Will backup antivirus replace?
Any protection system that actively analyzes the behavior of the system (antivirus, behavioral analyzer, protection against network attacks, etc.) consume, and often very actively, the resources of the protected system. Roughly speaking, the protection slows down the work of the applications (and in the case of non-optimal settings, sometimes very strongly). Naturally, this does not cause delight and the desire to refuse such protection is understandable, replacing it with alternative measures - restriction of rights, a reservation system, etc.
You can not grasp the immensity. Therefore, let's talk only about backup as an alternative to antivirus.
Naturally, large (and / or rich companies) can afford a lot, but in everyday life, most often data is backed up by simply copying over the network or on external media, synchronizing with the storage in the cloud, using shadow copying (which is very often presented as a panacea ) or by using a NAS. How reliable is this in terms of virus protection?
Let's not talk long and consider four examples:
')
And one more risk, which should not be forgotten. Modern malware designed for a long and imperceptible presence in the system. Due to the fact that antiviruses cannot know everything, viruses and trojans may remain undetected for years (as examples, practically any of the recent investigations can be cited). Accordingly, there is no guarantee that the restored from the backup system will not be affected (possibly later deleted) by a trojan
It's funny that backup is not the first technology, positioned as a replacement for antivirus. Behavioral analyzers, cloud antiviruses ... Who, apart from professionals, remembers products based purely on these technologies? And traditional antiviruses not only survived, but also increased the size of distributions by the amount of code and data needed to implement the technologies that were supposed to kill them. Dr.Web Security Space and Kaspersky Cristal now include features that can be attributed to backup ...
Wait and see. In the meantime, recommendations about using backup as a means of protecting against malicious programs are so common that even in the news about Trojan.Encoder.737 there is a paragraph about the need for regular backup.
And not to be misunderstood. The author does not belong to any of the sides of the dark force and does not believe that there is any one right decision. There are cases when it is advantageous to use an antivirus, if there are cases when its use is in principle contraindicated. This article wanted to show that no solution could be trusted, no matter how advertised it was. And protection against viruses is a great example - much of the above is possible only with incorrectly configured access rights. So, the command of deleting shadow copies works only with administrator rights, therefore, after enabling protection, it is necessary to work only under a user with limited rights and be attentive to all warnings from UAC about an attempt to enhance rights.

What is this article about?
You can not trust the myths and prevailing preferences (nothing lasts forever under the Moon. What was considered reliable yesterday will be handled by attackers tomorrow without problems), it will be carried out on advertising pads claiming that everything will work out with it. Especially when choosing the means of protection on which the fate of your data and money will depend. And soon (the Internet of things is coming!) And your health.
Good luck with your choice!
You can not grasp the immensity. Therefore, let's talk only about backup as an alternative to antivirus.
Naturally, large (and / or rich companies) can afford a lot, but in everyday life, most often data is backed up by simply copying over the network or on external media, synchronizing with the storage in the cloud, using shadow copying (which is very often presented as a panacea ) or by using a NAS. How reliable is this in terms of virus protection?
Let's not talk long and consider four examples:
')
- AlphaCrypt . He is Trojan.Encoder.1064. I got into the anti-virus database on May 13, 2015. A fairly recent example of a trojan.
AlphaCrypt, using the RSA-2048 encryption algorithm, encrypts files, assigning them after that the .ezz extension, and then, like all cryptographers, requires a ransom. The cost of decryption in the case of AlphaCrypt $ 500 bitcoins.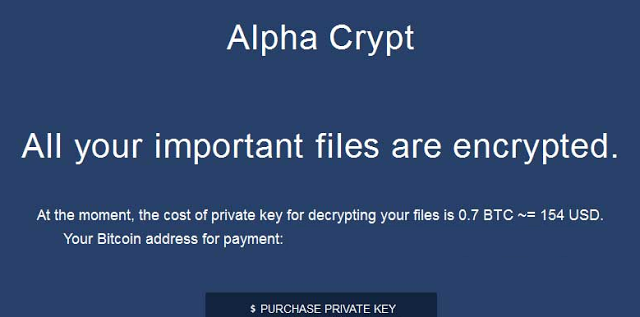
Traditionally can be spread using spam with an infected attachment, sending messages in messengers. Naturally, you can download the Trojan yourself as a legitimate application. Infection occurs via the Angler exploit kit.
In general, nothing particularly outstanding. With the exception of one feature - AlphaCrypt can delete shadow copies of Volume Shadow Copy Service, VSS. Naturally, the Trojan tries to perform this operation quietly - without displaying any notifications on the computer screen.
This operation is performed using the command:
vssadmin.exe delete shadows / all / Quiet /
Some more information about AlphaCrypt and ryptolocker in general can be obtained here and here .
On Habrahabr, the possibilities and limitations of shadow copying were discussed for example here . - Trojan.Encoder. With rare exceptions, they encrypt everything they can reach. If the network folder is mounted as a local network drive, almost all Trojan.Encoder representatives can encrypt the contents. With the exception of Trojan.Encoder.398 , which encrypts only fixed disks (DRIVE_FIXED) and Trojan.Encoder.453 , which also makes a list of only local non-removable media on which it selects files by mask. However, most encryptors do not do such checks and encrypt network folders along with local ones.
- Win32.Sector, a complex polymorphic virus that has been around since 2008. How the virus is able to spread on its own - including infecting files stored in public network folders. By the way, it can stop some anti-virus programs and block access to the sites of their developers (discussion of the need for self-defense as an antivirus component was here )
- Trojan.Encoder.737. Using vulnerabilities in the Synology Trojan’s NAS (Network Attached Storage) network storage software, it encrypts the data stored on the device and requires a ransom of $ 350 from the victim. Currently, decryption of files affected by the action of Trojan.Encoder.737 is not possible.
And one more risk, which should not be forgotten. Modern malware designed for a long and imperceptible presence in the system. Due to the fact that antiviruses cannot know everything, viruses and trojans may remain undetected for years (as examples, practically any of the recent investigations can be cited). Accordingly, there is no guarantee that the restored from the backup system will not be affected (possibly later deleted) by a trojan
It's funny that backup is not the first technology, positioned as a replacement for antivirus. Behavioral analyzers, cloud antiviruses ... Who, apart from professionals, remembers products based purely on these technologies? And traditional antiviruses not only survived, but also increased the size of distributions by the amount of code and data needed to implement the technologies that were supposed to kill them. Dr.Web Security Space and Kaspersky Cristal now include features that can be attributed to backup ...
Wait and see. In the meantime, recommendations about using backup as a means of protecting against malicious programs are so common that even in the news about Trojan.Encoder.737 there is a paragraph about the need for regular backup.
And not to be misunderstood. The author does not belong to any of the sides of the dark force and does not believe that there is any one right decision. There are cases when it is advantageous to use an antivirus, if there are cases when its use is in principle contraindicated. This article wanted to show that no solution could be trusted, no matter how advertised it was. And protection against viruses is a great example - much of the above is possible only with incorrectly configured access rights. So, the command of deleting shadow copies works only with administrator rights, therefore, after enabling protection, it is necessary to work only under a user with limited rights and be attentive to all warnings from UAC about an attempt to enhance rights.

What is this article about?
You can not trust the myths and prevailing preferences (nothing lasts forever under the Moon. What was considered reliable yesterday will be handled by attackers tomorrow without problems), it will be carried out on advertising pads claiming that everything will work out with it. Especially when choosing the means of protection on which the fate of your data and money will depend. And soon (the Internet of things is coming!) And your health.
Good luck with your choice!
Source: https://habr.com/ru/post/261881/
All Articles