A dangerous 0day vulnerability has been discovered in Adobe Flash Player.
Yesterday we wrote about the leakage of confidential data of the Hacking Team cyber group, which was subjected to large-scale hacking. The archive contained the source codes of several 0day exploits, including the LPE sandbox-escape exploit for the Internet Explorer web browser and the dangerous RCE + LPE exploit for the current version of Flash Player. The working version of the latter is already walking around the network and is very dangerous for users, because the exploit is universal and allows you to remotely execute code in several browsers (current versions), including Google Chrome, Opera, MS Internet Explorer, and even MS Edge as part of Windows 10.

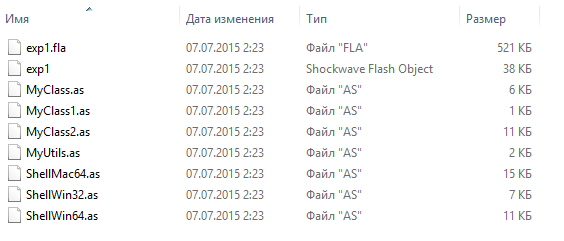
Fig. Sources of exploit.
')
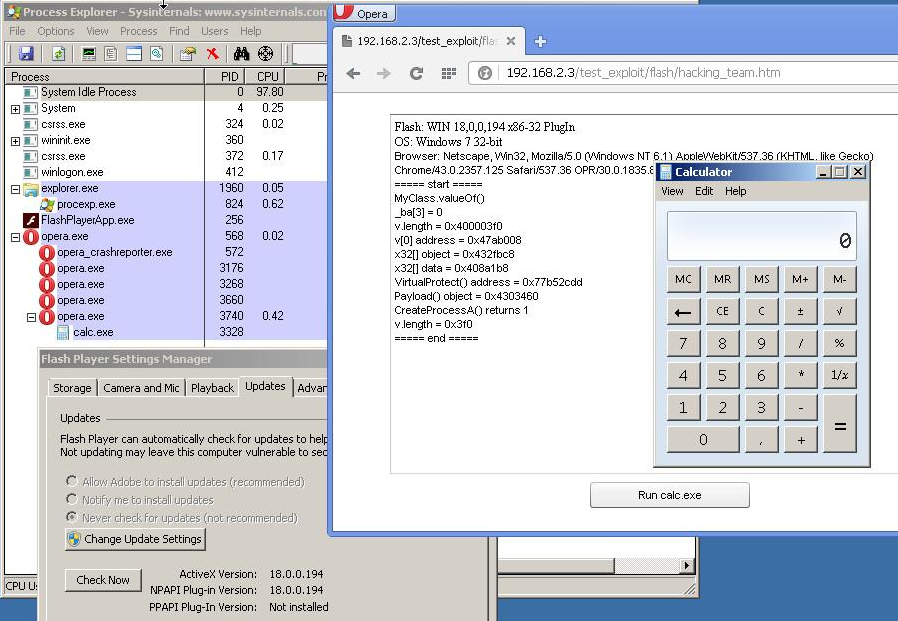
Fig. Demonstrate the success of the exploit for the Opera web browser on a 32-bit version of Windows 7.
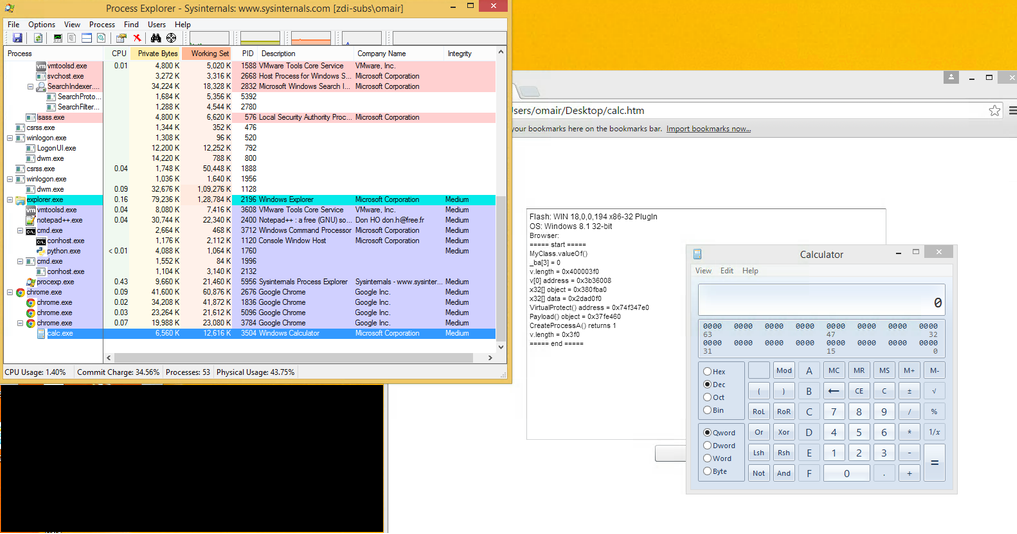
Fig. Same for google chrome. The source is here .
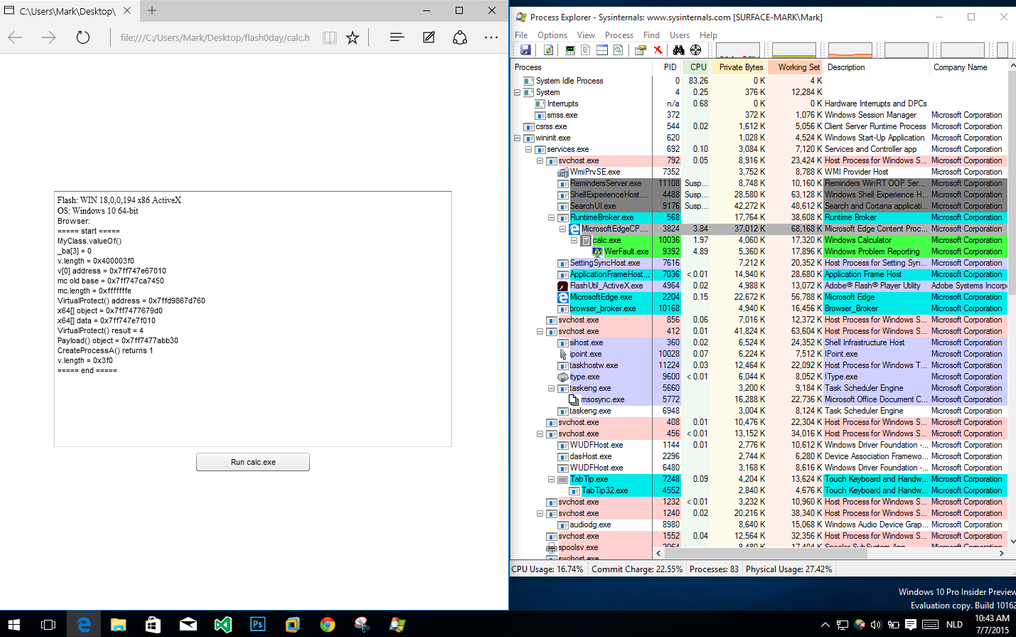
Fig. The exploit also works great on the latest MS Edge web browser on Windows 10 (build 10162).
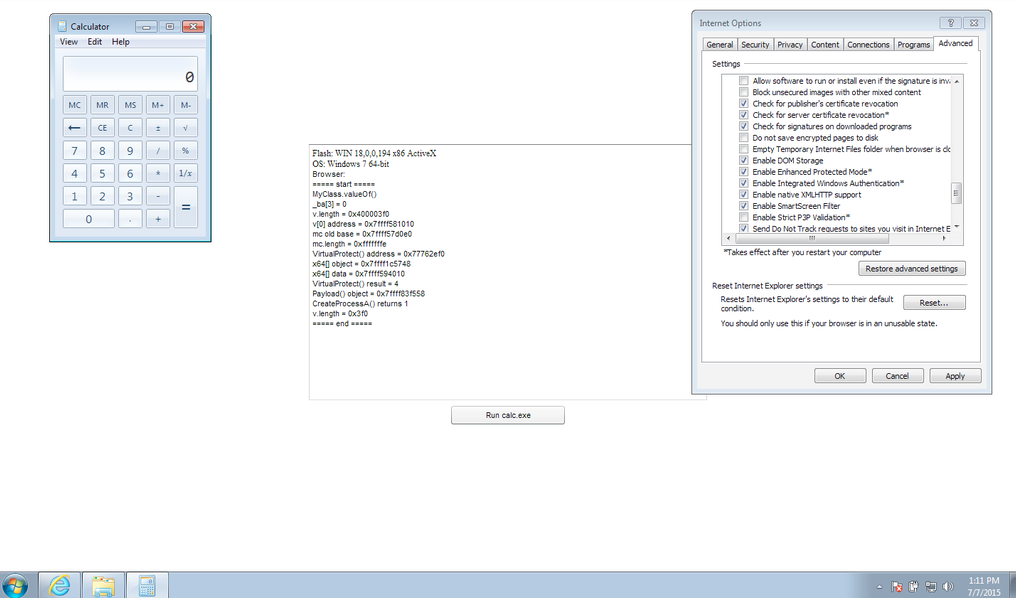
Fig. The exploit works fine for IE11 on a 64-bit up-to-date version of Windows 7 with EPM enabled .
In this case, the most dangerous development of the situation will be that this exploit can get into one or several sets of exploits and will be used by attackers to organize drive-by attacks with automatic installation of malicious programs.
We recommend that users disable Flash Player for the browser you are using until Adobe has released the corresponding patch. Instructions for this process can be found here .
UPD: Symantec has also confirmed the relevance of this 0day exploit.
Leaked Flash Zero
www.symantec.com/connect/blogs/leaked-flash-zero-day-likely-be-exploited-attackers
Users can use EMET to block the activity of this exploit.
www.kb.cert.org/vuls/id/561288
UPD1 : Vulnerability assigned an identifier CVE-2015-5119 (Windows, Linux, OS X). See Security Advisory for Adobe Flash Player (APSA15-03)
helpx.adobe.com/security/products/flash-player/apsa15-03.html
UPD2: ESET antivirus products detect the exploit as SWF / Exploit.Agent.IG .
virusradar.com/en/update/info/11902

be secure.


Fig. Sources of exploit.
')

Fig. Demonstrate the success of the exploit for the Opera web browser on a 32-bit version of Windows 7.

Fig. Same for google chrome. The source is here .

Fig. The exploit also works great on the latest MS Edge web browser on Windows 10 (build 10162).

Fig. The exploit works fine for IE11 on a 64-bit up-to-date version of Windows 7 with EPM enabled .
In this case, the most dangerous development of the situation will be that this exploit can get into one or several sets of exploits and will be used by attackers to organize drive-by attacks with automatic installation of malicious programs.
We recommend that users disable Flash Player for the browser you are using until Adobe has released the corresponding patch. Instructions for this process can be found here .
UPD: Symantec has also confirmed the relevance of this 0day exploit.
Leaked Flash Zero
www.symantec.com/connect/blogs/leaked-flash-zero-day-likely-be-exploited-attackers
Users can use EMET to block the activity of this exploit.
www.kb.cert.org/vuls/id/561288
UPD1 : Vulnerability assigned an identifier CVE-2015-5119 (Windows, Linux, OS X). See Security Advisory for Adobe Flash Player (APSA15-03)
helpx.adobe.com/security/products/flash-player/apsa15-03.html

UPD2: ESET antivirus products detect the exploit as SWF / Exploit.Agent.IG .
virusradar.com/en/update/info/11902

be secure.
Source: https://habr.com/ru/post/261979/
All Articles