Network security Instead of introducing
In today's global world, network security is crucial. Enterprises need to provide secure access for employees to network resources at any time, for which a modern network security strategy must take into account a number of factors, such as increasing network reliability, effective security management, and protection against constantly evolving threats and new attack methods. For many companies, the problem of network security is becoming increasingly difficult, because today's mobile workers using personal smartphones, laptops and tablets for work introduce new potential problems. At the same time, hackers also do not sit on their hands and make new cyber threats all the more sophisticated.

A recent survey of IT professionals who manage network security, [conducted by Slashdotmedia ] showed that among the important factors when choosing network security solutions, almost half of the respondents put reliability of the chosen network solution in the first place.
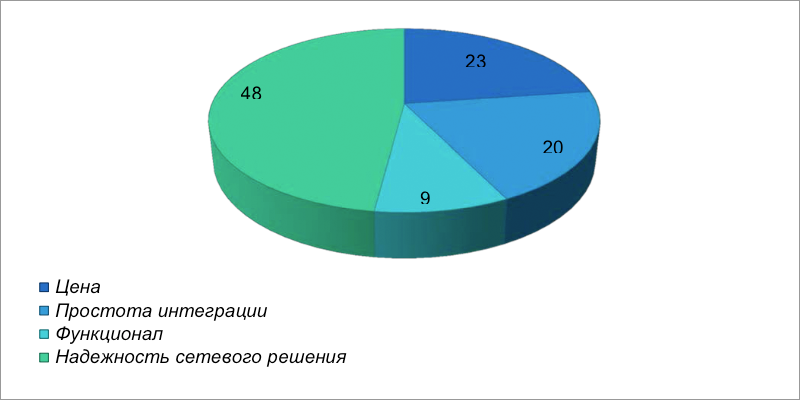
Asked Question: When you choose a network security solution, which factors are most important to your company?
')
Vulnerabilities associated with network security leave open a number of potential problems and expose the company to various risks. IT systems may be compromised through them, information may be stolen, employees and customers may have problems accessing the resources they are authorized to use, which may force customers to switch to a competitor.
Downtime related to security issues may have other financial implications. For example, a website that is down during peak hours can generate both direct losses and a powerful negative PR, which will obviously affect sales in the future. In addition, in some industries there are strict criteria for the availability of resources, the violation of which can lead to regulatory fines and other unpleasant consequences.
In addition to the reliability of solutions, there are still a number of issues that have come to the fore today. For example, about 23% of IT professionals surveyed highlight the cost of a solution as one of the main problems associated with network security; which is not surprising, given that the IT budgets of the last few years have been significantly limited. Further, about 20% of respondents identified the simplicity of integration as a priority parameter when choosing a solution. Which is natural in conditions when IT department is required to perform more with fewer resources.
Concluding the conversation about the key parameters in choosing a solution, I would like to note that only about 9% of respondents named network functions as a key factor when choosing solutions in the field of network security. When choosing a solution for ensuring network security of corporate systems and minimizing the associated risks, one of the most important factors for almost half (about 48%) of the respondents was the reliability of the network and its associated solution.
Asked Question: What type of network attacks is most concerned about your IT organization?
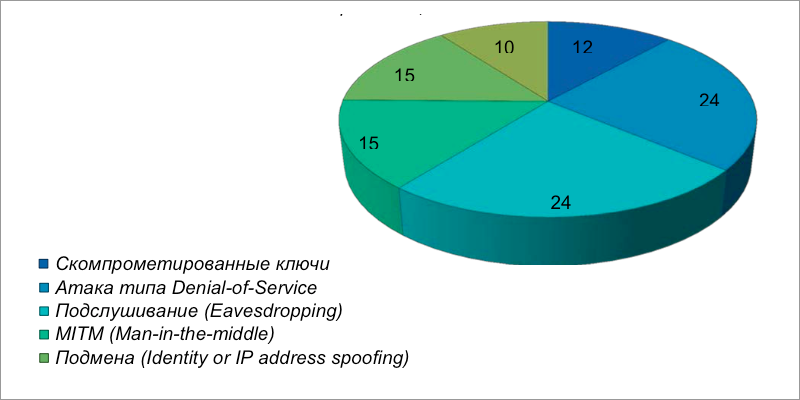
Today, hackers use a variety of methods to attack networks of companies. The study showed that IT professionals are most concerned about two specific types of attacks: denial of service attacks (DoS) and eavesdropping (Eavesdropping) - these attacks are listed as the most dangerous and top priority for about 25% of respondents. And 15% each selected key attacks as the type of IP Spoofing and MITM (man-in-the-middle). The remaining types of threats were given priority to less than 12% of respondents.
Asked Question: In terms of mobile vulnerabilities, what is most worrying your IT team?
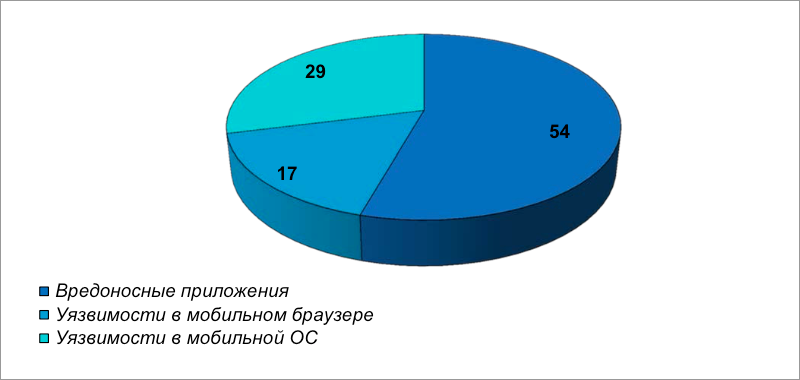
Today, the number of mobile workers is growing and the adaptation of the policy of using your own electronic devices for work (BOYD) is making new demands on network security. At the same time, unfortunately, the number of unsafe network applications is growing very rapidly. In 2013, HP tested more than 2,000 applications, which resulted in the discovery that 90% of applications have security vulnerabilities. This situation is a serious threat to corporate security and it is not surprising that 54% of respondents rated threats from malicious applications as the most dangerous.
Summarizing the above, we can draw the following conclusion: modern solutions for ensuring network security, among other things, must necessarily have the following properties:
A few words about the practice of ensuring information security in our country; We will briefly describe the current legal field that defines the aspects of information security in the Russian Federation. In the Russian Federation, all issues related to IS are governed by the following basic laws:
At the same time, laws regulating activities in areas related to information security imply serious responsibility for the violation of certain provisions, for example:
For most Russian enterprises, the relevance of network security issues is primarily related to the fact that they in one way or another process the data of individuals (at least, the data of their employees). Consequently, regardless of the type of activity, any company must take into account the requirements of the legislation of the Russian Federation and must apply various organizational and technical measures to protect information. Specific measures to protect this or that information are defined in the relevant Russian IB standards (GOST R ISO / IEC 15408, GOST R ISO 27001, etc.), as well as the guidelines of the Federal Service for Technical and Export Control (for example, the order of FSTEC № 58 dated 05.02.10, defining methods and methods for protecting systems that process personal data).
The fact that enterprises comply with the requirements of federal legislation today is controlled by three state bodies: the Federal Security Service (FSB), Roskomnadzor and FSTEC. Control is carried out by carrying out planned and sudden inspections, following which the company may be held accountable.
Thus, ignoring the problem of ensuring network security in our country can not only cause great losses to businesses, but also entail the criminal liability of specific company executives.
Information security threats are becoming more complex, hackers and cybercriminals are using new techniques and implementing increasingly sophisticated attacks with the aim of hacking systems and data theft.
The fight against new attacks requires solutions to ensure network security and the development of a network security strategy that meets the requirements of reliability, cost and integration with other IT systems. The solutions developed must be reliable, provide protection against attacks at the application level, and allow identifying traffic.
From the above, a simple conclusion suggests itself: in today's world, information security issues cannot be ignored; in response to new threats, you need to look for new approaches to implementing information protection strategies and use new methods and means of ensuring network security.
Our previous publications:
» HP Integrity NonStop: availability is key
» Cost-effective HP servers for SMB and providers
» HP OpenStack Helion - First Meet
» SDN: alternative or addition to traditional networks?
» New network architectures: open or closed solutions?
» Implementing MSA in a virtualized enterprise environment
» HP MSA Disk Arrays as a Basis for Data Consolidation
» Multivendor corporate network: myths and reality
» Available HP ProLiant server models (10 and 100 series)
» Convergence based on HP Networking. Part 1
» HP ProLiant ML350 Gen9 - server with insane extensibility
Thanks for attention!

A recent survey of IT professionals who manage network security, [conducted by Slashdotmedia ] showed that among the important factors when choosing network security solutions, almost half of the respondents put reliability of the chosen network solution in the first place.
Asked Question: When you choose a network security solution, which factors are most important to your company?
')

Vulnerabilities associated with network security leave open a number of potential problems and expose the company to various risks. IT systems may be compromised through them, information may be stolen, employees and customers may have problems accessing the resources they are authorized to use, which may force customers to switch to a competitor.
Downtime related to security issues may have other financial implications. For example, a website that is down during peak hours can generate both direct losses and a powerful negative PR, which will obviously affect sales in the future. In addition, in some industries there are strict criteria for the availability of resources, the violation of which can lead to regulatory fines and other unpleasant consequences.
In addition to the reliability of solutions, there are still a number of issues that have come to the fore today. For example, about 23% of IT professionals surveyed highlight the cost of a solution as one of the main problems associated with network security; which is not surprising, given that the IT budgets of the last few years have been significantly limited. Further, about 20% of respondents identified the simplicity of integration as a priority parameter when choosing a solution. Which is natural in conditions when IT department is required to perform more with fewer resources.
Concluding the conversation about the key parameters in choosing a solution, I would like to note that only about 9% of respondents named network functions as a key factor when choosing solutions in the field of network security. When choosing a solution for ensuring network security of corporate systems and minimizing the associated risks, one of the most important factors for almost half (about 48%) of the respondents was the reliability of the network and its associated solution.
Asked Question: What type of network attacks is most concerned about your IT organization?

Today, hackers use a variety of methods to attack networks of companies. The study showed that IT professionals are most concerned about two specific types of attacks: denial of service attacks (DoS) and eavesdropping (Eavesdropping) - these attacks are listed as the most dangerous and top priority for about 25% of respondents. And 15% each selected key attacks as the type of IP Spoofing and MITM (man-in-the-middle). The remaining types of threats were given priority to less than 12% of respondents.
Asked Question: In terms of mobile vulnerabilities, what is most worrying your IT team?

Today, the number of mobile workers is growing and the adaptation of the policy of using your own electronic devices for work (BOYD) is making new demands on network security. At the same time, unfortunately, the number of unsafe network applications is growing very rapidly. In 2013, HP tested more than 2,000 applications, which resulted in the discovery that 90% of applications have security vulnerabilities. This situation is a serious threat to corporate security and it is not surprising that 54% of respondents rated threats from malicious applications as the most dangerous.
Summarizing the above, we can draw the following conclusion: modern solutions for ensuring network security, among other things, must necessarily have the following properties:
- be able to work at the seventh level of the OSI model (at the application level);
- be able to associate a specific user with the content of traffic;
- have an integrated system of protection against network attacks (IPS)
- support built-in protection against attacks such as DoS and listening;
- generally have a high degree of reliability.
A few words about the practice of ensuring information security in our country; We will briefly describe the current legal field that defines the aspects of information security in the Russian Federation. In the Russian Federation, all issues related to IS are governed by the following basic laws:
- FL 149 "On Information, Information Technologies and Protection of Information";
- FZ 152 “On the protection of personal data”;
- FL 139 (amendments to the Federal Law 149, the Law on Communications and the Federal Law 436 on the protection of children from information);
- FZ 436 (on protection from children's information);
- FZ 187 (on protection of intellectual property and the Internet);
- FZ 398 (on blocking extremist sites);
- FZ 97 (about bloggers who equate them to the media);
- FZ 242 (on the placement of personal data on the territory of the Russian Federation).
At the same time, laws regulating activities in areas related to information security imply serious responsibility for the violation of certain provisions, for example:
- Under article 137 of the Criminal Code of the Russian Federation (illegal collection or dissemination of information about a person’s private life) - imprisonment for up to four years;
- Under article 140 of the Criminal Code of the Russian Federation (unlawful refusal to provide documents and materials collected in the prescribed manner) - a fine or deprivation of the right to occupy certain positions or engage in certain activities for a period of 2 to 5 years;
- Under article 272 of the Criminal Code of the Russian Federation (illegal access to legally protected computer information) - imprisonment for a term of up to 5 years.
For most Russian enterprises, the relevance of network security issues is primarily related to the fact that they in one way or another process the data of individuals (at least, the data of their employees). Consequently, regardless of the type of activity, any company must take into account the requirements of the legislation of the Russian Federation and must apply various organizational and technical measures to protect information. Specific measures to protect this or that information are defined in the relevant Russian IB standards (GOST R ISO / IEC 15408, GOST R ISO 27001, etc.), as well as the guidelines of the Federal Service for Technical and Export Control (for example, the order of FSTEC № 58 dated 05.02.10, defining methods and methods for protecting systems that process personal data).
The fact that enterprises comply with the requirements of federal legislation today is controlled by three state bodies: the Federal Security Service (FSB), Roskomnadzor and FSTEC. Control is carried out by carrying out planned and sudden inspections, following which the company may be held accountable.
Thus, ignoring the problem of ensuring network security in our country can not only cause great losses to businesses, but also entail the criminal liability of specific company executives.
Conclusion
Information security threats are becoming more complex, hackers and cybercriminals are using new techniques and implementing increasingly sophisticated attacks with the aim of hacking systems and data theft.
The fight against new attacks requires solutions to ensure network security and the development of a network security strategy that meets the requirements of reliability, cost and integration with other IT systems. The solutions developed must be reliable, provide protection against attacks at the application level, and allow identifying traffic.
From the above, a simple conclusion suggests itself: in today's world, information security issues cannot be ignored; in response to new threats, you need to look for new approaches to implementing information protection strategies and use new methods and means of ensuring network security.
Our previous publications:
» HP Integrity NonStop: availability is key
» Cost-effective HP servers for SMB and providers
» HP OpenStack Helion - First Meet
» SDN: alternative or addition to traditional networks?
» New network architectures: open or closed solutions?
» Implementing MSA in a virtualized enterprise environment
» HP MSA Disk Arrays as a Basis for Data Consolidation
» Multivendor corporate network: myths and reality
» Available HP ProLiant server models (10 and 100 series)
» Convergence based on HP Networking. Part 1
» HP ProLiant ML350 Gen9 - server with insane extensibility
Thanks for attention!
Source: https://habr.com/ru/post/261913/
All Articles