Cyber group Hacking Team has undergone large-scale hacking
The well-known cyber group Hacking Team ( @hackingteam ), which specializes in the development and sale of special spyware for law enforcement agencies and special services of various states, has become the target of a cyber attack, as a result of which an archive of 400GB of various confidential information has become available to the public. The Hacking Team’s personal correspondence with their clients, contracts for the sale of their cyber-products to various states, as well as a large amount of other information related to the company's activities have leaked to the network.

As a result of the leak, it became known that not only government agencies, but also private companies, resorted to HT services. Also from the published data it is clear that one of the HT clients were Russian structures or firms. The archive also contains information about the cyber group's exploits (Exploit_Delivery_Network_android, Exploit_Delivery_Network_Windows), as well as a huge amount of various explanatory information (wiki).
')

Fig. List of client countries HT. It is visible that in the list there are Russia, Kazakhstan, Uzbekistan. Azerbaijan.
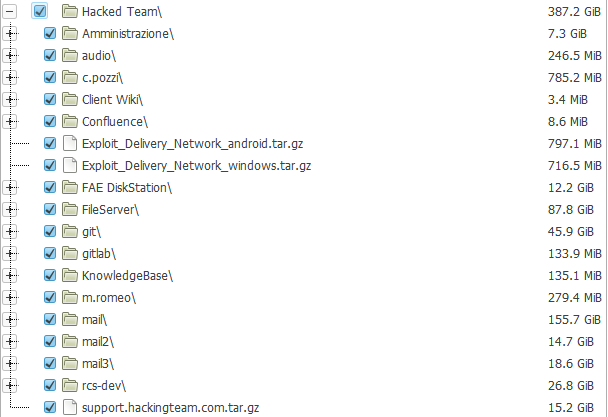
Fig. The structure of the published archive.

Fig. One of the documents confirming the cooperation of HT with the special services of Sudan, which is clearly contrary to the recently adopted additions to the Wassenaar Agreement, which imposes restrictions on the export of this type of software to countries with "non-democratic" regime. From the published data, it became clear that HT recommended that such countries use special VPN services located in Germany and the USA when working with their services.
HT specializes in the development of so-called. Spyware Remote Control Systems (RCS) , which special services and law enforcement agencies use for their purposes in cyberspace. HT products can work on a variety of platforms, including Windows, Android, OS X. One of the most famous HT products is known as DaVinci or Galileo, the files of which have repeatedly come under the “lenses” of antivirus companies.
The company is rather closed and until recently, little was known about its activities. One of the first organizations who shed light on the activities of HT was Wikileaks .

Fig. HT's proposed spying methods given by Wikileaks.
So the Hacking Team is positioning its software. The range of actions performed by him is quite extensive: collecting various data on a computer and then sending it to a remote server, keylogger, recording telephone conversations, storing device camera data, etc.

Fig. List of actions performed by DaVinci / Galileo given by Wikileaks.
UPD:

Fig. Source code HT software and their various tools from the archive. It can be seen that a variety of operating systems are supported, including mobile ones.
To sign iOS, HT applications used their enterprise developer certificate with the following identifiers .
Subject: UID = DE9J4B8GTF, CN = iPhone Distribution: HT srl, OU = DE9J4B8GTF, O = HT srl, C = IT

Fig. Part of the exploits that used HT.

Fig. Part of LPE (sandbox escape) source code 0day exploit for the atmfd.dll system library. [gitlab / Windows-Multi-Browser / 2_stage_shellcode_so urce / source_pie_8.1 / elevator.c]

Fig. HT presentation to intercept TOR traffic. [rcs-dev% 5cshare / HOME / Naga / httpX / Prese ntation.pptx]
UPD2 : HT notified its customers to discontinue use of the software.
Hacking Team Software After Hack
motherboard.vice.com/read/hacking-team-asks-customers-to-stop-using-its-software-after-hack
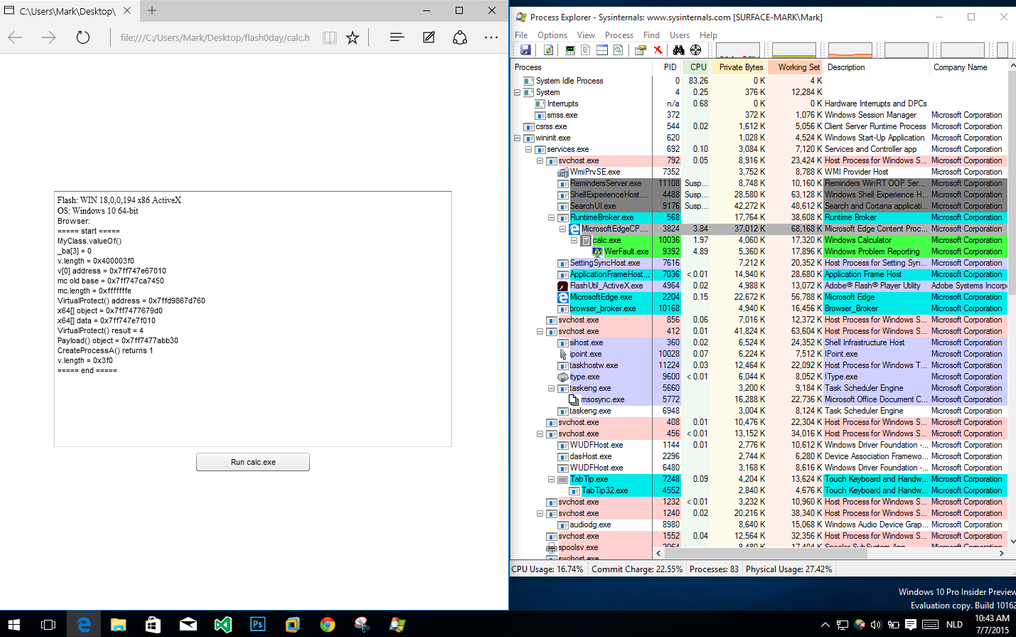
UPD3 Archive contains RCE 0day exploit for Flash Player with the ability to bypass the sandbox on the current version of Google Chrome.
Demonstration of successful operation. The source is here .
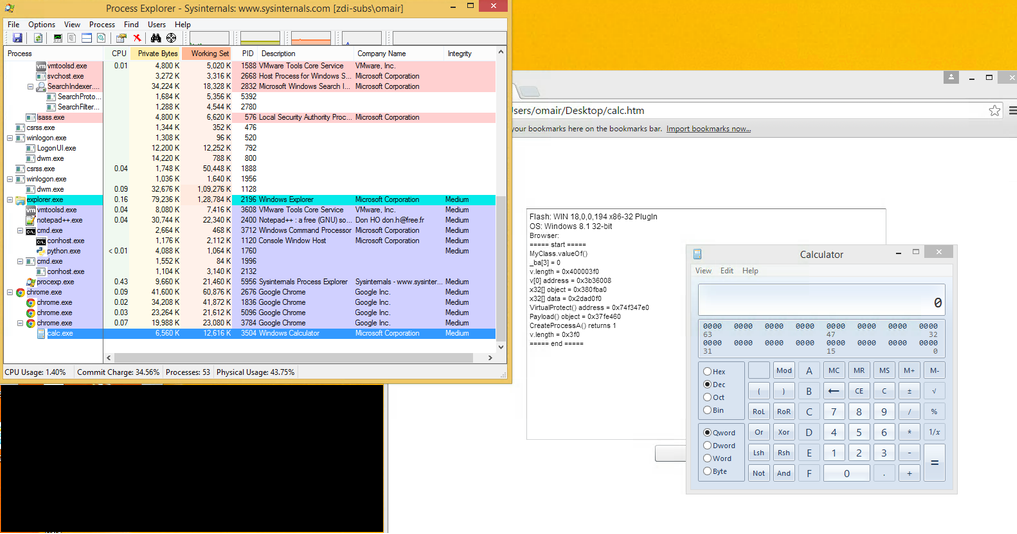
The exploit also works great on the latest MS Edge web browser on Windows 10 (build 10162).
The directory / rcs-dev \ share / Documentation / Manuals / contains a large amount of documentation on various versions of the RCS product. The /rcs-dev%5cshare/Documentation/Manuals/9.5.0/EN/RCS%209.5%20Technician%20EN.pdf document contains a detailed description of the functions of one of the latest RCS versions [170 pages].

UPD4 Separate post for information about 0day vulnerabilities in Flash Player.
A dangerous 0day vulnerability has been discovered in Adobe Flash Player.
habrahabr.ru/company/eset/blog/261979

As a result of the leak, it became known that not only government agencies, but also private companies, resorted to HT services. Also from the published data it is clear that one of the HT clients were Russian structures or firms. The archive also contains information about the cyber group's exploits (Exploit_Delivery_Network_android, Exploit_Delivery_Network_Windows), as well as a huge amount of various explanatory information (wiki).
')

Fig. List of client countries HT. It is visible that in the list there are Russia, Kazakhstan, Uzbekistan. Azerbaijan.

Fig. The structure of the published archive.

Fig. One of the documents confirming the cooperation of HT with the special services of Sudan, which is clearly contrary to the recently adopted additions to the Wassenaar Agreement, which imposes restrictions on the export of this type of software to countries with "non-democratic" regime. From the published data, it became clear that HT recommended that such countries use special VPN services located in Germany and the USA when working with their services.
HT specializes in the development of so-called. Spyware Remote Control Systems (RCS) , which special services and law enforcement agencies use for their purposes in cyberspace. HT products can work on a variety of platforms, including Windows, Android, OS X. One of the most famous HT products is known as DaVinci or Galileo, the files of which have repeatedly come under the “lenses” of antivirus companies.
The company is rather closed and until recently, little was known about its activities. One of the first organizations who shed light on the activities of HT was Wikileaks .

Fig. HT's proposed spying methods given by Wikileaks.
In modern digital communications, encryption is safe to protect users from eavesdropping. Unfortunately, the encryption also makes it impossible to monitor and control the country’s security.
It is possible to control the remote control system (RCS). RCS server is encrypted and untraceable.
So the Hacking Team is positioning its software. The range of actions performed by him is quite extensive: collecting various data on a computer and then sending it to a remote server, keylogger, recording telephone conversations, storing device camera data, etc.

Fig. List of actions performed by DaVinci / Galileo given by Wikileaks.
UPD:

Fig. Source code HT software and their various tools from the archive. It can be seen that a variety of operating systems are supported, including mobile ones.
To sign iOS, HT applications used their enterprise developer certificate with the following identifiers .
Subject: UID = DE9J4B8GTF, CN = iPhone Distribution: HT srl, OU = DE9J4B8GTF, O = HT srl, C = IT

Fig. Part of the exploits that used HT.

Fig. Part of LPE (sandbox escape) source code 0day exploit for the atmfd.dll system library. [gitlab / Windows-Multi-Browser / 2_stage_shellcode_so urce / source_pie_8.1 / elevator.c]

Fig. HT presentation to intercept TOR traffic. [rcs-dev% 5cshare / HOME / Naga / httpX / Prese ntation.pptx]
UPD2 : HT notified its customers to discontinue use of the software.
Hacking Team Software After Hack
motherboard.vice.com/read/hacking-team-asks-customers-to-stop-using-its-software-after-hack
UPD3 Archive contains RCE 0day exploit for Flash Player with the ability to bypass the sandbox on the current version of Google Chrome.
Demonstration of successful operation. The source is here .

The exploit also works great on the latest MS Edge web browser on Windows 10 (build 10162).

The directory / rcs-dev \ share / Documentation / Manuals / contains a large amount of documentation on various versions of the RCS product. The /rcs-dev%5cshare/Documentation/Manuals/9.5.0/EN/RCS%209.5%20Technician%20EN.pdf document contains a detailed description of the functions of one of the latest RCS versions [170 pages].

UPD4 Separate post for information about 0day vulnerabilities in Flash Player.
A dangerous 0day vulnerability has been discovered in Adobe Flash Player.
habrahabr.ru/company/eset/blog/261979
Source: https://habr.com/ru/post/261887/
All Articles