Analysis of tasks of the Competitive Intelligence Competition on PHDays V
 This year, not only traditional amateurs of the competition, but also CTF teams played in “ Competitive Intelligence ”, therefore, according to the level of difficulty, tasks were selected for those and for others. In addition, a team game was allowed. (But one person could not play in the individual standings, and for the CTF team, so we had to disqualify by mutual agreement the participant who took the 1st place on points - azrael ).
This year, not only traditional amateurs of the competition, but also CTF teams played in “ Competitive Intelligence ”, therefore, according to the level of difficulty, tasks were selected for those and for others. In addition, a team game was allowed. (But one person could not play in the individual standings, and for the CTF team, so we had to disqualify by mutual agreement the participant who took the 1st place on points - azrael ).Under the general legend of the state of United States of Soviet Unions, all competitions were combined, and in the framework of "Competitive Intelligence", participants had to look for information about employees of various companies "registered" in the USSU. In parallel, it was possible to answer five different questions about five different organizations; within one block, the questions opened one after the other as they received answers. ( One team found the answer using the brute force method, but they could not answer the next question - they did not have the necessary resources in their hands. )
1. Find out the dinner of Bank of Snatch (snatch-bank.phdays.com) Chairman of the Snatch (snatch-bank.phdays.com) chairman.
')
In this group of questions it was necessary to find information about the chairman of the board of Bank of Snatch.
1.1. Get his email address
You need to start small - to find out email chairman of the board. Google has tried for us a long time ago - it has cached several pages of snatch-bank.phdays.com, including a document with bank statements.
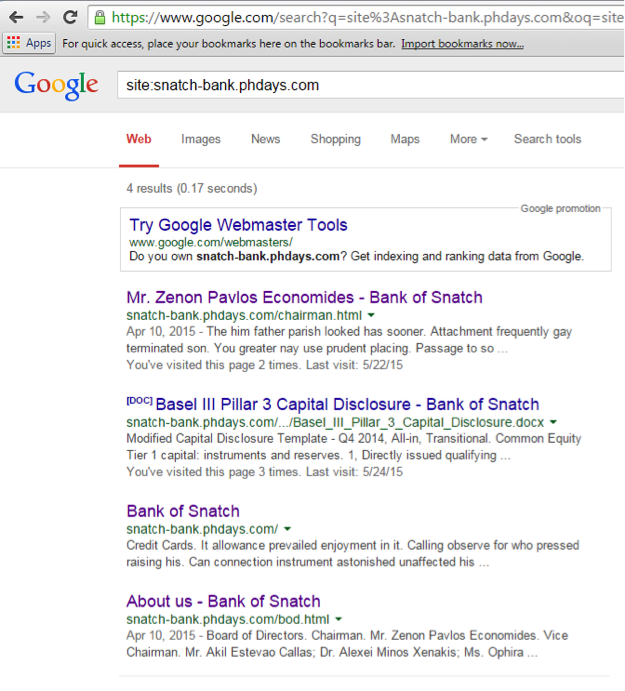
In the meta tags of this document it is clearly seen that the user Aldora Jacinta Artino has
a_j.artino.bank@ussu-gov.org . This means that the chairman of Zenon Pavlos Economides post should be z_p.economides.bank@ussu-gov.org .Correct answers: 47
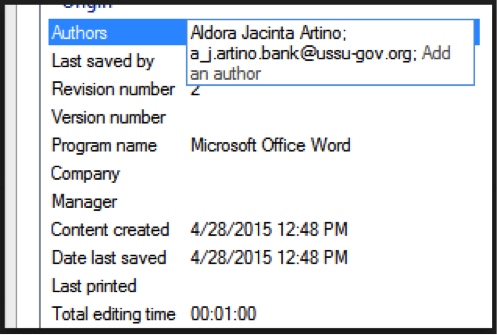
1.2. What is his domain account? (format: user: password)
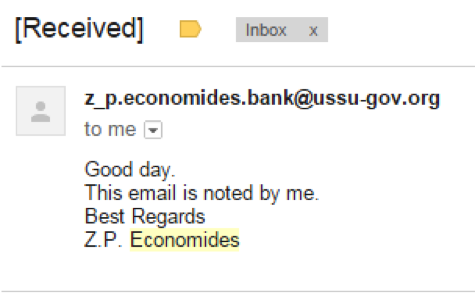
Now the task is complicated: you need to get a domain account - the name and password. But for those who play competitive intelligence regularly, this task was not too difficult. After all, if you send a letter to the address found in the previous step, you will receive an unambiguous hint that the person has read it. So, you can try to slip him a link in the letter.
Note: the chairman of the browser browser blocked all sorts of nonstandard web ports like 1337, so it was better to use the traditional 80 or 8080.
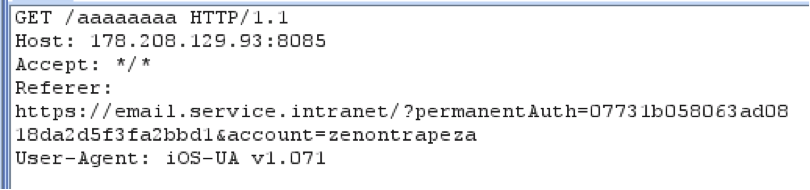
Having captured the request, you can find out that the mail resource sends the
Referer header in the requests, and from it you can get the mail account login and password: zenontrapeza:zenon123 .Correct answers: 17
1.3. And finally get the dinner place
Well, finally, you need to find out where the chairman of the board is having lunch. Everything else, we now know the pseudonym of the chairman - zenontrapeza. You can use Google again. For 2 clicks, you can find out the account of the chairman in FB, and it turns out that he likes to constantly use some kind of tracker.
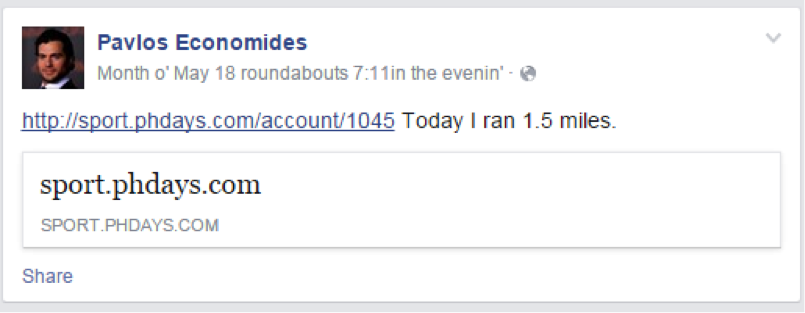
Only now the tracker works somehow wrong. And for a few simple manipulations with the url and id, you could get access to the Pavlos track file :
- sport.phdays.com/account/1045
- sport.phdays.com/achive/1045
- sport.phdays.com/img/1045
- sport.phdays.com/img/1 which gave an error by which you could find the final URL - sport.phdays.com/kmls/track.kml?id=1045
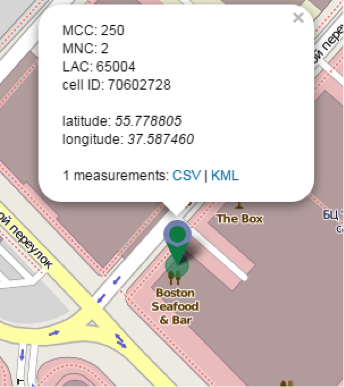
As a result, we get the desired track. The next problem: it does not contain the GPS coordinates, but the identifier of the base station of the cellular operator. Know the problems! After all, there is a wonderful resource
opencellid.org , which allows you to find the coordinates of a specific base station around the world.Finding out the coordinates of the base stations and determining the dinner interval (excluding Sunday), it was possible to find the name of the restaurant on the same opencellid: Boston Seafood & Bar :
Correct answers: 12
2. Get intel on MiTM Mobile (mitm-mobile.phdays.com) marketing director.
In this group of questions it was necessary to collect information about the director of marketing for the mobile operator MiTM Mobile.
2.1. We have a network laptop screen (https://mega.co.nz/#!34IEGYZa!Xowwo-UFTWMIfqfmiSPQXMWY0F7mySb-WtIxB3SVXWQ). Can you find out where he was treated?
Where did the marketing director go? The traffic dump allowed finding out not only the domain login of one of the Positive Technologies employees, but also a request to the USSU search engine . And judging by the banner and Cookies settings on ussu.phdays.com/search.php , the search engine uses the same utmz token mechanisms as in Google. And if we substitute these values in the request to
search.php , then contextual advertising about one clinic will be highlighted. What kind of clinic it is - you can find out by performing a search on the images (weeding out all unnecessary, because you needed an absolutely identical image) or even easier - by searching for the phone number from the image. The correct answer: Rayville Recovery .
Correct answers: 13
2.2. Ok, now we know his email account. It is l_u.imbesi@ussu-gov.org - we need access (give us email password).
Now we know the director's email, but the password is missing. Robots.txt files are sometimes just a storehouse of vulnerable scripts that need to be kept away, not from search engines, but from hackers. So here: there is a link to the backup script for recovering a password from the mail
restore.php . If you cause a password reset in debug mode - debug = On, then we will be able to find out that emails are sent through an appeal to the server on port 25. But the server name is taken directly from the Host header.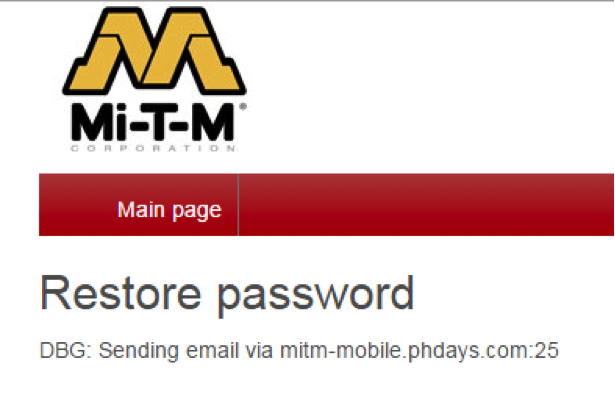
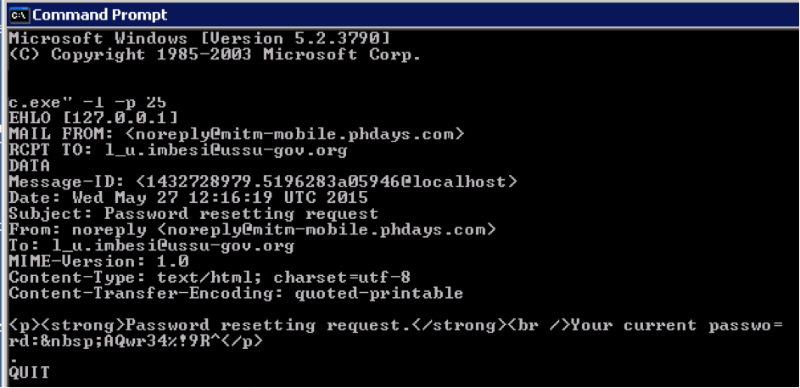
So, if you hang up netcat on port 25 and send a request with your IP address or domain name in the Host header, then a letter with the current password will be sent to port 25 ( AQwr34%! 9R ^ ).
Bonus: it was possible to go to the mail and find insider information in the drafts. The fact that from 10:30 am sms become cheaper, and this means that at this time is expected to increase in shares MiTM Mobile.
Correct answers: 4
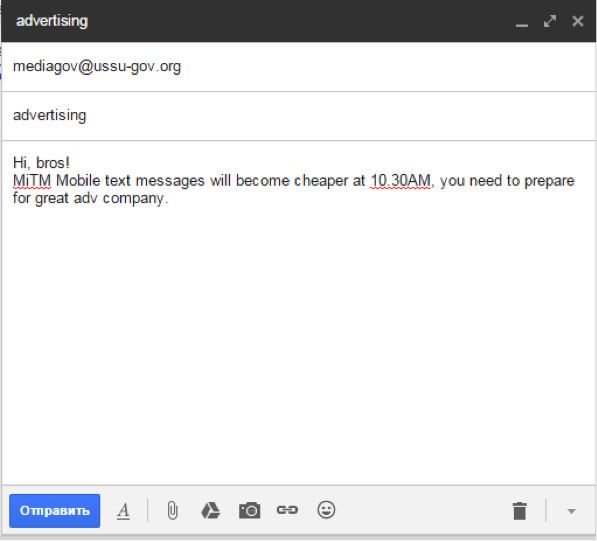
2.3. We need to find something to blackmail him
Unfortunately, nobody coped with this task. Where to look for a reason for blackmailing a person if not in his Google account? Mail life there is not very saturated, but the history of search queries gives a person with his head:
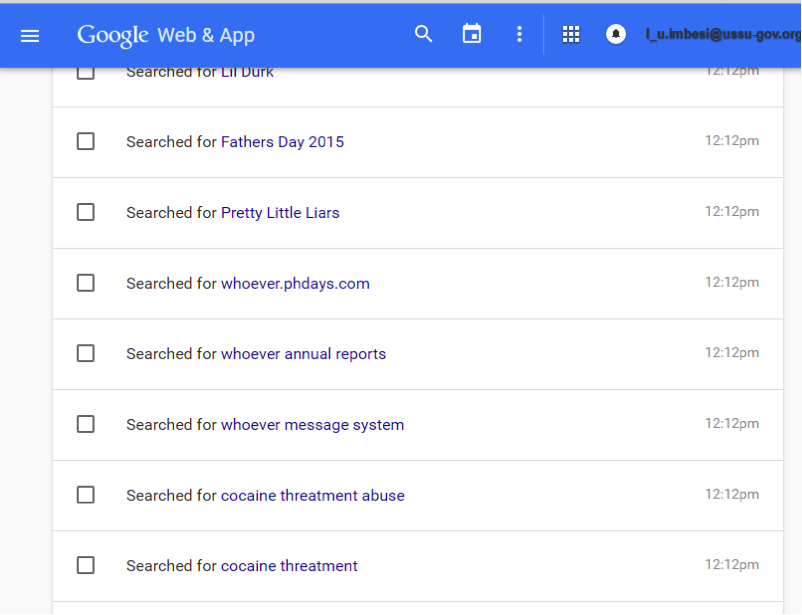
It turns out that the director of marketing moved to cocaine from alcohol ... ay-ay-ay, how bad it is! Correct answer: cocaine
Correct answers: 0
2.4. Some competitors with gov support are interested in directors jailing. Who is it?
Nobody could reach this technically difficult task either, because first it was necessary to go through the previous one. From the past assignment, it is clear that the director is also regularly trying to find the annual reports of a certain company Whoever, which is located on the domain whoever.phdays.com. Then everything is simple:
- Find robots.txt and find out what api.php is.
- Differently poke api.php, we guess parameters by errors. We understand that there is XXE and we merge sorts.
- We see that api.php has unserialize, which will allow INSERT SQL-inj.
- Having correctly inserted into the table, we call unserialize via index.php (the data from the database goes to unserialize) and finally we get RCE.
- In / home it was possible to find the email of the owner of Whoever - wh0wh0wh0ever@gmail.com
Correct answers: 0
3. This time is a big deal. Get infromation on President administration (ussu.phdays.com)
In this group, information about the presidential administration will have to be obtained in ways well known by the people.
3.1. Crawl all administration emails in order from a to z (format:
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012 ,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012 ,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012 | | |
|---|---|---|
| | |
| | |
,,, ...)
, : email . ussu.phdays.com/contacts.php.

, administration@ussu-gov.org for general requests.
MX- .

, , , email administration:

: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :
GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .


256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :

: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .


Chainbreaker Win32 keychain . #125_42-19.501

, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.

« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , , j_l.andrus@ussu-gov.org . McDonalds pushkin square.


: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.

— vk.com, , ptimes.phdays.com

, , , vk.com/id304632346 . email.

email FB, - .

, email FB Details, . : +79652843472#317

: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Positive Times. : sitemap.xml email, ( sentemails.log), , ptimes-registration@mailinator.com , — . , , - !
, , email.

? , email sentemails.log, ptimes@ussu-gov.org ? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .

( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .

uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :

: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)

: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .

md5(id) : md5 — Chipp37

,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671

: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.
,administration@ussu-gov.orgfor general requests.
MX- .
, , , email administration:
: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format::,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .

256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :
: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .

Chainbreaker Win32 keychain .#125_42-19.501
, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.
« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , ,j_l.andrus@ussu-gov.org. McDonalds pushkin square.

: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.
— vk.com, , ptimes.phdays.com
, , , vk.com/id304632346 . email.
email FB, - .
, email FB Details, . : +79652843472#317
: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format::)
Positive Times. : sitemap.xml email, ( sentemails.log), ,ptimes-registration@mailinator.com, — . , , - !
, , email.
? , email sentemails.log,ptimes@ussu-gov.org? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .
( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .
uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :
: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us., PositiveLeaks. , pleaks.phdays.com. :POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)
: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .
md5(id) : md5 — Chipp37
,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671
: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.
,administration@ussu-gov.orgfor general requests.
MX- .
, , , email administration:
: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format::,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .

256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :
: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .

Chainbreaker Win32 keychain .#125_42-19.501
, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.
« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , ,j_l.andrus@ussu-gov.org. McDonalds pushkin square.

: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.
— vk.com, , ptimes.phdays.com
, , , vk.com/id304632346 . email.
email FB, - .
, email FB Details, . : +79652843472#317
: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format::)
Positive Times. : sitemap.xml email, ( sentemails.log), ,ptimes-registration@mailinator.com, — . , , - !
, , email.
? , email sentemails.log,ptimes@ussu-gov.org? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .
( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .
uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :
: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us., PositiveLeaks. , pleaks.phdays.com. :POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)
: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .
md5(id) : md5 — Chipp37
,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671
: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012,,, ...)
, : email . ussu.phdays.com/contacts.php.
,administration@ussu-gov.orgfor general requests.
MX- .
, , , email administration:
: a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
: 19
3.2. Get all passwords, emails in order from a to z (format::,:,:, ...)
, Google . Sitemap.xml , ussu.phdays.com/_logs/access.log . , :GET /auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67 GET /auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
, - , . , , Padding Oracle , , .

256 , 99% , . 10 000 . , , .
, , ? email- id, 4 .
Google, :
: a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
: 6
, Oracle, :
blog.skullsecurity.org/2013/padding-oracle-attacks-in-depth
, :
www.slideshare.net/kochetkov.vladimir/hdswasm-russianproofreaded
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
. Mac OS — . , .

Chainbreaker Win32 keychain .#125_42-19.501
, « Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT) and MiTM Mobile (MITM)» 27 11 .
: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
. d_b.bertil@ussu-gov.org Google Cloud Printers www.google.com/cloudprint FTP. Omnieye.
« ».
: 0
3.5. Finally, break into any Administration's Iphone. There were some secret meeting in April. In what place?
, , , icloud.com email, , ,j_l.andrus@ussu-gov.org. McDonalds pushkin square.

: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
, Positive Times USSU.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
— , : VK.com FB.com. fb.com.
— vk.com, , ptimes.phdays.com
, , , vk.com/id304632346 . email.
email FB, - .
, email FB Details, . : +79652843472#317
: «» .
: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format::)
Positive Times. : sitemap.xml email, ( sentemails.log), ,ptimes-registration@mailinator.com, — . , , - !
, , email.
? , email sentemails.log,ptimes@ussu-gov.org? - Mailinator , — , ptimes@ussu-gov.org:Pt1M3P@ss . — , .
( , ). 11:30 . , , , XSS SQLi.
: 13
4.3. Get access to email account of another corrupt journalist with email mediagov@ussu-gov.org. Give us his password.
ptimes.phdays.com/feedback.php Google , - feedbackupload. .htaccess, feedbackupload 5 .
uploaded-13-05-2015.docx mediagov@ussu-gov.org, , 188.166.78.21 :443/. , MSF, Heartbleed Metasploit ( , ) « » :
: www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . : P@S$W0_PD
: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us., PositiveLeaks. , pleaks.phdays.com. :POST /userPage HTTP/1.1 Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="template" 123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598 Content-Disposition: form-data; name="action" createTemplate -----------------------------214580240818081871851160929598--
( Boris_The_Emperor ), ;)
: 0
5. Stock Exchange financial director was incriminate, but there were no evidence. Help to jailed him.
.
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
, . id id — .
md5(id) : md5 — Chipp37
,
case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
: 39
5.2. There were no evidence of being Financial director in the crime scene. We can blackmail him with knowing of deviceid and iccid of his phone and SIM. Give us them (format deviceid;iccid)
DeviceId , , ussu.phdays.com/getdocument.php .
iccid, Google deviceid. : a94360c365ab38810639911d355103c86367d5ba;897019903020414671
: 3
5.3. Where is director hiding now? We need to know city.
, , . XSS DOM , ( ). , 3G- OiWei. - , 192.168.44.1 Access-Control-Allow-Origin: *. cellid : Hamilton
: 1
5.4. As you know now, Stock Exchange have a backdoor for Executives. Give us private key (Private-MAC for prove would be enough)
, . , , 0 day PHP, openbasedir /home. ...
: 0
51 . djecka — 9 . rdot , 12 .
1 djecka 1700 2 sharsil 1700 3 MZC 1600
« » :
« » PHDays IV “ “ PHDays III PHDays 2012
Source: https://habr.com/ru/post/261459/
All Articles