Expanding the functionality of the "notebook"
In this article, we explore the equivalent of one very famous Windows program called Notepad and write a DLL that extends its capabilities. Analog is called NFOPad.
Source codes not included
This program can process text files and search, replace text, that is, the functionality is in no way inferior to the world famous Notepad. Now we will teach him to process encrypted files. There are no plug-ins for this miracle of technological progress either, and therefore we will need: Assembler knowledge, debugger, brains and compiler capable of breaking the code into a DLL.
')
In this article we will teach him to create encrypted files, and first we need to find the place where the file is written to when it is saved.
Open NFOPad in the debugger (I personally use the Cheat Engine) and go to the WriteFile function:
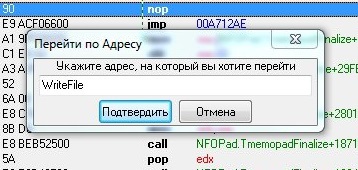
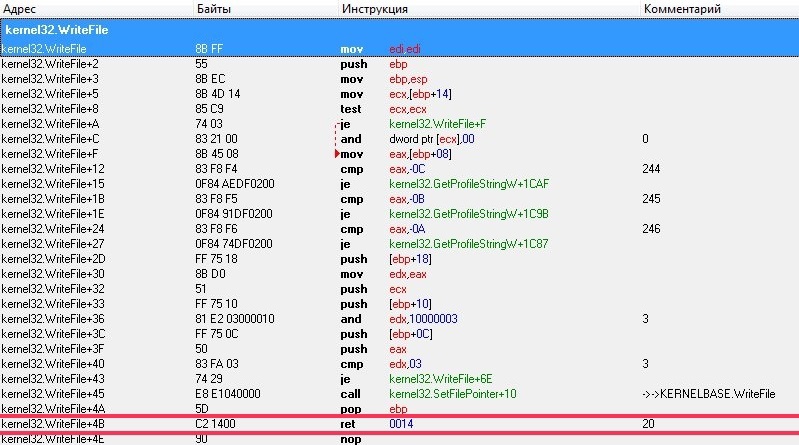
Here we are in the body of the function WriteFile. Now we need to find where this function will be called from when saving the file, and for this we set a breakpoint on the ret command
Now we will print some nonsense in a notebook and save:
After we ordered the notepad to save the text, the breakpoint worked and after pressing F8 we go to the return address:
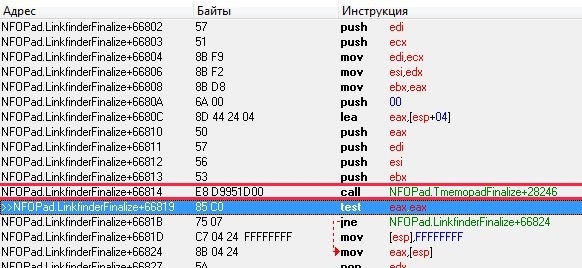
What is highlighted in red is a call to the WriteFile function that saves the entered text to a text file.
Here is a further action plan. We will create a DLL library in which there will be a function with identical arguments as in WriteFile and when loading it will replace the address of the function call that is highlighted in red with its own.
Open Visual Studio and create a DLL project. First of all, let's write a function that will be called instead of WriteFile and call it CrackWriteFile. It will encrypt the transmitted text and then call WriteFile and pass its arguments to it.
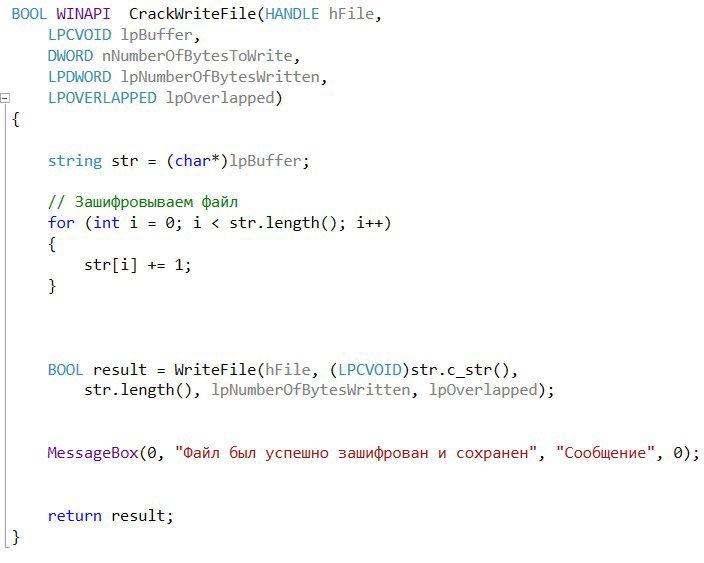
Now we will write a function that will replace the address:
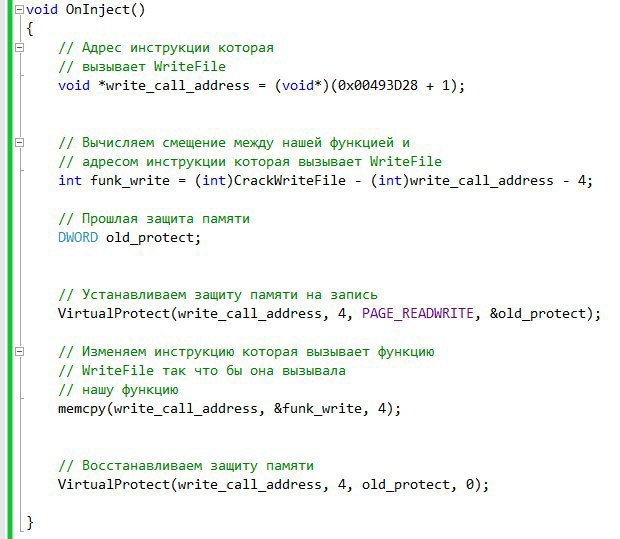
At the entry point still need to register a call to this function. I think everything is clear and proceed to testing. Inject the compiled DLL into the notepad process and enter the following text into the editor:
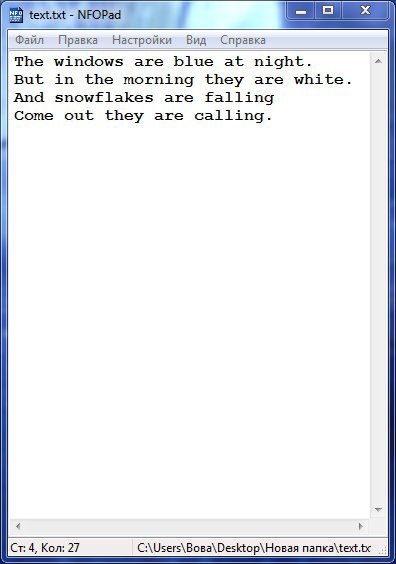
Now in the saved file we see not a beautiful poem, and here it is:
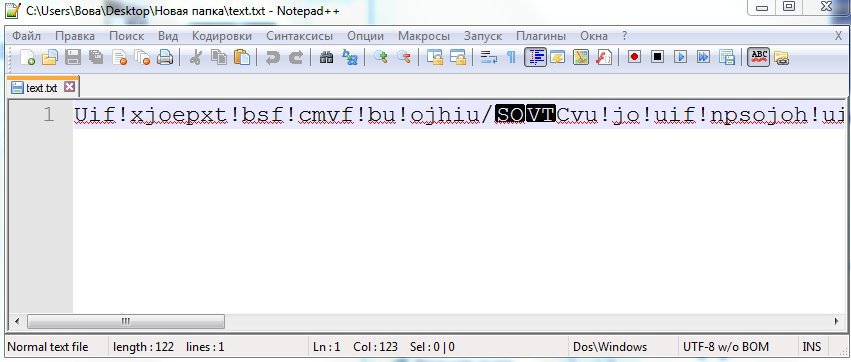
This is in fact the poem, but encrypted by our algorithm. Now we will teach him also to read the encrypted files. To do this, we also set brekpoint, but this bryak will work on the ReadFile function and when opening any file. Then, according to the script we have already worked out, go to the return address and find out where the function was called from.
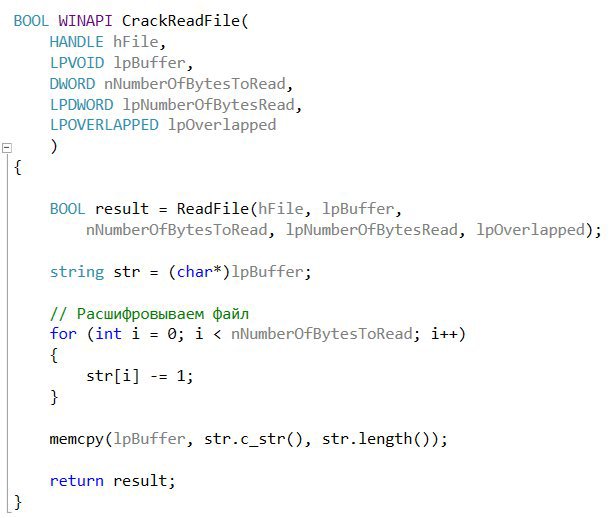
Now we add the CrackReadFile function to our project, which will be called when the notepad opens the file.
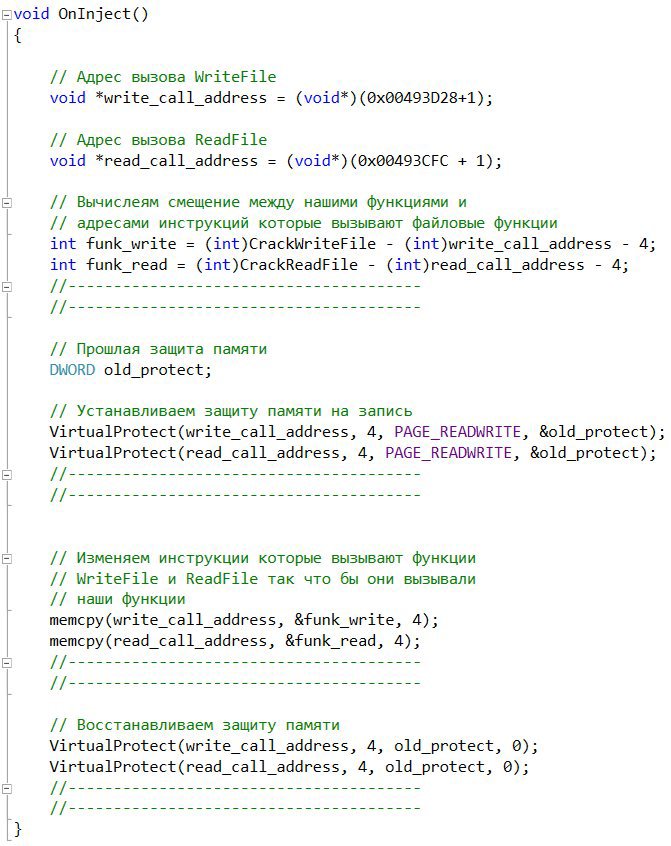
Now we change the OnInject function:
Now, if after the DLL injection into the process, the encrypted file is displayed normally, then everything is done correctly. In this article, we have expanded the functionality of the analog notebook. Of course, if desired, it was possible to significantly modify our extension, for example, to make the checkbox appear in the program's interface and only if it is installed, the program encrypts files, or the encryption algorithm can be improved, but this is not the point, since the purpose of the article was to tell that using reverse -engineering can expand the capabilities of programs. As time will be, I will continue to write similar articles, and since it is summer now, I’m full of it.
I hope my article was interesting to you.
Source codes not included

This program can process text files and search, replace text, that is, the functionality is in no way inferior to the world famous Notepad. Now we will teach him to process encrypted files. There are no plug-ins for this miracle of technological progress either, and therefore we will need: Assembler knowledge, debugger, brains and compiler capable of breaking the code into a DLL.
')
In this article we will teach him to create encrypted files, and first we need to find the place where the file is written to when it is saved.
Open NFOPad in the debugger (I personally use the Cheat Engine) and go to the WriteFile function:

Here we are in the body of the function WriteFile. Now we need to find where this function will be called from when saving the file, and for this we set a breakpoint on the ret command

Now we will print some nonsense in a notebook and save:

After we ordered the notepad to save the text, the breakpoint worked and after pressing F8 we go to the return address:

What is highlighted in red is a call to the WriteFile function that saves the entered text to a text file.
Here is a further action plan. We will create a DLL library in which there will be a function with identical arguments as in WriteFile and when loading it will replace the address of the function call that is highlighted in red with its own.
Open Visual Studio and create a DLL project. First of all, let's write a function that will be called instead of WriteFile and call it CrackWriteFile. It will encrypt the transmitted text and then call WriteFile and pass its arguments to it.

Now we will write a function that will replace the address:

At the entry point still need to register a call to this function. I think everything is clear and proceed to testing. Inject the compiled DLL into the notepad process and enter the following text into the editor:

Now in the saved file we see not a beautiful poem, and here it is:

This is in fact the poem, but encrypted by our algorithm. Now we will teach him also to read the encrypted files. To do this, we also set brekpoint, but this bryak will work on the ReadFile function and when opening any file. Then, according to the script we have already worked out, go to the return address and find out where the function was called from.
Now we add the CrackReadFile function to our project, which will be called when the notepad opens the file.

Now we change the OnInject function:

Now, if after the DLL injection into the process, the encrypted file is displayed normally, then everything is done correctly. In this article, we have expanded the functionality of the analog notebook. Of course, if desired, it was possible to significantly modify our extension, for example, to make the checkbox appear in the program's interface and only if it is installed, the program encrypts files, or the encryption algorithm can be improved, but this is not the point, since the purpose of the article was to tell that using reverse -engineering can expand the capabilities of programs. As time will be, I will continue to write similar articles, and since it is summer now, I’m full of it.
I hope my article was interesting to you.
Source: https://habr.com/ru/post/261541/
All Articles