastEthernet0 / 14
!
interface FastEthernet0 / 15
!
interface FastEthernet0 / 16
!
interface FastEthernet0 / 17
!
interface FastEthernet0 / 18
!
interface FastEthernet0 / 19
!
interface FastEthernet0 / 20
!
interface FastEthernet0 / 21
!
interface FastEthernet0 / 22
!
interface FastEthernet0 / 23
!
interface FastEthernet0 / 24
no switchport
ip address 10.4.0.14 255.255.255.0
!
interface GigabitEthernet0 / 1
description K15-ge0 / 1/0
no switchport
ip address 10.14.0.14 255.255.255.0
!
interface GigabitEthernet0 / 2
description r12-gi0 / 1
no switchport
ip address 10.12.2.14 255.255.255.0
!
interface vlan1
no ip address
shutdown
!
router eigrp 1
network 0.0.0.0
no auto-summary
!
ip classless
ip http server
ip http secure-server
!
!
ip access-list standard public
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
line vty 0 4
password cisco
login
line vty 5 15
password cisco
login
!
end
R14 #
Configure the switch:
K15 - Juniper EX-2200
root @ K15 # show
version 13.2X50-D15.3;
interfaces {
interface-range tagget-ports {
member "ge-0/0 / [4-11]";
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members [v-R11 v-R10];
}
filter {
input cisco;
}
}
}
}
ge-0/0/0 {
description odroid-mgmt;
unit 0 {
family ethernet-switching {
port-mode access;
vlan {
members v-odroid-mgmt;
}
}
}
}
ge-0/0/1 {
description odroid-c1;
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members [v-R14 v-R11 v-R10 v-S1 v-analyzer];
}
native-vlan-id v-odroid-mgmt;
}
}
}
ge-0/0/2 {
description S1;
unit 0 {
family ethernet-switching {
port-mode access;
vlan {
members v-S1;
}
filter {
input cisco;
}
}
}
}
ge-0/0/8 {
description R10;
}
ge-0/0/9 {
description R11;
}
ge-0/1/0 {
description R14;
unit 0 {
family ethernet-switching {
port-mode access;
vlan {
members v-R14;
}
filter {
input cisco;
}
}
}
}
ge-0/1/1 {
unit 0 {
family ethernet switching;
}
}
vlan {
unit 1001 {
family inet {
address 10.1.0.15/24;
}
}
unit 1010 {
family inet {
address 10.10.0.15/24;
}
}
unit 1011 {
family inet {
address 10.11.0.15/24;
}
}
unit 1014 {
family inet {
address 10.14.0.15/24;
}
}
}
}
firewall {
family ethernet-switching {
filter cisco {
term eigrp {
from {
protocol 88;
}
then {
accept;
analyzer cisco;
}
}
term others {
then accept;
}
}
}
}
ethernet-switching-options {
analyzer cisco {
output {
vlan {
v-analyzer;
}
}
}
dot1q-tunneling {
ether-type 0x8100;
}
}
vlans {
v-R10 {
vlan-id 1010;
l3-interface vlan.1010;
}
v-R11 {
vlan-id 1011;
l3-interface vlan.1011;
}
v-R14 {
vlan-id 1014;
l3-interface vlan.1014;
}
v-S1 {
vlan-id 1001;
l3-interface vlan.1001;
}
v-analyzer {
vlan-id 101;
dot1q-tunneling;
}
v-odroid-mgmt;
}
version 13.2X50-D15.3;
interfaces {
interface-range tagget-ports {
member "ge-0/0 / [4-11]";
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members [v-R11 v-R10];
}
filter {
input cisco;
}
}
}
}
ge-0/0/0 {
description odroid-mgmt;
unit 0 {
family ethernet-switching {
port-mode access;
vlan {
members v-odroid-mgmt;
}
}
}
}
ge-0/0/1 {
description odroid-c1;
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members [v-R14 v-R11 v-R10 v-S1 v-analyzer];
}
native-vlan-id v-odroid-mgmt;
}
}
}
ge-0/0/2 {
description S1;
unit 0 {
family ethernet-switching {
port-mode access;
vlan {
members v-S1;
}
filter {
input cisco;
}
}
}
}
ge-0/0/8 {
description R10;
}
ge-0/0/9 {
description R11;
}
ge-0/1/0 {
description R14;
unit 0 {
family ethernet-switching {
port-mode access;
vlan {
members v-R14;
}
filter {
input cisco;
}
}
}
}
ge-0/1/1 {
unit 0 {
family ethernet switching;
}
}
vlan {
unit 1001 {
family inet {
address 10.1.0.15/24;
}
}
unit 1010 {
family inet {
address 10.10.0.15/24;
}
}
unit 1011 {
family inet {
address 10.11.0.15/24;
}
}
unit 1014 {
family inet {
address 10.14.0.15/24;
}
}
}
}
firewall {
family ethernet-switching {
filter cisco {
term eigrp {
from {
protocol 88;
}
then {
accept;
analyzer cisco;
}
}
term others {
then accept;
}
}
}
}
ethernet-switching-options {
analyzer cisco {
output {
vlan {
v-analyzer;
}
}
}
dot1q-tunneling {
ether-type 0x8100;
}
}
vlans {
v-R10 {
vlan-id 1010;
l3-interface vlan.1010;
}
v-R11 {
vlan-id 1011;
l3-interface vlan.1011;
}
v-R14 {
vlan-id 1014;
l3-interface vlan.1014;
}
v-S1 {
vlan-id 1001;
l3-interface vlan.1001;
}
v-analyzer {
vlan-id 101;
dot1q-tunneling;
}
v-odroid-mgmt;
}
K15 - Juniper EX-2200 - as a set of commands
set interfaces interface-range tagget-ports member "ge-0/0 / [4-11]"
set interfaces interface-range tagset-ports unit 0 family ethernet switching port-mode trunk
set interfaces interface-range tagget-ports unit 0 family ethernet-switching vlan members v-R11
set interfaces interface-range tagget-ports unit 0 family ethernet-switching vlan members v-R10
set interfaces interface-range tagset-ports unit 0 family ethernet-switching filter input cisco
set interfaces ge-0/0/0 description odroid-mgmt
set interfaces ge-0/0/0 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members v-odroid-mgmt
set interfaces ge-0/0/1 description odroid-c1
set interfaces ge-0/0/1 unit 0 family ethernet-switching port-mode trunk
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-R14
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-R11
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-R10
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-S1
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-analyzer
set interfaces ge-0/0/1 unit 0 family ethernet-switching native-vlan-id v-odroid-mgmt
set interfaces ge-0/0/2 description S1
set interfaces ge-0/0/2 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members v-S1
set interfaces ge-0/0/2 unit 0 family ethernet-switching filter input cisco
set interfaces ge-0/0/8 description R10
set interfaces ge-0/0/9 description R11
set interfaces ge-0/1/0 description R14
set interfaces ge-0/1/0 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/1/0 unit 0 family ethernet-switching vlan members v-R14
set interfaces ge-0/1/0 unit 0 family ethernet-switching filter input cisco
set interfaces ge-0/1/1 unit 0 family ethernet-switching
set interfaces vlan unit 1001 family inet address 10.1.0.15/24
set interfaces vlan unit 1010 family inet address 10.10.0.15/24
set interfaces vlan unit 1011 family inet address 10.11.0.15/24
set interfaces vlan unit 1014 family inet address 10.14.0.15/24
set firewall family ethernet-switching filter cisco term eigrp from protocol 88
set firewall family ethernet-switching filter cisco term eigrp then accept
set firewall family ethernet-switching filter cisco term eigrp then analyzer cisco
ethernet-switching filter cisco term firewall family then accept
set ethernet-switching-options analyzer cisco output vlan v-analyzer
set ethernet-switching-options dot1q-tunneling ether-type 0x8100
set vlans v-R10 vlan-id 1010
set vlans v-r10 l3-interface vlan.1010
set vlans v-r11 vlan-id 1011
set vlans v-r11 l3-interface vlan.1011
set vlans v-R14 vlan-id 1014
set vlans v-r14 l3-interface vlan.1014
set vlans v-S1 vlan-id 1001
set vlans v-s1 l3-interface vlan.1001
set vlans v-analyzer vlan-id 101
set vlans v-analyzer dot1q-tunneling
set vlans v-odroid-mgmt
set interfaces interface-range tagset-ports unit 0 family ethernet switching port-mode trunk
set interfaces interface-range tagget-ports unit 0 family ethernet-switching vlan members v-R11
set interfaces interface-range tagget-ports unit 0 family ethernet-switching vlan members v-R10
set interfaces interface-range tagset-ports unit 0 family ethernet-switching filter input cisco
set interfaces ge-0/0/0 description odroid-mgmt
set interfaces ge-0/0/0 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members v-odroid-mgmt
set interfaces ge-0/0/1 description odroid-c1
set interfaces ge-0/0/1 unit 0 family ethernet-switching port-mode trunk
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-R14
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-R11
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-R10
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-S1
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-analyzer
set interfaces ge-0/0/1 unit 0 family ethernet-switching native-vlan-id v-odroid-mgmt
set interfaces ge-0/0/2 description S1
set interfaces ge-0/0/2 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members v-S1
set interfaces ge-0/0/2 unit 0 family ethernet-switching filter input cisco
set interfaces ge-0/0/8 description R10
set interfaces ge-0/0/9 description R11
set interfaces ge-0/1/0 description R14
set interfaces ge-0/1/0 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/1/0 unit 0 family ethernet-switching vlan members v-R14
set interfaces ge-0/1/0 unit 0 family ethernet-switching filter input cisco
set interfaces ge-0/1/1 unit 0 family ethernet-switching
set interfaces vlan unit 1001 family inet address 10.1.0.15/24
set interfaces vlan unit 1010 family inet address 10.10.0.15/24
set interfaces vlan unit 1011 family inet address 10.11.0.15/24
set interfaces vlan unit 1014 family inet address 10.14.0.15/24
set firewall family ethernet-switching filter cisco term eigrp from protocol 88
set firewall family ethernet-switching filter cisco term eigrp then accept
set firewall family ethernet-switching filter cisco term eigrp then analyzer cisco
ethernet-switching filter cisco term firewall family then accept
set ethernet-switching-options analyzer cisco output vlan v-analyzer
set ethernet-switching-options dot1q-tunneling ether-type 0x8100
set vlans v-R10 vlan-id 1010
set vlans v-r10 l3-interface vlan.1010
set vlans v-r11 vlan-id 1011
set vlans v-r11 l3-interface vlan.1011
set vlans v-R14 vlan-id 1014
set vlans v-r14 l3-interface vlan.1014
set vlans v-S1 vlan-id 1001
set vlans v-s1 l3-interface vlan.1001
set vlans v-analyzer vlan-id 101
set vlans v-analyzer dot1q-tunneling
set vlans v-odroid-mgmt
For the redirection of service traffic, port mirroring is used in VLAN with an IP filter overlay (EIGRP).
Dynamyps and Dynagen are installed on the debug board,
collected from source codes, it was emulated 7200.
Dynagen
[localhost]
[[7200]]
image = /opt/dgen/c7200-adventerprisek9-mz.124-4.T4.image
npe = npe-400
npe2 = npe-400
ram = 160
[[ROUTER R1]]
f0 / 0 = NIO_tap: tap0
f0 / 1 = NIO_tap: tap1
f1 / 1 = NIO_tap: tap2
[[7200]]
image = /opt/dgen/c7200-adventerprisek9-mz.124-4.T4.image
npe = npe-400
npe2 = npe-400
ram = 160
[[ROUTER R1]]
f0 / 0 = NIO_tap: tap0
f0 / 1 = NIO_tap: tap1
f1 / 1 = NIO_tap: tap2
R15 (virtual cisco)
cisco7200 - R15
R15 # sho running-config
Building configuration ...
Current configuration: 1203 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R15
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
!
resource policy
!
ip subnet-zero
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0 / 0
no ip address
duplex auto
speed auto
no mop enabled
!
interface FastEthernet0 / 0.1010
description R10
encapsulation dot1Q 1010
ip address 10.10.0.15 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0 / 0.1011
description R11
encapsulation dot1Q 1011
ip address 10.11.0.15 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0 / 1
description S1
ip address 10.1.0.15 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1 / 0
no ip address
duplex auto
speed auto
!
interface FastEthernet1 / 1
description R14
ip address 10.14.0.15 255.255.255.0
duplex auto
speed auto
!
router eigrp 1
network 0.0.0.0
auto-summary
!
ip classless
no ip http server
no ip http secure-server
!
!
!
logging alarm informational
!
!
!
!
control-plane
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
stopbits 1
line aux 0
stopbits 1
line vty 0 4
login
!
!
end
R15 # en
Building configuration ...
Current configuration: 1203 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R15
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
!
resource policy
!
ip subnet-zero
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0 / 0
no ip address
duplex auto
speed auto
no mop enabled
!
interface FastEthernet0 / 0.1010
description R10
encapsulation dot1Q 1010
ip address 10.10.0.15 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0 / 0.1011
description R11
encapsulation dot1Q 1011
ip address 10.11.0.15 255.255.255.0
no snmp trap link-status
!
interface FastEthernet0 / 1
description S1
ip address 10.1.0.15 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1 / 0
no ip address
duplex auto
speed auto
!
interface FastEthernet1 / 1
description R14
ip address 10.14.0.15 255.255.255.0
duplex auto
speed auto
!
router eigrp 1
network 0.0.0.0
auto-summary
!
ip classless
no ip http server
no ip http secure-server
!
!
!
logging alarm informational
!
!
!
!
control-plane
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
stopbits 1
line aux 0
stopbits 1
line vty 0 4
login
!
!
end
R15 # en
thus, a direct correspondence of the interfaces between K15 and R15 is obtained:
vlan.1001 - fa0 / 1
vlan.1010 - fa0 / 1.1010
vlan.1011 - fa0 / 0.1011
vlan.1014 - fa1 / 1
Now service traffic gets to odroid with a double tag,
and the responses from our control plane should go to K15 with only one, “second” tag.
for this we stand linux bridges:
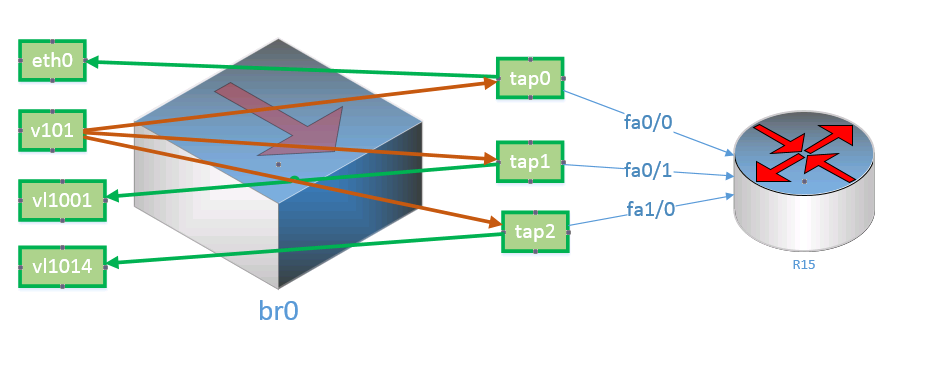
ip link add link eth0 v101 type vlan id 101 ip link add link eth0 vl1001 type vlan id 1001 ip link add link eth0 vl1014 type vlan id 1014 brctl addbr br0 brctl addif br0 v101 brctl addif br0 eth0 brctl addif br0 tap0 brctl addif br0 tap1 brctl addif br0 tap2 brctl addif br0 vl1001 brctl addif br0 vl1014 now we need the packets to be transmitted in accordance with the logic shown by arrows in the figure, and no more.

To do this, we will transfer the bridge to the hub mode (stops learning Macs):
brctl setageing br0 0 and we filter everything unnecessary:
ebtables -A FORWARD -i tap0 -o eth0 -j ACCEPT ebtables -A FORWARD -i tap1 -o vl1001 -j ACCEPT ebtables -A FORWARD -i tap2 -o vl1014 -j ACCEPT ebtables -A FORWARD -i v101 -o tap1 -p ipv4 --ip-source 10.1.0.0/24 -j ACCEPT ebtables -A FORWARD -i v101 -o tap2 -p ipv4 --ip-source 10.14.0.0/24 -j ACCEPT ebtables -A FORWARD -i v101 -o tap0 -p 802_1q -j ACCEPT ebtables -P FORWARD DROP in this place we are confronted with the fact that K15 and R15 have the same IP addresses, but different MAC addresses,
which leads to interesting problems, we solve this with the help of ebtables too, for a start we will learn the poppy with which K15 works:
root@K15> show ethernet-switching table | match router v-R10 78:fe:3d:11:22:33 Static - Router v-R11 78:fe:3d:11:22:33 Static - Router v-R14 78:fe:3d:11:22:33 Static - Router v-S1 78:fe:3d:11:22:33 Static - Router now we need all the packages to leave with this poppy:
ebtables -t nat -A POSTROUTING -o eth0 -j snat --to-src 78:fe:3d:11:22:33 --snat-arp --snat-target ACCEPT ebtables -t nat -A POSTROUTING -o vl1001 -j snat --to-src 78:fe:3d:11:22:33 --snat-arp --snat-target ACCEPT ebtables -t nat -A POSTROUTING -o vl1014 -j snat --to-src 78:fe:3d:11:22:33 --snat-arp --snat-target ACCEPT Everything, our “control plane” built RIB:
R15#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is not set 10.0.0.0/24 is subnetted, 9 subnets C 10.10.0.0 is directly connected, FastEthernet0/0.1010 C 10.11.0.0 is directly connected, FastEthernet0/0.1011 C 10.14.0.0 is directly connected, FastEthernet1/1 D 10.12.2.0 [90/28416] via 10.14.0.14, 00:53:32, FastEthernet1/1 D 10.12.1.0 [90/28416] via 10.11.0.11, 00:53:32, FastEthernet0/0.1011 D 10.2.0.0 [90/30720] via 10.10.0.10, 00:28:41, FastEthernet0/0.1010 D 10.3.0.0 [90/28672] via 10.14.0.14, 00:08:31, FastEthernet1/1 [90/28672] via 10.11.0.11, 00:08:31, FastEthernet0/0.1011 C 10.1.0.0 is directly connected, FastEthernet0/1 D 10.4.0.0 [90/30720] via 10.14.0.14, 00:03:09, FastEthernet1/1 R15# now we need to send this routing information to Juniper,
to do this, we use OSPF and the features of its implementation in the default vendor.
We also add a link and interfaces for the exchange of information between R15 and K15:
K15
set vlans v-cplane vlan-id 4000 l3-interface vlan.4000 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v-cplane set interfaces vlan.4000 family inet address 100.65.127.129/30 set protocols ospf area 0.0.0.0 interface vlan.4000 hello-interval 1 dead-interval 4 set protocols ospf area 0.0.0.0 interface vlan.1001 passive set protocols ospf area 0.0.0.0 interface vlan.1010 passive set protocols ospf area 0.0.0.0 interface vlan.1011 passive set protocols ospf area 0.0.0.0 interface vlan.1014 passive R15
R15>en R15#conf t R15(config)#interface fa0/0.4000 R15(config-subif)#encapsulation dot1Q 4000 R15(config-subif)#ip address 100.65.127.130 255.255.255.252 R15(config-subif)#ip ospf hello-interval 1 R15(config-subif)#ip ospf dead-interval 4 R15(config-subif)#exit R15(config)#router eigrp 1 R15(config-router)#no auto-summary R15(config-router)#exit R15(config)#router ospf 1 R15(config-router)#network 0.0.0.0 0.0.0.0 area 0 R15(config-router)#redistribute eigrp 1 subnets R15(config-router)#end R15# We add rules to ebtables so that the traffic in the 4000th VLAN is passed without changes.
add to the beginning of the chain.
ebtables -t nat -A POSTROUTING -p 802_1Q --vlan-id 4000 -j ACCEPT ebtables -A FORWARD -i eth0 -o tap0 -p 802_1q --vlan-id 4000 -j ACCEPT Check the availability of the necessary routes in the RIB at K15:
root@K15> show route inet.0: 16 destinations, 16 routes (16 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 10.1.0.0/24 *[Direct/0] 02:59:01 > via vlan.1001 10.1.0.15/32 *[Local/0] 1d 03:21:44 Local via vlan.1001 10.2.0.0/24 *[OSPF/150] 00:13:16, metric 20, tag 0 > to 10.10.0.10 via vlan.1010 10.3.0.0/24 *[OSPF/150] 00:13:16, metric 20, tag 0 > to 10.14.0.14 via vlan.1014 10.4.0.0/24 *[OSPF/150] 00:13:16, metric 20, tag 0 > to 10.14.0.14 via vlan.1014 10.10.0.0/24 *[Direct/0] 1d 03:21:26 > via vlan.1010 10.10.0.15/32 *[Local/0] 1d 03:21:44 Local via vlan.1010 10.11.0.0/24 *[Direct/0] 1d 03:21:26 > via vlan.1011 10.11.0.15/32 *[Local/0] 1d 03:21:44 Local via vlan.1011 10.12.1.0/24 *[OSPF/150] 00:13:16, metric 20, tag 0 > to 10.11.0.11 via vlan.1011 10.12.2.0/24 *[OSPF/150] 00:13:16, metric 20, tag 0 > to 10.14.0.14 via vlan.1014 10.14.0.0/24 *[Direct/0] 1d 03:21:27 > via vlan.1014 10.14.0.15/32 *[Local/0] 1d 03:21:44 Local via vlan.1014 100.65.127.128/30 *[Direct/0] 01:01:08 > via vlan.4000 100.65.127.129/32 *[Local/0] 01:01:08 Local via vlan.4000 224.0.0.5/32 *[OSPF/10] 01:01:09, metric 1 MultiRecv routes are in place, all servers are pinging.
launch iperf and pump traffic between S1-S3 and S2-S4:
root@S3:~# iperf -c 10.1.0.1 -t 10 -d ------------------------------------------------------------ Server listening on TCP port 5001 TCP window size: 85.3 KByte (default) ------------------------------------------------------------ ------------------------------------------------------------ Client connecting to 10.1.0.1, TCP port 5001 TCP window size: 413 KByte (default) ------------------------------------------------------------ [ 5] local 10.3.0.3 port 33375 connected with 10.1.0.1 port 5001 [ 4] local 10.3.0.3 port 5001 connected with 10.1.0.1 port 51122 [ ID] Interval Transfer Bandwidth [ 5] 0.0-10.0 sec 1.09 GBytes 939 Mbits/sec [ 4] 0.0-10.0 sec 1.08 GBytes 928 Mbits/sec root@S4:~# iperf -c 10.2.0.2 -t 10 -d ------------------------------------------------------------ Server listening on TCP port 5001 TCP window size: 85.3 KByte (default) ------------------------------------------------------------ ------------------------------------------------------------ Client connecting to 10.2.0.2, TCP port 5001 TCP window size: 82.5 KByte (default) ------------------------------------------------------------ [ 5] local 10.4.0.4 port 59485 connected with 10.2.0.2 port 5001 [ 4] local 10.4.0.4 port 5001 connected with 10.2.0.2 port 41829 [ ID] Interval Transfer Bandwidth [ 5] 0.0-10.0 sec 111 MBytes 92.5 Mbits/sec [ 4] 0.0-10.3 sec 102 MBytes 83.2 Mbits/sec make sure that normal traffic runs wire speed.
at the same time, during the entire testing time, the EIGRP neighborhood is not broken.
and that’s what they wanted.
limitations:
1. link aggregation is not considered.
2. Considered option only for RVI (Routed VLAN Interface).
3. Traffic balancing does not work, only one route is given to the switch.
4. slow convergence of the routing protocol, since based only on hello packages (the control plane does not see the port status and there is no BFD)
5. about 6-7 times the complicated configuration, since instead of one protocol on one device, we set up a whole set of protocols and rules on actually 3 entities.
Source: https://habr.com/ru/post/262047/
All Articles